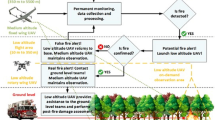
Abstract
Nowadays wireless sensor networks (WSNs) has been used in enormous applications for data collection in an unfriendly environment. Forest fire makes vast hazard to the consuming plant of the world. To preserve the forest from fire, sensor nodes monitor the environment temperature. If the temperature is increased and it exceeds the threshold, the sensor sends the notification message to the fire monitoring system. The forest fire is measured by Fire Weather Index. Most of the existing fire monitoring systems only highlight in detection, but not the verification of the sensor. Suppose, if the attacker inserts any malicious sensor, the malicious sensor sends false information or create an additional delay in fire monitoring system. As a result, the more chances for the forest to be destroyed by fire. To solve this problem, Shift Reduce Parser based Malicious Sensor Detection (SRP_MSD) in WSN is proposed. The Bivariate Pascal Triangle method hides the original identity of nodes, data route from the malicious observer and sends confidential information to the Base Station. This method is analyzed and evaluated using network simulator-2. The results show that it is possible to detect malicious sensor nodes and send the reliable information to the forest fire monitoring system.












Similar content being viewed by others
References
Lloret, J., Garcia, M., Bri, D., & Sendra, S. (2009). A wireless sensor network deployment for rural and forest fire detection and verification. Sensors, 9(11), 8722–8747.
Li, W., & Zhu, X. (2016). BAN-trust: An attack-resilient malicious node detection scheme for body area networks. In 2016 IEEE International conference on computing, networking, and communications, 1–5.
Molina-Pico, A., Cuesta-Frau, D., Araujo, A., Alejandre, J., & Rozas, A. (2016). Forest monitoring and wildland early fire detection by a hierarchical wireless sensor network. Journal of Sensors. https://doi.org/10.1155/2016/8325845.
Aravindh, S., Vinoth, R. S., & Vijayan, R. (2013). A trust-based approach for detection and isolation of malicious nodes in MANETs. International Journal of Engineering and Technology, 5(1), 193–199.
Sajjad, S. M., Bouk, S. H., & Yousaf, M. (2015). Neighbor node trust based intrusion detection system for WSN. 6th International Conference on Emerging Ubiquitous Systems and Pervasive Networks, 63, 183–188.
Prabha, V. R., & Latha, P. (2017). Fuzzy trust protocol for malicious node detection in wireless sensor networks. Wireless Personal Communications, 94(4), 2549–2559.
Ho, J. W., Wright, M., & Das, S. K. (2012). Distributed detection of mobile malicious node attacks in wireless sensor networks. Ad Hoc Networks, 10(3), 512–523.
Lal, N., Kumar, S., Saxena, A., & Chaurasiya, V. K. (2015). Detection of malicious node behaviour via I-watchdog protocol in mobile Ad Hoc network with DSDV routing scheme. Procedia Computer Science, 49, 264–273.
Subba, B., Biswas, S., & Karmakar, S. (2016). Intrusion detection in Mobile Ad hoc networks: Bayesian game formulation. Engineering Science and Technology, An International Journal, 19(2), 782–799.
Anjana, K. P., & Preetha, K. G. (2016). A novel approach for malicious node detection in MANET. In A. Abraham (Ed.), Innovations in bio-inspired computing and applications (pp. 163–173). Springer.
Zhang, Y., Shen, Y., Wang, H., Yong, J., & Jiang, X. (2016). On secure wireless communications for IoT under eavesdropper collusion. IEEE Transactions on Automation Science and Engineering, 13(3), 1281–1293.
Zhang, H., Cheng, P., Shi, L., & Chen, J. (2016). Optimal DoS attack scheduling in wireless networked control system. IEEE Transactions on Control Systems Technology, 24(3), 843–852.
Kumar, P., Gurtov, A., Iinatti, J., Ylianttila, M., & Sain, M. (2016). Lightweight and secure session-key establishment scheme in smart home environments. IEEE Sensors Journal, 16(1), 254–264.
Li, Y. (2013). Design of a key establishment protocol for smart home energy management system. In Computational intelligence, fifth international conference on communication systems and networks (CICSyN), June 2013 (pp. 88–93).
Han, K., Kim, J., Shon, T., & Ko, D. (2013). A novel secure key pairing protocol for rf4ce ubiquitous smart home systems. Personal and Ubiquitous Computing, 17(5), 945–949.
Sun, B., Li, C. C., Wu, K., & Xiao, Y. (2006). A lightweight secure protocol for wireless sensor networks. Computer Communications, 29(13), 2556–2568.
Delgado-Mohatar, O., Fúster-Sabater, A., & Sierra, J. M. (2011). A light-weight authentication scheme for wireless sensor networks. Ad Hoc Networks, 9(5), 727–735.
Raja Rajeswari, S., & Seenivasagam, V. (2015). Secured energy conserving slot-based topology maintenance protocol for wireless sensor networks. Wireless Personal Communications, 87(2), 527–550.
Qiu, Y., Zhou, J., Baek, J., & Lopez, J. (2010). Authentication and key establishment in dynamic wireless sensor networks. Sensors, 10(4), 3718–3731.
Wang, R., Du, W., Liu, X., & Ning, P. (2009). ShortPK: A short-term public key scheme for broadcast authentication in sensor networks. ACM Transactions on Sensor Networks, 6(1), Article 9.
Khan, S. U., Pastrone, C., Lavagno, L., & Spirito, M. A. (2012). An authentication and key establishment scheme for the IP-based wireless sensor networks. Procedia Computer Science, 10, 1039–1045.
Kwon, T., & Hong, J. (2010). Secure and efficient broadcast authentication in wireless sensor networks. IEEE Transactions on Computers, 59(8), 1120–1133.
He, D., Chan, S., Tang, S., & Guizani, M. (2013). Secure data discovery and dissemination based on hash tree for wireless sensor networks. IEEE Transactions on Wireless Communications, 12(9), 4638–4646.
Tang, D., Li, T., Ren, J., & Wu, J. (2015). Cost-Aware SEcure Routing (CASER) protocol design for wireless sensor networks. IEEE Transactions on Parallel and Distributed Systems, 26(4), 960–973.
Han, S., Han, Y., Jin, Y., & Zhou, W. (1992). The method for calculating forest fire behavior index. Fire Safety Science, 1, 77–82.
Johnson, E. A., Keith, D. M., & Martin, Y. E. (2013). Comparing measured duff moisture with a water budget model and the Duff and Drought Codes of the Canadian Fire Weather Index. Forest Science, 59(1), 78–92.
Bouabdellah, K., Noureddine, H., & Larbi, S. (2013). Using wireless sensor networks for reliable forest fires detection. Procedia Computer Science, 19, 794–801.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Komathi, A., Pushparani, M. Shift Reduce Parser Based Malicious Sensor Detection for Predicting Forest Fire in WSNs. Wireless Pers Commun 103, 2843–2861 (2018). https://doi.org/10.1007/s11277-018-5966-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-018-5966-0