Abstract
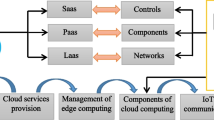
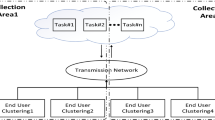
With the continuous development of science and technology, artificial intelligence technology, deep learning technology, and signal transmission technology have all been rapidly developed. The products of artificial intelligence can be used in all kinds of people’s lives and studies, making people’s lives and learning is more convenient. Some universities should also change their own teaching management methods, improve the quality of teaching, catch up with the trend of artificial intelligence development, improve the competitiveness of schools, and cultivate more talents for the society. Edge computing technology is a component of cloud computing. It can calculate data stored in cloud computing and has good storage capabilities. Users can calculate and store large quantities of data through edge computing technology. At present, the role of edge computing technology is becoming more and more important. In this research, we first gave a brief introduction to 5G technology, explained the role and status of 5G technology, and then conducted an in-depth analysis from the perspective of edge computing, and compared edge technology with other technologies. Deepen the understanding of edge computing technology. We also discussed the management of many universities in combination with 5G technology. The system we designed has three-tier architecture, including three functional modules, and each functional module is divided into multiple sub-modules. Finally, we made plans and suggestions for the development of artificial intelligence technology in university.





Similar content being viewed by others
References
Dadvar, M., Trieschnigg, D., Ordelman, R., de Jong, F. (2013). Improving cyberbullying detection with user context. In: European Conference on Information Retrieval, (pp. 693–696). Berlin, Heidelberg: Springer.
Dadvar, M., Jong, F. D., Ordelman, R., Trieschnigg, D. (2012). Improved cyberbullying detection using gender information. In: Proceedings of the Twelfth Dutch-Belgian Information Retrieval Workshop (DIR 2012). University of Ghent.
Raisi, E., Huang, B. (2017). Cyberbullying detection with weakly supervised machine learning. In: Proceedings of the 2017 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining 2017, pp. 409–416. ACM.
Balakrishnan, V., Khan, S., & Arabnia, H. R. (2020). Improving cyberbullying detection using Twitter users’ psychological features and machine learning. Computer's & Security, 90: 101710.
Kumar, A., Sachdeva, N. (2020). Cyberbullying checker: Online bully content detection using hybrid supervised learning. In: International Conference on Intelligent Computing and Smart Communication 2019, (pp. 371–382). Singapore: Springer.
Dadvar, M., & Eckert, K. (2018). Cyberbullying detection in social networks using deep learning based models; a reproducibility study. arXiv:1812.08046.
Agrawal, S., Awekar, A. (2018). Deep learning for detecting cyberbullying across multiple social media platforms. In: European Conference on Information Retrieval, (pp. 141–153). Cham: Springer.
Cheng, L., Guo, R., Silva, Y., Hall, D., Liu, H. (2019). Hierarchical attention networks for cyberbullying detection on the instagram social network. In: Proceedings of the 2019 SIAM International Conference on Data Mining, (pp. 235–243). Society for Industrial and Applied Mathematics.
Al-Hashedi, M., Soon, L. K., Goh, H. N. (2019). Cyberbullying detection using deep learning and word embeddings: an empirical study. In: Proceedings of the 2019 2nd International Conference on Computational Intelligence and Intelligent Systems, pp. 17–21.
Founta, A. M., Chatzakou, D., Kourtellis, N., Blackburn, J., Vakali, A., Leontiadis, I. (2019). A unified deep learning architecture for abuse detection. In: Proceedings of the 10th ACM Conference on Web Science, pp. 105–114.
Mahlangu, T., Tu, C. (2019). Deep learning cyberbullying detection using stacked embbedings approach. In: 2019 6th International Conference on Soft Computing & Machine Intelligence (ISCMI), pp. 45–49. IEEE.
Singh, V. K., Ghosh, S., Jose, C. (2019). Toward multimodal cyberbullying detection. In: Proceedings of the 2017 CHI Conference Extended Abstracts on Human Factors in Computing Systems, pp. 2090–2099.
Yang, F., Peng, X., Ghosh, G., Shilon, R., Ma, H., Moore, E., Predovic, G. (2019). Exploring deep multimodal fusion of text and photo for hate speech classification. In: Proceedings of the Third Workshop on Abusive Language Online, pp. 11–18.
Kansara, K. B., & Shekokar, N. M. (2015). A framework for cyberbullying detection in social network. Int J Current Eng Technol, 5(1), 494–498.
He, Z. (2015). Exploiting the topology property of social network for rumor detection. In: 2015 12th International Joint Conference on Computer Science and Software Engineering (JCSSE), pp. 41–46. IEEE.
Kumar, A., Sangwan, S. R., & Nayyar, A. (2019). Rumour veracity detection on twitter using p swarm optimized shallow classifiers. Multimed. Tools Appl., 78(17), 24083–24101.
Kumar, A., Sangwan, S. R. (2018). Rumour detection using machine learning techniques on social media. In: International Conference on Innovative Computing and Communication. Lecture Notes in Networks and Systems. Springer.
Yang, F., Liu, Y., Yu, X., Yang, M. (2012). Automatic detection of rumor on Sina Weibo. In: Proceedings of the ACM SIGKDD Workshop on Mining Data Semantics, p. 13. ACM.
Zhang, Q., Zhang, S., Dong, J., Xiong, J., & Cheng, X. (2015). Automatic detection of rumor on social network. In J. Li, H. Ji, D. Zhao, & Y. Feng (Eds.), Natural Language Processing and Chinese Computing. NLPCC 2015 (Vol. 9362, pp. 113–122). Cham: Springer.
Jin, Z., Cao, J., Jiang, Y. G., Zhang, Y. (2014). News credibility evaluation on microblog with a hierarchical propagation model. In: 2014 IEEE International Conference on Data Mining, pp. 230–239. IEEE.
Wang, S., Terano, T. (2015). Detecting rumor patterns in streaming social media. In: 2015 IEEE International Conference on Big Data (Big Data), pp. 2709–2715. IEEE.
Sahana, V. P., Pias, A. R., Shastri, R., Mandloi, S. (2015). Automatic detection of rumoured tweets and finding its origin. In: 2015 International Conference on Computing and Network Communications (CoCoNet), pp. 607–612. IEEE.
Zhao, Z., Resnick, P., Mei, Q. (2015). Enquiring minds: Early detection of rumors in social media from enquiry posts. In: Proceedings of the 24th International Conference on World Wide Web, pp. 1395–1405. International World Wide Web Conferences Steering Committee. https://doi.org/10.1007/978-3-319-67217-5_8.
Acknowledgements
This research has been supported by the Ministry of Education Human Society project of China (No. 20YJC760030), the key projects of Teaching Research and Teaching Reform of Nanjing Institute of Technology (No. JG2019009), the First Class Curriculum Construction project of Nanjing Institute of Technology (No. YZKC2019067), the Higher Education Research project of Nanjing Institute of Technology(No.2019YB26), Cultural and Artistic Creativity Design Institute (No. CACD202003).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Hou, J., Xu, L. Management of university and artificial intelligence statistics for 5G edge computing. Wireless Netw (2021). https://doi.org/10.1007/s11276-021-02689-w
Accepted:
Published:
DOI: https://doi.org/10.1007/s11276-021-02689-w