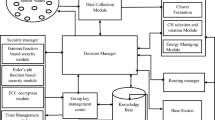
Abstract
The security of data communicated through wireless networks is a challenging issue due to the presence of malicious and unauthenticated users whose intention is either to disrupt the communication or to know context of the data communicated to perform data theft and prevent the communication made by genuine users. To address this problem, a new secure routing algorithm with a novel encryption scheme is proposed in this paper using the cyclic group based Elliptic curve cryptography in which an encryption key is formed from the points taken from the Beta and Gamma functions in the elliptic key cryptography. For this purpose, the elliptic key is encrypted using the proposed encryption and decryption schemes. Further, it is proved that the proposed model decreases the computational complexity and increases the security, when it is compared to the other signature schemes. This scheme has been tested both analytically and using computer implementation of the proposed secure routing algorithm for wireless sensor networks. It is proved that this proposed scheme is more reliable in providing security than the existing algorithms. The cyclic group used in this work makes the number of elements to be from a finite set of integers and hence the computational complexity is reduced and finite. The experiments have been carried out using Python coding and by transmitting different number of words through the wireless network. It is found that overall complexity for encryption and communication is less in this proposed algorithm than the existing Elliptic Curve Cryptography algorithm.









Similar content being viewed by others
References
Diffie, W., & Hellman, M. (1976). New directions in cryptography. IEEE Transactions on Information Theory, 22(6), 644–654.
Das, A., & Veni Madhavan, C. E. (2009). Public-key cryptography: Theory and practice. New Delhi: Pearson Education India.
Vijayakumar, P., Bose, S., & Kannan, A. (2013). Centralized key distribution protocol using the greatest common divisor method. Computers & Mathematics Applications, 65(9), 1360–1368.
Ferng, H. W., Tendean, R., & Kurniawan, A. (2012). Energy-efficient routing protocol for wireless sensor networks with static clustering and dynamic structure. Wireless Personal Communications, 65(2), 347–367.
Younis, O., & Fahmy, S. (2004). HEED: A hybrid, energy-efficient, distributed clustering approach for ad hoc sensor networks. IEEE Transactions on Mobile Computing, 3(4), 366–379.
Heinzelman, W. B., Chandrakasan, A. P., & Balakrishnan, H. (2002). An application-specific protocol architecture for wireless microsensor networks. IEEE Transactions on Wireless Communications, 1(4), 660–670.
Heinzelman, W. R., Chandrakasan, A., & Balakrishnan, H. (2000). Energy-efficient communication protocol for wireless microsensor networks. In Proceedings of the 33rd annual Hawaii international conference on System sciences, 2000 (pp. 3005–3014). IEEE.
Logambigai, R., & Kannan, A. (2016). Fuzzy logic based unequal clustering for wireless sensor networks. Wireless Networks, 22(3), 945–957.
Miller, V. S. (1985). Use of elliptic curves in cryptography. In Conference on the theory and application of cryptographic techniques (pp. 417–426). Berlin: Springer.
Koblitz, N. (1987). Elliptic curve cryptosystems. Mathematics of Computation, 48(177), 203–209.
Rivest, R. L., Shamir, A., & Adleman, L. (1978). A method for obtaining digital signatures and public-key cryptosystems. Communications of the ACM, 21(2), 120–126.
Hankerson, D., Menezes, A. J., & Vanstone, S. (2006). Guide to elliptic curve cryptography. Berlin: Springer.
Chou, W., & Washington, D. L. (2003). Elliptic curve cryptography and its applications to mobile devices. College Park: University of Maryland.
Koblitz, N., Menezes, A., & Vanstone, S. (2000). The state of elliptic curve cryptography. Designs, Codes and Cryptography, 19(2–3), 173–193.
Dabholkar, A., & Yow, K. C. (2004). Efficient implementation of elliptic curve cryptography (ECC) for personal digital assistants (PDAs). Wireless Personal Communications, 29(3–4), 233–246.
Silverman, J. H. (1985). The arithmetic of elliptic curves. Berlin: Springer.
Andrews, G. E., Askey, R., & Roy, R. (1999). Special functions. In Encyclopaedia of mathematics and its applications (Vol. 71).
Natanael, Dimas, & Faisal, Dewi Suryani. (2018). Text encryption in android chat applications using Elliptic Curve Cryptography (ECC). Procedia Computer Science, 135(2018), 283–291.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Viswanathan, S., Kannan, A. Elliptic key cryptography with Beta Gamma functions for secure routing in wireless sensor networks. Wireless Netw 25, 4903–4914 (2019). https://doi.org/10.1007/s11276-019-02073-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-019-02073-9