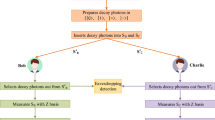
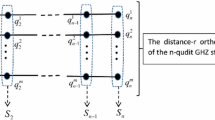
Abstract
Quantum secret sharing is a way to share secret messages among several people using the quantum channel with unconditional security. Hillery et al. (Phys Rev A 59(3):1829, 1999) proposed the first quantum secret sharing protocol for three parties by using the 3-qubit GHZ states and a possible generalization of the protocol for four parties by using the 4-qubit GHZ states. Also in the same paper, they proposed a three-party secret-sharing scheme to share quantum states. Later Xiao et al. (Phys Rev A 69(5):052307, 2004) generalized the quantum secret sharing protocol for n parties to share a classical secret message. In this paper, we implement these protocols in IBM simulators as well as real backends and check security against some quantum attacks. Also, we create a noise model and simulate the protocols using the noise model. Finally, we use the zero noise extrapolation method to mitigate errors due to noise.











































Similar content being viewed by others
Data availability
No dataset is available. Graphs and histograms are generated using Python code by running quantum circuits.
References
Shor, P.W.: Algorithms for quantum computation: discrete logarithms and factoring. In: Proceedings 35th Annual Symposium on Foundations of Computer Science, pp. 124–134. IEEE (1994)
Wootters, W.K., Zurek, W.H.: A single quantum cannot be cloned. Nature 299(5886), 802–803 (1982)
Heisenberg, W.: Über den anschaulichen inhalt der quantentheoretischen kinematik und mechanik. In: Original Scientific Papers Wissenschaftliche Originalarbeiten, pp. 478–504. Springer, New York (1985)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. Theor. Comput. Sci. 560, 7–11 (2014). Theoretical Aspects of Quantum Cryptography - celebrating 30 years of BB84
Ekert, A.K.: Quantum cryptography based on bell’s theorem. Phys. Rev. Lett. 67(6), 661 (1991)
Bennett, C.H., Bessette, F., Brassard, G., Salvail, L., Smolin, J.: Experimental quantum cryptography. J. Cryptol. 5(1), 3–28 (1992)
Lo, H.-K., Ma, X., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett. 94(23), 230504 (2005)
Alléaume, R., Branciard, C., Bouda, J., Debuisschert, T., Dianati, M., Gisin, N., Godfrey, M., Grangier, P., Länger, T., Lütkenhaus, N., et al.: Using quantum key distribution for cryptographic purposes: a survey. Theor. Comput. Sci. 560, 62–81 (2014)
Liao, S.-K., Cai, W.-Q., Liu, W.-Y., Zhang, L., Li, Y., Ren, J.-G., Yin, J., Shen, Q., Cao, Y., Li, Z.-P., et al.: Satellite-to-ground quantum key distribution. Nature 549(7670), 43–47 (2017)
Xu, F., Ma, X., Zhang, Q., Lo, H.-K., Pan, J.-W.: Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 92(2), 025002 (2020)
Xie, Y.-M., Lu, Y.-S., Weng, C.-X., Cao, X.-Y., Jia, Z.-Y., Bao, Y., Wang, Y., Fu, Y., Yin, H.-L., Chen, Z.-B.: Breaking the rate-loss bound of quantum key distribution with asynchronous two-photon interference. PRX Quantum 3(2), 020315 (2022)
Grünenfelder, F., Boaron, A., Resta, G.V., Perrenoud, M., Rusca, D., Barreiro, C., Houlmann, R., Sax, R., Stasi, L., El-Khoury, S., Hänggi, E., Bosshard, N., Bussiéres, F., Zbinden, H.: Fast single-photon detectors and real-time key distillation enable high secret-key-rate quantum key distribution systems. Nat. Photonics 17(5), 422–426 (2023)
Li, W., Zhang, L., Tan, H., Lu, Y., Liao, S.-K., Huang, J., Li, H., Wang, Z., Mao, H.-K., Yan, B., Li, Q., Liu, Y., Zhang, Q., Peng, C.-Z., You, L., Xu, F., Pan, J.-W.: High-rate quantum key distribution exceeding 110 mb s\(^{-1}\). Nat. Photonics 17(5), 416–421 (2023)
Zhou, L., Lin, J., Jing, Y., Yuan, Z.: Twin-field quantum key distribution without optical frequency dissemination. Nat. Commun. 14(1), 928 (2023)
Das, N., Paul, G.: Two efficient measurement device independent quantum dialogue protocols. Int. J. Quantum Inf. 18(07), 2050038 (2020)
Deng, F.-G., Long, G.L., Liu, X.-S.: Two-step quantum direct communication protocol using the einstein-podolsky-rosen pair block. Phys. Rev. A 68(4), 042317 (2003)
Das, N., Paul, G.: Cryptanalysis of quantum secure direct communication protocol with mutual authentication based on single photons and bell states. Europhys. Lett. 138(4), 48001 (2022)
Das, N., Paul, G.: Secure multi-party quantum conference and xor computation. Quantum Inf. Comput. 21(3–4), 0203–0232 (2021)
Das, N., Paul, G., Majumdar, R.: Quantum secure direct communication with mutual authentication using a single basis. Int. J. Theor. Phys. 60(11), 4044–4065 (2021)
Das, N., Paul, G.: Measurement-device-independent quantum secure direct communication with user authentication. Quantum Inf. Process. 21(7), 207 (2022)
Zhou, L., Sheng, Y.-B.: One-step device-independent quantum secure direct communication. Sci. China Phys. Mech. Astron. 65(5), 250311 (2022)
Liu, X., Li, Z., Luo, D., Huang, C., Ma, D., Geng, M., Wang, J., Zhang, Z., Wei, K.: Practical decoy-state quantum secure direct communication. Sci. China Phys. Mech. Astron. 64(12), 120311 (2021)
Liu, X., Luo, D., Lin, G., Chen, Z., Huang, C., Li, S., Zhang, C., Zhang, Z., Wei, K.: Fiber-based quantum secure direct communication without active polarization compensation. Sci. China Phys. Mech. Astron. 65(12), 120311 (2022)
Zhang, H., Sun, Z., Qi, R., Yin, L., Long, G.-L., Lu, J.: Realization of quantum secure direct communication over 100 km fiber with time-bin and phase quantum states. Light Sci. Appl. 11(1), 83 (2022)
Zhou, L., Xu, B.-W., Zhong, W., Sheng, Y.-B.: Device-independent quantum secure direct communication with single-photon sources. Phys. Rev. Appl. 19(1), 014036 (2023)
Cao, Z., Wang, L., Liang, K., Chai, G., Peng, J.: Continuous-variable quantum secure direct communication based on gaussian mapping. Phys. Rev. Appl. 16(2), 024012 (2021)
Hong, Y.-P., Zhou, L., Zhong, W., Sheng, Y.-B.: Measurement-device-independent three-party quantum secure direct communication. Quantum Inf. Process. 22(2), 111 (2023)
Hillery, M., Bužek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59(3), 1829–1834 (1999)
Xiao, L., Long, G.L., Deng, F.-G., Pan, J.-W.: Efficient multi-party quantum secret sharing schemes. Phys. Rev. A 69(5), 052307 (2004)
Zhang, Z.-j, Li, Y., Man, Z.-x: Multiparty quantum secret sharing. Phys. Rev. A 71(4), 044301 (2005)
Guo, G.-P., Guo, G.-C.: Quantum secret sharing without entanglement. Phys. Lett. A 310(4), 247–251 (2003)
Gottesman, D.: Theory of quantum secret sharing. Phys. Rev. A 61(4), 042311 (2000)
Tittel, W., Zbinden, H., Gisin, N.: Experimental demonstration of quantum secret sharing. Phys. Rev. A 63(4), 042301 (2001)
Zhou, Y., Yu, J., Yan, Z., Jia, X., Zhang, J., Xie, C., Peng, K.: Quantum secret sharing among four players using multipartite bound entanglement of an optical field. Phys. Rev. Lett. 121(15), 150502 (2018)
Joy, D., Sabir, M., Behera, B.K., Panigrahi, P.K.: Implementation of quantum secret sharing and quantum binary voting protocol in the ibm quantum computer. Quantum Inf. Process. 19(1), 1–20 (2020)
Liao, Q., Liu, H., Zhu, L., Guo, Y.: Quantum secret sharing using discretely modulated coherent states. Phys. Rev. A 103(3), 032410 (2021)
Yin, H.-L., Fu, Y., Li, C.-L., Weng, C.-X., Li, B.-H., Gu, J., Lu, Y.-S., Huang, S., Chen, Z.-B.: Experimental quantum secure network with digital signatures and encryption. Natl. Sci. Rev. 10(4), 228 (2022)
Sheng, Y.-B., Zhou, L.: Accessible technology enables practical quantum secret sharing. Sci. China Phys. Mech. Astron. 66(6), 260331 (2023)
Zhang, T., Zhou, L., Zhong, W., Sheng, Y.-B.: Multiple-participant measurement-device-independent quantum secret sharing protocol based on entanglement swapping. Laser Phys. Lett. 20(2), 025203 (2023)
Zhang, X., Wang, L., Lin, S., Wang, N., Hong, L.: Rational quantum secret sharing scheme based on ghz state. Quantum Inf. Process. 22(2), 91 (2023)
Bai, C.-M., Zhang, S., Liu, L.: Quantum secret sharing based on quantum information masking. Quantum Inf. Process. 21(11), 377 (2022)
Li, F., Hu, H., Zhu, S., Yan, J., Ding, J.: A verifiable (k, n)-threshold dynamic quantum secret sharing scheme. Quantum Inf. Process. 21(7), 259 (2022)
Bai, C.-M., Zhang, S., Liu, L.: Quantum secret sharing for a class of special hypergraph access structures. Quantum Inf. Process. 21(3), 119 (2022)
Tsai, C.-W., Yang, C.-W., Lin, J.: Multiparty mediated quantum secret sharing protocol. Quantum Inf. Process. 21(2), 63 (2022)
Yan, C., Li, Z., Liu, L., Lu, D.: Cheating identifiable (k, n) threshold quantum secret sharing scheme. Quantum Inf. Process. 21(1), 8 (2022)
Zhou, N., Zeng, G., Xiong, J.: Quantum key agreement protocol. Electron. Lett. 40(18), 1 (2004)
Chong, S.-K., Hwang, T.: Quantum key agreement protocol based on bb84. Opt. Commun. 283(6), 1192–1195 (2010)
Liu, B., Gao, F., Huang, W., Wen, Q.-y: Multiparty quantum key agreement with single particles. Quantum Inf. Process. 12(4), 1797–1805 (2013)
Zhou, N.-R., Zhu, K.-N., Wang, Y.-Q.: Three-party semi-quantum key agreement protocol. Int. J. Theor. Phys. 59(3), 663–676 (2020)
Das, N., Majumdar, R.: Comment on “quantum key agreement protocol’’. Int. J. Quantum Inf. 18(07), 2050039 (2020)
Yang, Y.-G., Lv, X.-L., Gao, S., Zhou, Y.-H., Shi, W.-M.: Detector-device-independent quantum key agreement based on single-photon bell state measurement. Int. J. Theor. Phys. 61(2), 1–16 (2022)
Shamir, A.: How to share a secret. Commun. ACM 22(11), 612–613 (1979)
Blakley, G.: Safeguarding cryptographic keys. In: Managing Requirements Knowledge, International Workshop On, p. 313. IEEE Computer Society, Los Alamitos, CA, USA (1979)
Karlsson, A., Koashi, M., Imoto, N.: Quantum entanglement for secret sharing and secret splitting. Phys. Rev. A 59(1), 162 (1999)
Cleve, R., Gottesman, D., Lo, H.-K.: How to share a quantum secret. Phys. Rev. Lett. 83(3), 648 (1999)
Karimipour, V., Bahraminasab, A., Bagherinezhad, S.: Entanglement swapping of generalized cat states and secret sharing. Phys. Rev. A 65(4), 042320 (2002)
Bagherinezhad, S., Karimipour, V.: Quantum secret sharing based on reusable greenberger-horne-zeilinger states as secure carriers. Phys. Rev. A 67(4), 044302 (2003)
Deng, F.-G., Long, G.L.: Secure direct communication with a quantum one-time pad. Phys. Rev. A 69(5), 052319 (2004)
Singh, S.K., Srikanth, R.: Generalized quantum secret sharing. Phys. Rev. A 71(1), 012328 (2005)
Deng, F.-G., Zhou, H.-Y., Long, G.L.: Circular quantum secret sharing. J. Phys. A Math. Gen. 39(45), 14089 (2006)
Hsu, J.-L., Chong, S.-K., Hwang, T., Tsai, C.-W.: Dynamic quantum secret sharing. Quantum Inf. Process. 12(1), 331–344 (2013)
Zhang, K.-J., Zhang, X., Jia, H.-Y., Zhang, L.: A new n-party quantum secret sharing model based on multiparty entangled states. Quantum Inf. Process. 18(3), 1–15 (2019)
Sutradhar, K., Om, H.: Efficient quantum secret sharing without a trusted player. Quantum Inf. Process. 19(2), 1–15 (2020)
Chen, Y.-A., Zhang, A.-N., Zhao, Z., Zhou, X.-Q., Lu, C.-Y., Peng, C.-Z., Yang, T., Pan, J.-W.: Experimental quantum secret sharing and third-man quantum cryptography. Phys. Rev. Lett. 95(20), 200502 (2005)
Schmid, C., Trojek, P., Bourennane, M., Kurtsiefer, C., Żukowski, M., Weinfurter, H.: Experimental single qubit quantum secret sharing. Phys. Rev. Lett. 95(23), 230505 (2005)
Gaertner, S., Kurtsiefer, C., Bourennane, M., Weinfurter, H.: Experimental demonstration of four-party quantum secret sharing. Phys. Rev. Lett. 98(2), 020503 (2007)
Bell, B., Markham, D., Herrera-Martí, D., Marin, A., Wadsworth, W., Rarity, J., Tame, M.: Experimental demonstration of graph-state quantum secret sharing. Nat. Commun. 5(1), 1–12 (2014)
Wu, X., Wang, Y., Huang, D.: Passive continuous-variable quantum secret sharing using a thermal source. Phys. Rev. A 101(2), 022301 (2020)
Wang, B.: Dwave Systems Adiabatic Quantum Computer. Next Big Future (2009). https://www.nextbigfuture.com/2009/10/dwave-systems-adiabatic-quantum.html
al., F.A.: Quantum supremacy using a programmable superconducting processor. Nature 574(7779), 505–510 (2019)
Castelvecchi, D.: Ibm’s quantum cloud computer goes commercial. Nature 543(7644), 159 (2017)
al., K.W.: Benchmarking an 11-qubit quantum computer. Nat. Commun. 10(1), 5464 (2019)
al., P.C.H.: Continuous-variable quantum computing in optical time-frequency modes using quantum memories. Phys. Rev. Lett. 113(13), 130502 (2014)
Krantz, P., Kjaergaard, M., Yan, F., Orlando, T.P., Gustavsson, S., Oliver, W.D.: A quantum engineer’s guide to superconducting qubits. Appl. Phys. Rev. 6(2), 021318 (2019)
Zhang, X., Li, H.-O., Wang, K., Cao, G., Xiao, M., Guo, G.-P.: Qubits based on semiconductor quantum dots. Chin. Phys. B 27(2), 020305 (2018)
Cirac, J.I., Zoller, P.: Quantum computations with cold trapped ions. Phys. Rev. Lett. 74(20), 4091–4094 (1995)
Preskill, J.: Quantum computing in the NISQ era and beyond. Quantum 2, 79 (2018)
Cao, N., Lin, J., Kribs, D., Poon, Y.-T., Zeng, B., Laflamme, R.: NISQ: Error Correction, Mitigation, and Noise Simulation (2022). arxiv:2111.02345
Temme, K., Bravyi, S., Gambetta, J.M.: Error mitigation for short-depth quantum circuits. Phys. Rev. Lett. 119(18), 180509 (2017)
Giurgica-Tiron, T., Hindy, Y., LaRose, R., Mari, A., Zeng, W.J.: Digital zero noise extrapolation for quantum error mitigation. In: 2020 IEEE International Conference on Quantum Computing and Engineering (QCE), pp. 306–316 (2020). IEEE
Qiskit for Quantum Computation. https://www.ibm.com/blogs/research/2018/02/qiskit-index/
Open-Source Quantum Development. https://qiskit.org/
Nielsen, M.A., Chuang, I.L.: Quantum Computation and Quantum Information: First South Asia Edition, 10th edn., pp. 373–386. Cambridge University Press, Cambridge (2013). Chap. 8. First south asia edition
Qiskit Documentation: Error from backend. https://qiskit.org/documentation/stable/0.19/stubs/qiskit.providers.aer.noise.NoiseModel.from_backend.html
Qiskit Documentation: Device gate error. https://qiskit.org/documentation/stable/0.19/stubs/qiskit.providers.aer.noise.device.basic_device_gate_errors.html
Jattana, M.S., Jin, F., Raedt, H.D.: General error mitigation for quantum circuits. Quantum Inf. Process. 19(11), 414 (2020)
Qiskit Textbook: Measurement Error Mitigation. https://qiskit.org/textbook/ch-quantum-hardware/measurement-error-mitigation.html
Cai, Z., Babbush, R., Benjamin, S.C., Endo, S., Huggins, W.J., Li, Y., McClean, J.R., O\(\acute{{\rm B}}\)rien, T.E.: Quantum Error Mitigation. Preprint arXiv:2210.00921 (2022)
Fair-Share Queuing. https://quantum-computing.ibm.com/lab/docs/iql/manage/systems/queue/
Acknowledgements
The authors are very thankful to the IBM team and the IBM Q Experience project. The views developed in this work are only those of the authors and do not reflect the official policy, opinions or position of IBM or the IBM Q Experience team.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
There is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Basak, N., Das, N., Paul, G. et al. Quantum secret sharing protocol using GHZ state: implementation on IBM qiskit. Quantum Inf Process 22, 393 (2023). https://doi.org/10.1007/s11128-023-04129-4
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-023-04129-4