Abstract
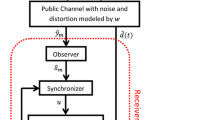
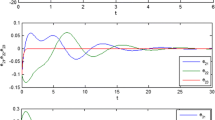
In this paper, the security performance analysis for a self-synchronization and closed-loop feedback-based chaotic stream cipher is given. According to the chosen-ciphertext attack method, it is found that under the condition of selecting the ciphertext as fixed value, the original chaotic iterative equation is degenerated into an asymptotically stable iterative one, so that the explicit function of state variables and key parameters can be obtained. Based on this idea, and according to the chosen-ciphertext attack method, a single key decipher algorithm is further investigated. Firstly, multiple pairs of plaintext–ciphertext are obtained by choosing the corresponding multiple frames of ciphertext as fixed values. Secondly, a set of possible estimated values for this single key is acquired by utilizing among one pair of plaintext–ciphertext. Finally, the only estimated value that satisfies all the conditions of multiple pairs of plaintext–ciphertext is determined, as an estimated value from the set of all possible estimated values. Security performance analysis results have shown that, under the condition that only one unknown key needs to be deciphered while the remaining keys are all known, the proposed algorithm can, respectively, decipher each individual key accurately. In addition, the attack complexity of the proposed method is lower than that of the exhaustive attack.










Similar content being viewed by others
References
Chen, Z., Yuan, X., Yuan, Y., Iu, H.H.C., Fernando, T.: Parameter identification of chaotic and hyper-chaotic systems using synchronization-based parameter observer. IEEE Trans. Circuits Syst. I Regul. Pap. 63(9), 1464–1475 (2016)
Gan, Q., Yu, S., Li, C., Lü, J., Lin, Z., Chen, P.: Design and ARM-embedded implementation of a chaotic map-based multicast scheme for multiuser speech wireless communication. Int. J. Circuit Theory Appl. 45, 1849–1872 (2017)
Gao, F., Tong, H.Q.: Parameter estimation for chaotic system based on particle swarm optimization. Acta Physica Sin. 55(2), 577–582 (2006)
Gao, T., Chen, Z.: A new image encryption algorithm based on hyper-chaos. Phys. Lett. A 372(4), 394–400 (2008)
Hu, G., Feng, Z., Ruiling, M.: Chosen ciphertext attack on chaos communication based on chaotic synchronization. IEEE Trans. Circuits and Syst. I: Fundam. Theory Appl. 50(2), 275–279 (2003)
Kerckhoffs, A.: La cryptographie militaire. J. Des Sci. Mil. 9, 5–83 (1883)
Li, C., Chen, G.: On the security of a class of image encryption schemes. In: 2008 IEEE International Symposium on Circuits and Systems, pp. 3290–3293. IEEE (2008)
Li, C., Liu, Y., Zhang, L.Y., Chen, M.Z.: Breaking a chaotic image encryption algorithm based on modulo addition and xor operation. Int. J. Bifurc. Chaos 23(04), 1350075 (2013)
Li, C., Lo, K.T.: Optimal quantitative cryptanalysis of permutation-only multimedia ciphers against plaintext attacks. Sig. Process. 91(4), 949–954 (2011)
Li, S., Li, C., Chen, G., Bourbakis, N.G., Lo, K.T.: A general quantitative cryptanalysis of permutation-only multimedia ciphers against plaintext attacks. Sig. Process. Image Commun. 23(3), 212–223 (2008)
Lin, Z., Yu, S., Lü, J., Cai, S., Chen, G.: Design and arm-embedded implementation of a chaotic map-based real-time secure video communication system. IEEE Trans. Circuits Syst. Video Technol. 25(7), 1203–1216 (2015)
Lü, J., Chen, G.: A new chaotic attractor coined. Int. J. Bifurc. Chaos 12(03), 659–661 (2002)
Matthews, R.: On the derivation of a “chaotic” encryption algorithm. Cryptologia 13(1), 29–42 (1989)
Rao, K.D.D., Gangadhar, C.: Modified chaotic key-based algorithm for image encryption and its VLSI realization. In: 15th International Conference on Digital Signal Processing, pp. 439–442. IEEE (2007)
Van Den Bergh, F.: An analysis of particle swarm optimizers. Ph.D. thesis, University of Pretoria (2007)
Wang, J., Jiang, G.: Cryptanalysis of a hyper-chaotic image encryption algorithm and its improved version. Acta Physica Sin. 60(6), 83–93 (2011)
Wang, L., He, W.P., Wan, S.Q., Liao, L.J., He, T., Center, N.C.: Evolutionary modeling for parameter estimation for chaotic system. Acta Physica Sin. 63(1), 247–254 (2014)
Wu, C.W., Chua, L.O.: A simple way to synchronize chaotic systems with applications to secure communication systems. Int. J. Bifurc. Chaos 3(06), 1619–1627 (1993)
Xu, Y., Zhou, W., Fang, J., Sun, W.: Adaptive lag synchronization and parameters adaptive lag identification of chaotic systems. Phys. Lett. A 374(34), 3441–3446 (2010)
Yen, J., Guo, J.: Efficient hierarchical chaotic image encryption algorithm and its vlsi realisation. IEE Proc.-Vision, Image Signal Process. 147(2), 167–175 (2000)
Yu, S., Lü, J., Li, C.: Some progresses of chaotic cipher and its applications in multimedia secure communications. J. Electron. Inf. Technol. 38(3), 735–752 (2016)
Zhu, C., Sun, K.: Cryptanalysis and improvement of a class of hyperchaos based image encryption algorithms. Acta Physica Sin. 61(12), 76–87 (2012)
Funding
This work was supported by the National Key Research and Development Program of China (No. 2016YFB0800401), and the National Natural Science Foundation of China (Nos. 61771176, 61401134, 61532020, 61671161).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Rights and permissions
About this article
Cite this article
Lin, Z., Wang, G., Wang, X. et al. Security performance analysis of a chaotic stream cipher. Nonlinear Dyn 94, 1003–1017 (2018). https://doi.org/10.1007/s11071-018-4406-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-018-4406-8