Abstract
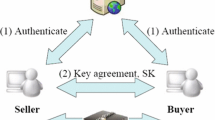
Three-party password-authenticated key exchange (3PAKE) protocol allows two users to establish a secure session key over an insecure communication channel with the help of a trusted server. Recently, Farash and Attari proposed a chaotic maps-based 3PAKE protocol without using server’s public key, smart card and symmetric cryptosystems and claimed its security by providing well-organized security proof. Unfortunately, in this paper, we demonstrate that their protocol cannot resist impersonation attack and off-line password guessing attack. To overcome their security weaknesses, we propose an improved chaotic maps-based 3PAKE protocol with the same advantages. Further, we apply the pi calculus-based formal verification tool ProVerif to show that our 3PAKE protocol achieves authentication and security and show that our protocol is more efficient than Farash and Attari’s protocol in terms of computation and communication costs.
Similar content being viewed by others
References
Baptista, M.S.: Cryptography with chaos. Phys. Lett. A 240(1–2), 50–54 (1998)
Özkaynak, F., Yavuz, S.: Designing chaotic S-boxes based on time-delay chaotic system. Nonlinear Dyn. 74(3), 551–557 (2013)
Hussain, I., Shah, T., Gondal, M., Mahmood, H.: An efficient approach for the construction of LFT S-boxes using chaotic logistic map. Nonlinear Dyn. 71(1–2), 133–140 (2013)
Hussain, I., Shah, T., Gondal, M.: A novel approach for designing substitution-boxes based on nonlinear chaotic algorithm. Nonlinear Dyn. 70(3), 1791–1794 (2012)
Behnia, S., Akhshani, A., Ahadpour, S., Mahmodi, H., Akhavan, A.: A fast chaotic encryption scheme based on piecewise nonlinear chaotic maps. Phys. Lett. A 366(4–5), 391–396 (2007)
Khan, M., Shah, T., Mahmood, H., Gondal, M.: An efficient method for the construction of block cipher with multi-chaotic systems. Nonlinear Dyn. 71(3), 489–492 (2013)
Anees, A., Siddiqui, A.M., Ahmed, F.: Chaotic substitution for highly autocorrelated data in encryption algorithm. Commun. Nonlinear Sci. Numer. Simul. 19(9), 3106–3118 (2014)
Huang, X., Ye, G.: An efficient self-adaptive model for chaotic image encryption algorithm. Commun. Nonlinear Sci. Numer. Simul. 19(12), 4094–4104 (2014)
Hussain, I., Gondal, M.A.: An extended image encryption using chaotic coupled map and S-box transformation. Nonlinear Dyn. 76(2), 1355–1363 (2014)
Chen, J.X., Zhu, Z.L., Fu, C., Yu, H.: A fast image encryption scheme with a novel pixel swapping-based confusion approach. Nonlinear Dyn. 77(4), 1191–1207 (2014)
Chain, K., Kuo, W.C.: A new digital signature scheme based on chaotic maps. Nonlinear Dyn. 74(4), 1003–1012 (2013)
Deng, S., Li, Y., Xiao, D.: Analysis and improvement of a chaos-based Hash function construction. Commun. Nonlinear Sci. Numer. Simul. 15(5), 1338–1347 (2010)
Jabbari, A., Bagherzadeh, J.: A revised key agreement protocol based on chaotic maps. Nonlinear Dyn. (2014). doi:10.1007/s11071-014-1467-1
Farash, M.S., Attari, m A.: Cryptanalysis and improvement of a chaotic map-based key agreement protocol using Chebyshev sequence membership testing. Nonlinear Dyn. 76(2), 1203–1213 (2014)
Lee, C.C., Lou, D.C., Li, C.T., Hsu, C.W.: An extended chaotic-maps-based protocol with key agreement for multiserver environments. Nonlinear Dyn. 76(1), 853–866 (2014)
Islam, S.H.: Provably secure dynamic identity-based three-factor password authentication scheme using extended chaotic maps. Nonlinear Dyn. (2014). doi:10.1007/s11071-014-1584-x
Xiao, D., Liao, X., Deng, S.: Using time-stamp to improve the security of a chaotic maps-based key agreement protocol. Inf. Sci. 178(6), 1598–1602 (2008)
Han, S., Chang, E.: Chaotic map based key agreement with/out clock synchronization. Chaos Solitons Fractals 39(3), 1283–1289 (2009)
Guo, X., Zhang, J.: Secure group key agreement protocol based on chaotic Hash. Inf. Sci. 180(20), 4069–4074 (2010)
He, D., Chen, Y., Chen, Y.: Cryptanalysis and improvement of an extended chaotic maps-based key agreement protocol. Nonlinear Dyn. 69(3), 1149–1157 (2012)
Gong, P., Li, P., Shi, W.: A secure chaotic maps-based key agreement protocol without using smart cards. Nonlinear Dyn. 70(4), 2401–2406 (2012)
Niu, Y., Wang, X.: An anonymous key agreement protocol based on chaotic maps. Commun. Nonlinear Sci. Numer. Simulat. 16(4), 1986–92 (2011)
Xue, K., Hong, P.: Security improvement on an anonymous key agreement protocol based on chaotic maps. Commun. Nonlinear Sci. Numer. Simul. 17(7), 2969–2977 (2012)
Yoon, E.: Efficiency and security problems of anonymous key agreement protocol based on chaotic maps. Commun. Nonlinear Sci. Numer. Simul. 17(7), 2735–2740 (2012)
Tan, Z.: A chaotic maps-based authenticated key agreement protocol with strong anonymity. Nonlinear Dyn. 72(1–2), 311–320 (2013)
Lee, C., Hsu, C.: A secure biometric-based remote user authentication with key agreement scheme using extended chaotic maps. Nonlinear Dyn. 71(1–2), 201–211 (2013)
Guo, C., Chang, C.C.: Chaotic maps-based password-authenticated key agreement using smart cards. Commun. Nonlinear Sci. Numer. Simul. 18(6), 1433–1440 (2013)
Lin, H.Y.: Improved chaotic maps-based password-authenticated key agreement using smart cards. Commun. Nonlinear Sci. Numer. Simul. 20(2), 482–488 (2015)
Yau, W.C., Phan, R.C.W.: Cryptanalysis of a chaotic map-based password-authenticated key agreement protocol using smart cards. Nonlinear Dyn. (2014). doi:10.1007/s11071-014-1704-7
Xie, Q., Dong, N., Tan, X., Wong, D.S., Wang, G.L.: Improvement of a three-party password-based key exchange protocol with formal verification. Inf. Technol. Control 42(3), 231–237 (2013)
Wang, X., Zhao, J.: An improved key agreement protocol based on chaos. Commun. Nonlinear Sci. Numer. Simul. 15(12), 4052–4057 (2010)
Yoon, E., Jeon, I.: An efficient and secure Diffie–Hellman key agreement protocol based on Chebyshev chaotic map. Commun. Nonlinear Sci. Numer. Simul. 16(6), 2383–2389 (2011)
Lai, H., Xiao, J., Li, L., Yang, Y.: Applying semigroup property of enhanced Chebyshev polynomials to anonymous authentication protocol. Math. Probl. Eng. (2012). doi:10.1155/2012/454823
Zhao, F., Gong, P., Li, S., Li, M., Li, P.: Cryptanalysis and improvement of a three-party key agreement protocol using enhanced Chebyshev polynomials. Nonlinear Dyn. 74(1–2), 419–427 (2013)
Lee, C., Li, C., Hsu, C.: A three-party password-based authenticated key exchange protocol with user anonymity using extended chaotic maps. Nonlinear Dyn. 73(1–2), 125–132 (2013)
Hu, X., Zhang, Z.F.: Cryptanalysis and enhancement of a chaotic maps-based three-party password authenticated key exchange protocol. Nonlinear Dyn. (2014). doi:10.1007/s11071-014-1515-x
Xie, Q., Hu, B., Dong, N., Wong, D.S.: Anonymous three-party password-authenticated key exchange scheme for telecare medical information systems. PLoS One 9(7), e102747 (2014). doi:10.1371/journal.pone.0102747
Xie, Q., Zhao, J., Yu, X.: Chaotic maps-based three-party password-authenticated key agreement scheme. Nonlinear Dyn. 74(4), 1021–1027 (2013)
Lai, H., Orgun, M.A., Xiao, J.H., Pieprzyk, J., Xue, L.Y., Yang, Y.X.: Provably secure three-party key agreement protocol using Chebyshev chaotic maps in the standard model. Nonlinear Dyn. 77(4), 1427–1439 (2014)
Farash, M.S., Attari, M.A.: An efficient and provably secure three-party password-based authenticated key exchange protocol based on Chebyshev chaotic maps. Nonlinear Dyn. 77(1–2), 399–411 (2014)
Abadi, M., Fournet, C.: Mobile values, new names, and secure communication. In: Proceedings of the 28th ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, pp. 104–115. New York, USA (2001)
Abadi, M., Blanchet, B., Lundh, H.C.: Models and proofs of protocol security: a progress report. In: 21st International Conference on Computer Aided Verification, , pp. 35–49. Grenoble, France (2009)
Dolev, D., Yao, A.C.: On the security of public key protocols. IEEE Trans. Inf. Theory 29(2), 198–208 (1983)
Acknowledgments
This research was supported by Natural Science Foundations of Zhejiang Province (Nos. LZ12F02005, LY12F02006), the Major State Basic Research Development (973) Program of China (No. 2013CB834205), and National Natural Science Foundation of China (No. 61070153).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Xie, Q., Hu, B. & Wu, T. Improvement of a chaotic maps-based three-party password-authenticated key exchange protocol without using server’s public key and smart card. Nonlinear Dyn 79, 2345–2358 (2015). https://doi.org/10.1007/s11071-014-1816-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-014-1816-0