Abstract
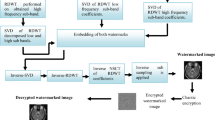
Telemedicine is the field that uses medical images for diagnosing various diseases. The transmitting and storing of medical images via the cloud-based network must meet several stringent criteria, including confidentiality, validity, and security, and are viewed as very sensitive, irrespective of the image processing context. Medical image copyright protection has been essential since little alterations can even put the lives of patients in danger. Hence numerous significant watermarking methods need to be developed. Watermarking conceals sensitive data by embedding it in a harmless medium, such as a cover. The challenging issue of quick and extremely safe image encryption can be solved more effectively with chaos-based cryptography. Thus the image is encrypted by using enhanced chaos with the Fruit Fly Optimization Algorithm (FFOA). The work proposes an efficient medical image watermarking approach using the Two-level Stationary Wavelet Transform (SWT) and Singular Value Decomposition (SVD) technique on chaotic encrypted medical images. Finally, the proposed method is compared with existing methods to demonstrate higher performance. To check robustness and imperceptibility results, the work is examined under various attacks and produces good results in Peak Signal-to-Noise Ratio (PSNR) and Normalized Cross Correlation (NCC) measures. For different kinds of medical images, the PSNR of the suggested methodology is greater than 40 dB, and NCC values are close to 1 illustrating the technique's superior efficacy.











Similar content being viewed by others
Data availability
The datasets created and/or analyzed during the current work can be provided by the corresponding author upon request.
References
Krishnagopal S, Pratap S, Prakash B (2015) Image encryption and steganography using chaotic maps with double key protection. Adv Intell Syst Comput 336:67–78. https://doi.org/10.1007/978-81-322-2220-0_6
Charan GS, Nithin Kumar SSV, Karthikeyan B, Vaithiyanathan V, Divya Lakshmi K (2015) A novel LSB based image steganography with multi-level encryption. International Conference on Innovations in Information, Embedded and Communication Systems (ICIIECS), Coimbatore, India pp 1–5. https://doi.org/10.1109/ICIIECS.2015.7192867
Hamid N, Yahya A, Ahmad RB, Al-Qershi OM (2012) Image steganography techniques: an overview. Int J Comput Sci Sec (IJCSS) 6(3):168–187
Dahiya M, Kumar R (2018) A literature survey on various image encryption & steganography techniques. International Conference on Secure Cyber Computing and Communication (ICSCCC), Jalandhar, India, pp 310–314. https://doi.org/10.1109/ICSCCC.2018.8703368
Singh KU, Abu-Hamatta HS, Kumar A, Singhal A, Rashid M, Bashir AK (2022) Secure watermarking scheme for color DICOM images in telemedicine applications. Comput Mater Continua 70(2):2525–2542
Lei X, Du M, Xu J, Tan Y (2014) Chaotic fruit fly optimization algorithm. In: Tan Y, Shi Y, Coello CAC (eds) Advances in swarm intelligence. ICSI 2014. Lecture notes in computer science, vol 8794. Springer, Cham. https://doi.org/10.1007/978-3-319-11857-4_9
Boussif M, Aloui N, Cherif A (2020) DICOM imaging watermarking for hiding medical reports. Med Biol Eng Comput 58:2905–2918. https://doi.org/10.1007/s11517-020-02269-8
Awasthi D, Srivastava VK (2023) Robust, invisible, and optimized watermarking of DICOM image using Schur decomposition, LWT-DCT-SVD, and its authentication using SURF. Multimedia Tools and Applications 82(11):16555–16589. https://doi.org/10.1007/s11042-022-14002-8
Pulgam ND, Shinde SK (2022) Robust digital watermarking using pixel color correlation and chaotic encryption for medical image protection. Int J Intell Syst App Eng 10(4):29-38.1
Alhussan AA, Abdallah HA, Alsodairi S, Ateya AA (2023) Hybrid watermarking and encryption techniques for securing medical images. Comput Syst Sci Eng 46(1):403–416. https://doi.org/10.3390/electronics12071554
Singh KU, Aljrees T, Kumar A, Singh T (2023) Secure NIfTI image authentication scheme for modern healthcare system. Appl Sci 13(9):5308. https://doi.org/10.3390/app13095308
Sasikaladevi N, Geetha K, Revathi A (2022) EMOTE–Multilayered encryption system for protecting medical images based on binary curves. J King Saud Univ-Comput Inf Sci 34(3):676–686. https://doi.org/10.1016/j.jksuci.2019.01.014
Elhadad A, Ghareeb A, Abbas S (2021) A blind and high-capacity data hiding of DICOM medical images based on fuzzification concepts. Alex Eng J 60(2):2471–2482. https://doi.org/10.1016/j.aej.2020.12.050
Fang Y, Liu J, Li J, Cheng J, Hu J, Yi D, Bhatti UA (2022) Robust zero-watermarking algorithm for medical images based on SIFT and Bandelet-DCT. Multimed Tools App 81(12):16863–16879. https://doi.org/10.1007/s11042-022-12592-x
Sajeer M, Mishra A (2023) A robust and secured fusion based hybrid medical image watermarking approach using RDWT-DWT-MSVD with Hyperchaotic system-Fibonacci Q Matrix encryption. Multimed Tools Appl 82:37479–37501. https://doi.org/10.1007/s11042-023-15001-z
Liu Z, Li J, Ai Y, Zheng Y, Liu J (2022) A robust encryption watermarking algorithm for medical images based on ridgelet-DCT and THM double chaos. J Cloud Comput 11(1):1–20. https://doi.org/10.1186/s13677-022-00331-4
Chen J, Liao X, Wang W, Qian Z, Qin Z, Wang Y (2023) SNIS: a signal noise separation-based network for post-processed image forgery detection. IEEE Trans Circuits Syst Video Technol 33(2):935–951. https://doi.org/10.1109/TCSVT.2022.3204753
Liao X, Wang Y, Wang T, Juan Hu, Xiaoshuai Wu (2023) FAMM: facial muscle motions for detecting compressed deepfake videos over social networks. IEEE Trans Circuits Syst Video Technol 33(12):7236–7251. https://doi.org/10.1109/TCSVT.2023.3278310
Tan J, Liao X, Liu J, Cao Y, Jiang H (2022) Channel attention image steganography with generative adversarial networks. IEEE Trans Netw Sci Eng 9(2):888–903. https://doi.org/10.1109/TNSE.2021.3139671
Jiao G, Li L, Zou Y (2019) Improved security for android system based on multi-chaotic maps using a novel image encryption algorithm. Int J Performability Engineering 15(6):1692–1701. https://doi.org/10.23940/ijpe.19.06.p20.16921701
Alzubi JA, Alzubi OA, Suseendran G, Akila D (2019) +A Novel chaotic map encryption methodology for image cryptography and secret communication with steganography. Int J Recent Technol Eng 8(1C2):1122–1128
Ghebleh M, Kanso A (2014) A robust chaotic algorithm for digital image steganography. Commun Nonlinear Sci Numer Simul 19(6):1898–1907. https://doi.org/10.1016/j.cnsns.2013.10.014
Xing B, Gao WJ, Xing B, Gao WJ (2014) Fruit fly optimization algorithm. Innovative computational intelligence: a rough guide to 134 clever algorithms, pp 167–170. https://doi.org/10.1007/978-3-319-03404-1_11
Saini J, Harsh V (2013) A hybrid approach for image security by combining encryption and steganography. IEEE 2nd International Conference on Image Information Processing. IEEE ICIIP 2013:607–611. https://doi.org/10.1109/ICIIP.2013.6707665
Tripathi D, Sharma S (2016) A robust 3-SWT multiple image steganography and contrast enhancement technique. Proc Int Conf Inventive Comput Technol ICICT 2016:1. https://doi.org/10.1109/INVENTIVE.2016.7823256
Funding
No funding was obtained for this manuscript's preparation.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interests/Competing interests
The authors have absolutely no financial or proprietary interests in any of the content covered within. This ensures that the information received is unbiased and free from any potential conflicts of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
R, A., C, M. Medical image security by crypto watermarking using enhanced chaos and fruit fly optimization algorithm with SWT and SVD. Multimed Tools Appl (2024). https://doi.org/10.1007/s11042-024-19019-9
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11042-024-19019-9