Abstract
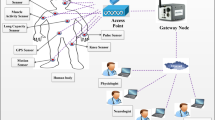
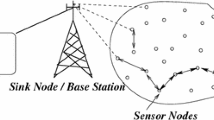
Wireless Sensor Networks (WSNs) play a significant role in the health care industry in this digitised world. This technology is used to monitor and store the health-related data for patients. As a result, if such data is not kept secure, it can pose a serious threat to the patient’s life. Maintaining the anonymity of such data is an equally important task. As WSNs use an open channel to transfer data between sensor nodes, users and gateway, they are vulnerable to attackers. A user authentication strategy for remote healthcare applications has been recently developed by Soni et al. However, it has been noted in this work that this user authentication approach is not secure against user impersonation attack and offline password-guessing attack. Additionally, to overcome the shortcomings of the Soni et al.’s protocol, an effective user authentication protocol for wireless healthcare sensor networks has been put forth. The formal security verification of the proposed protocol is carried out using the ProVerif tool and the formal verification of mutual authentication is demonstrated using BAN logic. Its performance in terms of cost associated with communication, storage and computation along with its security aspects is compared to those of the other similar schemes. From such a comparison, it is evident that the proposed protocol is more secure.










Similar content being viewed by others
Availability of data and materials
Not applicable.
References
Amin R, Islam SH, Biswas G, Khan MK, Leng L, Kumar N (2016) Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput Netw 101:42–62
Berini ADE, Ferrag MA, Farou B, Seridi H (2023) Hcala: hyperelliptic curve-based anonymous lightweight authentication scheme for internet of drones. Pervasive Mob Comput 92:101798
Burrows M, Abadi M, Needham RM (1989) A logic of authentication. Proc R Soc Lond A. Math Phys Sci 426(1871):233–271
Challa S, Das AK, Odelu V, Kumar N, Kumari S, Khan MK, Vasilakos AV (2018) An efficient ECC-based provably secure three-factor user authentication and key agreement protocol for wireless healthcare sensor networks. Comput Electr Eng 69:534–554
Chen TH, Shih WK (2010) A robust mutual authentication protocol for wireless sensor networks. ETRI J 32(5):704–712
Das AK, Sharma P, Chatterjee S, Sing JK (2012) A dynamic password-based user authentication scheme for hierarchical wireless sensor networks. J Netw Comput Appl 35(5):1646–1656
Das ML (2009) Two-factor user authentication in wireless sensor networks. IEEE Trans Wirel Commun 8(3):1086–1090
Dolev D, Yao A (1983) On the security of public key protocols. IEEE Trans Inf Theory 29(2):198–208
Farash MS, Turkanović M, Kumari S, Hölbl M (2016) An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the internet of things environment. Ad Hoc Netw 36:152–176
Gope P, Hwang T (2016) A realistic lightweight anonymous authentication protocol for securing real-time application data access in wireless sensor networks. IEEE Trans Ind Electron 63(11):7124–7132
He D, Kumar N, Chen J, Lee CC, Chilamkurti N, Yeo SS (2015) Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimedia Systems 21(1):49–60
Jiang Q, Ma J, Lu X, Tian Y (2015) An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks. Peer Peer Netw Appl 8(6):1070–1081
Kaur D, Kumar D (2021) Cryptanalysis and improvement of a two-factor user authentication scheme for smart home. J Inf Secur Appl 58:102787
Kaur D, Kumar D, Saini KK, Grover HS (2019) An improved user authentication protocol for wireless sensor networks. Trans Emerg Telecommun Technol 30(10):e3745
Kaur D, Saini KK, Kumar D (2022) Cryptanalysis and enhancement of an authentication protocol for secure multimedia communications in IoT-enabled wireless sensor networks. Multimedia Tools Appl 81(27):39367–39385
Khan MK, Alghathbar K (2010) Cryptanalysis and security improvements of a two-factor user authentication in wireless sensor networks. Sensors 10(3):2450–2459
Kim K, Ryu J, Lee Y, Won D (2023) An improved lightweight user authentication scheme for the internet of medical things. Sensors 23(3):1122
Kumar D, Grover HS, Kaur D, Verma A, Saini KK, Kumar B (2021) An efficient anonymous user authentication and key agreement protocol for wireless sensor networks. Int J Commun Syst 34(5):e4724
Kumar P, Lee SG, Lee HJ (2012) E-sap: efficient-strong authentication protocol for healthcare applications using wireless medical sensor networks. Sensors 12(2):1625–1647
Leng L, Teoh ABJ (2015) Alignment-free row-co-occurrence cancelable palmprint fuzzy vault. Pattern Recognit 48(7):2290–2303
Leng L, Teoh ABJ, Li M, Khan MK (2014) A remote cancelable palmprint authentication protocol based on multi-directional two-dimensional PalmPhasor-fusion. Secur Commun Netw 7(11):1860–1871
Leng L, Zhang J (2011) Dual-key-binding cancelable palmprint cryptosystem for palmprint protection and information security. J Netw Comput Appl 34(6):1979–1989
Li J, Zhang W, Kumari S, Choo KKR, Hogrefe D (2018) Security analysis and improvement of a mutual authentication and key agreement solution for wireless sensor networks using chaotic maps. Trans Emerg Telecommun Techn 29(6):e3295
Li W, Li B, Zhao Y, Wang P, Wei F (2018) Cryptanalysis and security enhancement of three authentication schemes in wireless sensor networks. Wirel Commun Mob Comput 2018
Liu CH, Chung YF (2017) Secure user authentication scheme for wireless healthcare sensor networks. Comput Electr Eng 59:250–261
Kumar D (2023) Cryptanalysis and improvement of an authentication protocol for wireless sensor networks. Trans Emerg Telecommun Technol e4747
Shuai M, Yu N, Wang H, Xiong L (2019) Anonymous authentication scheme for smart home environment with provable security. Comput Secur 86:132–146
Soni P, Pal AK, Islam SH (2019) An improved three-factor authentication scheme for patient monitoring using WSN in remote health-care system. Comput Methods Prog Biomed 182:105054
Spreitzer R, Moonsamy V, Korak T, Mangard S (2017) Systematic classification of side-channel attacks: a case study for mobile devices. IEEE Commun Surv Tutor 20(1):465–488
Sureshkumar V, Amin R, Vijaykumar V, Sekar SR (2019) Robust secure communication protocol for smart healthcare system with FPGA implementation. Futur Gener Comput Syst 100:938–951
Turkanović M, Brumen B, Hölbl M (2014) A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the internet of things notion. Ad Hoc Netw 20:96–112
Turkanovic M, Holbl M (2013) An improved dynamic password-based user authentication scheme for hierarchical wireless sensor networks. Elektronika ir Elektrotechnika 19(6):109–116
Wang D, Wang P (2016) Two birds with one stone: two-factor authentication with security beyond conventional bound. IEEE Trans Dependable Secure Comput 15(4):708–722
Wu F, Li X, Sangaiah AK, Xu L, Kumari S, Wu L, Shen J (2018) A lightweight and robust two-factor authentication scheme for personalized healthcare systems using wireless medical sensor networks. Futur Gener Comput Syst 82:727–737
Xie Q, Tang Z, Chen K (2017) Cryptanalysis and improvement on anonymous three-factor authentication scheme for mobile networks. Comput Electr Eng 59:218–230
Xu S, Wang X (2013) A new user authentication scheme for hierarchical wireless sensor networks. Int Rev Comput Softw 8(6):197–203
Xue K, Ma C, Hong P, Ding R (2013) A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J Netw Comput Appl 36(1):316–323
Funding
Not applicable.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Ethical Approval and Consent to participate
Not applicable.
Competing interests
The authors have no relevant financial or non-financial interests to disclose.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Saini, K.K., Kaur, D., Kumar, D. et al. An efficient three-factor authentication protocol for wireless healthcare sensor networks. Multimed Tools Appl (2024). https://doi.org/10.1007/s11042-024-18114-1
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11042-024-18114-1