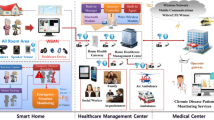
Abstract
E-health has emerged as a key research area as long as the advent of the Internet of Things (IoT). Maintaining patients' privacy seems complex because patient data is so sensitive. In medical uses, patient health information is often kept in the cloud, which bounds the user’s ability to fully control their data. To overcome the issues of privacy and security, medical data is collected from IoT sensors embedded in patients to the Personal Digital Assistant (PDA) for further processing. A hybrid encryption algorithm is used to ensure data security during transmission from the gathered medical-related data. The encrypted report is deposited in the cloud for later retrieval with appropriate access controls and encryption mechanisms in place. The use of blockchain for transmitting encrypted data further enhances the transmission of data securely and reduces the risk of data breaches. The generation of encryption and decryption keys using a hybrid deep learning model (LSTM and CNN) ensures the uniqueness and robustness of the keys. The selection of the optimal key using the Self-Improved Lion Optimization Algorithm (SI-LA) ensures the efficiency and effectiveness of the encryption and decryption process. Moreover, the execution of the model is equated with the existing technology; therefore, the proposed model is ensured as a more effective technique than the existing technique in terms of performance metrics.














Similar content being viewed by others
Data Availability
The UCI Heart Disease Data utilized in this research is publicly available and can be accessed through the UCI Machine Learning Repository (https://archive.ics.uci.edu/ml/datasets/Heart+Disease). The dataset provides valuable insights into various cardiovascular parameters and has been instrumental in our study on ensuring the privacy and security of IoT-medical data.
References
Sleeman KE, De Brito M, Etkind S, Nkhoma K, Guo P, Higginson IJ, Gomes B, Harding R (2019) The escalating global burden of serious health-related suffering: projections to 2060 by world regions, age groups, and health conditions. Lancet Glob Health 7(7):e883–e892
Chen Y, Ding S, Xu Z, Zheng H, Yang S (2019) Blockchain-based medical records secure storage and medical service framework. J Med Syst 43:1–9
Fan K, Jiang W, Li H, Yang Y (2018) Lightweight RFID protocol for medical privacy protection in IoT. IEEE Trans Industr Inf 14(4):1656–1665
Onesimu JA, Karthikeyan J, Sei Y (2021) An efficient clustering-based anonymization scheme for privacy-preserving data collection in IoT based healthcare services. Peer Peer Netw Appl 14:1629–1649
Saha R, Kumar G, Rai MK, Thomas R, Lim SJ (2019) Privacy ensured ${e} $-healthcare for fog-enhanced IoT based applications. IEEE Access 7:44536–44543
Luo E, Bhuiyan MZA, Wang G, Rahman MA, Wu J, Atiquzzaman M (2018) Privacyprotector: privacy-protected patient data collection in IoT-based healthcare systems. IEEE Commun Mag 56(2):163–168
Renuka K, Kumari S, Li X (2019) Design of a secure three-factor authentication scheme for smart healthcare. J Med Syst 43:1–12
Prince PB, Lovesum SJ (2020) Privacy enforced access control model for secured data handling in cloud-based pervasive health care system. SN Comput Sci 1(5):239
Chenthara S, Ahmed K, Wang H, Whittaker F (2019) Security and privacy-preserving challenges of e-health solutions in cloud computing. IEEE Access 7:74361–74382
Vijayalakshmi AV, Arockiam L (2018) ARO_EDGE: a technique to ensure data security in Internet of Things (IoT). Asian J Comput Sci Technol 7(2):52–56
Akkaoui R, Hei X, Cheng W (2020) EdgeMediChain: a hybrid edge blockchain-based framework for health data exchange. IEEE Access 8:113467–113486
Yaacoub JPA, Noura M, Noura HN, Salman O, Yaacoub E, Couturier R, Chehab A (2020) Securing internet of medical things systems: limitations, issues and recommendations. Futur Gener Comput Syst 105:581–606
Sengan S, Khalaf OI, Sharma DK, Hamad AA (2022) Secured and privacy-based IDS for healthcare systems on E-medical data using machine learning approach. Int J Reliab Qual E-Healthc (IJRQEH) 11(3):1–11
Baban AB, Hameed SA (2023) Securing a web-based hospital management system using a combination of AES and HMAC 93–99
Wahab F, Zhao Y, Javeed D, Al-Adhaileh MH, Almaaytah SA, Khan W, Saeed MS, Kumar Shah R (2022) An AI-driven hybrid framework for intrusion detection in IoT-enabled E-health. Comput Intell Neurosci 2022:1–11
El Zouka HA, Hosni MM (2021) Secure IoT communications for smart healthcare monitoring system. Internet Things 13:100036
Mohiyuddin A, Javed AR, Chakraborty C, Rizwan M, Shabbir M, Nebhen J (2022) Secure cloud storage for medical IoT data using adaptive neuro-fuzzy inference system. Int J Fuzzy Syst 24(2):1203–1215
Dwivedi AD, Srivastava G, Dhar S, Singh R (2019) A decentralized privacy-preserving healthcare blockchain for IoT. Sensors 19(2):326
Stamatellis C, Papadopoulos P, Pitropakis N, Katsikas S, Buchanan WJ (2020) A privacy-preserving healthcare framework using hyperledger fabric. Sensors 20(22):6587
Almaiah MA, Hajjej F, Ali A, Pasha MF, Almomani O (2022) A novel hybrid trustworthy decentralized authentication and data preservation model for digital healthcare IoT based CPS. Sensors 22(4):1448
Ali A, Rahim HA, Pasha MF, Dowsley R, Masud M, Ali J, Baz M (2021) Security, privacy, and reliability in digital healthcare systems using blockchain. Electronics 10(16):2034
Ngabo D, Wang D, Iwendi C, Anajemba JH, Ajao LA, Biamba C (2021) Blockchain-based security mechanism for the medical data at fog computing architecture of internet of things. Electronics 10(17):2110
Jyotheeswari P, Jeyanthi N (2020) Hybrid encryption model for managing the data security in medical internet of things. Int J Internet Protoc Technol 13(1):25–31
Bi H, Liu J, Kato N (2021) Deep learning-based privacy preservation and data analytics for IoT enabled healthcare. IEEE Trans Industr Inf 18(7):4798–4807
Din IU, Almogren A, Guizani M, Zuair M (2019) A decade of internet of things: analysis in the light of healthcare applications. IEEE Access 7:89967–89979
Hssayni EH, Joudar NE, Ettaouil M (2022) A deep learning framework for time series classification using normal cloud representation and convolutional neural network optimization. Comput Intell 38(6):2056–2074
Joudar NE, Ettaouil M (2022) An adaptive drop method for deep neural networks regularization: estimation of DropConnect hyperparameter using generalization gap. Knowl-Based Syst 253:109567
Hssayni EH, Joudar NE, Ettaouil M (2022) Localization and reduction of redundancy in CNN using L 1-sparsity induction. J Ambient Intell Humaniz Comput:14(10):13715–13727
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing Interests
There isn't any competing interests associated with the research presented in this article, “Ensuring the Privacy and Security of IoT-Medical Data: A Hybrid Deep Learning-Based Encryption and Blockchain-Enabled Transmission”. No financial or non-financial conflicts of interest exist that could influence the research, analysis, or interpretation of the findings. The focus of this work is solely on advancing methodologies to enhance the privacy and security of medical data in the context of the Internet of Things.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Ranjan, A.K., Kumar, P. Ensuring the privacy and security of IoT-medical data: a hybrid deep learning-based encryption and blockchain-enabled transmission. Multimed Tools Appl (2024). https://doi.org/10.1007/s11042-023-18043-5
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11042-023-18043-5