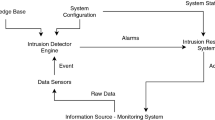
Abstract
The proliferation of wireless networks as a primary data transmission channel has brought about a surge in data volume but also raised security threats and privacy concerns. Intrusion Detection Systems (IDS) have proven effective in safeguarding data transmission, yet they struggle to detect minor or rare attacks that mimic normal traffic. To address this challenge, we propose a novel two-layer classification model integrating K-nearest neighbor (KNN) and support vector machines (SVMs). In the first layer, KNN classifies data into Normal, Major, and Minor Attack categories, while the second layer further distinguishes Major Attacks into DoS or Probe and Minor Attacks into U2R or R2. Our framework incorporates Common Correlated Feature Selection (CCFS) to optimize feature discrimination, partitioning training data into three groups. Furthermore, we explore data preprocessing techniques to enhance data interpretation and maintain statistical normalcy in traffic connection features. Our experimental analysis utilizes the NSL-KDD dataset, demonstrating that our approach significantly improves detection rates, particularly for Minor Attacks, achieving a remarkable 92.33% detection rate for U2R and 91.33% for R2L attacks. This represents a substantial 10% enhancement over existing methods, outperforming Multi-Layer Perceptron (MLP) by 13.23%, Random Forest (RF) by 10.11%, J48- Decision Tree (DT) by 9.23%, and Naïve Bayes (NB) by 9.42% and 8.17% in terms of detection rates. These results underscore the effectiveness of our approach in enhancing intrusion detection performance.






Similar content being viewed by others
Data availability
Data sharing not applicable to this article as no datasets were generated or analyzed during the current study.
References
Eddermoug N, Mansour A, Sadik, M, Sabir E and Azmi M (2019) Klm-PPSA: Klm-based profiling and preventing security attacks for cloud environments. In 2019 International Conference on Wireless Networks and Mobile Communications (WINCOM). IEEE 1–7
Eddermoug N, Mansour A, Sadik M, Sabir E, Azmi M (2021) KLM-based profiling and preventing security attacks for cloud computing: A comparative study. In 2021 28th International Conference on Telecommunications (ICT). IEEE 1–6
Abusitta A, Bellaiche M, Dagenais M (2018) A trust-based game theoretical model for cooperative intrusion detection in multi-cloud environments. In 2018 21st Conference on Innovation in Clouds, Internet and Networks and Workshops (ICIN). IEEE 1–8
Cirillo S, Desiato D, Scalera M, Solimando G (2023) A visual privacy tool to help users in preserving social network data
Resende PAA, Drummond AC (2019) A survey of random forest based methods for intrusion detection systems. ACM Comput Surv 51(3):1–36
Hasson and Timothy. Bad BOT report 2021. Available: https://www.imperva.com/blog/bad-bot-report-2021-the-pandemic-of-the-internet/
Aburomman AA, Reaz MBI (2017) A survey of intrusion detection systems based on ensemble and hybrid classifiers. Comput Secur 65:135–152
Pacheco F, Exposito E, Gineste M, Baudoin C, Aguilar J (2019) Towards the deployment of machine learning solutions in network traffic classification: a systematic survey. IEEE Commun Surveys Tuts 21(2):1988–2014
I. A. N. Authority. Protocol ASSIGNMENTS. Available: https://www.iana.org/protocols
Erlacher F, Dressler F (2022) On high-speed flow-based intrusion detection using snort-compatible signatures. IEEE Trans Dependable Secure Comput 19(1):495–506
Ahmad Z, Khan AS, Shiang CW, Abdullah J, Ahmad F (2021) Network intrusion detection system: a systematic study of machine learning and deep learning approaches. Trans Emerg Telecommun Technol 32(1):e4150
Krishnan N, Salim A (2018) Machine learning based intrusion detection for virtualized infrastructures. In 2018 International CET Conference on Control, Communication, and Computing (IC4). IEEE 366–371
Sharma S, Zavarsky P, Butakov S (2020) Machine learning based intrusion detection system for web-based attacks. In 2020 IEEE 6th Intl Conference on Big Data Security on Cloud (BigDataSecurity), IEEE Intl Conference on High Performance and Smart Computing,(HPSC) and IEEE Intl Conference on Intelligent Data and Security (IDS). IEEE 227–230
Ahmad I, Basheri M, Iqbal MJ, Raheem A (2018) Performance comparison of support vector machine, random forest, and extreme learning machine for intrusion detection. IEEE Access 6:33789–33795
Vinayakumar R, Alazab M, Soman K, Poornachandran P, Al-Nemrat A, Venkatraman S (2019) Deep learning approach for intelligent intrusion detection system. IEEE Access 7:41525–41550
Li W, Yi P, Wu Y, Pan L, Li J (2014) A new intrusion detection system based on KNN classification algorithm in wireless sensor network. J Electr Comput Eng 2014:1–8
Zhang B, Liu Z, Jia Y, Ren J, Zhao X (2018) Network intrusion detection method based on PCA and Bayes algorithm. Secur Commun Netw 2018:1–11
Zhang Y, Yang Q, Lambotharan S, Kyriakopoulos K, Ghafir I, AsSadhan B (2019) Anomaly-based network intrusion detection using SVM. In 2019 11th International conference on wireless communications and signal processing (WCSP). IEEE 1–6
Sahu S, Mehtre BM (2015) Network intrusion detection system using J48 Decision Tree. In 2015 International Conference on Advances in Computing, Communications and Informatics (ICACCI). IEEE 2023–2026
Fouladi RF, Kayatas CE, Anarim E (2016) Frequency based DDoS attack detection approach using naive Bayes classification. In 2016 39th International Conference on Telecommunications and Signal Processing (TSP). IEEE 104–107
Li M (2017) Application of CART decision tree combined with PCA algorithm in intrusion detection. In 2017 8th IEEE international conference on software engineering and service science (ICSESS). IEEE 38–41
Sukumar JA, Pranav I, Neetish MM, Narayanan J (2018) Network intrusion detection using improved genetic k-means algorithm. In 2018 international conference on advances in computing, communications and informatics (ICACCI). IEEE 2441–2446
Khalid S, Khalil T, Nasreen S (2014) A survey of feature selection and feature extraction techniques in machine learning. In 2014 science and information conference. IEEE 372–378
Thaseen IS, Kumar CA (2016) Intrusion detection model using fusion of chi-square feature selection and multi class SVM. J King Saud Univ-Comput Inf Sci 29(4):462–472
Yao H, Wang Q, Wang L, Zhang P, Li M, Liu Y (2019) An intrusion detection framework based on hybrid multi-level data mining. Int J Parallel Program 47(4):740–758
Li G, Yan Z, Fu Y, Chen H (2018) Data fusion for network intrusion detection: a review. Secur Commun Netw 2018:1–16
Aljawarneh S, Aldwairi M, Yassein MB (2018) Anomaly-based intrusion detection system through feature selection analysis and building hybrid efficient model. J Comput Sci 25:152–160
Jiang K, Wang W, Wang A, Wu H (2020) Network intrusion detection combined hybrid sampling with deep hierarchical network. IEEE Access 8:32464–32476
Mazini M, Shirazi B, Mahdavi I (2019) Anomaly network-based intrusion detection system using a reliable hybrid arti_cial bee colony and Adaboost algorithms. J King Saud Univ Comput Inf Sci 31(4):541–553
Çavuşoğlu Ü (2019) A new hybrid approach for intrusion detection using machine learning methods. Appl Intell 49(7):2735–2761
Pajouh HH, Dastghaibyfard G, Hashemi S (2017) Two-tier network anomaly detection model: A machine learning approach. J Intell Inf Syst 48(1):61–74
Tama BA, Comuzzi M, Rhee K (2019) TSE-IDS: A two-stage classifier ensemble for intelligent anomaly-based intrusion detection system. IEEE Access 7:94497–94507
Gao X, Shan C, Hu C, Niu Z, Liu Z (2019) An adaptive ensemble machine learning model for intrusion detection. IEEE Access 7:82512–82521
Li L, Yu Y, Bai S, Hou Y, Chen X (2018) An effective two-step intrusion detection approach based on binary classification and KNN. IEEE Access 6:12060–12073
Ieracitano C, Adeel A, Morabito FC, Hussain A (2020) A novel statistical analysis and auto-encoder driven intelligent intrusion detection approach. Neurocomputing 387:51–62
Mohammadi S, Mirvaziri H, Ghazizadeh-Ahsaee M, Karimipour H (2019) Cyber intrusion detection by combined feature selection algorithm. J Inf Secur Appl 44:80–88
Golrang A, Golrang AM, YildrimYayilgan S, Elezaj O (2020) A novel hybrid IDS based on modified NSGAII-ANN and random forest. Electronics 9(4):577
Liu C, Gu Z, Wang J (2021) A hybrid intrusion detection system based on scalable K-means+ random forest and deep learning. IEEE Access 9:75729–75740
Zhao R, Yingxue M, Zou L, Wen X (2022) A hybrid intrusion detection system based on feature selection and weighted stacking classifier. IEEE Access 10:71414–71426
Chkirbene Z, Erbad A, Hamila R, Mohamed A, Guizani M, Hamdi M (2020) TIDCS: a dynamic intrusion detection and classification system based feature selection. IEEE Access 8:95864–95877
Sarvari S, Mohd Sani NF, Hanapi ZM, Abdullah MT (2020) An efficient anomaly intrusion detection method with feature selection and evolutionary neural network. IEEE Access 8:70651–70663
Stiawan D, Heryanto A, Bardadi A, PalupiRini D, Subroto IMI, Kurniabudi, Idris MYB, Abdullah AH, Kerim B, Budiarto R (2021) An approach for optimizing ensemble intrusion detection systems. IEEE Access 9:6930–6947
Tavallaee M, Bagheri E, Lu W, Ghorbani AA (2009) A detailed analysis of the KDD CUP 99 data set. In 2009 IEEE symposium on computational intelligence for security and defense applications. IEEE 1–6
Revathi S, Malathi A (2013) A detailed analysis on NSL-KDD dataset using various machine learning techniques for intrusion detection. Int J Eng Res Technol 2(12):1848–1853
Sugumaran VR, Rajaram A Lightweight blockchain-assisted intrusion detection system in energy efficient MANETs. Journal of Intelligent & Fuzzy Systems, (Preprint) 1–16
Arulselvan G, Rajaram A (2023) Hybrid trust-based secure routing protocol for detection of routing attacks in environment monitoring over MANETs. Journal of Intelligent & Fuzzy Systems, (Preprint) 1–16
Ilakkiya N, Rajaram A (2023) Blockchain-assisted secure routing protocol for cluster-based mobile-ad hoc networks. Int J Comput Commun Control 18(2):1
Rathish CR, Rajaram A (2018) Sweeping inclusive connectivity based routing in wireless sensor networks. ARPN J Eng Appl Sci 3(5):1752–1760
Acknowledgements
There is no acknowledgement involved in this work.
Funding
No funding is involved in this work.
Author information
Authors and Affiliations
Contributions
All authors are contributed equally to this work.
Corresponding author
Ethics declarations
Ethics approval and consent to participate
No participation of humans takes place in this implementation process.
Conflict of interest
Conflict of Interest is not applicable in this work.
Human and animal rights
No violation of Human and Animal Rights is involved.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Patthi, S., Singh, S. & P, I.C.K. 2-layer classification model with correlated common feature selection for intrusion detection system in networks. Multimed Tools Appl (2024). https://doi.org/10.1007/s11042-023-17781-w
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11042-023-17781-w