Abstract
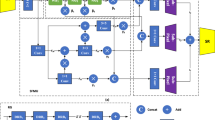
The swift growth of diverse editing software has resulted in image splicing manipulation becoming more complex, the discovery of a meticulously crafted splice forgery in digital images poses a significant challenge for both humans and machines. Existing image splicing manipulation detection algorithms have low localization accuracy and poor detection of small manipulation areas. In this paper, we proposed an end-to-end effective image manipulation location method based on a multi-scale and dual-channel model, MD_Unet. First, a dual-channel encoding network model is constructed. Adding a high-pass filtering branch containing SRM filters and Gabor filters at the input of the model and helps it to learn the manipulation traces of the image. Secondly, the dual-channel features are fused using an improved multi-scale pyramid pooling module. Then, Squeeze-Excitation is introduced to recalibrate the fused features so that the network pays more attention to splicing manipulation-related features. Finally, the fused feature map is input to the decoder, and the predicted image is decoded layer by layer to segment the manipulation region. We have performed extensive experimental validation and powerfully demonstrate the efficacy of the proposed approach.















Similar content being viewed by others
Data availability
The datasets generated during and/or analysed during the current study are available from the corresponding author on reasonable request.
References
Chen X, Dong C, Ji J et al (2021) Image manipulation detection by multi-view multi-scale supervision[C]. Proceedings of the IEEE/CVF international conference on computer vision, pp 14185–14193
Zampoglou M, Papadopoulos S, Kompatsiaris Y (2017) Large-scale evaluation of splicing localization algorithms for web images[J]. Multimed Tools Appl 76(4):1–34
Zhou P, Han X, Morariu VI, Davis LS (2018) Learning rich features for image manipulation detection. 2018 IEEE/CVF conference on computer vision and pattern recognition, Salt Lake City, UT, USA, pp 1053–1061. https://doi.org/10.1109/CVPR.2018.00116
Lee JC, Chang CP, Chen WK (2015) Detection of copy–move image forgery using histogram of orientated gradients[J]. Inf Sci 321:250–262
Huh M, Liu A, Owens A et al (2018) Fighting fake news: image splice detection via learned self-consistency[J]. Springer, Cham
Bahrami K, Kot AC, Li L et al (2015) Blurred image splicing localization by exposing blur type inconsistency[J]. IEEE Trans Inf Forensics Secur 10(5):999–1009
Kakar P, Sudha N, Ser W (2011) Exposing digital image forgeries by detecting discrepancies in motion blur[J]. IEEE Trans Multimedia 13(3):443–452
Liu G, Wang J, Lian S et al (2013) Detect image splicing with artificial blurred boundary[J]. Math Comput Model 57(11–12):2647–2659
Zeng H, Zhan Y, Kang X et al (2017) Image splicing localization using PCA-based noise level estimation[J]. Multimed Tools Appl 76(4):4783–4799
Hu WC, Dai JS, Jian JS (2015) Effective composite image detection method based on feature inconsistency of image components[J]. Digit Signal Process 39:50–62
Popescu AC, Farid H (2005) Exposing digital forgeries in color filter array interpolated images[J]. IEEE Trans Signal Process 53(10):3948–3959
Farid H (2008) Digital image ballistics from JPEG quantization: a follow up study [J]. Department of Computer Science, Dartmouth College, Tech Rep TR2008-638, pp 1–28
Cao G, Zhou AT, Huang XL et al (2019) Resampling detection of recompressed images via dual-stream convolutional neural network[J]. Math Biosci Eng 16(5):5022–5040
Iakovidou C, Zampoglou M, Papadopoulos S et al (2018) Content-aware detection of JPEG grid inconsistencies for intuitive image forensics[J]. J Vis Commun Image Represent 155–170. https://doi.org/10.1016/j.jvcir.2018.05.011
Rosa LD, L’Abbate S, Kusmic C et al (2022) Applications of artificial intelligence in lung ultrasound: review of deep learning methods for COVID-19 fighting[J]. Artif Intell Med Imaging 3(2):13
Yang Y, Zhu D, Qu T et al (2021) Single-stream CNN with learnable architecture for multi-source remote sensing data[J]. https://doi.org/10.48550/arXiv.2109.06094
Wang B, Wang R, Tang B et al (2021) A Research on advanced technology of target detection in unmanned driving[J]. J Phys Conf Ser 2010(1):012158-
Ronneberger O, Fischer P, Brox T (2015) U-net: convolutional networks for biomedical image segmentation[C]//. International Conference on Medical image computing and computer-assisted intervention. Springer, Cham, pp 234–241
Chen L C, Zhu Y, Papandreou G et al (2018) Encoder-decoder with atrous separable convolution for semantic image segmentation[C]//. Proceedings of the European conference on computer vision (ECCV), pp 801–818
Ren S, He K, Girshick R et al (2017) Faster R-CNN: towards real-time object detection with region proposal networks[J]. IEEE Trans Pattern Anal Mach Intell 39(6):1137–1149. https://doi.org/10.1109/TPAMI.2016.2577031
Bappy M, Roy-Chowdhury AK, Bunk J et al (2017) Exploiting Spatial structure for localizing manipulated image regions[C]//. IEEE international conference on computer vision. IEEE Computer Society
Salloum R, Ren Y, Kuo CCJ (2018) Image splicing localization using a multi-task fully convolutional network (MFCN)[J]. J Vis Commun Image Represent 51:201–209
Wu Y, AbdAlmageed W, Natarajan P (2019) Mantra-net: Manipulation tracing network for detection and localization of image forgeries with anomalous features[C]//. Proceedings of the IEEE/CVF conference on computer vision and pattern recognition, pp 9543–9552
Bi X, Wei Y, Xiao B et al (2019) RRU-Net: The ringed residual U-Net for image splicing forgery detection[C]. 2019 IEEE/CVF conference on computer vision and pattern recognition workshops (CVPRW), IEEE. https://doi.org/10.1109/CVPRW.2019.00010
Li H, Huang J (2019) Localization of Deep inpainting using high-pass fully convolutional network[C]//. 2019 IEEE/CVF international conference on computer vision (ICCV). IEEE
Bayar B, Stamm MC (2018) Constrained convolutional neural networks: a new approach towards general purpose image manipulation detection[J]. IEEE Trans Inf Forensics Secur 2691–2706
Zhang R, Ni J (2020) A dense U-Net with cross-layer intersection for detection and localization of image forgery[C]//. ICASSP 2020 - 2020 IEEE international conference on acoustics, speech and signal processing (ICASSP). IEEE
Fridrich J (2012) Rich models for steganalysis of digital images[J]. IEEE Trans Inf Forensics Secur 7(3):868–882
Gabor D (1946) Theory of communication[J]. Iee Proc London 93(73):58
Jie H, Li S, Gang S et al (2017) Squeeze-and-Excitation Networks[J]. IEEE Trans Pattern Anal Mach Intell PP(99)
Simonyan K, Zisserman A (2014) Very deep convolutional networks for large-scale image recognition[J]. Comput Sci. https://doi.org/10.48550/arXiv.1409.1556
He K, Zhang X, Ren S, Sun J (2016) Deep residual learning for image recognition. Proceedings of the IEEE conference on computer vision and pattern recognition, pp 770–778
Li B, Wei W, Ferreira A et al (2018) ReST-Net: diverse activation modules and parallel sub-nets based CNN for spatial image steganalysis[J]. IEEE Signal Process Lett PP(99):1–1
Verdoliva L, Cozzolino D, Poggi G (2015) A feature-based approach for image tampering detection and localization[C]//. IEEE workshop on information forensics and security. IEEE
Yedroudj M, Comby F, Chaumont M (2018) Yedrouj-Net: an efficient CNN for spatial steganalysis[C]//. 2018 IEEE international conference on acoustics, speech and signal processing (ICASSP). IEEE
Rui Y, Huang TS, Chang SF (1999) Image retrieval: past, present, and future[J]. J Vis Commun Image Represent 10(1):1–23
Liu S, Huang D, Wang Y (2018) Receptive field block net for accurate and fast object detection. In: Ferrari V, Hebert M, Sminchisescu C, Weiss Y (eds) Computer Vision – ECCV 2018 (Lecture Notes in Computer Science), vol 11215. Springer, Cham. https://doi.org/10.1007/978-3-030-01252-6_24
Hu J, Shen L, Sun G (2018) Squeeze-and-excitation networks. 2018 IEEE/CVF conference on computer vision and pattern recognition, Salt Lake City, UT, USA, pp 7132–7141. https://doi.org/10.1109/CVPR.2018.00745
Lin TY, Goyal P, Girshick R, He K, Dollar P (2020) Focal loss for dense object detection. IEEE Trans Pattern Anal Mach Intell 42(2):318–327. https://doi.org/10.1109/TPAMI.2018.2858826
Dong J, Wang W, Tan T (2013) Casia image tampering detection evaluation database[C]//. 2013 IEEE China summit and international conference on signal and information processing. IEEE, pp 422–426
Asati SR, Pardhi PR (2013) Exposing digital image forgeries by illumination color classification[J]. IEEE Trans Inf Forensics Secur 8(7):1182–1194
Hsu Y F, Chang SF (2006) Detecting image splicing using geometry invariants and camera characteristics consistency[C]//. 2006 IEEE international conference on multimedia and expo. IEEE
Dirik AE, Memon N (2009) Image tamper detection based on demosaicing artifacts, 2009 16th IEEE international conference on image processing (ICIP), Cairo, Egypt, pp 1497–1500. https://doi.org/10.1109/ICIP.2009.5414611
Bianchi T, Piva A (2012) Image forgery localization via block-grained analysis of JPEG artifacts. IEEE Trans Inf Forensics Secur 7(3):1003–1017. https://doi.org/10.1109/TIFS.2012.2187516
Xiao B, Wei Y, Bi XL, Li WS, Ma JF (2020) Image splicing forgery detection combining coarse to refined convolutional neural network and adaptive clustering. Inf Sci 511:172–191. ISSN 0020-0255
Zhao H, Shi J, Qi X, Wang X, Jia J (2017) Pyramid Scene Parsing Network. 2017 IEEE conference on computer vision and pattern recognition (CVPR), Honolulu, HI, USA, pp 6230–6239. https://doi.org/10.1109/CVPR.2017.660
Chen LC, Papandreou G, Schroff F et al (2017) Rethinking atrous convolution for semantic image segmentation[J]. arXiv preprint arXiv:1706.05587
Ronneberger O, Fischer P, Brox T (2015) U-Net: Convolutional networks for biomedical image segmentation. In: Navab N, Hornegger J, Wells W, Frangi A (eds) Medical image computing and computer-assisted intervention – MICCAI 2015. MICCAI 2015. Lecture Notes in Computer Science(), vol 9351. Springer, Cham. https://doi.org/10.1007/978-3-319-24574-4_28
Wu Y, Abdalmageed W, Natarajan P (2019) ManTra-Net: manipulation tracing network for detection and localization of image forgeries with anomalous features[C]// 2019 IEEE/CVF conference on computer vision and pattern recognition (CVPR). IEEE
Bi X, Wei Y, Xiao B et al (2019) RRU-Net: the ringed residual U-Net for image splicing forgery detection[C]//. 2019 IEEE/CVF conference on computer vision and pattern recognition workshops (CVPRW). IEEE
Ding H, Chen L, Tao Q et al (2023) DCU-Net: a dual-channel U-shaped network for image splicing forgery detection. Neural Comput & Applic 35:5015–5031. https://doi.org/10.1007/s00521-021-06329-4
Acknowledgements
This work was supported by major programs incubation plan of Xizang Minzu University: 22MDZ03 and key project of the Natural Science Foundation of the Tibet Autonomous Region: image forgery detection and location based on multi semantics and attention: XZ202301ZR0042G.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Hu, J., Xue, R., Teng, G. et al. Image splicing manipulation location by multi-scale dual-channel supervision. Multimed Tools Appl 83, 31759–31782 (2024). https://doi.org/10.1007/s11042-023-16705-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-16705-y