Abstract
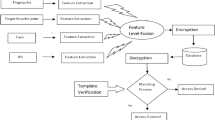
Biometric cryptosystem (BCS) is a challenging field of study where data is secured using biometrics features and cryptographic encryption. The necessity for retaining login credentials has been eliminated by the incorporation of biometrics in encrypted technology. The integration of biometrics into cryptographic systems eliminates the necessity of recalling passwords. This manuscript puts forward an innovative approach referred to as Scale Invariant Feature Transform (SIFT) based Biometric Cryptosystem (SIFTBCS) for the construction of cryptographic keys from the obtained features. The foundation of this technique rests upon the established Fuzzy Vault scheme utilized for safeguarding data. The motive behind employing the SIFT scheme in biometric cryptosystems is that the extracted features remain unaltered by changes in orientation and scaling, thereby enhancing the accuracy and reliability of authentication. SIFTBCS method is comprised of three distinct stages, namely Key generation, Enrollment and Authentication. Comprehensive experiments were performed on five different ear databases, namely Mathematical Analysis of Images, Carreira-Perpinan, Indian Institute of Technology Delhi (version 1 & 2) and University of Science & Technology Beijing (version 2). Statistical and non-numeric data are used to draw meaningful conclusions from the study. The proposed technique achieves an accuracy of \(\approx \) \(94\%\) on USTB-v2, IITD-v1 and CP databases. Our approach demonstrated superior performance using both kinds of performance evaluations.















Similar content being viewed by others
Data Availability
There is no associated data in the manuscript. The experiments in the manuscript are conducted on publicly available datasets which can be accessed using the references given in the manuscript.
References
Manisha KN (2020) Cancelable biometrics: a comprehensive survey. Artif Intell Rev 53:3403–3446
Kholmatov A, Yanikoglu B (2006) Biometric cryptosystem using online signatures. In: International symposium on computer and information sciences. pp 981–990
Rathgeb C, Uhl A (2011) A survey on biometric cryptosystems and cancelable biometrics. EURASIP J Inf Secur 2011:1–25
Kaur P, Kumar N, Singh M (2022) Biometric cryptosystems: a comprehensive survey. Multimedia Tools and Appl, pp 1–56
Juels A, Sudan M (2006) A fuzzy vault scheme. Des Codes Cryptogr 38:237–257
Huixian L, Man W, Liaojun P, Weidong Z (2009) Key binding based on biometric shielding functions. In: Fifth international conference on information assurance and security, pp 19–22
Rathgeb C, Uhl A (2009) An iris-based interval–mapping scheme for biometric key generation. In: Proceedings of 6th international symposium on image and signal processing and analysis, pp 511–516
Krivoku’ca V, Abdulla W (2014) Intra–class variance among multiple samples of the same person’s fingerprint in a cooperative user scenario. In: International conference on pattern recognition applications and methods. pp 77–92
Koetter R, Vardy A (2003) Algebraic soft-decision decoding of Reed-Solomon codes. IEEE Trans Inf Theory 49:2809–2825
Ratha NK, Connell JH, Bolle RM (2001) An analysis of minutiae matching strength. In: International conference on audio–and video–based biometric person authentication, pp 223–228
Greg C (2020) ISO/IEC JTC 1/SC 37 Biometrics. In: ISO. https://www.iso.org/committee/313770.html. Accessed 12 Feb 2022
Lowe DG (2004) Distinctive image features from scale-invariant keypoints. Int J Comput Vis 60:91–110
Ponce-Hernandez W, Blanco-Gonzalo R, Liu-Jimenez J, Sanchez-Reillo R (2020) Fuzzy vault scheme based on fixed-length templates applied to dynamic signature verification. IEEE Access 8:11152–11164. https://doi.org/10.1109/ACCESS.2020.2965165
Ong TS, Jin ATB, Ngo DCL (2008) Application-specific key release scheme from biometrics. Int J Netw Secur 6:127–133
Clancy TC, Kiyavash N, Lin DJ (2003) Secure smartcardbased fingerprint authentication. In: Proceedings of the 2003 ACM SIGMM workshop on biometrics methods and applications, pp 45–52
Uludag U, Jain A (2006) Securing fingerprint template: fuzzy vault with helper data. In: Conference on computer vision and pattern recognition workshop (CVPRW’06), pp 1–8
Lee YJ, Bae K, Lee SJ et al (2007) Biometric key binding: fuzzy vault based on iris images. In: International conference on biometrics. pp 800–808
Hyvarinen A, Oja E (2000) Independent component analysis: algorithms and applications. Neural Netw 13:411–430
Nagar A, Nandakumar K, Jain AK (2008) Securing fingerprint template: fuzzy vault with minutiae descriptors. In: 19th international conference on pattern recognition, pp 1–4
Wang Y, Plataniotis KN (2007) Fuzzy vault for face based cryptographic key generation. In: Biometrics symposium, pp 1–6
Wu Z, Liang B, You L et al (2016) High-dimension space projection-based biometric encryption for fingerprint with fuzzy minutia. Soft Comput 20:4907–4918
Hine GE, Maiorana E, Campisi P (2017) A zero-leakage fuzzy embedder from the theoretical formulation to real data. IEEE Trans Inf Forensics Secur 12:1724–1734
Elrefaei LA, Al-Mohammadi AM (2022) Machine vision gait-based biometric cryptosystem using a fuzzy commitment scheme. J King Saud Univ-Comput Inf Sci 34:204–217
Sujitha V, Chitra D (2018) Highly secure palmprint based biometric template using fuzzy vault. Concurr Comput Pract Exp 31:1–7. https://doi.org/10.1002/cpe.4513
Sujitha V, Chitra D (2019) A novel technique for multi biometric cryptosystem using fuzzy vault. J Med Syst 43:1–9
Moon D, Choi W-Y, Moon K, Chung Y (2009) Fuzzy fingerprint vault using multiple polynomials. In: IEEE 13th international symposium on consumer electronics, pp 290–293
Zhang W, Chen T (2005) Generalized optimal thresholding for biometric key generation using face images. In: IEEE international conference on image processing, pp 781–784
Panchal G, Samanta D (2018) A novel approach to fingerprint biometric-based cryptographic key generation and its applications to storage security. Comput Electr Eng 69:461–478. https://doi.org/10.1016/j.compeleceng.2018.01.028
Loukhaoukha K, Chouinard J-Y, Berdai A (2012) A secure image encryption algorithm based on Rubik’s cube principle. J Electr Comput Eng 2012:1–13
Gonzalez E, Alvarez L, Mazorra L (2012) AMI Ear Database. In: Univ. Las Palmas Gran Canar. https://ctim.ulpgc.es/research.works/ami.ear.database. Accessed 11 Jan 2022
Mathur A, Conway R (2013) Ear recognition system Using Principal component analysis. Dissertation, University of Limerick
Kumar A, Wu C (2012) Automated human identification using ear imaging. Pattern Recognit 45:956–968
Mu Z (2002) USTB Ear database. In: Univ. Sci. Technol. Beijing. http://www1.ustb.edu.cn/resb/en/visit/visit.htm. Accessed 12 Jan 2022
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interest
The authors declare that they have no conict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Kaur, P., Kumar, N. SIFTBCS: scale invariant feature transform based fuzzy vault scheme in biometric cryptosystem. Multimed Tools Appl 83, 28635–28656 (2024). https://doi.org/10.1007/s11042-023-16643-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-16643-9