Abstract
This research introduces a novel and robust watermarking scheme for medical Brain MRI DICOM images, addressing the challenge of maintaining high imperceptibility and robustness simultaneously. The scheme ensures privacy control, content authentication, and protection against the detachment of vital Electronic Patient Record information. To enhance imperceptibility, a Dynamic Visibility Threshold parameter leveraging the Human Visual System is introduced. Embeddable Zones and Non-Embeddable Zones are defined to enhance robustness, and an enhanced Knight Tour algorithm based on Slantlet Transform shuffles the embedding sequence for added security. The scheme achieves remarkable results with a Peak Signal-to-Noise Ratio (PSNR) evaluation surpassing contemporary techniques. Extensive experimentation demonstrates resilience to various attacks, with low Bit Error Rate (BER) and high Normalized Cross-Correlation (NCC) values. The proposed technique outperforms existing methods, emphasizing its superior performance and effectiveness in medical image watermarking.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Modern technology has brought about significant advancements in medical imaging facilities and their management systems, revolutionizing the way hospitals and healthcare institutions operate. These technological advancements, particularly in the realm of electronic patient records, have contributed to improved service delivery in terms of efficiency and quality. However, alongside these benefits, they have also introduced a potential vulnerability, providing a backdoor for hackers and unauthorized individuals to gain access to the system. This breach of security raises concerns pertaining to both legal and ethical aspects [38]. Also, deploying such modern technologies in healthcare applications makes the patient record vulnerable. For instance, transmission of medical images and Electronic Patient Record over the internet or even intranet, as a result, will have a risk of being vulnerable to corruption by noisy transmission. Hence, security is an essential requirement for healthcare management.
By using the latest image processing software such as Photoshop, hackers can easily modify or edit the medical image for illegal purposes such as false insurance claiming. As reported by Mehta on his report, of all the medical claims an insurer receives between 25% to 30% are manipulated, and 10 % of those claiming is outright fraudulent [22]. Furthermore, a doctor maybe misdiagnoses the patient thru the medical image if the medical image has been tampered [35].
In the current era of globalization, effectively preventing copyright infringement of digital biomedical images has become increasingly challenging. This issue becomes particularly critical in the context of Digital Imaging and Communications in Medicine (DICOM), which is inherently linked to personal information and confidentiality. Adhering to the standards set by the International Organization for Standardization (ISO) offers a viable solution to meet the international legal requirements concerning healthcare security. By implementing ISO standards, healthcare organizations can ensure the protection and security of sensitive medical data, maintaining the integrity and privacy of patients’ information in the realm of DICOM imaging [18]. Thus, a digital watermarking adhering to ISO is being introduced as an alternative solution to resolve the problem. In between, the embedded watermarking scheme should not produce any degradation in the medical image in human visual at the same time having high robustness since it is crucial for diagnosis [3, 14, 39]. Moreover, hackers nowadays are of very high knowledgeable in retrieving and recovering watermarks. Hence, robustness watermarking for medical images is the must to prevent third party and unauthorized party from extracting the watermark from the host image [27, 29]. Proposed scheme needs to emphasis on the different embedding sequence rather than conventional raster scan in the watermarking embedding process. Other than that, working on preserving the EPR information from DICOM file also need to be carried out to maintain the permanent link between it and its corresponding image file [19, 27, 42]. Embedding watermark in ROI requires a lossless or reversible watermarking scheme whereby RONI-based watermarking scheme will increasing the chance of hackers recovering the watermarks. How to achieve a balance point or compromising convey point to achieve the equilibrium between high imperceptibility, high robustness, and high security at once for a medical image watermarking scheme is become the center of research problem.
The current paper builds upon the foundation laid by a conference paper previously published [36] by the authors. While the [36] primarily focuses on achieving high imperceptibility in medical image watermarking using the Slantlet Transform and a Dynamic Visibility Threshold, the extended journal paper expands upon this approach by introducing an enhanced Knight Tour algorithm coupled with the Slantlet Transform. The current extended article centres around Brain MRI Coupled with Enhanced Knight Tour Algorithm for medical Brain MRI DICOM images, while also addressing privacy control and content authentication simultaneously. The primary objective of this research is to propose a digital watermarking scheme that ensures both high imperceptibility and robustness for brain MRI DICOM images, while also considering the importance of Electronic Patient Record (EPR) information in adherence to ISO standards for enhanced security protection. The scope of this research is limited to the following aspects: (a) the development of a fragile and irreversible watermarking scheme, (b) the utilization of a standard dataset sourced from OsiriX consisting of grayscale Brain MRI DICOM images, and (c) the application of the proposed scheme for content authentication purposes. This addition aims to enhance the robustness of the watermarking scheme, making it more resilient against various attacks and ensuring the integrity and authenticity of medical Brain MRI DICOM images. Furthermore, the extended journal paper presents comprehensive experimental evaluations and comparisons with contemporary techniques, demonstrating superior performance in terms of Peak Signal-to-Noise Ratio (PSNR), Bit Error Rate (BER), and Normalized Cross-Correlation (NCC) values. This paper not only emphasizes the high imperceptibility but also addresses the critical aspect of robustness, making it a significant advancement in the field of medical image watermarking.
The organization of this paper is as follows: In Section 2, a review of previous studies related to medical image watermarking is investigated. In Section 3, the methodology of research is presented in detail. In Section 4, the qualitative and quantitative experimental results are described. Finally, in Section 5, a general conclusion is drawn.
2 Literature review
Watermarking has brought some unique advantages for medical image nowadays. Nonetheless, watermarking also has an inevitable impact on the quality of perceptual and difficulties in term of legacy content. In 2009, three methods [17] had been mentioned to overcome the image distortion. Firstly, accepting the distortion in the specified range; Second, separating protection zone from the insertion zone to avoid compromising diagnostic where the protection zone is free for any watermarking to preserve the medical image from modification and the insertion zone will be used for embedding of the watermarking image [12]. Lastly, make sure the embedded watermarked image can be recovered to its original image (i.e., reversible). By separating the medical image into these two zones, the insertion zone will become ROI of watermarking whereby RONI of watermarking will fall into the protection zone. The doctor will diagnose the medical image before further diagnosing process. Also, medical image eliminates the needs of open up the patient body surgically for medical practitioners to observe the inner body. By separating the medical image into these two zones, the insertion zone will become a region of interest (ROI) of watermarking (but RONI in medical perspective), whereby the region of non-interest (RONI) of watermarking (ROI in medical perspective) will fall into the protection zone. Since the ROI of medical image is very important, some researchers utilize the concept of ROI-based in their invented methods, such as [1, 2, 10, 13, 20, 23, 25].
Wakatani [37] proposed a scheme where the watermark is embedded in a region from outside the ROI but is vulnerable to introduce copy attack on the ROI regions. Rodrigues et al. [31] proposed a scheme where it looks for suitable pixels for embedding using a spiral scan from the centroid of the image. However, if this applied to the medical image, it will interrupt the medical image pixels. Giakoumaki et al. [13] and Woo et al. [40] also proposed a multiple watermarking schemes in medical images respectively. Al-Qershi and Khoo [1] whereby, proposed a scheme which based on DE for data hiding of patient data. In their method, ROI is used to embed patient’s particulars and hash it using Guo [17] with some modification. Whereas the watermarking map is combined with recovery information and embedded into RONI by employing the method by Kundur [21]. This hybrid method shows that the watermark image can withstand (robust) certain level of salt and pepper and cropping noise. Hence it fails to recover tampered area of the watermarked image.
A watermarking technique has been proposed by [11] where the RONI of Magnetic Resonance Imaging (MRI) is used to insert the ROI of the same image. By means of that, any tampering will be detected and the watermarked image able to recover to its original state (i.e., image before undergo watermarking). The particular case in medical image is the separation of ROI and RONI is not as easy as in general image, and it requires professional knowledge from doctor and medical staff to verify itself, although it has been applied into several watermarking schemes [1, 7, 9, 24] previously. Moreover, although computational properties may incur additional complexity in different processing domains, developing the reversible watermarking scheme (as mentioned above) is promising for the medical image without taking the risk for sacrificing the diagnostic accuracy. Not only the complexity of the computational will occur, but also another two additional drawbacks will be coming along as mentioned by [4], (1) it imposes the watermark removal before a diagnosis is made upon the image. (2) it dons a secured environment since the medical image is unprotected once the watermark is removed.
Kundu and Das [19] proposed a watermarking scheme that can be used to enhance confidentiality, integrity, security and verification of medical information with combining spatial domain watermarking technique with lossless data compression and encryption at once. They claim that the method is high in imperceptibility and payload capacity. Their experiment scope covers not only on specific modality but as well on different medical images (CT, MRI, angiogram, mammography, barium study, X-ray). In terms of payload capacity, the experiment shows that as much as 10,000 characters embedded in the image causing PSNR value to be well over 40 dB. The drawback of this method is the selection of polygonal as ROI needs to be defined by doctor interactively, which means that the algorithm cannot segments the medical image automatically.
All of the factors above lead us come to a point that a combination of suitable type of watermarking schemes can be developed in order to solve the medical image security issues [2, 13, 15, 16, 23, 28]. The research gaps from the current existing method congregated from literature review are: low imperceptibility when encountering a big watermark, detachment of DICOM header files which causing loss of EPR details, neither nor high embedding capacity and high imperceptibility can be granted at the same and integrity issues when the intentional attacks against DICOM file to modify the EPR.
3 Research methodology
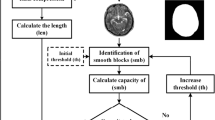
This section provides a research framework specially designed for this study, which consists of four stages namely Pre-processing stage, Embedding Stage, Attacking Stage and Extraction Stage. Detail about the proposed design framework for the new watermarking scheme for medical brain MRI DICOM image for privacy control and content authentication will be discussed here. In this context, four main stages are being involved: (1) Pre-processing stage - At this stage, all the prerequisite resource, namely DICOM [26] image contrast, EPR watermark preparation and EBD zone (embeddable zone) Extraction are being prepared for the next stage; (2) Embedding Stage – A subsequence of earlier stage where all the prerequisite resource is used to perform the embedding process: decomposition of MRI DICOM image, watermark shuffling and imperceptibility control. (3) Attacking Stage – A stage where the host image is undergoing various with image attacking. (4) Extraction Stage – A stage where the embedded watermark is being extracted. Evaluation of imperceptibility and robustness are the two measurements involved here.
3.1 Standard DICOM MRI dataset
The DICOM MRI dataset utilized in this study was obtained from BRAINIX, a medical database provided by OsiriX, Pixmeo SARL (http://www.osirix-viewer.com/resources/dicom-image-library/). OsiriX is a Swiss company headquartered in Geneva, specializing in the development of medical imaging software and PACS systems. It is worth noting that OsiriX holds ISO 13485 certification, highlighting its adherence to internationally recognized standards for medical device quality management. The dataset used in this research is based on a well-established and widely recognized standard dataset [26]. This dataset is extensively employed by researchers in the field of medical imaging, ensuring its reliability and suitability for medical image research purposes. The dataset comprises a total of 232 DICOM images, encompassing various MRI scans.
3.2 Pre-processing stage
The pre-processing stage plays a crucial role in minimizing the computational burden associated with the watermarking process. Figure 1 illustrates the workflow of the pre-processing stage within the proposed method. At this stage, the input consists of brain MRI DICOM images. Additionally, the Electronic Patient Record (EPR), serving as the watermark, undergoes necessary processing before embedding it into the host MRI DICOM image. This pre-processing step sets the foundation for seamless integration of the watermarking process into the subsequent stages of the proposed method.
3.2.1 EPR watermark preparation
In this proposed scheme, the watermarking used to embed into the host image is made up of EPR from the DICOM image. The EPR is chosen to offer private and confidential patient information which coherent between patient and his MRI DICOM image. The DICOM is a medical field standard which consists of many metadata fields with different variable classes. With the intention of getting the selected field of EPR from the DICOM and turn it into watermark bit stream, the traditional dicominfo which returns all the metadata information of the DICOM cannot be used as the MATLAB does not allow concatenation of different class of variable into the bit stream. Hence, to parse the bit stream, following MATLAB code is designed to outfit the proposed scheme. A total of 12 entities of extracted metadata from DICOM is selected to embed and each of it is concatenated with character ‘#’ for field delimiter to form a single string watermark.
3.2.2 Embeddable zone (EBD) segmentation using active contour with global region
In this research, segmentation based on edge is not the focus because we need to know the details of the brain but not all in all inside the skull, viz., the contour of the ROI is appeared more critical than edges. Consequently, the traditional active contour and snakes which rely on the edge function and image gradient for edge detection is not practical. The sequence of this section can be summarized in Fig. 2. Thus, segmentation based on Active Contour with Global Region Approach is being introduced. This enhancement achieves traditional active contour results in a global region which eliminates any edges inside that detected region by introducing a layer of the kernel of its size same with input DICOM file which consists of small circle distributed equally across the latter. The kernel used is illustrated in Fig. 3.
The essential part of the active contour with global region approach is the Signed Distance Function, SDF. The SDF will be calculated by using the Euclidean distance transform of the initial mask which consists of small circles. This two- dimensional transform has positive values for points inside the circle (the ROI region) and negative values for points outside the circle (the RONI region). Those positive values will decrease gradually as the force come close to the boundary where the SDF is zero and will take negative values outside of the region. Segmentation is done by using the small circle scatter around the brain MRI image and ‘see-sawing battle’ between two forces, F1 Equation {1} and F2 Equation {2} where the latter will be shrinking and expanding the circle to achieve the equilibrium.
where
- 𝒖𝟎:
-
binary image of brain DICOM file,
- 𝒄𝟏:
-
mean of 𝑢0 inside the contour,
- c2:
-
mean of 𝑢0 outside the contour.
Two forces achieve the equilibrium where the contour of the brain is found, the sum of F1 and F2 are equal to zero and the segmentation process is done.
3.3 Embedding stage
Figure 4 shows the overall flowchart of the embedding stage of the proposed method and the description followed by the process is indicated in the figure too.
3.3.1 EBD zone decomposition using Slantlet transform
In this proposed algorithm, a data hiding technique for EPR information by frequency coefficient decomposition based on Slantlet Transform (SLT) is being employed to create more bit planes for embedding purposes. The SLT be based upon DWT having a new parameter of orthogonal with two zero moments and at the same time, improving time-localization. Unlike DWT, the processing time for SLT is shorter than DWT. This is due to SLT able to be implemented by using filterbank as parallel, and different filters have been configured for each scale, i.e., SLT has improved time localization with degradation frequency selectivity. The EBD zone of the Brain MRI DICOM (which produced by Section 3.2.2 Embeddable Zone (EBD) Segmentation Using Active Contour with Global Region) will pass to SLT for purposes mentioned above. As a consequence, it allows the EBD zone to have more spaces for embedding purposes. The process in SLT decomposition is explained below.
Decompose the ROI into sub-band using Slantlet Transform, SLT. Four sub-bands namely, LL (approximate details), HL (horizontal details), LH (vertical details) and HH (diagonal details) will be produced (Fig. 5 The conventional 2D SLT decomposition for dividing an image). The SLT filter bank is implemented in the form of parallel structure, means different filters are used for different scale instead of filter iteration for each level. Three filter banks involved are low pass filter hi(n), adjacent of low pass filter, fi(n)whereby remaining pixel is filtered by gi(n).
where
where
where
By referring to the formulas mentioned above, since the standard image size of a DICOM file is 512 × 512 pixels, to boot, no scale or shrink down should be allowed against the DICOM as described in Section 3.1, the size of Slantlet matrix formulated is 25 × 25 pixel (i.e.: 32 × 32 pixels).
This can be seen in function getSlantTransform, where N is the size of the ROI region. The value of N is used to create the same size of Slantlet matrix as embellished in function sltmtx below (please refer Figs. 6 and 8 for Slantlet matrix used in this research and explanation for the mentioned Slantlet matrix).
The dimension of the input, or in this case, the ROI region will be reduced by half since the output of the SLT will produce four equal quadrants sub-band with total dimension same with the input before SLT transform (Fig. 7). This is caused by the low pass filter, ℎ𝑖(𝑛) which is a half band filter of fulfilling the Shannon’s Sampling Theory [34].
As per, the first row of the Slantlet matrix is always constant which obeys the periodic results of finite length signal.
3.3.2 Watermark flow confusion using enhanced knight tour with heuristic preset rules
Another contribution of this research is how to implement the night tour algorithm. Conventionally, Knight Tour is used in spatial domain to visit pixel in spatial domain, whereby in this research, Knight Tour is taken to a new level where its algorithm has been enhanced with few rules, and it is introduced into coefficient of the sub-band of frequency domain where it is in charge of the “sequence” instead of “process” of the embedding stage. In other words, it is used for the sequence of the embedding rather than the method how the watermark is embedded. In addition, the sequence of embedding is being shuffled which is called Watermark Flow Confusion which thus can increase the security of the proposed method by protecting the watermark if compared to raster scan sequence. The purpose of including this into the scheme is to prevent third party or unauthorized person from recovering the EPR from the host DICOM image. Even if the hacker or unauthorized person manages to exact the watermarking bit from the host image, they cannot reconstruct the original watermark since the watermarking bit is not sorted and embedded in normal raster sequence. Further, they are still unable to guess the watermark even though they get to know the Knight Tour since the Knight Tour algorithm is protected by the three new-special-designed heuristic rules (Fig. 8).
Explanation of formula used in Fig. 7
Generally, a typical Knight Tour algorithm utilize backtracking algorithm with the aim of visiting every single pixel of an image. By mean of this, the “Knight” needs to predict the wrong move and must go back to the previous move and try another move until getting a solution that works. This kind of “Trial and Error” method although can cater the problem by trying all configurations but it is not an efficient way since it recursively checks whether that move leads to a solution or not. If that chosen fail to give a solution then it should be removed from the sequence and continue try other moves, i.e.: A Knight can make its move to eight positions (refer to Fig. 9, exception to border pixel), literally, it can give a try to first possible solution, and if that fails then it will need to try another seven positions.
Instead of guessing, in this research, three heuristic rules are being used to optimize the Knight Tour algorithm, especially in large dimension image. The heuristic algorithm will suggest the possible move, and that particular move is always being the best move based on some preset rules. Thus, the Knight will visit each coefficient of sub-band without having sixes and sevens and save up the computational power on unwanted route.
-
Heuristic Rule 1: Each time of Knight move, it must try to expand outward in a way that it leans against the outer coefficient.
-
HeuristicRule2: When meeting a corner, no bounce back is allowed, it should try the best to cover outer pixel without going inside inner coefficient with respect to Rule 1.
-
Heuristic Rule 3: When Knight reaches the corner, there are only two possible moves, M1 and M2 are accepted at each corner pixel of the image as shown in Fig. 11. By way of this, Knight will not access coefficient which out of the boundary, also, if any M1 and M2 is accessed in the middle of the sequence, it should have forwarded to corresponding corner coefficient to form a path between itself and corner coefficient, or else a complete Knight Tour is not possible.
The Knight Tour is used here which is an extended version of the structural concept by Parberry [30] but eliminating the needs of divide-and-conquer concept on a large board. Figure 10 shows the overall workflow of the enhanced Knight Tour with preset heuristic rules implemented (Fig. 11).
Deducted from the scenario above, total of twelve coefficients (four corner coefficients + eight connected coefficients) out of 36 coefficients already covered at the first iteration inthealgorithm. Toforma complete closed Knight sequence, Knight, K1, K2, K3, and K4 is connected to two other coefficients. In this context, K1 is connected to SW1 and SW2, K2 is connected to NW1 and NW2, Knight 3 is connected to NE1 and NE2 wherebyKnight 4 is connected to SE1 and SE2. For example, whenever the Knight sequence is reaching SE1, the next step for the sequence need go to K4 and followed by SE2 or the inverse sequence. Figure 12 shows the subsequence of expanding of Knight Tour after Fig. 11. Notice that each Knight did not move inward into inner coefficient due to Heuristic Rule 1 restriction.
Subsequence of expanding of Knight Tour in Fig. 11
It is good to take note that Heuristic Rule 1 and Rule 2 make sure inner ring is accessed after outer ring is fully covered if there is no outer coefficient is available. In order to fulfill the Heuristic Rule 1 and Rule 2, a priority move which based on Fig. 9 is designed as below (Table 1).
As shown in Table 1, it is shown that each Knight has their own preferred move which ranging priority from 1 to 7 (1 with highest priority and 7 is the lowest priority). As for example, algorithm hoping that SW1 is moving along the edge of the chessboard. The nearest edge of the chessboard from SW1 is left part of the chessboard, so SW1 always moving to the left with moving direction (−1,2) which is the highest priority of preferred move the list. At certain level of expansion, the SW1 will come to the top of the chessboard which cannot proceed further with the first priority move, so algorithm will help it to move its foot step to the right side of the chessboard with (1,2) which rightward the moving direction. The third priority move for SW1 is moving downward along the right side of the chessboard, and it explains the preferred move of third priority is (2,-1] as noted by the negative value of coordinate y because we want the Knight moving down along y-axis. The same concept is applied to the rest of the Knight with its connected coefficients.
As the Knight iterates and expands over the time, more and more coefficients will be covered. Generally, board size equals to 4n + 2 where n > 1 in order to obtain a closed complete Knight Tour path. Also, notice that the smallest image dimension accepted in this research is 6 × 6 pixel (refer to Table 2) whereby the total number of coefficients “stepped” by Knight in each expansion is shown in Table 3.
After obtaining the closed complete Knight Tour path, the algorithm will pick a starting coefficient to be the initial point and follow the closed path to complete the sequence. The closed Knight Tour only exists on square board with board size must be 4n + 2, where n ≥ 1. As a result, for the minimum board size accept by this algorithm is when n = 1, board size = 6. An example of a Knight Tour’s move with board size 6 × 6 is illustrated in Fig. 13a. For any board size did not fulfil the 4n + 2, where n ≥ 1, for example, 8 × 8 board will not be going to have a completely closed Knight Tour on it. Figure 13b shows the incomplete Knight Tour on an 8 × 8 board. To prevent the incomplete Knight Tour situation from happening, any of the board sizes which did not fulfill the condition will be pre-cropped from the upper left corner, and the remaining of the coefficients will not be involved in embedding stage. An example of Knight Tour on a board of size 62 × 62 is depicted in Fig. 13c. As can be seen, all squares are visited by the Knight only once.
3.3.3 Embedding with dynamic visibility threshold, DVT for imperceptibility control
In typical scenarios, watermarking involves the substitution of pixel values in the spatial domain or coefficients in the frequency domain of the host image. However, in this research, a different approach is adopted, where the watermark is inserted into the frequency domain by modifying the coefficient values within two specific sub-bands, namely HL and LH. This alteration process is facilitated by a comparing algorithm. The selection of these particular coefficients for watermark embedding is influenced by the characteristics of the Human Visual System (HVS). Taking into consideration that the sub-band LL contains the highest energy, while the sub-band HH captures the edges and essential texture features of the image, the middle-frequency sub-bands HH and LH are chosen for embedding. This choice is made to minimize the chances of detection by the naked human eye.
Figure 14 demonstrates the embedding of the watermark through coefficient alteration, employing the Dynamic Visibility Threshold process. This sub-process is an integral part of the primary embedding process illustrated in Fig. 4. Algorithm 1 outlines the steps involved in selecting the desired coefficient for the watermark embedding procedure.
For a watermark (EPR) binary stream, w_before, the horizontal and vertical high-frequency sub-coefficient that have the same matrix coordinate are being chosen as (𝑗,) and 𝐿𝐻 𝑗,). The embedding watermark process is done by altering the (j, k) and 𝐿𝐻 (j, k) to magnify the difference between sub-coefficient. As a result, Dynamic Visibility Threshold, DVT is being introduced here as a parameter to disturb the original image signal. The magnifying difference between sub-coefficient use Eqs. (6) and (7).
If the watermark binary stream, 𝑤𝑎𝑡𝑒rmarki = 1 𝑎𝑛𝑑 𝐷𝑖𝑓𝑓𝑒𝑟𝑒𝑛𝑐𝑒1 (j, k) < 𝐷𝑉𝑇
Else if the watermark binary stream, 𝑤𝑎𝑡𝑒𝑟𝑚𝑎𝑟𝑘𝑖 = 0 𝑎𝑛𝑑 𝐷𝑖𝑓𝑓𝑒𝑟𝑒𝑛𝑐𝑒2(𝑗,𝑘) < 𝐷𝑉𝑇
For this research, three kinds of value have been selected to be involved in the experiment and one optimal value for Dynamic Visibility Threshold, DVT will be selected (First Quartile, Second Quartile, and Third Quartile in Fig. 15).
3.4 Attacking stage
Nowadays, technology has made a unique way for everyone process an image. To evaluate the performance of the enforced algorithm implemented in this research, different type of image attacking is being adopted. Applying attacks on the watermarking image will result in incapability on watermarking to perform its intended purpose.
3.4.1 Gaussian noise
Gaussian Noise is introduced over the image by random fluctuation on the image. In other words, random values are added to the pixel as a disturbance (Eq. (8)).
where g = gray level; μ = mean; σ = standard deviation.
3.4.2 Salt and pepper noise
Salt and Pepper noise, which also known as impulse noise, is another generic form of noise that consists of white and black pixels scattered randomly. It described as “On and off pixels” in MATLAB documentation where both (or either) salt and pepper like pixels are introduced into the image with the probability density function, PDF as Eq. (9):
Where
3.4.3 Speckle noise
Speckle Noise is similar to Gaussian noise, but the former is modeled by multiplying pixel with some random values where the resultant pixel equals to p(1 + n) as Eq. (10):
where n is uniformly distributed random noise.
3.4.4 Poisson noise
Poisson Noise is named due to its’ characteristic where it follows the Poisson distribution. Poisson noise is showing due to the distribution of independent photons are randomly placed. For this type of noise, it is impossible to diminish because it is a native property of a light beam. In practice, it is mimicked using a Gaussian distribution depends on the number of the expected photon detected by probability mass function as Eq. (11):
𝑤ℎ𝑒𝑟𝑒
- k:
-
number of occurence
- λ:
-
average number of occurence
3.4.5 Blurring filter attack
Blur Filter is also known as low pass filter which replacing a group of pixel value with an average pixel from that neighboring pixel. The filter kernel used for the blur filter attack is a circle in shape which reflected in the code segment section by creating a circular averaging filter with a radius of 5 where input array values outside the kernel are treated replicated to the nearest array border value. The imfilterfrom MATLAB employed in the algorithm taking the advantages of hardware to process the DICOM (datatype uint16) to decrease the process time.
3.4.6 Sharpening filter attack
Unlike blurring filter, a sharpening filter is a high pass filter that works in the same way with former, but it amplifies the noise. With the sharpening filter, all fair and tiny details are being exaggerated.
3.4.7 Geometric attack
For geometric attack, the purpose of the designed attacking is to disturb and disable the watermarking detection rather than remove the watermark. This attacking intended to break the correlation detection between extracted and original watermarking sequence, which including rotation, scaling and cropping by rearranging the pixel of the host image.
3.4.8 Extraction stage
Extraction Stage is the last stage of a watermarking scheme where in this stage, a watermark that is previously embedded into the host image is being extracted. Also, two evaluations will be involved at this stage. To reconstruct the watermark, the following steps has been involved whereby Figure 16 shows the flowchart of the reconstruction of watermark process in extraction stages in Algorithm2.

Algorithm 2 watermark process in extraction stages
3.4.9 Imperceptibility evaluation
Peak signal to noise ratio (PSNR) is used to measure the quality of result in this research. It measures the imperceptibility between the original image and watermarked image with Eq. (12) and (13).
𝑤ℎ𝑒𝑟𝑒
- 𝑚:
-
𝑖𝑚𝑎𝑔𝑒 𝑠𝑖𝑧𝑒 𝑜𝑓 𝑡ℎ𝑒 w𝑎𝑡𝑒𝑟𝑚𝑎𝑟𝑘 𝑎𝑛𝑑 ℎ𝑜𝑠𝑡 𝑖𝑚𝑎𝑔𝑒.
- 𝐼(𝑖,𝑗):
-
ℎ𝑜𝑠𝑡 𝑖𝑚𝑎𝑔𝑒 𝑝𝑖𝑥𝑒𝑙 𝑣𝑎𝑙𝑢𝑒.
- 𝐾(𝑖,𝑗):
-
𝑤𝑎𝑡𝑒𝑟𝑚𝑎𝑟𝑘 𝑖𝑚𝑎𝑔𝑒 𝑝𝑖𝑥𝑒𝑙 𝑣𝑎𝑙𝑢𝑒.
- 𝑀𝑆𝐸:
-
𝑚𝑒𝑎𝑛 𝑠𝑞𝑢𝑎𝑟𝑒 𝑒𝑟𝑟𝑜𝑟 𝑓𝑜𝑟 𝐼 𝑎𝑛𝑑 𝐾.
3.4.10 Robustness evaluation
In order to measure the level of robustness of a watermarking system, Bit Error Rate (BER) and Normalized Cross Correlation (NCC) are used [32]. These two measurements are adopted to assess the degree of similarity between the original embedded watermark and watermark after extracting. The main advantage of using NCC over traditional Cross Correlation (CC) is that it is less sensitive to linear changes in the amplitude of illumination of original watermark image and extracted watermark [6]. NCC formula was given by (Eq. (14)) below:
𝑤ℎ𝑒𝑟𝑒.
- 𝑊′(𝑥,𝑦):
-
𝑒𝑥𝑡𝑟𝑎𝑐𝑡𝑒𝑑 𝑤𝑎𝑡𝑒𝑟𝑚𝑎𝑟𝑘.
- 𝑊(𝑥,𝑦):
-
𝑤𝑎𝑡𝑒𝑟𝑚𝑎𝑟𝑘 𝑖𝑚𝑎𝑔𝑒.
Apart from NCC, the BER is being adopted to evaluate the similarity between original and extracted EPR watermark from the host DICOM image. It is measured by comparing the number of error or tampered bits received against the total number of bits extracted. The formula of BER is defined as Eq. (15):
𝑤ℎ𝑒𝑟𝑒
- 𝑊:
-
𝑜𝑟𝑖𝑔𝑖𝑛𝑎𝑙 𝐸𝑃𝑅 𝑤𝑎𝑡𝑒𝑟𝑚𝑎𝑟𝑘
- 𝑊′𝑖:
-
𝑒𝑥𝑡𝑟𝑎𝑐𝑡𝑒𝑑 𝐸𝑃𝑅 𝑤𝑎𝑡𝑒𝑟𝑚𝑎𝑟𝑘
- 𝑁:
-
𝑡ℎ𝑒 𝑙𝑒𝑛𝑔𝑡ℎ 𝑜𝑓 𝐸𝑃𝑅 𝑏𝑖𝑡𝑠 𝑎𝑓𝑡𝑒𝑟 𝑒𝑥𝑡𝑟𝑎𝑐𝑡𝑒𝑑.
Since the arithmetic operation in upper part of the formula is minus (−) which indicates the difference between 𝑊 and 𝑊′𝑖, the value of BER is directly proportional to the differences of two mentioned parameters. On top of that, value of BER will be zero if there are no any disparity in between or at most value of 1, means those two watermarks is totally different from each other.
4 Qualitative and quantitative experimental result
This section presents in detail the experimental results, analysis, and discussion against the accomplishment of the proposed objectives. The performance of the proposed methods from pre-processing stage, embedding stage, attacking stage to extraction stage which including contrast enhancement using histogram equalization, EPR watermark preparation, EBD zone segmentation, EBD zone decomposition using SLT, embedding sequence using enhance Knight Tour with heuristic preset rules, and results after intentional attack along with the evaluation results using various measurement as described in this section.
4.1 DICOM brain MRI images
A set of twenty (20) DICOM brain MRI images are being selected arbitrarily to evaluate the proposed watermarking scheme. The host images are in a gray scale format with a size of 512 × 512 pixels and 256 × 256 pixels. All the host images are represented by 16-bit depths. The brain MRI images are retrieved from BRAINIX database provided by OsiriX [26] where it is available for research and teaching purposes.
4.2 Pre-processing stage
In this section, all the pre-processing result will be shown here with a real- world medical image. EPR watermark preparation and EBD zone segmentation using Active Contour with the global region-based approach are the two main parts involved in this stage.
4.2.1 EPR watermarking preparation
As mentioned in the previous chapter, Electronic Patient Records (EPR) is the watermark that is embedded into the host image. The EPR information that has been selected for embedding fully respect to the DICOM ISO standard published by 2017 [26] in Basic Profile and found from all of the standard dataset images. Factors below whereby the EPR extracted and which going to embedded into host image: (a)Patient ID, (b) Patient Birth Date, (c)Patient Sex, (d) Patient Weight, (e)Accession Number, (f)Study Date, (g)Study Time, (h)Study ID, (i)Modality, (j)Study Description, (k)Institution Name, (l)Preferring Physician Name.
4.2.2 Embeddable zone (EBD) segmentation using active contour with global region
In this medical image watermarking research, a new concept of embedding zone is being introduced, namely Embeddable zone (EBD zone) and Non-embeddable zone (NEBD) instead of traditional whole host image in either spatial or frequency domain and general ROI and RONI embedding region. As the presence of a new concept of EBD and NEBD, directly, it will increase the security and integrity control of the DICOM images in terms of protecting the DICOM file from hacker or third party to extract or modify the watermark (Fig. 17).
Table 4 shows the result of EBD zone which segmented using Active Contour with the global region-based approach. Pixel covered per host image is calculated in percentage for each host image, the lowest EBD zone in twenty testing images is of 22.1207% whereby the highest EBD zone presented in the testing image is 62.2711% from MRI 20.
4.3 Embedding stage
In this stage, a new method of watermarking embedding technique is being proposed using Slantlet Transform onto EBD zone for increasing embedding capacity; Enhanced Knight Tour with preset heuristic rules for shuffling the sequence of watermark binary bits for increasing the security of the scheme; Dynamic Visibility Threshold Scalar, DVT is a new parameter taken account in embedding process for imperceptibility control.
4.3.1 Waterflow confusion using enhanced knight tour with heuristic preset rules
In this section, a small sample (6 × 6) of an enhanced version of Knight Tour with preset heuristic rules will be presented along with the comparison with other existing methods. As the Knight iterate and expand each time, more and more coefficients of the sub-band are being covered. Before the Knight Tour start, we already have a total of 12 coefficients covered (4 corner coefficients +8 interconnect coefficients). Knight Tour scans 36 coefficients in four expansions, and it stops (Table 5).
As a comparison, Table 6 below shows the execution time that found from previous significant study with time provided. The proposed method outperforms all of the previous studies on the term of execution time with a very outstanding result. The time needed for the proposed method is about less than 1 second to form a closed Knight Tour path.
This proposed method suggests an algorithm that able to shuffle the watermarking with shorter execution time by using three heuristic preset rules and the concept of structural Knight Tour. With the present of preset rules, the watermarking binary stream can be embedded into EBD SLT sub-band coefficient uniquely. Example of Enhanced Knight Tour with Heuristic Preset Rules on a 6 × 6 frequency coefficient sub-band is shown in Fig. 18.
4.3.2 Embedding with dynamic visibility threshold, DVT for imperceptibility control
In this section, the formation and calculation of the Dynamic Visibility Threshold, DVT will be shown with a sample image (MRI 1) from the standard dataset. Figure 19 illustrates how an optimal DVT is being calculated from the host image. The EBD zone which segmented from Active Contour with Global Region-Based Approach will undergo SLT Transform to generate LL, LH, HL and HH sub-band of each size is half from the EBD. As explained earlier (Section 3), LL and HH are not suitable for embedding from HVS perspective, LH and HL will be the interested sub- band coefficient for manipulation. Therefore, the difference between both selected coefficients is hereby calculated, and Third Quartile value is produced which is a new contribution in the watermarking field (Table 7).
For better understanding, MRI 1 from the standard dataset is used to demonstrate the SLT decomposition and Fig. 20 shows the HL and LH sub-band coefficient from Slantlet Transform of MRI 1.
As explained, Difference1 and Difference2 will be derived from HL and LH by using the Eqs. (6) and (7) from Section 3.3.3 in Section 3 previously.
Table 8 below shows the first quartile, median and third quartile value derived from Difference1 (MRI 1). At this stage, parameter value chosen as DVT for embedding process is hereby done calculated, and the most suitable quartile will be selected to function as DVT.
4.4 Extraction stage
After the host image was embedded with the watermark, the next process is to evaluate the robustness of the proposed scheme with the watermarking extraction. The robustness of the proposed method is evaluated by applying signal processing and geometric attacks on the watermarked images. The level of robustness is measured by using BER and NCC value.
4.5 Analysis of enhanced knight tour with heuristic preset rules with dynamic visibility threshold scalar in Slantlet transform algorithm
The proposed high imperceptibility with privacy control protection over EPR information technique is presented to embed EPR information from DICOM header directly into the DICOM using enhanced knight tour with heuristics preset, and the embedding process is done by altering the sub-band of SLT transform of EBD zone instead of convention substitution technique. Several experiments have been conducted during the embedding and also extraction stage in the aim of evaluating the proposed method. Those experiments are being included are:
-
(a).
Analysis of the imperceptibility of the watermarked image
-
(b).
Analysis of relationship between Dynamic Visibility Threshold, DVT and embedding capacity
-
(c).
Analysis of the robustness of the proposed algorithm
The results obtained from aforementioned experiments are analysed and discussed in the following section.
4.5.1 Analysis of the imperceptibility of watermarked image
The imperceptibility analysis against watermarked image is important after the host image (DICOM) undergoes the embedding stage. As per mentioned in Section 3, calculate the imperceptibility value between the original image before and after embedding using PSNR and SSIM value (Eqs. (9) and (10) respectively). PSNR is usually expressed in terms of decibel (dB) unit. If both the host image before and after embedding image are identical, then the value of PSNR will be infinity. In this analysis, EPR from the DICOM header is extracted and converted into a binary stream and then embedded into 20 host images of size of 512 × 512 pixels. The result of the imperceptibility of the watermarked host image is tabulated in Tables 8, 9 and 10.
As indicated in Fig. 21 below, as the host image consists of larger EBD zone, proposed watermarking scheme able to produce higher PSNR value ranging from 250.4459 to 269.6355. A green dotted line in Fig. 21 shows the trend line between two parameters with the linear equation.
4.5.2 Analysis of the robustness of the proposed algorithm
Another perspective of performance evaluation is robustness of the proposed watermarking algorithm. Medical image watermarking having a tradeoff between imperceptibility, embedding capacity and robustness of the watermark embedded. In other words, two of the other elements will be affected if one of them is being increased or decreased. The watermarked host image is subjected to various kinds of attacks which including geometric attacking, signal processing attacking and specialized knowledgeable attacking.
After the embedding process, ten types of attacks are applied on the watermarked host image. The sample of impacts produced by attacking on the watermarked image is shown in Fig. 22 with (k) as the original host image (Figs. 23 and 24).
BER and NCC are used to evaluate the robustness of the proposed method. The best DVT is chosen based on the BER and NCC value where the DVT can perform the best of BER = 0 and NCC = 1. Goes through the experiment and testing, the most suitable DVT is hence the Third Quartile. Third Quartile able to perform the desired result where when it is applied to all host images, BER and NCC showing 0 and 1 respectively as noted in Tables 11 and 12 below.
In terms of BER for the robustness evaluation, proposed method able to suffer from the rotation attacks with average BER value of 0.0091 and crop attacks of zero. Furthermore, Gaussian noise having the most impact against the watermark in the proposed method with average BER value of 0.5116 to 0.5688, followed by blur filter attack and scaling attacks with BER value ranging from 0.4593 to 0.5203 and 0.4516 to 0.4990. Both BER and NCC evaluation shows (Tables 13 and 14) that the proposed method is not robust to Gaussian Noise, blur filter and scaling attacks. This is because Gaussian Noise is disturbing the statistical pixel value of its probability density function. The mean and standard deviation is being employed in adding the noise into host image while the third quartile is used as a parameter in thresholding to determine the strength of watermarking. On top of that, for those host image having left skewed normal distribution, i.e., the median value is closed with third quartile value, the Gaussian noise will have the chance to tamper the watermark embedded, consequence, more coefficients of sub-band are disturbed by the noise. As a result, more bits are tempered by the noise making BER value is increased.
Based on the experimental result using twenty (20) host images, as shown in Fig. 25, all host images (i.e., brain MRI images) are resilient to Salt & Pepper Noise and Cropping attacking. The original watermark can be extracted albeit the watermarked image is being cropped.
As illustrated in Fig. 26 below, there are seven image attacks out of total ten intentional attack produce a favorable result higher than acceptance value 0.7. This is a very encouraging result that enhanced version of Knight Tour with a heuristic preset rule which ported into Slantlet Transform coupled with DVT is robust to make the watermark suffer from the attacking applied on top of it.
Across all the noise attacking which adding disturbance in terms of the pixel value, the proposed algorithm able to withstand these noises attacking with an acceptable value of NCC 0.7. However, the proposed method is not robust against the other attacking of scaling, blur filter and median filter with average NCC value of 0.4914, 0.4271 and 0.6495 respectively which lower than acceptance rate.
Within twelve (12) attacking, scaling attack (scaling factor: 0.5) having the second most crucial attack on the watermark of the proposed method. This is due to the Slantlet Transform that has been implemented using a fix SLT Matrix (as illustrated in Fig. 8) of size 32 × 32 for the host image decomposition. In considering of a fix SLT Matrix is used, the size of the host image become a vital role in the watermarking scheme which currently only able to handle two types of host image size which is 256 × 256 and 512 × 512 as presented in the standard database. This watermarking scheme becomes fragile if the size of the watermarked image is changed and as a consequence, the watermark cannot be retrieved correctly from the watermarked image. As depicted in Tables 12 and 13, result for both BER and NCC gradually change from the first quartile, median and simultaneously achieve 0 and 1 respectively at third quartile which making the latter being selected as the best DVT in this research.
4.6 A comparative study
In this section, the proposed watermarking scheme is compared with several medical image watermarking schemes with high imperceptibility: [5, 8, 9, 33]. The reason for carrying out the comparative study is to evaluate and investigate the indisputable performance of the proposed method with real contemporary method. In this context, it is actually hard to compare and correlate proposed method with other methods as different method implement different techniques in several domains. Likewise, various of the method applied to different host images as well as offering different function such as content authentication, tamper detection and imperceptibility. As a consequence of many scenarios of targets and aims, this comparative study conducted on the performance of each scheme in terms of visual quality, robustness and a few factors of the watermarking scheme as shown below (Table 15).
5 Conclusion
The primary focus of this research revolves around achieving a watermarking scheme that ensures both visual quality (imperceptibility) and robustness, aiming to enhance overall security. Common embedding methods, which embed watermarks into widely recognized regions of the host image, often struggle to strike a balance between imperceptibility and robustness. This limitation creates a vulnerability that allows third parties to potentially guess the watermarking sequence and location. To address these concerns and provide confidentiality and content authentication for host medical images, several innovations are proposed. Specifically, in the case of brain MRI images, Electronic Patient Record (EPR) information is extracted from the DICOM header and directly embedded into the image itself. This is achieved by introducing the novel concepts of Embeddable Zone (EBD) and Non-Embeddable Zone (NEBD), along with an innovative embedding method. The proposed method incorporates statistical mathematics through an enhanced version of the Knight Tour algorithm, utilizing four Knights and heuristic preset rules. The experimental results include comprehensive discussions and analyses of the proposed method, specifically focusing on visual quality and robustness. The outcomes validate the effectiveness and potential of the proposed method in maintaining high imperceptibility according to the Human Visual System (HVS), while preserving the EPR information and enhancing the security of the embedded watermark. Throughout the experiments, the proposed method exhibits a remarkable balance between imperceptibility and robustness, evidenced by an average Peak Signal-to-Noise Ratio (PSNR) of 260.4767 dB, average Bit Error Rate (BER) of 0.2573, and a high Normalized Cross-Correlation (NCC) value of up to 0.7262. Moreover, comparative studies reveal that the proposed scheme significantly outperforms other methods in terms of visual quality and robustness. These findings reinforce the capability and superiority of the proposed watermarking method, providing a more secure solution for medical image protection.
Data availability
The DICOM MRI dataset utilized in this study was obtained from BRAINIX, a medical database provided by OsiriX, Pixmeo SARL (http://www.osirix-viewer.com/resources/dicom-image-library/).
References
Al-Qershi OM, Khoo BE (2011) Authentication and data hiding using a hybrid ROI-based watermarking scheme for DICOM images. J Digit Imaging 24(1):114–125
Badran EF, Sharkas MA, Attallah OA (2009) Multiple watermark embedding scheme in wavelet-spatial domains based on ROI of medical images. National Radio Science Conference, pp 1–8
Badshah G et al (2016) Watermark compression in medical image watermarking using Lempel-Ziv-Welch (LZW) lossless compression technique. J Digit Imaging 29(2):216–225
Coatrieux G et al (2006) A low distorsion and reversible watermark: application to angiographic images of the retina. In 2005 IEEE engineering in medicine and biology 27th annual conference. IEEE
Coatrieux G et al (2007) Mixed reversible and RONI watermarking for medical image reliability protection. In 2007 29th annual international conference of the IEEE engineering in medicine and biology society. IEEE
Coatrieux G, Maitre H, Sankur B (2001) Strict integrity control of biomedical images. in Security and watermarking of multimedia contents III. International Society for Optics and Photonics
Cox I et al (2007) Digital watermarking and steganography: Morgan kaufmann
Das S, Kundu MK (2013) Effective management of medical information through ROI-lossless fragile image watermarking technique. Comput Methods Prog Biomed 111(3):662–675
Dong C, Li J, Chen Y-w (2012) A DWT-DCT based robust multiple watermarks for medical image. In 2012 symposium on photonics and optoelectronics. IEEE
Dhavale SV, Patnaik L (2010) High capacity, robust lossless EPR data hiding using CDCS with ROI tamper detection. In: International Conference on Computer and Communication Technology (ICCCT), pp 108–112. https://doi.org/10.1109/ICCCT.2010.5640422
Fotopoulos V, Stavrinou ML, Skodras AN (2008) Medical image authentication and self-correction through an adaptive reversible watermarking technique. In: Proc. 8th IEEE Int. Conference on BioInformatics and BioEngineering, Athens, pp 1–5. https://doi.org/10.1109/BIBE.2008.4696803
Garg K (2015) Digital watermarking: potential challenges and issues. Int J Sci Eng Comput Technol 5(3):48
Giakoumaki A, Pavlopoulos S, Koutsouris D (2004) A multiple watermarking scheme applied to medical image management. In the 26th annual international conference of the IEEE engineering in medicine and biology society. IEEE
Giakoumaki A, Pavlopoulos S, Koutsouris D (2004) A multiple watermarking scheme applied to medical image management. In: The 26th Annual International Conference of the IEEE Engineering in Medicine and Biology Society, vol 2, pp 3241–3244
Giakoumaki A, Pavlopoulos S, Koutsouris D (2006) Secure and efficient health data management through multiple watermarking on medical images. Med Biol Eng Comput 44(8):619–631
Guo X, Zhuang TG (2009) A region-based lossless watermarking scheme for enhancing security of medical data. J Digital Imaging 22:53–64
Hamidovic H, Kabil J (2011) An introduction to information security management in health care organizations. ISACA Journal 5:2–3
Kundu MK, Das S (2010) Lossless ROI medical image watermarking technique with enhanced security and high payload embedding. In: 2010 20th International Conference on Pattern Recognition. IEEE, pp 1457–1460
Kundur D, Hatzinakos D (1999) Digital watermarking for telltale tamper proofing and authentication. Proc IEEE 87(7):1167–1180
Li J, Liu Y (2013) The medical image watermarking algorithm based on dwt-dft and logistic map. In: Conference of the 2nd International Conference on Computer Science and Electronics Engineering (ICCSEE 2013). Atlantis Press, pp 337–340
Mehta MK (2012) Fake insurance claims may invite police action. Retrieved February 21, 2018, from https://timesofindia.indiatimes.com/city/mumbai/Fakeinsurance-claims-may-invite-police-action/articleshow/12957634.cms
Memon NA, Gilani SAM (2008) NROI watermarking of medical images for content authentication. In: 2008 IEEE International Multitopic Conference. IEEE, pp 106–110
Memon, N. A., & Gilani, S. A. M. (2008). NROI watermarking of medical images for content authentication. In 2008 IEEE International Multitopic Conference (pp. 106–110). IEEE.
Mousavi SM, Naghsh A, Abu-Bakar SAR (2014) Watermarking techniques used in medical images: a survey. J Digit Imaging 27(6):714–729. https://doi.org/10.1007/s10278-014-9700-5
Nakhaie AA, Shokouhi SB (2011, May) No reference medical image quality measurement based on spread spectrum and discrete wavelet transform using ROI processing. In: 2011 24th Canadian Conference on Electrical and Computer Engineering (CCECE). IEEE, pp 000121–000125
NEMA., Security and System Management Profiles (2017) In The DICOM Standard: p. 3065–3206
Nyeem H, Boles W, Boyd C (2013) A review of medical image watermarking requirements for teleradiology. J Digit Imaging 26:326–343
Osborne D, Abbott D, Sorell M, Rogers D (2004) Multiple embedding using robust watermarks for wireless medical images. In: Proceedings of the 3rd international conference on Mobile and ubiquitous multimedia - MUM ’04. ACM Press, New York, pp 245–250. https://doi.org/10.1145/1052380.1052414
Parberry I (1997) An efficient algorithm for the Knight’s tour problem. Discrete Appl Math 73(3):251–260. https://doi.org/10.1016/S0166-218X(96)00010-8
Pradhan C, Rath S, Bisoi AK (2012) Non blind digital watermarking technique using DWT and cross chaos. Procedia Technol 6:897–904
Raúl RC, Claudia FU, Trinidad-Blas GDJ (2007) Data hiding scheme for medical images. In: 17th International Conference on Electronics, Communications and Computers, CONIELECOMP’07, Proceedings. IEEE, pp 32–32. https://doi.org/10.1109/CONIELECOMP.2007.14
Shannon CE (1949) Communication in the presence of noise. Proc IRE 37(1):10–21
Solanki N, Malik SK, Chhikara S (2014) Roni medical image watermarking using dwt and rsa. Int J Comput Appl 96(9)
Tan CK, Ng JC, Xu X, Poh CL, Guan YL, Sheah K (2011) Security protection of DICOM medical images using dual-layer reversible watermarking with tamper detection capability. J Digit Imaging 24:528–540
Tao H, Chongmin L, Zain JM, Abdalla AN (2014) Robust image watermarking theories and techniques: A review. J Appl Res Technol 12(1):122–138. https://doi.org/10.1016/S1665-6423(14)71612-8
Vasudeva K, Singh PK, Singh Y (2016) A methodical review on issues of medical image management system with watermarking approach
Wakatani A (2002) Digital watermarking for ROI medical images by using compressed signature image. In proceedings of the 35th annual Hawaii international conference on system sciences. IEEE
Wee TC et al (2020) High imperceptibility medical image watermarking scheme based on Slantlet transform by using dynamic visibility threshold. In 2020 6th international conference on interactive digital media (ICIDM). IEEE
Wong YL et al (2021) A comparative study on medical image watermarking using hybrid approach and rivagan. in International Conference on Digital Transformation and Applications (ICDXA)
Woo C, Du J, Pham B (2005) Multiple watermark method for privacy control and tamper detection in medical images. APRS Workshop on Digital Image Computing (WDIC). Retrieved from http://www.aprs.org.au/wdic2005/fullproceedings.pdf
Zain JM, Baldwin LP, Clarke M (2004) Reversible watermarking for authentication of DICOM images. In the 26th annual international conference of the IEEE engineering in medicine and biology society. IEEE
Zhu S, Liu J (2009) An optimal adaptive quantization index modulation watermarking algorithm. Chinese Opt Lett 7(7):580–584
Funding
This paper received no specific grant from any funding agency in the public, commercial, or not-for-profit sectors.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
We certify that there is no actual or potential conflict of interest in relation to this manuscript.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Kolivand, H., Wee, T.C., Asadianfam, S. et al. High imperceptibility and robustness watermarking scheme for brain MRI using Slantlet transform coupled with enhanced knight tour algorithm. Multimed Tools Appl 83, 22221–22260 (2024). https://doi.org/10.1007/s11042-023-16459-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-16459-7