Abstract
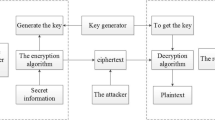
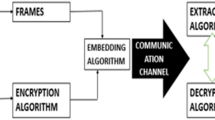
Nowadays coverless steganography has fascinated huge attentiveness in the field of information security as it does not modify the transmission carrier of the secret information so it won’t be detected by steganalysis algorithms constructively. Yet, the present techniques have a limited capacity for transferring bits and a few of them use deep neural networks, plus most coverless techniques don’t use videos as carriers and benefit from the privilege of having more abundant content. To address these problems, a coverless video steganography technique is proposed that has unlimited hiding capacity and provides effective resistance against different noises. This paper utilizes two different deep neural networks to alter the video frames to new ones and extract information. The first one is a deep high-resolution network that segments the input frame and converts it to a label map. Then with a generative adversarial network, the semantic label is synthesized into a new frame from which the receiver acquires information in a way that makes it independent of using other frames. The sender should also dispatch the receiver some auxiliary info about each frame. The method is evaluated on two popular datasets: common objects in context (COCO), and the densely annotated video segmentation (DAVIS) dataset. Ostensibly, this is the first method with infinite capacity per each video frame. The proposed has great noise robustness of more than 29% compared to its rival on the DAVIS dataset, and also about 12% stronger against common noise compared to some state of art methods. Besides this technique can effectively resist steganalysis tools. Some methods have also been introduced to limit the effect of noise in the proposed method.










Similar content being viewed by others
Change history
20 December 2023
A Correction to this paper has been published: https://doi.org/10.1007/s11042-023-17901-6
References
Ahmed, B. T. (2021). A systematic overview of secure image steganography. International Journal of Advances in Applied Sciences (IJAAS) ISSN, 2252(8814), 8814.
Al Hussien SS, Mohamed MS, Hafez EH (2021) Coverless image steganography based on optical mark recognition and machine learning. IEEE Access 11(9):16522–16531
Alshinina R, Elleithy KM (n.d.) A High Payload Video Steganography algorithm in DWT Domain based on BCH (15, 11)
Anggriani K et al (2023) A high-capacity coverless information hiding based on the lowest and highest image fragments. Electronics 12(2):395
Barra S, Carta SM, Corriga A, Podda AS, Recupero DR (2020) Deep learning and time series-to-image encoding for financial forecasting. IEEE/CAA J Autom Sin 7(3):683–692
Barz B, Denzler J (2020) Do we train on test data? Purging cifar of near-duplicates. J Imaging 6(6):41
Boroumand M, Chen M, Fridrich J (2018) Deep residual network for steganalysis of digital images. IEEE Transactions on Information Forensics and Security 14(5):1181–1193
Cao Y, Zhou Z, Sun X, Gao C (2018) Coverless information hiding based on the molecular structure images of material. Comput Mater Continua 54(2):197–207
Din R, Samsudin A (2009) Digital steganalysis: computational intelligence approach. International Journal of Computers 3(1):161–170
Douglas M, Bailey K, Leeney M, Curran K (2018) An overview of steganography techniques applied to the protection of biometric data. Multimedia Tools and Applications 77(13):17333–17373
Duan X, Song H (2018) Coverless information hiding based on generative model. arXiv preprint arXiv:1802.03528. 2018 Feb 10
Duta IC, Liu L, Zhu F, Shao L (2021) Improved residual networks for image and video recognition. In: 2020 25th international conference on pattern recognition (ICPR). IEEE, pp 9415-9422
Fararni KA, Nafis F, Aghoutane B, Yahyaouy A, Riffi J, Sabri A (2021) Hybrid recommender system for tourism based on big data and AI: a conceptual framework. Big Data Mini Anal 4(1):47–55. https://doi.org/10.26599/BDMA.2020.9020015
Feng Q, He D, Liu Z, Wang H, Choo KK (2020) SecureNLP: a system for multi-party privacy-preserving natural language processing. IEEE Trans Inf Forensic Secur 25(15):3709–3721
He K, Zhang X, Ren S, Sun J (2016) Deep residual learning for image recognition. In: Proceedings of the IEEE conference on computer vision and pattern recognition, pp 770–778
Hu D, Wang L, Jiang W, Zheng S, Li B (2018) A novel image steganography method via deep convolutional generative adversarial networks. IEEE Access 4(6):38303–38314
Huang K, Sun T, Jiang X, Dong Y, Fang Q (2020) Combined features for steganalysis against PU partition mode-based steganography in HEVC. Multimedia Tools and Applications 79(41):31147–31164
Jenifer JM, Ratna SR, Loret JS, Gethsy DM (2018) A survey on different video steganography techniques. In2018 2nd international conference on trends in electronics and informatics (ICOEI) 2018 may 11 (pp. 627-632). IEEE
Kim WJ, Youn CH (2021) Cooperative scheduling schemes for explainable DNN acceleration in satellite image analysis and retraining. IEEE Trans Parallel Distribute Syst 33(7):1605–1618
Kwon OY, Lee MH, Guan C, Lee SW (2019) Subject-independent brain–computer interfaces based on deep convolutional neural networks. IEEE Trans Neural Netw Learn Syst 31(10):3839–3852
Li Q, Feng G, Ren Y, Zhang X (2021) Embedding probability guided network for image steganalysis. IEEE Signal Processing Letters 28:1095–1099
Li J, Wang K, Jia X (2023) A coverless audio steganography based on generative adversarial networks. Electronics 12(5):1253
Liu Q, Xiang X, Qin J, Tan Y, Tan J, Luo Y (2020) Coverless steganography based on image retrieval of DenseNet features and DWT sequence mapping. Knowl-Based Syst 15(192):105375
Liu Q et al (2020) Coverless image steganography based on DenseNet feature mapping. EURASIP J Image Vid Process 2020:1–18
Lu S-P et al (2021) Large-capacity image steganography based on invertible neural networks. Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition
Luo Y, Qin J, Xiang X, Tan Y, Liu Q, Xiang L (2020) Coverless real-time image information hiding based on image block-matching and dense convolutional network. J Real-Time Image Proc 17(1):125–135
Luo Y, Qin J, Xiang X, Tan Y (2020) Coverless image steganography based on multi-object recognition. IEEE Trans Circ Syst Vid Technol
Lusson F, Bailey K, Leeney M, Curran K (2013) A novel approach to digital watermarking, exploiting color spaces. Signal Processing 93(5):1268–1294
Masoumi M, Amiri S (2013) A blind scene-based watermarking for video copyright protection. AEU-Int J Electron Commun 67(6):528–535
Meng L, Jiang X, Zhang Z, Li Z, Sun T (2020) Coverless Video Steganography based on Maximum DC Coefficients. arXiv preprint arXiv:2012.06809
Mstafa RJ, Elleithy KM (2014) A highly secure video steganography using hamming code (7, 4). In IEEE Long Island systems, applications and technology (LISAT) conference 2014 2014 may 2 (pp. 1-6). IEEE
Mstafa RJ, Younis YM, Hussein HI, Atto M (2020) A new video steganography scheme based on Shi-Tomasi corner detector. IEEE Access 3(8):161825–161837
Pan N, Qin J, Tan Y, Xiang X, Hou G (2020) A video coverless information hiding algorithm based on semantic segmentation. Eurasip J Image Video Process 2020(1):1–18
Peng F, Chen G, Long M (2022) A robust coverless steganography based on generative adversarial networks and gradient descent approximation. IEEE Trans Circ Syst Vid Technol 32(9):5817–5829
Qian Z, Feng G, Zhang X, Wang S (2011) Image self-embedding with high-quality restoration capability. Digit Signal Process 21(2):278–286
Qin J et al (2020) Coverless image steganography based on generative adversarial network. Mathematics 8(9):1394
Ruan S, Qin Z (2017) Coverless covert communication based on gif image. Commun Technol 50(7):1506–1510
Shyla MK, Kumar KS, Das RK (2021) Image steganography using genetic algorithm for cover image selection and embedding. Soft Computing Lett 1(3):100021
Soundararajan, D, Ramakrishnan S (2023) Coverless data hiding in VoIP based on DNA steganography with authentication. The Int Arab J Inf Technol 20(2)
Sun K, Xiao B, Liu D, Wang J (2019) Deep high-resolution representation learning for human pose estimation. In Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition 2019 (pp. 5693–5703)
Sun K, Zhao Y, Jiang B, Cheng T, Xiao B, Liu D, Mu Y, Wang X, Liu W, Wang J (2019) High-resolution representations for labeling pixels and regions. arXiv preprint arXiv:1904.04514. 2019 Apr 9
Sushko V, Schönfeld E, Zhang D, Gall J, Schiele B, Khoreva A (2020) You Only Need Adversarial Supervision for Semantic Image Synthesis. arXiv preprint arXiv:2012.04781. 2020 Dec 8
Tan Y, Qin J, Xiang X, Zhang C, Wang Z (2021) Coverless steganography based on motion analysis of video. Secur Commun Netw 22:2021
Valueva MV, Nagornov NN, Lyakhov PA, Valuev GV, Chervyakov NI (2020) Application of the residue number system to reduce hardware costs of the convolutional neural network implementation. Math Comput Simul 1(177):232–243
Wang XY, Wang CP, Yang HY, Niu PP (2013) A robust blind color image watermarking in quaternion Fourier transform domain. J Syst Softw 86(2):255–277
Wang J, Zheng Y, Wang M, Shen Q, Huang J (2021) Object-scale adaptive convolutional neural networks for high-spatial resolution remote sensing image classification. IEEE J Sel Top Appl Earth Obs Remote Sens 14:283–299. https://doi.org/10.1109/JSTARS.2020.3041859
Xu X, Dong J, Tan T (2012) Universal spatial feature set for video steganalysis. In: 19th IEEE International Conference on Image Processing, Orlando, pp 245–248. https://doi.org/10.1109/ICIP.2012.6466841
Ye J, Ni J, Yi Y (2017) Deep learning hierarchical representations for image steganalysis. IEEE Trans Inf Forensic Secur 12(11):2545–2557
Yin P, Yuan R, Cheng Y, Wu Q (2020) Deep guidance network for biomedical image segmentation. IEEE Access 8:116106–116116. https://doi.org/10.1109/ACCESS.2020.3002835
Yuan C, Xia Z, Sun X (2017) Coverless image steganography based on SIFT and BOF. J Int Technol 18(2):435–442
Zhai L, Wang L, Ren Y (2019) Universal detection of video steganography in multiple domains based on the consistency of motion vectors. EEE Trans Inf Forensics Secur 24(15):1762–1777
Zhang X, Peng F, Long M (2018) Robust coverless image steganography based on DCT and LDA topic classification. IEEE Trans Multimed 20(12):3223–3238
Zheng S, Wang L, Ling B, Hu D (2017) Coverless information hiding based on robust image hashing. International conference on intelligent computing 2017 Aug 7 (pp. 536–547). Springer, Cham
Zhou B, Zhao H, Puig X, Fidler S, Barriuso A, Torralba A (2017) Scene parsing through ade20k dataset. InProceedings of the IEEE conference on computer vision and pattern recognition 2017 (pp. 633–641)
Zhou Z, Mu Y, Wu QJ (2019) Coverless image steganography using partial-duplicate image retrieval. Soft Comput 23(13):4927–4938
Zhou Z et al (2019) faster-RCNN based robust coverless information hiding system in cloud environment. IEEE. Access 7:179891–179897
Zhou Z, Sun H, Harit R, Chen X, Sun X (2015) Coverless image steganography without embedding. In: Cloud Computing and Security: First International Conference, ICCCS. Springer International Publishing, Nanjing. Revised Selected Papers 1, pp 123–132
Zou L, Sun J, Gao M, Wan W, Gupta BB (2019) A novel coverless information hiding method based on the average pixel value of the sub-images. Multimed Tools Appl 78(7):7965–7980
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflicts of interest
All authors have no conflicts of interest to disclose.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
The original online version of this article was revised: The original publication of this article contains an error in the first affiliation.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Jahromi, Z.T., Hasheminejad, S.M.H. & Shojaedini, S.V. Deep learning semantic image synthesis: a novel method for unlimited capacity, high noise resistance coverless video steganography. Multimed Tools Appl 83, 17047–17065 (2024). https://doi.org/10.1007/s11042-023-16278-w
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-16278-w