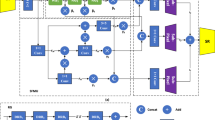
Abstract
Steganography technology can effectively conceal secret information in the carrier medium, enable covert communication without drawing the attention of a third party, and ensure the safe and reliable transmission of confidential information. However, with the development of steganalysis technology, steganalysers based on deep learning can accurately identify the modification traces in the steganographic cover, which poses a huge threat to steganography. Therefore, the focus of the research is how to reduce the detection accuracy of deep learning-based steganalyzer. In this work, we design an Adversarial Example STeganography (AEST) method, which hides the secret grayscale image into the color cover image to obtain the stego image that is difficult to distinguish by the naked eye. Then, the attack module composed of the FGM and PGD adversarial attacks added small perturbations to generate adversarial steganographic images, reducing the detection accuracy of the steganalyzer. In addition, to reduce the impact of adversarial examples on secret information recovery, we designed a decoder based on adversarial training and the generative adversarial network. Finally, the experimental results show that AEST has a good performance of anti-steganalysis ability. For example, the adversarial steganographic image based on PGD attack can make the detection error rate of the XuNet steganalyzer reach 63.511%.











Similar content being viewed by others
Availability of data and materials
The datasets generated during and/or analysed during the current study are available from the corresponding author on reasonable request.
Code Availability
The code during the current study are available from the corresponding author on reasonable request.
References
Baluja S (2017) Hiding images in plain sight: deep steganography. Advances in Neural Information Processing Systems, 30
Brock A, Donahue J, Simonyan K (2018) Large scale gan training for high fidelity natural image synthesis. arXiv:1809.11096
Chan C-K, Cheng L-M (2004) Hiding data in images by simple lsb substitution. Patt Recogn 37(3):469–474
Chaumont M (2020) Deep learning in steganography and steganalysis. Digital Media Steganography
Donahue J, Krähenbühl P, Darrell T (2016) Adversarial feature learning. arXiv:1605.09782
Frid-Adar M, Diamant I, Klang E, Amitai M, Goldberger J, Greenspan H (2018) Gan-based synthetic medical image augmentation for increased cnn performance in liver lesion classification. Neurocomputing 321:321–331
Ghamizi S, Cordy M, Papadakis M, Traon Y L (2021) Evasion attack steganography: turning vulnerability of machine learning to adversarial attacks into a real-world application. In: 2021 IEEE/CVF International Conference on Computer Vision Workshops (ICCVW), pp 31–40
Ghosal S K, Chatterjee A, Sarkar R (2021) Image steganography based on kirsch edge detection. Multimed Syst 27(1):73–87
Goodfellow I, Pouget-Abadie J, Mirza M, Xu B, Warde-Farley D, Ozair S, Courville A, Bengio Y (2020) Generative adversarial networks. Commun ACM 63(11):139–144
Goodfellow I J, Shlens J, Szegedy C (2014) Explaining and harnessing adversarial examples. arXiv:1412.6572
Holub V, Fridrich J J (2012) Designing steganographic distortion using directional filters. In: 2012 IEEE International Workshop on Information Forensics and Security (WIFS), pp 234–239
Holub V, Fridrich J J, Denemark T (2014) Universal distortion function for steganography in an arbitrary domain. EURASIP J Inf Secur 2014:1–13
Huang G B, Mattar M A, Berg T L, Learned-Miller E (2008) Labeled faces in the wild: a database forstudying face recognition in unconstrained environments
Hussain M, Wahab A W A, Idris Y I B, Ho ATS, Jung K-H (2018) Image steganography in spatial domain: a survey. Signal Process: Image Commun 65:46–66
Karampidis K, Kavallieratou E, Papadourakis G (2018) A review of image steganalysis techniques for digital forensics. J Inform Secur Applic 40:217–235
Kharrazi M, Sencar H T, Memon N (2006) Cover selection for steganographic embedding. In: 2006 International conference on image processing. IEEE, pp 117–120
Kurakin A, Goodfellow I J, Bengio S (2016) Adversarial examples in the physical world. arXiv:1607.02533
Li B, Wang M, Huang J, Li X (2014) A new cost function for spatial image steganography. In: 2014 IEEE International Conference on Image Processing (ICIP), pp 4206–4210
Liao X, Yin J, Chen M, Qin Z (2020) Adaptive payload distribution in multiple images steganography based on image texture features. IEEE Trans Dependable Secure Comput 19(2):897–911
Liu Y, Liu S, Wang Y, Zhao H, Liu S (2019) Video steganography: a review. Neurocomputing 335:238–250
Liu J, Ke Y, Zhang Z, Lei Y, Li J, Zhang M, Yang X (2020) Recent advances of image steganography with generative adversarial networks. IEEE Access 8:60575–60597
Liu X, Ma Z, Ma J, Zhang J, Schaefer G, Fang H (2022) Image disentanglement autoencoder for steganography without embedding. In: Proceedings of the IEEE/CVF conference on computer vision and pattern recognition, pp 2303–2312
Madry A, Makelov A, Schmidt L, Tsipras D, Vladu A (2018) Towards deep learning models resistant to adversarial attacks. arXiv:1706.06083
Pan W, Yin Y, Wang X, Jing Y, Song M (2021) Seek-and-hide: adversarial steganography via deep reinforcement learning. IEEE Trans Pattern Anal Mach Intell 44(11):7871–7884
Pevnỳ T, Filler T, Bas P (2010) Using high-dimensional image models to perform highly undetectable steganography. In: Information hiding: 12th international conference, IH 2010, Calgary, AB, Canada, June 28-30, 2010, revised selected papers 12. Springer, pp 161–177
Qian Y, Dong J, Wang W, Tan T (2015) Deep learning for steganalysis via convolutional neural networks. In: Electronic imaging
Qian Y, Dong J, Wang W, Tan T (2016) Learning and transferring representations for image steganalysis using convolutional neural network. In: 2016 IEEE International Conference on Image Processing (ICIP). IEEE, pp 2752–2756
Reinel T-S, Raul R-P, Gustavo I (2019) Deep learning applied to steganalysis of digital images: a systematic review. IEEE Access 7:68970–68990
Ruan F, Zhang X, Zhu D, Xu Z, Wan S, Qi L (2020) Deep learning for real-time image steganalysis: a survey. J Real-Time Image Proc 17:149–160
Subhedar M S, Mankar V H (2014) Current status and key issues in image steganography: a survey. Comput Sci Rev 13:95–113
Subramanian N, Elharrouss O, Al-Maadeed S, Bouridane A (2021) Image steganography: a review of the recent advances. IEEE access 9:23409–23423
Szegedy C, Vanhoucke V, Ioffe S, Shlens J, Wojna Z (2016) Rethinking the inception architecture for computer vision. In: 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), pp 2818–2826
Tang W, Tan S, Li B, Huang J (2017) Automatic steganographic distortion learning using a generative adversarial network. IEEE Signal Process Lett 24(10):1547–1551
Tang W, Li B, Tan S, Barni M, Huang J (2019) Cnn-based adversarial embedding for image steganography. IEEE Trans Inf Forensics Secur 14:2074–2087
Tang W, Li B, Barni M, Li J, Huang J (2020) An automatic cost learning framework for image steganography using deep reinforcement learning. IEEE Trans Inf Forensics Secur 16:952–967
Wang Z, Bovik A C, Sheikh H R, Simoncelli E P (2004) Image quality assessment: from error visibility to structural similarity. IEEE Trans Image Process 13:600–612
Wu S, Zhong S, Liu Y (2018) Deep residual learning for image steganalysis. Multimed Tools Applic 77:10437–10453
Wu C, Huang F, Dai J, Zhou N (2022) Quantum susan edge detection based on double chains quantum genetic algorithm. Physica A 605:128017
Xu G (2017) Deep convolutional neural network to detect j-uniward. In: Proceedings of the 5th ACM workshop on information hiding and multimedia security
Yang J, Ruan D, Huang J, Kang X, Shi Y-Q (2019) An embedding cost learning framework using gan. IEEE Trans Inf Forensics Secur 15:839–851
Ye J, Ni J, Yi Y (2017) Deep learning hierarchical representations for image steganalysis. IEEE Trans Inf Forensics Secur 12:2545–2557
Yedroudj M, Comby F, Chaumont M (2018) Yedroudj-net: an efficient cnn for spatial steganalysis. In: 2018 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP). IEEE, pp 2092–2096
Zeng J, Tan S, Li B, Huang J (2018) Large-scale jpeg image steganalysis using hybrid deep-learning framework. IEEE Trans Inf Forensics Secur 13:1200–1214
Zhang K A, Cuesta-Infante A, Xu L, Veeramachaneni K (2019) Steganogan: high capacity image steganography with gans. arXiv:1901.03892
Zhang C, Benz P, Karjauv A, Kweon I S (2021) Universal adversarial perturbations through the lens of deep steganography: towards a fourier perspective. In: Proceedings of the AAAI conference on artificial intelligence, vol 35, pp 3296–3304
Zhou N-R, Zhang T-F, Xie X-W, Wu J-Y (2023) Hybrid quantum–classical generative adversarial networks for image generation via learning discrete distribution. Signal Process: Image Commun 110:116891
Zhu J-Y, Park T, Isola P, Efros A A (2017) Unpaired image-to-image translation using cycle-consistent adversarial networks. In: Proceedings of the IEEE international conference on computer vision, pp 2223–2232
Funding
Nofunds, grants, or other support was received.
Author information
Authors and Affiliations
Contributions
All authors contributed to the study conception and design. Material preparation, data collection and analysis were performed by Ye Peng, GuoBin Fu, Qi Yu, YingGunag Luo, Jia Hu and ChaoFan Duan. The first draft of the manuscript was written by Ye Peng and all authors commented on previous versions of the manuscript. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors have no competing interests to declare that are relevant to the content of this article.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Peng, Y., Fu, G., Yu, Q. et al. Enhancing the anti-steganalysis ability of steganography via adversarial examples. Multimed Tools Appl 83, 6227–6247 (2024). https://doi.org/10.1007/s11042-023-15306-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-15306-z