Abstract
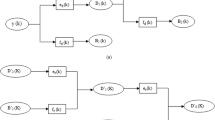
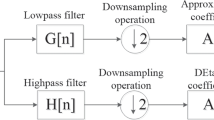
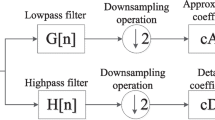
In this paper, a blind dual image watermarking scheme for copyright protection, tamper proofing and self-recovery is proposed. For purpose of copyright protection, we use binary handwritten signature, a high correlative biometric to owner as robust watermark, and embed it into hybrid domain constructed by dual tree complex wavelet transform (DT-CWT) and discrete cosine transform (DCT). For purpose of tamper proofing and self-recovery, source encoding output bits generated by set partitioning in hierarchical trees (SPIHT) encoding are embedded into image based on least significant bits (LSB) replacement, moreover, in order to enhance the robustness of self-recovery, repeated encoding technique is adopted, and hash-based check bits are used for tamper proofing. Experimental results indicate the proposed watermarking mechanism can withstand various image processing attacks, accurately locate and recover the tampered area of an image, especially it has the ability of tamper discrimination that other existing schemes do not have. It can find application for joint ownership and content authentication synchronously.















Similar content being viewed by others
Data Availability
The raw data required to reproduce the above finding cannot be shared at this time as the data also forms part of an ongoing study.
References
Ahmad F, Cheng LM (2018) Authenticity and copyright verification of printed images. Signal Processing, pp 322–335
Ahmaderaghi B, Kurugollu F, Rincon JMD et al (2018) Blind image watermark detection algorithm based on discrete shearlet transform using statistical decision theory. IEEE Trans Comput Imag 4:46–59
Ansari IA, Pant M (2017) Multipurpose image watermarking in the domain of DWT based on SVD and ABC. Pattern Recogn Lett 94:228–236
Ayesha SK, Masilamani V (2018) A novel digital watermarking scheme for data authentication and copyright protection in 5G networks. Comput Electri Engin, pp 589–605
Chen Y, Jia ZG, Peng Y, et al. A new structure-preserving quaternion QR decomposition method for color image blind watermarking, Signal Proc. https://doi.org/10.1016/j.sigpro.2021.108088
Chen ZG, Peng HP, Liu YH et al (2018) A novel digital watermarking based on general non-negative matrix factorization. IEEE Trans Multimed 20:1973–1986
Chen B, Lu W, Huang JW et al (2022) Secret sharing based reversible data hiding in encrypted images with multiple data-hiders. IEEE Trans Dependable Secure Comput 19:978–991
Divya Shivani JL, Senapati RK (2017) Robust image embedded watermarking using DCT and listless SPIHT. Future Internet, 33. p1–16
Ernawan F, Kabir MN (2018) A robust image watermarking technique with an optimal DCT-psycho visual threshold. IEEE Access 6:20464–20480
Fan MQ (2019) A source coding scheme for authenticating audio signal with capability of self-recovery and anti-synchronization counterfeiting attack. Multimed Tools Appli. https://doi.org/10.1007/s11042-019-08095-x
Fan MQ, Wang HX (2018) An enhanced fragile watermarking scheme to digital image protection and self-recovery. Sig Proc: Image Comm 66:19–29
Faranak T, Manoranjan P, Mohammad RH (2021) Detection and recovery of higher tampered images using novel feature and compression strategy. IEEE Access 9:57510–57528
Guo YF, Au OC, Wang R et al (2018) Halftone image watermarking by content aware double-sided embedding error diffusion. IEEE Trans Image Proc 27:3387–3402
Haghighi B, Taherinia AH, Harati A et al (2021) WSMN: an optimized multipurpose blind watermarking in shearlet domain using MLP and NSGA-II. Appl Soft Comput 101:1–23
Hurrah NN, Parah SA, Loan NA (2019) Dual watermarking framework for privacy protection and content authentication of multimedia, Future Generation Computer Systems, pp 654–673
Jamali M, Rafiee S, Soroushmehr SMR et al. Adaptive blind image watermarking using fuzzy inference system based on human visual perception, arXiv:1709.06536
Khaled L, Ahmed R, Khalil Z (2017) Ambiguity attacks on robust blind image watermarking scheme based on redundant discrete wavelet transform and singular value decomposition. J Electri Syst Inform Technol 4:359–368
Khushwant S, Samriddhi R, Ashutosh M et al (2021) Robust and secure digital image watermarking technique using Arnold transform and memristive chaotic oscillators. IEEE Access 9:72465–72483
Laouamer L, Tayan O (2018) Performance evaluation of a document image watermarking approach with enhanced tamper localization and recovery. IEEE Access 6:26144–26166
Liu XL, Lin CC, Yuan SM (2018) Blind dual watermarking for color images’ authentication and copyright protection. IEEE Trans Circuits Syst Video Technol 28:1047–1055
Loan NA, Hurrah NN, Parah SA et al (2018) Secure and robust digital image watermarking using coefficient differencing and chaotic encryption. IEEE Access 6:19876–19897
Magdy M, Neveen IG, Said G et al (2022) Multiple zero-watermarking of medical images for internet of medical things. IEEE Access 10:38821–38831
Nandhini S, Omar E, Somaya A et al (2021) Image steganography: a review of the recent advances. IEEE Access 9:23409–23423
Rudman K, Bonenfant M, Celik M et al (2016) Toward real-time detection of forensic watermarks to combat piracy by live streaming. SMPTE Motion Imag J 125:34–41
Saeed S, Mohammad AA (2015) A source-channel coding approach to digital image protection and self-recovery. IEEE Trans Image Proc 24:2266–2277
Shehab A, Elhoseny M, Muhammad K et al (2018) Secure and robust fragile watermarking scheme for medical images. IEEE Access 6:10269–10278
Singh P, Agarwal S (2017) A self recoverable dual watermarking scheme for copyright protection and integrity verification. Multimed Tools Appli 76:6389–6428
Sinhal R, Ansari IA (2022) Multipurpose image watermarking: ownership check, tamper detection and self-recovery. Circuits Syst Signal Proc 41:3199–3221
Su QT, Liu DC, Yuan ZH et al (2019) New rapid and robust color image watermarking technique in spatial domain. IEEE Access 7:30398–30409
Wu YD, Weng J, Wang ZX, et al. Attacks and countermeasures on privacy-preserving biometric authentication schemes, IEEE Trans Dependable Sec Comput. https://doi.org/10.1109/TDSC.2022.3162623
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interests
The author declares that there are no conflict of interests, and does not have any possible conflicts of interest. Furthermore, the datasets generated during and/or analysed during the current study are available from the corresponding author on reasonable request.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Fan, M. Blind Dual Image Watermarking for Copyright Protection, Tamper Proofing and Self-Recovery. Multimed Tools Appl 82, 45503–45518 (2023). https://doi.org/10.1007/s11042-023-15261-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-15261-9