Abstract
Modern medical examinations have produced a large number of medical images. It is a great challenge to transmit and store them quickly and securely. Existing solutions mainly use medical image encryption algorithms, but these encryption algorithms, which were developed for ordinary images, are time-consuming and must cope with insufficient security considerations when encrypting medical images. Compared with ordinary images, medical images can be divided into the region of interest and the region of background. In this paper, based on this characteristic, a plain-image correlative semi-selective medical image encryption algorithm using the enhanced two dimensional Logistic map was proposed. First, the region of interest of a plain medical image is permuted at the pixel level, then for the whole medical image, substitution is performed pixel by pixel. An ideal compromise between encryption speed and security can be achieved by full-encrypting the region of interest and semi-encrypting the region of background. Several main types of medical images and some normal images were selected as the samples for simulation, and main image cryptanalysis methods were used to analyze the results. The results showed that the cipher-images have a good visual quality, high information entropy, low correlation between adjacent pixels, as well as uniformly distribute histogram. The algorithm is sensitive to the initial key and plain-image, and has a large keyspace and low time complexity. The time complexity is lower when compared with the current medical image full encryption algorithm, and the security performance is better when compared with the current medical image selective encryption algorithm.
Similar content being viewed by others
1 Introduction
1.1 Background
Modern medical examinations have produced a large number of medical images such as X-ray, computed tomography (CT), magnetic resonance imaging (MRI), ultrasound and positron emission tomography(PET) [9, 11, 35, 38, 55, 56, 69, 71]. These medical images are stored in digital format and may need to be transmitted between doctors and hospitals over an open public network [16]. Transmitting medical images over open networks is risky and easily accessed illegally by hackers [5, 8, 23]. Safe and effective medical services can only be achieved when these medical data are highly secure [38]. In this case, many countries have passed legislation to regulate the security of medical images [19, 70].
In early research, the protection of medical image privacy was mostly based on classical encryption algorithms, which include classical public-key cryptography algorithms, such as RSA cryptography [31] and ElGamal cryptography [66], and classical symmetric encryption algorithms, such as Data Encryption Standard (DES), Advanced Encryption Standard (AES) [49] and International Data Encryption Algorithm (IDEA) [57]. To reduce the encryption time of classical algorithms, the research focus on the frontier of image encryption technology which are currently the chaotic map-based encryption algorithms [75]. Among the algorithms, the most important structure is the “Confusion-Diffusion”, which was proposed by Fridrich [25]. Confusion includes two basic operations, “Permutation” and “Substitution.” Permutation, also called “Shuffle” or “Scrambling” in different literature, aims to permutate the position of pixels in a medical image and reduce the correlation of adjacent pixels. Meanwhile, substitution adjust the values of pixels to alter the statistical characteristics of images. Diffusion can associate each part of the image with each part of the key, which can improve plain-image sensitivity and key sensitivity, and enhance the ability to resist differential attack. By using this structure, many medical image full-encryption algorithms have emerged [14, 18, 26, 29, 41, 42, 44, 58, 60, 61, 71].
In recent years, to further increase the encryption speed of medical image encryption algorithms, many selective or partial encryption schemes have been proposed for the uneven distribution of medical image information. Abdmouleh, M. K et al.proposed an algorithm on transform domain, in which medical images were first decomposed by using the discrete wavelet transform (DWT) with different levels, and then the LL sub-band with maximum information content was encrypted [3]. Zhou, J. et al. proposed another algorithm to partially encrypting the transform domain, while the two-dimensional lifting wavelet transform(2D LWT) was adopted [78]. Two selective encryption algorithms were proposed by Ravichandran, D. et al. and Prabhavathi, K. respectively, in which the rectangle region in the central part of a medical image is manually selected as the region of interest (ROI) for encryption [52, 59]. In another work, a 4D Cat map-based selective encryption scheme was designed by Kanso, A, & Ghebleh, M., the algorithm needs to run multiple rounds, and each round of encryption consists of permutation and substitution [34]. Khashan, O. A., & Alshaikh, M. proposed a lightweight chaotic map-based encryption algorithm to encrypt the edge image of medical images [36]. In literature [51], based on cellular automata (CA), Ping P. et al. proposed a method to encrypt the ROI of medical images. Unfortunately, none of the above methods have any processing on the non-selected region of medical images, resulting in poor security of cipher-images. Their typical features are that the shape of the selected region can be easily seen from the cipher image, and all information about the unselected region can be obtained directly from the cipher-image.
Noura, M. et al. proposed a middle-full encryption mode, in which the ROI of medical images was first encrypted by adopting substitution operation, and then the whole medical image was encrypted by using permutation operation [50]. Manikandan, V. et al. proposed a semi-full encryption scheme based on the transform domain [46]. Firstly, the whole medical image is permutated using the Bülban map, and then substitute the LL sub-band, which is extracted by using 5/3 lifting transform, with high information. However, these two schemes did not change the statistical characteristics of the region of not interest (RONI), leading to risks of statistical attacks.
Another study aimed at the characteristics of different information amounts in different bit-planes of medical images, a multi-chaotic maps-based medical image semi-full encryption algorithm was designed [21]. In this algorithm, according to the information amount of each bit-plane, different rounds of permutation were run in the bit-plane itself respectively, and then the whole medical image was encrypted by using substitution operation. However, the algorithm needs to run too many rounds, even up to 100, which costs a lot of time when encrypting medical images. Another bit-plane based scheme was proposed by Muthu J. S. et al. [48]. Four bit-planes with the high information content of medical images were selected to be permutated, and then the whole medical image was substituted. Compared with the scheme [21], the processing speed is significantly improved.
DNA computing and the Dual Hyperchaotic map had also been proposed for selective encryption algorithm [4]. First, the selected region of a medical image was encrypted by using permutation operation and then encrypted the whole image with substitution operation. However, the actual DNA computing requires additional bio-computing equipment. Besides, there will be additional computing overhead when simulations are run on computers. Shafique A. et al. proposed a 3-level structure to encrypt medical images [63]. In the first and third levels, four bit-planes with high information content were selected to be permutated inner the bit-planes respectively. In the second level, the LL sub-band of the transform domain was selected to be substituted. However, the efficiency of the scheme is low, and it will take more than 3 seconds to encrypt a medical image. Manikandan, V et al. also proposed a 3-level medical image encryption structure [45]. In the first and third levels, the whole medical image was encrypted by using the “permutation-substitution” structure. And in the second level, the classical RC6 algorithm was used to encrypt the LL sub-band of the transform domain. However, the time complexity of the method is so high that it takes tens of seconds to encrypt a medical image.
Literature review shows that the existing medical image selective encryption methods have problems of inadequate security and high computing complexity. Therefore, it is an urgent need to develop a fast and secure selective encryption algorithm for medical images.
1.2 Contributions
In this work, a plain-image correlative semi-selective medical image encryption algorithm using an enhanced 2D-Logistic map was proposed. The main contributions are as follows:
-
Based on the original 1D-Logistic chaotic map, an enhanced 2D-Logistic chaotic map was proposed, which not only increased the number of chaotic control parameters and chaotic initial values but also expanded the value range of chaotic parameters and chaotic sequences.
-
A plain-image correlative semi-selective medical image encryption algorithm using the enhanced 2D-Logistic map was designed.
-
The security and time complexity of the proposed algorithm were analyzed objectively.
The work is demonstrated as follows. Section 2 defines the detail of the enhanced 2-D logistic chaotic map, analyzes its chaos, and then briefly introduces the Secure Hash Algorithm SHA-256. Section 3 defines the detail of the proposed plain-image correlative semi-selective medical image encryption algorithm. Section 4 illustrates the simulation results of the algorithm and discusses its security and time complexity. Section 5 defines the conclusion of the work.
2 Preliminaries
2.1 The original 1-D logistic chaotic map
The Logistic map, also known as the insect population model in ecology [21], is a typical nonlinear chaotic system, which is highly sensitive to the initial state [1] and can produce complex chaotic behaviors [33]. This system has been widely used in the research field of medical image encryption [1, 7, 8, 10, 12, 17, 20,21,22, 24, 27, 28, 33, 37, 39, 40, 43, 47, 53, 54, 62, 65, 68, 73, 74, 76, 77]. The original 1-D Logistic chaotic map can be defined by the following Eq. 1.
Here:
-
xn is the first n iteration result of the system, and xn ∈ (0, 1).
-
a is the chaotic control parameter, and a ∈ (0, 4].
The chaotic bifurcation diagram of the original 1-D Logistic chaotic map is illustrated in Fig. 1. It can be seen that the Logistic map is in chaos when the chaotic control parameter value is a ∈ (3.6,4] [32], that is to say, when the chaotic iteration continues, the generated chaotic sequence will be an aperiodic and non-convergent pseudo-random sequence [21]. On the contrary, when the chaotic control parameter value is a ∈ (0,3.6], the Logistic map shows determinism, that is to say, when the number of chaotic iterations is large enough, the result sequence will converge to a certain constant value [21]. Furthermore, it can be seen that even when the chaotic control parameter value is a ∈ (3.6,4], there are still some periodic (non-chaotic) windows. In order to solve this problem, the traditional works usually select the chaotic control parameter to ensure the chaotic characteristics of cryptosystems [76].
2.2 The enhanced 2-D logistic chaotic map
The chaotic sequence value distribution of the original 1-D Logistic chaotic map is not uniform, and there is a problem of small keyspace when it is applied to cryptosystems. In some research work, multi chaotic systems combined with the Logistic chaotic map have been proposed for medical image encryption, such as Logistic-Tent map [58], Logistic-Sine map [2, 16, 29, 58], Double Humped Logistic map [30], and Logistic-Chebyshev map [13]. In some other research works, the original 1-D Logistic chaotic map was extended to multi-dimensional, such as 2-D Logistic chaotic map [64], 3-D Logistic chaotic map [15], 4-D Logistic chaotic map [67]. However, the problems of chaotic windows and non-uniform chaotic sequence value distribution have not been solved well. Besides, it has not established organic connections among multi chaotic systems.
In this work, an enhanced 2-D Logistic chaotic map was proposed, which can be defined by the following Eq. 2.
Here:
-
The symbol […] means to take the integer part, and the fractional part is discarded directly.
-
k ∈ N+;x, y ∈ (0, 1);a, b ∈ R+.
In the case of chaotic control parameters value range is0 < a, b ≤ 10, the bifurcation diagram of components x and y are illustrated in Fig. 2.
It can be seen that the enhanced 2-D Logistic chaotic map increases the number of initial values and chaotic control parameters, the system shows chaos when the control parameters are in a wider range of values, the values of chaotic sequences are distributed uniformly in the interval [0,1], and chaotic windows are eliminated.
2.3 Secure hash algorithm
The Secure hash algorithm 256 (SHA-256) can map a message M of any length to a 256-bits hash code SHA-256(M). When the input M changes slightly to M’, the hash code SHA-256(M’) changes completely in an unpredictable way. Besides, the SHA-256 algorithm is unidirectional, which means it is easy to compute SHA-256(M) from the input M, while it is computationally infeasible to compute M from SHA-256(M). In addition, the SHA-256 has error detection capability, which can be used to verify the integrity of a message. In this work, the plain medical image is used as the input of SHA-256, and the output of 256-bits length is divided into 32 pieces, where each piece is 8-bits length, as shown in Eq. 3.
Here:
-
image is the binary code of the input image.
-
s(n) is the NTH segment of the hash sequence.
3 The proposed plain-image correlative semi-selective medical image encryption algorithm
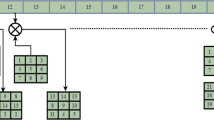
In this work, a plain-image correlative semi-selective medical image encryption algorithm using the proposed chaotic map is designed. The flow chart of the algorithm is shown in Fig. 3. First, the plain medical image is read, and the SHA-256 value of the image is calculated. Then chaotic initial values and control parameters of the enhanced 2D-Logistic chaotic map are generated randomly. Two sets of plain-image correlative chaotic sequences are obtained by using enough round iterations of the enhanced 2D-Logistic chaotic map. The following step is based on the first set of chaotic sequence, where the permutation key is generated and used for encrypting the ROI of the medical image. The semi-encrypted image can be obtained by merging the region of background (ROB) and the permuted ROI. Finally, based on the second set of chaotic sequences, the substitution key is generated, which is used to encrypt the semi-encrypted image to obtain the final cipher medical image.
The detailed implementation of the algorithm includes the following steps:
-
Step1: Select a plain medical image: Img (M, N).
-
Here M is the number of rows of the Img and N is the number of columns of the Img
-
-
Step2: Segment the medical image Img into Img(ROI) and Img(ROB), and count the pixel number of Img(ROI).
Img(ROI), Img(ROB) = Segment(Img).
Count = the pixel number of Img(ROI)
-
Step3: Calculate the SHA-256 value of image Img.
SHA-256(Img) = s1, s2, s3,…, s32
-
Step4: Generate chaotic control parameters and chaotic initial values randomly, with the precision of 15 decimal places, where the parameter a′ requires plain-image correlation.
$$ a,b,{x}_1,{y}_1= random $$
-
Step5: Generate two sets of plain-image correlated chaotic sequences CS1 and CS1 according to Eq. 2, and the number of iterations rounds isM × N + 10000.
$$ CS1, CS2= Chaoticmap\left({a}^{\prime },b,{x}_1,{y}_1\right) $$ -
Step6: Generate the encryption key. The chaotic sequences CS1 are selected according to the size of ROI, which is sorted to generate the key for the permutation. The chaotic sequences CS2 are amplified 2d times and then take the integer part to generate the key for the substitution.
-Here, d is the color depth of the Img, and ‘[]’ is the symbol of taking the integer part.
-
Step7: Encrypt the ROI by permutating the pixel position.
-
Step8: Merge permuted ROI with ROB.
-
Step9: Encrypt the P(Img) by substituting its pixel one by one to achieve the final encryption image.
The decryption algorithm is the inverse of the encryption algorithm, and the structure is illustrated in Fig. 4. First, the cipher medical image is read and the decryption keys are regenerated according to a, b, x1, y1 and SHA-256(Img), which can be obtained from the secret key transfer channel. Then, according to the opposite steps of the encryption algorithm, using inverse substitution operation to the entire cipher-image and inverse permutation operation to the ROI respectively, to get the decrypted medical image. Finally, the SHA-256 value of the decrypted image was calculated and compared with the original SHA-256(Img) to verify the integrity of the medical image.
4 Simulation results and analysis
4.1 Simulation platform and data samples
This research is algorithm research about medical image encryption. Therefore, the simulation platforms required are only computer hardware and software. The details of them are listed in Table 1.
This research is algorithm research about medical image encryption. Therefore, the main types of medical images, including, X-ray, CT, MRI, ultrasound, PET and COVID-19 virus images, are selected as simulation samples. In addition, some normal images are also used as samples to further analyze the proposed algorithm. The basic attributes of these simulation samples are shown in Table 2, and the plain images of them are illustrated in Fig. 5.
4.2 Simulation results and analysis
In this section, the encryption results of the simulation samples are illustrated and analyzed. The analysis methods used in the research include two main categories: confidentiality analysis and time complexity analysis.
4.2.1 Confidentiality analysis
In confidentiality analysis, four different types of analysis methods are mainly adopted. (1) The visual quality analysis of cipher-images. (2) Statistical analysis, including histogram analysis, information entropy analysis, and correlation analysis of adjacent pixels. (3) The key analysis, including keyspace and key sensitivity analysis. (4) Chosen plain-image analysis.
Cipher-image visual quality analysis
Using the proposed algorithm to process samples in Fig. 5, the permutation results of ROI, final encryption results, and corresponding decryption results are illustrated in Fig. 6. Since Fig. 5g and h are normal images without ROB, the whole images of them were treated as ROI in the permutation step. Here the chaotic control parameters and chaotic initial value are randomly selected as Table 3. It can be seen that the ROI after permutation processing has obtained primary protection. After substitution processing for the whole image, any subjective visual information cannot be seen from the cipher-image. This means that the quality of the cipher-image subjective visual is good. Meanwhile, there is no visual difference between the decrypted image and the original plain image.
Statistical analysis
Histogram analysis The pixel distribution histogram can intuitively describe the number of pixels with different values in an image. For an ideal cipher-image, it should have a completely different histogram from the corresponding plain-image, and generally speaking, its histogram should be approximately uniform distributed. The histograms of sample images are analyzed, and the results are illustrated in Fig. 7. It can be seen that each cipher-image has a uniform distributed histogram, which means that the algorithm does well with histogram analysis.
Information entropy analysis Entropy is a quantitative measure of disorder or uncertainty in a system. The higher of the information entropy value, the more chaotic of the system. For an image I, its information entropy value can be calculated as Eq. 4:
Here:
-
P(Ik) is the proportion of the pixel with the value of k in the total number of pixels,
-
d is the color depth of image I.
-
Σ is the continuous addition symbol.
According to Eq. 4, it is easy to know that an image with a color depth of d can have the maximum information entropy value of d. The larger the result value, the better the randomness of the cipher-image, and the higher security of the algorithm. The information entropy value of sample images is calculated, and the results are listed in Table 4. It can be seen that the information entropy of cipher-image is very close to the ideal value 8, which indicates that the number of pixels with different pixel values is very close to uniform distribution from a quantitative perspective. Cryptanalysts can hardly get any useful information by using information entropy analysis.
Correlation analysis of adjacent pixels Correlation analysis of adjacent pixels is another important statistical analysis method. For visually meaningful images, the correlation between adjacent pixels is usually high because their pixel values are usually close. A good medical image encryption algorithm should ensure that the correlation between adjacent pixels of the cipher-image is low enough. The correlation of adjacent pixels can be calculated from horizontal, vertical, and diagonal directions as Eq. 5.
Here:
-
E() means the Expectation.
-
D() means the square deviation.
It can be known from the mathematical properties of Eq. 5 that the value of corx, y must be between [−1, 1]. The value is closer to 0, the correlation between the adjacent pixels is weaker, and the security of the encryption algorithm is higher. The correlation of adjacent pixels of plain-images and cipher-images in Fig. 6 is calculated, and the values are listed in Table 5.
It can be seen from the data that the correlation of adjacent pixels of plain-images is strong, while the correlation of adjacent pixels of corresponding cipher-image images is very weak, and the values are close to the ideal value 0. The correlation of adjacent pixels can be illustrated as another intuitive form in Fig. 8 and b. In these figures, it can be easily seen that the correlation of adjacent pixels of plain medical images is strong and its distribution is close to the line of x = y, while the correlation of adjacent pixels of corresponding cipher-images is very weak and close to a uniform distribution. Cryptanalysts can hardly get any useful information from the adjacent pixels of the cipher image.
a. The correlation of sample images a-d in different directions (1st column: plain-images and corresponding cipher-image; 2nd column: correlation diagram in horizontal; 3rd column: correlation diagram in vertical; 4th column: correlation diagram in diagonal). b. The correlation of sample images e-h in different directions (1st column: plain-images and corresponding cipher-image; 2nd column: correlation diagram in horizontal; 3rd column: correlation diagram in vertical; 4th column: correlation diagram in diagonal)
The key analysis
Keyspace analysis Keyspace is the set of all possible keys in a cryptosystem. The larger the keyspace, the higher the security of the encryption algorithm, and the stronger the ability to resist brute force attacks. In general, the keyspace of a cryptosystem should not be less than 2100 [6], which is about 1.27 × 1030. However, as computing power continues to improve, we recommend that the keyspace should be much larger than 2100.
For chaotic map-based cryptosystems, the range of chaotic control parameters and chaotic initial values are usually the keyspace. For the proposed algorithm, the factors affecting the keyspace are chaotic control parametersa, b and chaotic initial valuesx1, y1. The computing accuracy used in this paper is 1 × 10−15, so the key space should be (1 × 1015)4, which is about 2200 and large enough to resist brute force attacks. Even with the current world’s fastest computer, the ‘Fugaku’ in Japanese, whose peak computing power is about 5 × 1019 times per second, it will take an average of 4 × 1040 seconds or about 1032 years to find the correct key. Moreover, the key space of the proposed algorithm has the potential of expansion, which only needs to improve the computing accuracy of the proposed chaotic map.
Key sensitivity analysis The key sensitivity analysis should include two aspects, (1) using two slightly different keys to encrypt the same plain medical image, the corresponding cipher-image will be completely different; (2) using the decryption key, which is slightly different from the encryption key, to decrypt the cipher-image will get a wrong result, and the decryption result should not contain information beyond the cipher-image. Several groups of slightly different chaotic control parameters and chaotic initial values used in key sensitivity analysis are listed in Table 6.
In order to analyze the change degree between the different cipher-image, two quantitative indexes, the number of pixel change rate (NPCR) and the unified average changing intensity (UACI), are used. These two indexes can be calculated as Eq. 6 and Eq. 7, respectively.
Where
In the Eq. 6, Eq. 7, and Eq. 8:
-
M, N is the number of rows and columns of the image respectively.
-
d is the color depth of the image I.
-
I1(i, j) is the pixel value of the i row and j column of the image I.
-
Σ is the continuous addition symbol.
For two random 8-bit color depth images, the NPCR value should be larger than 0.995693, and the UACI value should be close to 0.334636 [72]. Using the keys in Table 6 to encrypt the examples in Fig. 5, the NPCR and UACI of the results are listed in Tables 7 and 8 respectively. It can be seen from the data in these two tables, a slight change in the key will produce completely different encryption results.
The correct decryption results and the incorrect decryption results with slightly different keys for image Fig. 5a are illustrated in Fig. 9, and the statistical indicators of them are analyzed, which are listed in Table 9. The data shows that no useful information can be derived from the incorrect decryption results. The above analysis of encryption and decryption results with slightly different keys shows that the algorithm has good key sensitivity.
Chosen plain-image analysis
Differential analysis Differential analysis is a common method of chosen plain-image cryptanalysis, in which the same key is used to encrypt two slightly different plain-image and then compare the corresponding two cipher-images to find useful information. An excellent medical image encryption algorithm should ensure that the NPCR and UACI values are close to the value of the two random images when using the differential attack to analyze it.
For the eight samples in Fig. 5, one pixel was selected randomly, and its value was changed slightly. Then these two slightly different images were encrypted with the same key. The original images, slightly changed images, corresponding encryption results, and the difference between these two sets of encryption results with their histograms are illustrated in Fig. 10. The NPCR and UACI values of these two cipher-image groups are listed in Tables 10 and 11. It can be seen from the data that completely different cipher-image can be obtained even if the plain-image is only changed slightly, and the comparative analysis of the two cipher-images can hardly find any useful information. Therefore, the proposed algorithm can resist the attack of differential analysis.
Slightly different plain image, corresponding cipher-image, and the different between them (1st column: original plain-images; 2nd column: slightly changed images; 3rd column: cipher-images of original; 4th column: cipher-images of slightly changed images; 5th column: The difference between two sets of cipher-images; 6th column: histogram of the difference between two sets of cipher-images)
Black and white image analysis Black and white image analysis is another commonly used method of chosen plain-image cryptanalysis, which is often used to try to obtain the encryption key of the substitution phase. The visual quality and histogram analysis of cipher black and white images is shown in Fig. 11. It can be seen from the figure that the cipher-images visual quality is good, and the corresponding histograms distribute uniformly. Table 12 shows part of the quantitative analysis results of the black and white image analysis. The results show that the correlation between adjacent pixels of cipher-image is low, and its information entropy is close to the theoretical upper limit.
Since the black and white images have no medical visual significance, the whole image is divided into ROB. So there isn’t any permutation was performed, and only the substitution was performed to encrypt black and white images. The cipher-image is the encryption key of the substitution phase. However, it is not feasible to crack the encryption results of other images only through the substitution key of black and white images. The first reason is that there is no feasible method to obtain the key generation key, which is chaotic initial values and chaotic parameters, from the substitution key. This was because of the introduction of the ‘mod’ operations in the encryption key generation phase. The second reason is that the encryption key is plain-image correlative. Even if the same key generation key is used to encrypt different images, different encryption keys will be generated in the process.
The results of differential analysis and black and white images analysis show that the proposed algorithm has the ability to resist chosen plain-image attacks.
4.2.2 Time complexity analysis
The proposed encryption algorithm consists of the key generation stage and the image encryption stage. In the key generation stage, the time complexity of generating chaotic sequences with M × N length is O(MN). Since only the ROI of medical images need to be permutated, the key length is smaller than M × N, so the time complexity of generating the key for permutation is less than O (MNlog2(MN)). At the same time, the time complexity of generating the key for substitution is O(MN). Therefore, the time complexity of the key generation stage is less than O(MNlog2(MN)). In the image encryption stage, pixel permutation and substitution are both linear operations, in which the time complexity of permutation is less than O(MN) and the time complexity of substitution is O(MN), so the time complexity of the encryption stage is less than O(2MN).
The proposed algorithm was simulated and the actual running time was measured. The results are listed in Table 13. As can be seen from the table, for images of the same size, the permutation and overall encryption speed of medical images are significantly faster than that of normal images due to the reduction of the amount of data permutated.
4.3 Comparative analysis
The proposed algorithm is compared with some methods discussed in the literature review of Section 1. The cipher-image visual quality comparative analyses are shown in Table 14. It can be seen from the table that the cipher-image visual quality of the proposed semi-selective encryption algorithm is better than that of full-selective encryption algorithms. Some main quantitative index values of the proposed algorithm are compared with other semi-selective encryption algorithms, and the results are listed in Table 15. It can be seen that the proposed algorithm is superior to or at least not worse than the existing method in all major indicators.
5 Conclusion
In this work, an enhanced 2D-Logistic chaotic map was designed, in which the number of chaotic control parameters and chaotic initial values was increased, the value range of chaotic control parameters was expanded, and the chaotic windows were eliminated, when compared with the original 1-D Logistic map. Then, based on the characteristics that medical images can be divided into ROI and ROB, a plain-image correlative semi-selective medical image encryption algorithm using enhanced 2D-Logistic map was proposed. The simulation results analysis showed that the algorithm has good security and high encryption speed. Therefore, it is suitable to protect the confidentiality of medical images. The future recommended work is to combine the semi-selective image encryption structure with other high-information region segmentation methods, such as bit-plane segmentation or transform domain. Another suggested research direction is to explore the implementation of the algorithm on different medical platforms.
References
Aashiq Banu S, Amirtharajan R (2020) A robust medical image encryption in dual domain : chaos-DNA-IWT combined approach. Med Biol Eng Comput 58(7):1445–1458
Abd El-Latif AA, Abd-El-Atty B, Talha M (2017) Robust encryption of quantum medical images. IEEE Access 6:1073–1081. https://doi.org/10.1109/ACCESS.2017.2777869
Abdmouleh, M. K., Khalfallah, A., & Bouhlel, M. S. (2017). A novel selective encryption DWT-based algorithm for medical images. 2017 14th international conference on computer graphics, imaging and visualization, 79–84. https://doi.org/10.1109/CGiV.2017.10
Akkasaligar PT, Biradar S (2020) Selective medical image encryption using DNA cryptography. Inf Sec J: A Global Persp 29(2):91–101. https://doi.org/10.1080/19393555.2020.1718248
Al-haj A, Abandah G, Hussein N (2015) Crypto-based algorithms for secured medical image transmission. IET Inf Secur 9(6):365–373. https://doi.org/10.1049/iet-ifs.2014.0245
Alvarez G, Li S (2006) Some basic cryptographic requirements for chaos-based cryptosystems. Int J Bifurcation Chaos 16(08):2129–2151
Arumugham S, Rajagopalan S, Bosco J, Rayappan B, Amirtharajan R (2018) Networked medical data sharing on secure medium--A web publishing mode for DICOM viewer with three layer authentication. J Biomed Inform 86:90–105. https://doi.org/10.1016/j.jbi.2018.08.010
Arunkumar S, Subramaniyaswamy V, Vijayakumar V, Chilamkurti N, Logesh R (2019) SVD-based robust image steganographic scheme using RIWT and DCT for secure transmission of medical images. Measurement 139:426–437. https://doi.org/10.1016/j.measurement.2019.02.069
Bakshi A, Patel AK (2019) Secure telemedicine using RONI halftoned visual cryptography without pixel expansion. J Inf Sec Appl 46:281–295. https://doi.org/10.1016/j.jisa.2019.03.004
Balasamy K, Suganyadevi S (2021) A fuzzy based ROI selection for encryption and watermarking in medical image using DWT and SVD. Multimed Tools Appl 80:7167–7186
Banik A, Shamsi Z, Laiphrakpam DS (2019) An encryption scheme for securing multiple medical images. J Inf Sec Appl 49:102398. https://doi.org/10.1016/j.jisa.2019.102398
Barik RC, Changder S (2021) A novel and efficient amino acid codon based medical image encryption scheme colligating multiple chaotic maps. Multimed Tools Appl 80:10723–10760
Belazi A, Talha M, Kharbech S, Xiang W (2019) Novel medical image encryption scheme based on chaos and DNA encoding. IEEE Access 7:36667–36681. https://doi.org/10.1109/ACCESS.2019.2906292
Chandrasekaran J, Thiruvengadam SJ (2017) A hybrid chaotic and number theoretic approach for securing DICOM images. Sec Comm Networks 2017:1–12
Chen M, Ma G, Tang C, Lei Z (2020) Generalized optical encryption framework based on Shearlets for medical image. Opt Lasers Eng 128:106026. https://doi.org/10.1016/j.optlaseng.2020.106026
Chen X, Hu C (2017) Adaptive medical image encryption algorithm based on multiple chaotic mapping. Saudi J Biol Sci 24(8):1821–1827. https://doi.org/10.1016/j.sjbs.2017.11.023
Chen X, Hu C-J (2017) Medical image encryption based on multiple chaotic mapping and wavelet transform. Biomed Res 28(20):8834–8837
Chirakkarottu S, Mathew S (2020) A novel encryption method for medical images using 2D Zaslavski map and DNA cryptography. SN Appl Sci 2(1):1–10. https://doi.org/10.1007/s42452-019-1685-8
Cryptography Law, (2019).
Dagadu JC, Li J, Aboagye EO (2019) Medical image encryption based on hybrid chaotic DNA diffusion. Wirel Pers Commun 108(1):591–612. https://doi.org/10.1007/s11277-019-06420-z
Dai Y, Wang H, Wang Y (2016) Chaotic medical image encryption algorithm based on bit-plane decomposition. Int J Pattern Recognit Artif Intell 30(4):1657001. https://doi.org/10.1142/S0218001416570019
Dai Y, Wang H, Zhou Z, Jin Z (2016) Research on medical image encryption in telemedicine systems. Technol Health Care 24(s2):S435–S442. https://doi.org/10.3233/THC-161166
Devi RS, Thenmozhi K, Rayappan JBB, Amirtharajan R, Praveenkumar P (2019) Entropy influenced RNA diffused quantum chaos to conserve medical data privacy. Int J Theor Phys 56(6):1937–1956
Dridi M, Hajjaji MA, Bouallegue B, Mtibaa A (2016) Cryptography of medical images based on a combination between chaotic and neural network. IET Image Process 10(11):830–839. https://doi.org/10.1049/iet-ipr.2015.0868
Fridrich J (1998) Symmetric ciphers based on two-dimensional chaotic maps. Int J Bifurcation Chaos 8(06):1259–1284
Gafsi M, Abbassi N, Hajjaji MA, Malek J, Mtibaa A (2020) Improved chaos-based cryptosystem for medical image encryption and decryption Sci Prog 2020
Ge J (2020) Alcencryption : A secure and efficient algorithm for medical. IEEE Signal Process Lett 125(3):1083–1100. https://doi.org/10.32604/cmes.2020.013039
Gupta R, Pachauri R, Singh AK (2018) An effective approach of secured medical image transmission using encryption method. Mole Cell Biomech 15(2):63. https://doi.org/10.3970/mcb.2018.00114
Hua Z, Yi S, Zhou Y (2018) Medical image encryption using high-speed scrambling and pixel adaptive diffusion. Signal Process 144:134–144. https://doi.org/10.1016/j.sigpro.2017.10.004
Ismail SM, Said LA, Radwan AG, Madian AH, Abu-elyazeed MF (2018) Generalized double-humped logistic map-based medical image encryption. J Advan Res 10:85–98. https://doi.org/10.1016/j.jare.2018.01.009
Jain M, Choudhary RC, Kumar A (2016) Secure medical image steganography with RSA cryptography using decision tree. In: 2016 2nd international conference on contemporary computing and informatics (IC3I), pp 291–295. https://doi.org/10.1109/IC3I.2016.7917977
Jiao G, Peng X, Duan K (2019) Image encryption with the cross diffusion of two chaotic maps. KSII Trans Int Inform Syst (TIIS) 13(2):1064–1079
Jiao G, Zhou S, Li L, Zou Y (2019) Hybrid chaotic encryption algorithm for securing dicom systems. Int J Perform Eng 15(5):1436–1444. https://doi.org/10.23940/ijpe.19.05.p20.14361444
Kanso A, Ghebleh M (2015) An efficient and robust image encryption scheme for medical applications. Commun Nonlinear Sci Numer Simul 24(1–3):98–116. https://doi.org/10.1016/j.cnsns.2014.12.005
Kanso A, Ghebleh M (2018) An efficient lossless secret sharing scheme for medical images. J Vis Commun Image Represent 56:245–255. https://doi.org/10.1016/j.jvcir.2018.09.018
Khashan OA, Alshaikh M (2020) Edge-based lightweight selective encryption scheme for digital medical images. Multimed Tools Appl 79(35):26369–26388
Khond S, Vijayakumar B (2019) Secure medical image processing using chaos and DNA encryption enhanced using reversible data hiding. Int J Eng Adv Technol (IJEAT) 8(6S):1062–1067. https://doi.org/10.35940/ijeat.F1202.0886S19
Koppu S, Viswanatham VM (2018) Medical image security enhancement using two dimensional chaotic mapping optimized by self-adaptive grey wolf algorithm. Evol Intel 11(1):53–71. https://doi.org/10.1007/s12065-018-0159-z
Kumar CV, Natarajan V, Poonguzhali P (2015) Secured patient information transmission using reversible watermarking and DNA Encrytion for medical images. Appl Math Sci 9(48):2381–2391
Kumar S, Panna B, Kumar R (2019) Medical image encryption using fractional discrete cosine transform with chaotic function. Med Biol Eng Comput 57(11):2517–2533
Lakshmi C, Thenmozhi K, Rayappan JBB, Rajagopalan S, Amirtharajan R, Chidambaram N (2020) Neural-assisted image-dependent encryption scheme for medical image cloud storage. Neural Comput Appl 33:9–6684. https://doi.org/10.1007/s00521-020-05447-9
Liu J, Ma Y, Li S, Lian J, Zhang X (2018) A new simple chaotic system and its application in medical image encryption. Multimed Tools Appl 77(17):22787–22808
Liu J, Li J, Cheng J, Ma J, Sadiq N, Han B, Geng Q, Ai Y (2019) A novel robust watermarking algorithm for encrypted medical image based on DTCWT-DCT and chaotic map. Comput, Mat Continua 61(2):889–910. https://doi.org/10.32604/cmc.2019.06034
Madhusudhan K, Sakthivel P (2020) A secure medical image transmission algorithm based on binary bits and Arnold map. J Ambient Intell Human Comp:1–8. https://doi.org/10.1007/s12652-020-02028-5
Manikandan V, Amirtharajan R (2021) On dual encryption with RC6 and combined logistic tent map for grayscale and DICOM. Multimed Tools Appl 80(15):23511–23540
Manikandan V, Amirtharajan R (2022). A simple embed over encryption scheme for DICOM images using Bülban Map. Med Biol Eng Comput, 1–17. https://doi.org/10.1007/s11517-021-02499-4
Mortajez S, Tahmasbi M, Zarei J, Jamshidnezhad A (2020) A novel chaotic encryption scheme based on efficient secret keys and confusion technique for confidential of DICOM images. Inform Med Unlocked 20:100396. https://doi.org/10.1016/j.imu.2020.100396
Muthu JS, Murali P (2022) A novel DICOM image encryption with JSMP map. Optik 251(2022):168416. https://doi.org/10.1016/j.ijleo.2021.168416
Norcen R, Podesser M, Pommer A, Schmidt H-P, Uhl A (2003) Confidential storage and transmission of medical image data. Comput Biol Med 33(3):277–292. https://doi.org/10.1016/S0010-4825(02)00094-X
Noura M, Noura H, Chehab A, Mansour MM, Sleem L, Couturier R (2018) A dynamic approach for a lightweight and secure cipher for medical images. Multimed Tools Appl 77(23):31397–31426
Ping P, Zhang X, Yang X, Abdelsattar Y, Hashems A (2022) A novel medical image encryption based on cellular automata with ROI position embedded. Mult Tools Appl:1–21
Prabhavathi K, Sathisha C, Ravikumar K (2017). Region of interest based selective medical image encryption using multi chaotic system. 2017 international conference on electrical, electronics, communication, computer, and optimization techniques (ICEECCOT), 1–5
Praveenkumar P, Devi NK, Ravichandran D, Avila J, Thenmozhi K, Rayappan JBB, Amirtharajan R (2018) Transreceiving of encrypted medical image-a cognitive approach. Multimed Tools Appl 77(7):8393–8418. https://doi.org/10.1007/s11042-017-4741-7
Qasim KR, Qasim SS (2020) Encrypt medical image using Csalsa20 stream algorithm. Medico-Legal Update 20(3):1248–1256
Rahmatullah B, Besar R (2007) Comparison of morphological-based segmentation methods for fetal femur length measurements. J Mech Med Biol 7(03):247–263
Rahmatullah B, Noble JA (2013) Anatomical object detection in fetal ultrasound: computer-expert agreements. Int Conf Biom Inf Technol:207–218
Raja S (2019) Multiscale transform-based secured joint efficient medical image compression-encryption using symmetric key cryptography and ebcot encoding technique. Int J Wavelets, Multiresolution Inform Process 17(05):1950034. https://doi.org/10.1142/S0219691319500346
Ravichandran D, Praveenkumar P, Rayappan JBB, Amirtharajan R (2016) Chaos based crossover and mutation for securing DICOM image. Comput Biol Med 72:170–184. https://doi.org/10.1016/j.compbiomed.2016.03.020
Ravichandran D, Praveenkumar P, Rayappan JBB, Amirtharajan R (2017) DNA chaos blend to secure medical privacy. IEEE Trans Nanobiosci 16(8):850–858
Ravichandran D, Aashiq Banu S, Murthy BK, Balasubramanian V, Fathima S, Amirtharajan R (2021) An efficient medical image encryption using hybrid DNA computing and chaos in transform domain. Med Biol Eng Comput 59(3):589–605
Sangavi V, Thangavel P (2020) An exotic multi-dimensional conceptualization for medical image encryption exerting Rossler system and sine map. J Inform Secur Appl 55:102626. https://doi.org/10.1016/j.jisa.2020.102626
Sasikaladevi N, Geetha K, Revathi A (2019) EMOTE – multilayered encryption system for protecting medical images based on binary curve. J King Saud Univ - Comput Inform Sci 32(10):1215. https://doi.org/10.1016/j.jksuci.2019.01.014
Shafique A, Ahmed J, Rehman MUR, Hazzazi MM (2021) Noise-resistant image encryption scheme for medical images in the chaos and wavelet domain. IEEE Access 9:59108–59130. https://doi.org/10.1109/ACCESS.2021.3071535
Shahzadi R, Anwar SM, Qamar F, Ali M, Rodrigues JJPC (2019) Chaos based enhanced RC5 algorithm for security and integrity of clinical images in remote health monitoring. IEEE Access 7:52858–52870. https://doi.org/10.1109/ACCESS.2019.2909554
Shankar K, Elhoseny M, Dhiravida E, Lakshmanaprabu SK, Wu W (2018) An efficient optimal key based chaos function for medical image security. IEEE Access 6:77145–77154. https://doi.org/10.1109/ACCESS.2018.2874026
Singh LD, Singh KM (2017) Medical image encryption based on improved ElGamal encryption technique. Optik - Int J Light Electron Optics 147:88–102. https://doi.org/10.1016/j.ijleo.2017.08.028
Stalin S, Maheshwary P, Shukla PK, Maheshwari M, Gour B, Khare A (2019) Fast and secure medical image encryption based on non linear 4D logistic map and DNA sequences (NL4DLM_DNA). J Med Syst 43(8):267
Tamilselvi R, Ravindran G (2015) Comparison of encryption efficiency in DICOM images based on radon and block transform. Int J ChemTech Res 8(6):843–846
Tamrin KF, Rahmatullah B, Samuri SM (2015) Aberration compensation of holographic particle images using digital holographic microscopy. J Mod Opt 62(9):701–711. https://doi.org/10.1080/09500340.2014.1003257
The Health insurance portability and accountability act, (1996).
Weijia C, Yicong Z, Philip CLC, Liming, X. (2017) Medical image encryption using edge maps. Signal Process 132:96–109. https://doi.org/10.1016/j.sigpro.2016.10.003
Wu Y, Noonan JP, Agaian S (2011) NPCR and UACI randomness tests for image encryption. Cyber Journals: Multidisciplinary Journals in Science and Technology. J Selected Areas Telecommun (JSAT) 1(2):31–38
Yang Y, Xiao X, Cai X, Zhang W (2019) A secure and high visual-quality framework for medical images by contrast-enhancement reversible data hiding and homomorphic encryption. IEEE Access 7:96900–96911
Ye C, Xiong Z, Ding Y, Zhang X, Wang G, Xu F (2015) Joint fingerprinting/encryption for medical image security. Int J Sec Appl 9(1):409–418
Zhang B, Rahmatullah B, Wang SL, Zaidan A, Zaidan B, Liu P (2020) A review of research on medical image confidentiality related technology coherent taxonomy , motivations , open challenges and recommendations. Multimedia Tools Appl:1–40
Zhang L, Zhu Z, Yang B, Liu W, Zhu H, Zou M (2015) Cryptanalysis and improvement of an efficient and secure medical image protection scheme. Math Probl Eng 2015:1–11
Zhang L, Zhu Z, Yang B, Liu W, Zhu H, Zou M (2015) Medical image encryption and compression scheme using compressive sensing and pixel swapping based permutation approach. Math Probl Eng 2015:2015–2019
Zhou J, Li J, Di X (2020) A novel lossless medical image encryption scheme based on game theory with optimized ROI parameters and hidden ROI position. IEEE Access 8:122210–122228. https://doi.org/10.1109/ACCESS.2020.3007550
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Declarations
No conflicts of interest, all medical image samples are obtained from open sources and do not involve the patient’s privacy.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Zhang, B., Rahmatullah, B., Wang, S.L. et al. A plain-image correlative semi-selective medical image encryption algorithm using enhanced 2D-logistic map. Multimed Tools Appl 82, 15735–15762 (2023). https://doi.org/10.1007/s11042-022-13744-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-13744-9