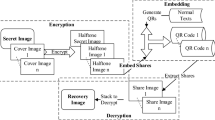
Abstract
Visual cryptography (VC) is a technique that can encrypt images without complicated calculation. As the image, the quick response (QR) code can also be encrypted by VC to ensure its safe transmission on the network. In recent years, VC has developed rapidly. The original VC has been developed into many forms, such as (n, n)-VC, (k, n)-VC. These new VC schemes can be applied to the QR code to make it more secure in the network. This paper proposes a new VC scheme for the QR code by using the mechanism of the error correction code (ECC). ECC is used to control the number of shares to recover whether the secret QR code can be decoded correctly. The codewords in the same block of the QR code are evenly distributed to each share. If the number of shares is less than the threshold, the restored QR code will not be decoded correctly. The number of wrong codewords exceeds its error correction capability. The theoretical analysis shows that the proposed scheme is secure when the standard decoder is used. The experimental results also prove the feasibility of the proposed scheme.




Similar content being viewed by others
References
Abdulla A A (2015) Exploiting similarities between secret and cover images for improved embedding efficiency and security in digital steganography. Ph.D. Thesis, University of Buckingham
Ateniese G, Blundo C, De Santis A, Stinson D R (1996) Visual cryptography for general access structures. Inf Comput 129(2):86–106
Cheng Y, Fu Z, Yu B (2018) Improved visual secret sharing scheme for QR code applications. IEEE Trans Inf Forensic Secur 13(9):2393–2403
Chiu P-L, Lee K-H (2019) Efficient constructions for progressive visual cryptography with meaningful shares. Signal Process 165:233–249
Chow Y-W, Susilo W, Yang G, Phillips J G, Pranata I, Barmawi A M (2016) Exploiting the error correction mechanism in QR codes for secret sharing. In: Australasian conference on information security and privacy. Springer, pp 409–425
Fang W-P (2011) Offline QR code authorization based on visual cryptography. In: 2011 Seventh international conference on intelligent information hiding and multimedia signal processing. IEEE, pp 89–92
Hao L-Y, Yan B, Pan J-S, Chen N, Yang H-M, Acquah M A (2019) Adaptive unified data embedding and scrambling for three-dimensional mesh models. IEEE Access 7:162366–162386
Huang B-Y, Juan J S-T (2020) Flexible meaningful visual multi-secret sharing scheme by random grids. Multimed Tools Appl:1–25
Huang P-C, Chang C-C, Li Y-H (2018) Sudoku-based secret sharing approach with cheater prevention using QR code. Multimed Tools Appl 77(19):25275–25294
Huang P-C, Chang C-C, Li Y-H, Liu Y (2020) Efficient QR code secret embedding mechanism based on hamming code. IEEE Access 8:86706–86714
Huang P-C, Chang C-C, Li Y-H, Liu Y (2021) Enhanced (n, n)-threshold QR code secret sharing scheme based on error correction mechanism. J Inf Secur Appl 58:102719
Huang P-C, Li Y-H, Chang C-C, Liu Y (2019) Efficient QR code authentication mechanism based on sudoku. Multimed Tools Appl 78 (18):26023–26045
Information technology (2006) automatic identification and data capture techniques. QR code 2005 bar code symbology specification. ISO/IEC 18004, 126
Kannojia S P, Kumar J (2021) XOR-based visual secret sharing scheme using pixel vectorization. Multimed Tools Appl 80(10):14609–14635
Katzenbeisser S, Petitcolas FAP (2000) Digital watermarking. Artech House, London, pp 2
Li L, Yuan X, Lu Z, Pan J-S (2010) Rotation invariant watermark embedding based on scale-adapted characteristic regions. Inf Sci 180(15):2875–2888
Liu T, Yan B, Pan J-S (2019) Color visual secret sharing for QR code with perfect module reconstruction. Appl Sci 9(21):1–20
Naor M, Shamir A (1994) Visual cryptography. In: Workshop on the Theory and Application of of Cryptographic Techniques. Springer, pp 1–12
Pan J-S, Hsin Y-C, Huang H-C, Huang K-C (2004) Robust image watermarking based on multiple description vector quantisation. Electron Lett 40(22):1409–1410
Pan J-S, Li W, Yang C-S, Yan L-J (2015) Image steganography based on subsampling and compressive sensing. Multimed Tools Appl 74 (21):9191–9205
Pan J-S, Sun X-X, Chu S-C, Abraham A, Yan B (2020) Digital watermarking with improved SMS applied for QR code. Eng Appl Artif Intell 97:104049
Petitcolas FAP, Anderson R J, Kuhn M G (1999) Information hiding-a survey. Proc IEEE 87(7):1062–1078
Sun Y-X, Yan B, Pan J-S, Yang H-M, Chen N (2019) Reversible data hiding in encrypted color halftone images with high capacity. Appl Sci 9 (24):1–18
Tian A-Q, Chu S-C, Pan J-S, Cui H, Zheng W-M (2020) A compact pigeon-inspired optimization for maximum short-term generation mode in cascade hydroelectric power station. Sustainability 12(3):767
Tian A-Q, Chu S-C, Pan J-S, Liang Y (2020) A novel pigeon-inspired optimization based MPPT technique for PV systems. Processes 8(3):356
Wang D, Li X, Yi F (2007) Probabilistic (n, n) visual secret sharing scheme for grayscale images. In: International Conference on Information Security and Cryptology. Springer, pp 192–200
Wang D, Zhang L, Ma N, Li X (2007) Two secret sharing schemes based on boolean operations. Pattern Recogn 40(10):2776–2785
Wang F-H, Yen K K, Jain L C, Pan J-S (2007) Multiuser-based shadow watermark extraction system. Inf Sci 177(12):2522–2532
Weng S, Zhao Y, Pan J-S, Ni R (2007) A novel reversible watermarking based on an integer transform. In: 2007 IEEE International Conference on Image Processing, vol 3. IEEE, pp 241–244
Wu T-Y, Chen C-M, Wang K-H, Meng C, Wang E K (2019) A provably secure certificateless public key encryption with keyword search. J Chin Inst Eng 42(1):20–28
Wu T-Y, Lee Z, Obaidat M S, Kumari S, Kumar S, Chen C-M (2020) An authenticated key exchange protocol for multi-server architecture in 5G networks. IEEE Access 8:28096–28108
Yan B, Wang Y-F, Song L-Y, Yang H-M (2016) Size-invariant extended visual cryptography with embedded watermark based on error diffusion. Multimed Tools Appl 75(18):11157–11180
Yan X, Lu Y, Liu L, Song X (2020) Reversible image secret sharing. IEEE Trans Inf Forensic Secur 15:3848–3858
Yan X, Lu Y, Liu L, Wan S, Ding W, Liu H (2020) Exploiting the homomorphic property of visual cryptography. In: Cryptography: Breakthroughs in Research and Practice. IGI Global, pp 416–427
Yang C-N, Yang Y-Y (2014) New extended visual cryptography schemes with clearer shadow images. Inf Sci 271:246–263
Zxing library (2021). https://github.com/zxing/zxing
Funding
This work is supported by the National Natural Science Foundation of China (61872085), the Natural Science Foundation of Fujian Province (2018J01638) and the Fujian Provincial Department of Science and Technology (2018Y3001).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interests
The authors declare that they have no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Liu, T., Yan, B., Yang, HM. et al. A fake threshold visual cryptography of QR code. Multimed Tools Appl 81, 39635–39653 (2022). https://doi.org/10.1007/s11042-022-13011-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-13011-x