Abstract
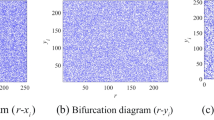
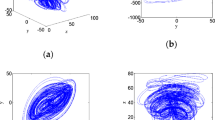
In nonlinear dynamical systems, chaotic behavior is an attractive characteristic that has been broadly examined and researched over the most recent few decades. The chaotic systems are widely used in artificial intelligence and cryptology. Especially, these are considered efficient for multimedia data security. This manuscript has introduced a novel three dimensional (3-D) chaotic systems. The proposed maps are investigated through bifurcation diagrams and phase plots. The resulting diagrams demonstrates the chaotic attractor characteristic and the dynamic behavior of the suggested maps. Furthermore, a lossless audio encryption scheme is introduced utilizing the proposed chaotic maps. In the suggested scheme, the suggested 3-D chaotic sequences are utilized to shuffle the audio data points to achieve the diffusion property. In the confusion module, initially, the sequence of the audio data is divided into 8-bit and 7-bit sequences. Subsequently, the separated sequences are then substituted with different good quality substitution boxes, which are generated through a Mobius transformation over Galois fields. The suggested encryption algorithm is applied to the different audio files of various sizes and characters. The experimental results have revealed that the proposed scheme is capable to secure all kinds of audio files. The security analysis shows that the suggested scheme is capable to withstand differential and statistical attacks.







Similar content being viewed by others
References
Arshad U et al (2019) An efficient image privacy scheme based on nonlinear chaotic system and linear canonical transformation. Physica A: Statistical Mechanics and its Applications:123458
Arshad U et al (2019) An efficient image privacy scheme based on nonlinear chaotic system and linear canonical transformation. Physica A: Statistical Mechanics and its Applications:123458
Bhargava B, Shi C, Wang S-Y (2004) MPEG video encryption algorithms. Multimed Tools Appl 24(1):57–79
Conrad E (1997) Advanced encryption standard. White Paper
Farah MAB, Kachouri A, Samet M (2011) Improvement of cryptosystem based on iterating chaotic map. Commun Nonlinear Sci Numer Simul 16(6):2543–2553
Farah MAB et al (2020) A new design of cryptosystem based on S-box and chaotic permutation. Multimed Tools Appl:1–22
Farsana FJ, Devi VR, Gopakumar K (2019) An audio encryption scheme based on fast Walsh Hadamard transform and mixed chaotic keystreams. Applied Computing and Informatics
Grangetto M, Magli E, Olmo G (2006) Multimedia selective encryption by means of randomized arithmetic coding. IEEE Trans Multimed 8(5):905–917
Habib Z, (2017) Secure speech communication algorithm via DCT and TD-ERCS chaotic map. 4th international conference on electrical and electronic engineering (ICEEE). IEEE, 2017.
Haider MI, et al. (2020) Block cipher’s nonlinear component design by elliptic curves: an image encryption application. Multimed Tools Appl: 1–26.
Hussain, Sadam, et al. (2020) A power associative loop structure for the construction of non-linear components of block cipher. IEEE Access
Jahangir S, Shah T (2020) Designing S-boxes triplet over a finite chain ring and its application in RGB image encryption. Multimed Tools Appl 79:26885–26911
Kalpana M, Ratnavelu K, PagavathiBalasubramaniam (2019) An audio encryption based on synchronization of robust BAM FCNNs with time delays. Multimed Tools Appl 78(5):5969–5988
Khan M, Masood F (2019) A novel chaotic image encryption technique based on multiple discrete dynamical maps. Multimed Tools Appl 78(18):26203–26222
Khan M, Hussain I, Jamal SS, Amin M (2019) A privacy scheme for digital images based on quantum particles. Int J Theor Phys 58(12):4293–4310
Kordov K (2019) A novel audio encryption algorithm with permutation-substitution architecture. Electronics 8(5):530
Lima JB, da Silva Neto EF (2016) Audio encryption based on the cosine number transform. Multimed Tools Appl 75(14):8403–8418
Lima JB, da Silva EF, Neto (2016) Audio encryption based on the cosine number transform. Multimed Tools Appl 75(14):8403–8418
Madain A, Abu Dalhoum AL, Hiary H, Ortega A, Alfonseca M (2014) Audio scrambling technique based on cellular automata. Multimed Tools Appl 71(3):1803–1822
Min L, et al. (2013) A novel 3 dimensional chaotic system and design of pseudorandom number generator. Ninth International Conference on Computational Intelligence and Security. IEEE, 2013.
Mosa E et al (2011) Chaotic encryption of speech signals. Int J Speech Technol 14(4):285
Naseer Y, Shah D, Shah T (2019) A novel approach to improve multimedia security utilizing 3D mixed chaotic map. Microprocess Microsyst 65:1–6
Naskar PK, Paul S, Nandy D, Chaudhuri A (2019) DNA encoding and channel shuffling for secured encryption of audio data. Multimed Tools Appl 78(17):25019–25042
Rivest RL (1994) The RC5 encryption algorithm. International Workshop on Fast Software Encryption. Springer, Berlin, Heidelberg
Sathiyamurthi P, Ramakrishnan S (2017) Speech encryption using chaotic shift keying for secured speech communication. EURASIP Journal on Audio, Speech, and Music Processing 2017(1):1–11
Sathiyamurthi P, Ramakrishnan S (2017) Speech encryption using chaotic shift keying for secured speech communication. EURASIP Journal on Audio, Speech, and Music Processing 1(2017):20
Servetti A, De Martin JC (2002) Perception-based partial encryption of compressed speech. IEEE Trans Speech Audio Process 10(8):637–643
Servetti A, Testa C, De Martin JC (2003) Frequency-selective partial encryption of compressed audio. IEEE International Conference on Acoustics, Speech, and Signal Processing, 2003. Proceedings.(ICASSP'03).. Vol. 5. IEEE
Shah T, Shah D (2019) Construction of highly nonlinear S-boxes for degree 8 primitive irreducible polynomials over ℤ 2. Multimed Tools Appl 78(2):1219–1234
Shah D, Shah T (2020) Binary Galois field extensions dependent multimedia data security scheme. Microprocess Microsyst 103181
Shah T, Haq TU, Farooq G (2020) Improved SERPENT algorithm: design to RGB image encryption implementation. IEEE Access 8:52609–52621
Standard, Data Encryption (1977) Federal information processing standards publication 46. National Bureau of Standards, US Department of Commerce 23
Thorwirth NJ, et al. (2000) Security methods for MP3 music delivery. Conference Record of the Thirty-Fourth Asilomar Conference on Signals, Systems and Computers (Cat. No. 00CH37154). Vol. 2. IEEE
Ul Haq T, Shah T (2020) 12× 12 S-box design and its application to RGB image encryption. Optik:164922
Ullah A, Jamal SS, Shah T (2018) A novel scheme for image encryption using substitution box and chaotic system. Nonlinear Dynamics 91(1):359–370
Ullah A, Javeed A, Shah T (2019) A scheme based on algebraic and chaotic structures for the construction of substitution box. Multimed Tools Appl 78(22):32467–32484
Waseem HM, Khan M, Shah T (2018) Image privacy scheme using quantum spinning and rotation. Journal of Electronic Imaging 27(6):063022
Waseem HM, Alghafis A, Khan M (2020) An efficient public key cryptosystem based on dihedral group and quantum spin states. IEEE Access 8:71821–71832
Yan W-Q, Wei-Gang F, Kankanhalli MS (2008) Progressive audio scrambling in compressed domain. IEEE Transactions on Multimedia 10(6):960–968
Zhou J, Au OC (2010) Security and efficiency analysis of progressive audio scrambling in compressed domain. IEEE International Conference on Acoustics, Speech and Signal Processing. IEEE, 2010.
Zimmermann R, Curiger A, Bonnenberg H, Kaeslin H, Felber N, Fichtner W (1994) A 177 Mb/s VLSI implementation of the international data encryption algorithm. IEEE J Solid State Circuits 29(3):303–307
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Shah, D., Shah, T., Ahamad, I. et al. A three-dimensional chaotic map and their applications to digital audio security. Multimed Tools Appl 80, 22251–22273 (2021). https://doi.org/10.1007/s11042-021-10697-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-021-10697-3