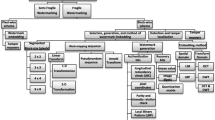
Abstract
Ensuring the image content authentication is a necessity need when images are used as supporting evidence in critical applications such as law enforcement, medical diagnosis, news reporting, and forensic investigation. Fragile watermarking is an effective solution for ensuring image content authentication. This paper presents a survey on fragile watermarking schemes for tamper localization and self-recovery. The characteristics and general framework are included to get an overview of these schemes. A brief review and comparison of various fragile watermarking schemes along with their merits and limitations are also given. The observations drawn from the comparative study are included to aid further research in this area. In addition to this, experimental evaluation of state-of-the-art tamper localization and self-recovery schemes in terms of watermarked image quality, tamper localization accuracy, and recovery capability is carried out.




Similar content being viewed by others
References
Ansari IA, Pant M, Ahn CW (2015) Svd based fragile watermarking scheme for tamper localization and self-recovery. Int J Mach Learn Cybern 7 (6):1225–1239
Azeroual A, Afdel K (2017) Real-time image tamper localization based on fragile watermarking and faber-schauder wavelet. AEU-Int J Electron Commun 79:207–218
Benrhouma O, Hermassi H, Belghith S (2017) Security analysis and improvement of an active watermarking system for image tampering detection using a self-recovery scheme. Multimed Tools Appl 76(20):21,133–21,156
Bravo-Solorio S, Calderon F, Li C, Nandi AK (2018) Fast fragile watermark embedding and iterative mechanism with high self-restoration performance. Digit Sig Process 73:83–92
Celik MU, Sharma G, Saber E, Tekalp AM (2002) Hierarchical watermarking for secure image authentication with localization. IEEE Trans Image Process 11(6):585–595
Chang CC, Chen KN, Lee CF, Liu LJ (2011) A secure fragile watermarking scheme based on chaos-and-hamming code. J Syst Softw 84(9):1462–1470
Chang CC, Fan YH, Tai WL (2008) Four-scanning attack on hierarchical digital watermarking method for image tamper detection and recovery. Pattern Recogn 41(2):654–661
Chang CC, Hu YS, Lu TC (2006) A watermarking-based image ownership and tampering authentication scheme. Pattern Recogn Lett 27(5):439–446
Dadkhah S, Manaf AA, Hori Y, Hassanien AE, Sadeghi S (2014) An effective svd-based image tampering detection and self-recovery using active watermarking. Sig Process Image Commun 29(10):1197–1210
Fridrich J (2002) Security of fragile authentication watermarks with localization. In: Security and watermarking of multimedia contents IV. International society for optics and photonics, vol 4675, pp 691–700
Fridrich J, Goljan M (1999) Images with self-correcting capabilities. In: Proceedings 1999 international conference on image processing 1999. ICIP 99, vol 3. IEEE, pp 792–796
Fridrich J, Goljan M, Memon N (2002) Cryptanalysis of the yeung-mintzer fragile watermarking technique. J Electron Imaging 11(2):262–275
Geetha R, Geetha S (2020) Embedding electronic patient information in clinical images: an improved and efficient reversible data hiding technique. Multimed Tools Appl 79:1–22
Gonzalez R, Woods R, Eddins S (2020) Image databases. http://www.imageprocessingplace.com. Accessed on August
Gul E, Ozturk S (2019) A novel hash function based fragile watermarking method for image integrity. Multimed Tools Appl 78:1–18
Gull S, Loan NA, Parah SA, Sheikh JA, Bhat G (2018) An efficient watermarking technique for tamper detection and localization of medical images. J Ambient Intell Humaniz Comput 11:1–10
Haghighi BB, Taherinia AH, Harati A (2018) Trlh: Fragile and blind dual watermarking for image tamper detection and self-recovery based on lifting wavelet transform and halftoning technique. J Vis Commun Image Represent 50:49–64
He H, Chen F, Tai HM, Kalker T, Zhang J (2012) Performance analysis of a block-neighborhood-based self-recovery fragile watermarking scheme. IEEE Trans Inform Forensic Secur 7(1):185–196
He H, Zhang J (2012) Cryptanalysis on majority-voting based self-recovery watermarking scheme. Telecommun Syst 49(2):231–238
He HJ, Zhang JS, Chen F (2009) Adjacent-block based statistical detection method for self-embedding watermarking techniques. Sig Process 89 (8):1557–1566
Holliman M, Memon N (2000) Counterfeiting attacks on oblivious block-wise independent invisible watermarking schemes. IEEE Trans Image Process 9(3):432–441
Hong W, Chen M, Chen TS (2017) An efficient reversible image authentication method using improved pvo and lsb substitution techniques. Sig Process Image Commun 58:111–122
Hsu CS, Tu SF (2010) Probability-based tampering detection scheme for digital images. Opt Commun 283(9):1737–1743
Huang SC, Jiang CF (2012) A color image authentication and recovery method using block truncation code embedding. J Mar Sci Technol 20(1):49–55
Kim C, Shin D, Yang CN (2018) Self-embedding fragile watermarking scheme to restoration of a tampered image using ambtc. Pers Ubiquit Comput 22 (1):11–22
Korus P, Dziech A (2013) Efficient method for content reconstruction with self-embedding. IEEE Trans Image Process 22(3):1134–1147
Lee TY, Lin SD (2008) Dual watermark for image tamper detection and recovery. Pattern Recogn 41(11):3497–3506
Li C, Wang Y, Ma B, Zhang Z (2013) Multi-block dependency based fragile watermarking scheme for fingerprint images protection. Multimed Tools Appl 64(3):757–776
Lin PL, Hsieh CK, Huang PW (2005) A hierarchical digital watermarking method for image tamper detection and recovery. Pattern Recognit 38 (12):2519–2529
Neena Raj NR, Shreelekshmi R (2018) Blockwise fragile watermarking schemes for tamper localization in digital images. In: International conference on control, communication, and computing (IC4). IEEE, pp 441–446
Neena Raj NR, Shreelekshmi R (2019) Security analysis of hash based fragile watermarking scheme for image integrity. In: 2019 2nd international conference on intelligent computing, instrumentation and control technologies (ICICICT), vol 1. IEEE, pp 651–654
Parah SA, Ahad F, Sheikh JA, Bhat GM (2017) Hiding clinical information in medical images: a new high capacity and reversible data hiding technique. J Biomed Inform 66:214–230
Phan RCW (2008) Tampering with a watermarking-based image authentication scheme. Pattern Recogn 41(11):3493–3496
Prasad S, Pal AK (2020) Hamming code and logistic-map based pixel-level active forgery detection scheme using fragile watermarking. Multimed Tools Appl 79(29):20897–20928
Prasad S, Pal AK (2020) A tamper detection suitable fragile watermarking scheme based on novel payload embedding strategy. Multimed Tools Appl 79(3):1673–1705
Qin C, Ji P, Chang CC, Dong J, Sun X (2018) Non-uniform watermark sharing based on optimal iterative btc for image tampering recovery. IEEE Multimed 25(3):36–48
Qin C, Wang H, Zhang X, Sun X (2016) Self-embedding fragile watermarking based on reference-data interleaving and adaptive selection of embedding mode. Inform Sci 373:233–250
Rajput V, Ansari IA (2019) Image tamper detection and self-recovery using multiple median watermarking. Multimed Tools Appl 79:1–17
Rawat S, Raman B (2011) A chaotic system based fragile watermarking scheme for image tamper detection. AEU-Int J Electron Commun 65(10):840–847
Sarreshtedari S, Akhaee MA (2015) A source-channel coding approach to digital image protection and self-recovery. IEEE Trans Image Process 24 (7):2266–2277
Shehab A, Elhoseny M, Muhammad K, Sangaiah AK, Yang P, Huang H, Hou G (2018) Secure and robust fragile watermarking scheme for medical images. IEEE Access 6:10269–10278
Singh D, Singh SK (2016) Effective self-embedding watermarking scheme for image tampered detection and localization with recovery capability. J Vis Commun Image Represent 38:775–789
Singh D, Singh SK (2017) Dct based efficient fragile watermarking scheme for image authentication and restoration. Multimed Tools Appl 76(1):953–977
Singh D, Singh SK (2019) Block truncation coding based effective watermarking scheme for image authentication with recovery capability. Multimed Tools Appl 78(4):4197–4215
Sreenivas K, Prasad VK (2018) Fragile watermarking schemes for image authentication: a survey. Int J Mach Learn Cybern 9(7):1193–1218
Tai WL, Liao ZJ (2018) Image self-recovery with watermark self-embedding. Signal Process Image Commun 65:11–25
Tong X, Liu Y, Zhang M, Chen Y (2013) A novel chaos-based fragile watermarking for image tampering detection and self-recovery. Sig Process Image Commun 28(3):301–308
Walton S (1995) Image authentication for a slippery new age. Dr Dobb’s J 20(4):18–26
Wang MS, Chen WC (2007) A majority-voting based watermarking scheme for color image tamper detection and recovery. Comput Stand Interfaces 29 (5):561–570
Wang C, Zhang H, Zhou X (2018) A self-recovery fragile image watermarking with variable watermark capacity. Appl Sci 8(4):548
Wong PW (1998) A public key watermark for image verification and authentication. In: Proceedings international conference on image processing (ICIP), vol 1, IEEE, pp 455–459
Wong PW (1998) A watermark for image integrity and ownership verification. In: PICS, pp 374–379
Wong PW, Memon N (2001) Secret and public key image watermarking schemes for image authentication and ownership verification. IEEE Trans Image Process 10(10):1593–1601
Yeung MM, Mintzer F (1997) An invisible watermarking technique for image verification. In: Proceedings international conference on image processing (ICIP), vol 2. IEEE, pp 680–683
Zhang X, Wang S (2008) Fragile watermarking with error-free restoration capability. IEEE Trans Multimed 10(8):1490–1499
Zhang X, Wang S, Qian Z, Feng G (2011) Reference sharing mechanism for watermark self-embedding. IEEE Trans Image Process 20(2):485–495
(2020) The cvg-ugr image database. http://decsai.ugr.es/cvg/dbimagenes, Accessed on August
Acknowledgements
Authors extend gratitude to the Department of Higher Education, Government of Kerala, for granting the research fellowship.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Raj, N.R.N., Shreelekshmi, R. A survey on fragile watermarking based image authentication schemes. Multimed Tools Appl 80, 19307–19333 (2021). https://doi.org/10.1007/s11042-021-10664-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-021-10664-y