Abstract
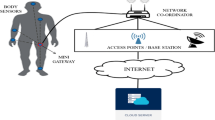
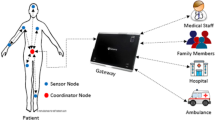
Wireless body area networks (WBANs) comprises a number of sensor nodes and the portable mobile device such as smartphone. It is used to monitor the physical condition and provide a reliable healthcare system. Utilizing the wireless communication network, sensor nodes collect the physiological data of one patient to the portable mobile device and the latter analyzes and transmits them to the application providers. Therefore, the personal data confidentiality and user privacy are cores of WBANs. Recently, Shen et al. presented a multi-layer authentication protocol for WBANs, which is lightweight and much easier to implement. However, we observe that their authentication between sensor nodes and the portable mobile device could ensure the forward security property only when the sensor nodes are changed (add or delete). When the sensor nodes are constant, the security property is not satisfied. Meanwhile, the authentication between the portable mobile device and application provider is prone to mutual impersonation attack, so the critical goal of mutual authentication can not be achieved. In this paper, an improved two-layer authentication scheme is proposed to remove the flaws. The analysis shows that our method is more secure and could withstand various attacks.







Similar content being viewed by others
References
Al-Riyami, S.S., and Paterson, K.G., Certificateless public key cryptography. Berlin: Springer, 2003.
Ali, A., and Khan, F.A., Energy-efficient cluster-based security mechanism for intra-wban and inter-wban communications for healthcare applications. Eurasip. J. Wirel. Comm. 2013(1):1–19, 2013.
Amin, R., and Biswas, G.P., A novel user authentication and key agreement protocol for accessing multi-medical server usable in tmis. J. Med. Syst. 39(3):33, 2015.
Amin, R., Islam, S.H., Biswas, G.P., Khan, M.K., and Kumar, N., An efficient and practical smart card based anonymity preserving user authentication scheme for tmis using elliptic curve cryptography. J. Med. Syst. 39(11):180, 2015.
Amin, R., Islam, S.H., Biswas, G.P., and Obaidat, M.S., A robust mutual authentication protocol for wsn with multiple base-stations. Ad. Hoc. Netw. 75-76:1–18, 2018.
Amin, R., Islam, S.H., Kumar, N., and Choo, K.R., An untraceable and anonymous password authentication protocol for heterogeneous wireless sensor networks. J. Netw. Comput. Appl. 104:133–144, 2018.
Delmastro, F., Arnaboldi, V., and Conti, M., People-centric computing and communications in smart cities. IEEE Commun. Mag. 54(7):122–128, 2016.
Dent, A.W., A survey of certificateless encryption schemes and models. Int. J. Inf. Secur. 7(5):349–377, 2008.
Diffie, W., and Hellman, M., New directions in cryptography. IEEE T Inform. Theory 22(6):644–654, 1976.
Fujisaki, E., and Okamoto, T., Secure integration of asymmetric and symmetric encryption schemes. J. Cryptol. 26(1):80–101, 2013.
Gura, N., Patel, A., Wander, A., Eberle, H., and Shantz, S.C., Comparing elliptic curve cryptography and RSA on 8-bit CPUs. Berlin: Springer, 2004.
Hankerson, D., Vanstone, S., and Menezes, A., Guide to elliptic curve cryptography. New York: Springer, 2004.
Hanson, M.A., Powell, H.C., Barth, A.T., Ringgenberg, K., Calhoun, B.H., Aylor, J.H., and Lach, J., Body area sensor networks: challenges and opportunities. Computer 42(1):58–65, 2009.
He, D.B., Wang, H.Q., Zhang, J.H., and Wang, L., Insecurity of an identity-based public auditing protocol for the outsourced data in cloud storage. Inf. Sci. 375:48–53, 2017.
He, D.B., Zeadally, S., Kumar, N., and Lee, J.H., Anonymous authentication for wireless body area networks with provable security. IEEE Syst. J. 11(4):2590–2601, 2017.
Javadi, S.S., and Razzaque, M.A., Security and privacy in wireless body area networks for health care applications. Berlin: Springer, 2013.
Jiang, Q., Lian, X.X., Yang, C., Ma, J.F., Tian, Y.L., and Yang, Y.Y., A bilinear pairing based anonymous authentication scheme in wireless body area networks for mhealth. J. Med. Syst. 40(11):231, 2016.
Johny, B., and Anpalagan, A., Body area sensor networks: requirements, operations, and challenges. IEEE Potentials 33(2):21–25, 2014.
Koblitz, N., Elliptic curve cryptosystems. Math. Comput. 48(177):203–209, 1987.
Latré, B, Braem, B., Moerman, I., Blondia, C., and Demeester, P., A survey on wireless body area networks. Wirel. Netw. 17(1):1–18, 2011.
Li, F.G., and Hong, J.J., Efficient certificateless access control for wireless body area networks. IEEE Sens. J. 16(13):5389–5396, 2016.
Li, F.G., Zheng, Z.H., and Jin, C.H., Secure and efficient data transmission in the internet of things. Telecommun. Syst. 62(1):111–122, 2016.
Li, F.G., Han, Y.N., and Jin, C.H., Cost-effective and anonymous access control for wireless body area networks. IEEE Syst. J. 12(1):747–758, 2018.
Li, M., Lou, W.J., and Ren, K., Data security and privacy in wireless body area networks. IEEE Wirel. Commun. 17(1):51–58, 2010.
Li, M., Yu, S.C., Lou, W.J., and Ren, K.: Group device pairing based secure sensor association and key management for body area networks. In: International conference on computer communications, pp 2651–2659, 2010
Li, X., Peng, J.Y., Kumari, S., Wu, F., Karuppiah, M., and Choo, K.R., An enhanced 1-round authentication protocol for wireless body area networks with user anonymity. Comput. Electr. Eng. 61:238–249, 2017.
Liu, J.W., Zhang, Z.H., Chen, X.F., and Kwak, K.S., Certificateless remote anonymous authentication schemes for wirelessbody area networks. IEEE T Parall. Distr. 25(2):332–342, 2014.
Liu, J.W., Zhang, L.H., and Sun, R., 1-raap: an efficient 1-round anonymous authentication protocol for wireless body area networks. Sensors 16(5):728, 2016.
Liu, Y.L., and Liu, G.Y., User-centric wireless network for 5G. Cham: Springer, 2017.
Lu, R.X., Lin, X.D., Zhu, H.J., Ho, P.H., and Shen, X.M., A novel anonymous mutual authentication protocol with provable link-layer location privacy. IEEE T. Veh. Technol. 58(3):1454–1466, 2009.
Miller, V.S., Use of elliptic curves in cryptography. Berlin: Springer, 1986.
Mondal, S., Mohanty, S.K., and Nandi, S., Energy efficient secure communication architecture for wireless sensor network. Secur. Commun. Netw. 9(16):3314–3323, 2016.
Movassaghi, S., Abolhasan, M., Lipman, J., Smith, D., and Jamalipour, A., Wireless body area networks: a survey. IEEE Commun. Surv. Tut. 16(3):1658–1686, 2014.
Omala, A.A., Kibiwott, K.P., and Li, F.G., An efficient remote authentication scheme for wireless body area network. J. Med. Syst. 41(2):25, 2017.
Pardo, J.L., Identity-based cryptography. Berlin: Springer, 2013.
Salomaa, A., Public-key cryptography. Berlin: Springer, 1990.
Shamir, A., Identity-based cryptosystems and signature schemes. Berlin: Springer, 1985.
Shen, J., Chang, S.H., Shen, J., Liu, Q., and Sun, X.M., A lightweight multi-layer authentication protocol for wireless body area networks. Future Gener. Comp. Sy. 78(3):956–963, 2018.
Tan, C.C., Wang, H., Zhong, S., and Li, Q., Ibe-lite: a lightweight identity-based cryptography for body sensor networks. IEEE T. Inf. Technol. B 13(6):926–932, 2009.
Tobón, D P, Falk, T.H., and Maier, M., Context awareness in wbans: a survey on medical and non-medical applications. IEEE Wirel. Commun. 20(4):30–37, 2013.
Wang, C.Z., and Zhang, Y.M., New authentication scheme for wireless body area networks using the bilinear pairing. J. Med. Syst. 39(11):136, 2015.
Xiong, H., Cost-effective scalable and anonymous certificateless remote authentication protocol. IEEE T. Inf. Foren. Sec. 9(12):2327–2339, 2014.
Xiong, H., and Qin, Z.G., Revocable and scalable certificateless remote authentication protocol with anonymity for wireless body area networks. IEEE T. Inf. Foren. Sec. 10(7):1442–1455, 2015.
Zhang, F.T., Sun, Y.X., Zhang, L., Geng, M.M., and Li, S.J., Research on certificateless public key cryptography. J. Softw. 22(6):1316–1332, 2011.
Zhao, Z., An efficient anonymous authentication scheme for wireless body area networks using elliptic curve cryptosystem. J. Med. Syst. 38(2):13, 2014.
Funding
This work is supported by the Key Fund Project of Sichuan Provincial Department of Education (No: 17ZA0414), and the Laboratory for Internet of Things and Mobile Internet Technology of Jiangsu Province (No: JSWLW-2017-006).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interests
The authors declare that we have no conflicts of interest.
Additional information
Ethical Approval
This article does not contain any studies with human participants or animals performed by any of the authors.
This article is part of the Topical Collection on Mobile & Wireless Health
Rights and permissions
About this article
Cite this article
Liu, X., Jin, C. & Li, F. An Improved Two-Layer Authentication Scheme for Wireless Body Area Networks. J Med Syst 42, 143 (2018). https://doi.org/10.1007/s10916-018-0990-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-018-0990-x