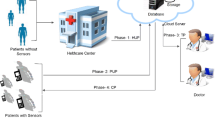
Abstract
Unlike the traditional medical system, telecare medicine information system (TMIS) ensures that patients can get health-care services via the Internet at home. Authenticated key agreement protocol is very important for protecting the security in TMIS. Recently scholars have proposed a lot of authenticated key agreement protocols. In 2016, Chiou et al. demonstrated that Chen et al.’s authentication scheme fails to provide user’s anonymity and message authentication and then proposed an enhanced scheme (Chiou et al., J. Med. Syst. 40(4):1–15, 2006) to overcome these drawbacks. In this paper, we demonstrate that Chiou et al.’s scheme is defenseless against key compromise impersonation (KCI) attack and also fails to provide forward security. Moreover, we propose a novel authentication scheme namely ICASME to overcome the mentioned weaknesses in this paper. Security analyses show that ICASME achieves the forward security and KCI attack resistance. In addition, it is proved that the time taken to implement the ICASME is not intolerable compared to the original protocol.








Similar content being viewed by others
References
Rashvand, H., Salcedo, V., Sanchez, E., and Iliescu, D., Ubiquitous Wireless Telemedicine. IET Communications 2(2):237–254, 2008.
Xia, Z., Wang, X., Sun, X., and Wang, Q., A Secure and Dynamic Multi-keyword Ranked Search Scheme over Encrypted Cloud Data. IEEE Transactions on Parallel and Distributed Systems 27(2):340–352, 2016.
He, D., Zeadally, S., and Wu, L., Certificateless Public Auditing Scheme for Cloud-assisted Wireless Body Area Networks. IEEE Systems Journal. doi:10.1109/JSYST.2015.2428620, 2015.
He, D., and Wang, D., Robust Biometrics-based Authentication Scheme for Multi-server Environment. IEEE Systems Journal 9(3):816–823, 2015.
He, D., Neeraj, K., Naveen, C., A Secure Temporal-credential-based Mutual Authentication and Key Agreement Scheme with Pseudo Identity for Wireless Sensor Networks. Information Sciences 321:263–277, 2015.
Hassan, M. M., Lin, K., and et al., A Multimedia Healthcare Data Sharing Approach Through Cloud-based Body Area Network. Future Generation Computer Systems 66(1):48–58, 2017.
Jiang, Q., Wei, S., and et al., Robust Extended Chaotic Maps-based Three-factor Authentication Scheme Preserving Biometric Template Privacy. Nonlinear Dynamics 83(4):2085–2101, 2016.
Lamport, L., Password Authentication with Insecure Communication. Communications of the ACM 24(24): 770–772, 1981.
Lee, J. K., Ryu, S. R., and Yoo, K. Y., Fingerprint-based Remote User Authentication Scheme Using Smart Cards. Electronics Letters 38(12):554–555, 2002.
Lin, C. H., and Lai, Y. Y., A Flexible Biometrics Remote User Authentication Scheme. Computer Standards & Interfaces 27(1):19–23, 2004.
Das, A. K., Analysis and Improvement on an Efficient Biometric-based Remote User Authentication Scheme Using Smart Cards. IET Information Security 5(3):145–151, 2011.
Tan, Z. W., An Efficient Biometric-based Authentication Scheme for Telecare Medicine Information Systems. Przeglad Elektrotechniczny 89(5):200–204, 2013.
Jiang, Q., Ma, J., and et al., Improvement of Robust Smart-card-based Password Authentication Scheme. International Journal of Communication Systems 28(2):383–393, 2015.
David, D. B., Rajappa, M., Karupuswamy, T., and et al., A Dynamic-Identity Based Multimedia Server Client Authentication Scheme for Tele-Care Multimedia Medical Information System. Wireless Personal Communications 85(1):241–261, 2015.
Chiou, S. Y., Ying, Z., and Liu, J., Improvement of a Privacy Authentication Scheme Based on Cloud for Medical Environment. J. Med. Syst. 40(4):1–15, 2016.
Fu, Z., Wu, X., Guan, C., and et al., Towards Efficient Multi-keyword Fuzzy Search over Encrypted Outsourced Data with Accuracy Improvement. IEEE Transactions on Information Forensics and Security 11(12):2706–2716, 2016.
He, D., and Zeadally, S., Authentication Protocol for Ambient Assisted Living System. IEEE Communications Magazine 35(1):71–77, 2015.
Jiang, Q., Muhammad, K., and et al., A Privacy Preserving Three-factor Authentication Protocol for E-health Clouds. Journal of Supercomputing 72(10):3826–3849, 2016.
He, D., Sherali, Z., Neeraj, K., Lee, J.: Anonymous Authentication for Wireless Body Area Networks with Provable Security. IEEE Systems Journal. doi:10.1109/JSYST.2016.2544805, 2016.
Zhang, L., Zhu, S., and Tang, S., Privacy Protection for Telecare Medicine Information Systems using a Chaotic Map-based Three-factor Authenticated Key Agreement Scheme. IEEE Journal of Biomedical & Health Informatics. doi:10.1109/JBHI.2016.2517146, 2016.
Colin, B., and Anish, M., Protocols for Authentication and Key Establishment. Springer (2003)
Menezes, A. J., Vanstone, S. A., and Oorschot, P.C.V., Handbook of Applied Cryptography. CRC Press, 1997.
Anderson, R., Two Remarks on Public-Key Cryptology. Proceedings of CCCS: Invited lecture, 1997.
Bellare, M., and Rogaway, P., Random Oracles are Practical: a Paradigm for Designing Efficient Protocols. In: Proceedings of the First ACM conference on Computer and communications security. 62–73, 1993.
He, D., Kumar, N., Khan, M. K., and Lee, J. H., Anonymous Two-factor Authentication for Consumer Roaming Service in Global Mobility Networks. IEEE Transactions on Consumer Electronics 59(4):811–817, 2013.
Jiang, Q., Ma, J., Li, G., and Yang, L., An Efficient Ticket Based Authentication Protocol with Unlinkability for Wireless Access Networks. Wireless Personal Communications 77(2):1489–1506, 2014.
Acknowledgment
The authors express their deep appreciation to the helpful comments and suggestions of the anonymous reviewers, which have improved the presentation. This work was was funded by the National High Technology Research and Development Program (863 Program) (No. 2015AA016007 & No. 2015AA017203).
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Mobile & Wireless Health
Rights and permissions
About this article
Cite this article
Cheng, Q., Zhang, X. & Ma, J. ICASME: An Improved Cloud-Based Authentication Scheme for Medical Environment. J Med Syst 41, 44 (2017). https://doi.org/10.1007/s10916-017-0693-8
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-017-0693-8