Abstract
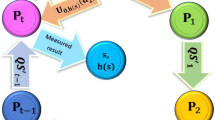
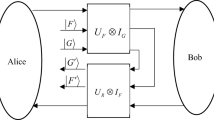
In this paper, we propose a novel verifiable quantum secret sharing scheme tailored for a specific class of low-density parity-check (LDPC) codes. In the proposed protocol, Alice, the dealer, initially utilizes the generator matrix of the chosen LDPC code to calculate all secret shares and distributes individual shares to all participants in a quantum secure direct communication channel. In the distribution phase, each participant computes a hash value based on their respective share and a randomly generated sequence, which is then published. In the recover phase, each participant performs a unitary operation on these received particles and sends them to the next participant using the decoy-photon technique. Furthermore, the last participant performs Bell measurements on the final quantum states to obtain the original secret. At last, we demonstrate our protocol to be secure against intercept-and-resend attack, entangle-and-measure attack and dishonest participant attack. In addition, we present a comparison of our protocol with other existing schemes.



Similar content being viewed by others
Data Availability
The data sets generated during and/or analysed during the current study are available from the corresponding author on reasonable request.
References
Cabello, A.: Quantum key distribution in the Holevo limit. Phys. Rev. Lett. 85(26), 5635 (2000)
Zhou, N., Zeng, G., Xiong, J.: Quantum key agreement protocol. Electron. Lett. 40(18), 1 (2004)
Yang, Y.G., Lv, X.L., Gao, S., et al.: Detector-device-independent quantum key agreement based on single-photon bell state measurement. Int. J. Theor. Phys. 61(2), 1–16 (2022)
Sheng, Y.B., Zhou, L., Long, G.L.: One-step quantum secure direct communication. Sci. Bull. 67(4), 367–374 (2022)
Hillery, M., Buzek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59, 1829 (1999)
Cleve, R., Gottesman, D., Lo, H.-K.: How to share a quantum secret. Phys. Rev. Lett. 83, 648 (1999)
Gottesman, D.: Theory of quantum secret sharing. Phys. Rev. A 61, 042311 (2000)
Lipinska, V., Murta, G., Ribeiro, J., Wehner, S.: Verifiable hybrid secret sharing with few qubits. Phys. Rev. A 101, 032332 (2020)
Li, F., Chen, T., Zhu, S.: Dynamic \((t, n)\) threshold quantum secret sharing based on d-dimensional Bell state. Physica A Stat. Mech. Appl. 606, 128122 (2022)
Yang, C.W., Tsai, C.W.: Improved dynamic multiparty quantum direct secret sharing protocol based on generalized GHZ states to prevent collusion attack. Mod. Phys. Lett. A 35(8), 2050040 (2020)
Yang, C.W., Tsai, C.W.: Participant attack and improving dynamic quantum secret sharing using d-dimensional GHZ state. Mod. Phys. Lett. A 35(6), 2050024 (2020)
Shamir, A.: How to share a secret. Commun. ACM 22(11), 612 (1979)
Blakley, G.R.: in Proceedings of the National Computer Conference (AFIPS, 1979), pp. 313–317 (1979)
Wootters, W.K., Zurek, W.H.: A single quantum cannot be cloned. Nature 299(5886), 802–803 (1982)
Xiao, L., Long, G.L., Deng, F.G., Pan, J.W.: Efficient multiparty quantum-secret-sharing schemes. Phys. Rev. A 69, 052307 (2004)
Grice, W.P., Qi, B.: Quantum secret sharing using weak coherent states. Phys. Rev. A 100, 022339 (2019)
Qin, H.W., Zhu, X.H., Dai, Y.W.: \((t, n)\) threshold quantum secret sharing using the phase shift operation. Quantum Inf Process 14, 2997–3004 (2015)
Maitra, A., De, S.J., Paul, G., Pal, A.K.: Proposal for quantum rational secret sharing. Phys. Rev. A 92, 022305 (2015)
Gu, J., Cao, X.Y., Yin, H.L., et al.: Differential phase shift quantum secret sharing using a twin field. Optics Express 29(6), 9165–9173 (2021)
Mashhadi, S.: Improvement of a \((t, n)\) threshold d-level quantum secret sharing scheme. Journal of Applied Security Research 17(1), 123–134 (2022)
Bai, C.M., Li, Z.H., Wang, J.T., et al.: Restricted (k, n)-threshold quantum secret sharing scheme based on local distinguishability of orthogonal multiqudit entangled states. Quantum Inf Process 17(11), 312 (2018)
Li, F., Luo, M., Zhu, H., et al.: A \((w, t, n)\)-weighted threshold dynamic quantum secret sharing scheme with cheating identification. Physica A Stat. Mech. Appl. 612, 128494 (2023)
Li, L., Li, Z.: An efficient quantum secret sharing scheme based on restricted threshold access structure. Entropy 25(2), 265 (2023)
Jia, H.Y., Wen, Q.Y., Gao, F., Qin, S.J., Guo, F.Z.: Dynamic quantum secret sharing. Phys. Lett. A 376(10?C11), 1035–1041 (2012)
Hsu, J.L., Chong, S.K., Hwang, T., Tsai, C.W.: Dynamic quantum secret sharing. Quantum Inf Process 12(1), 331–344 (2013)
Liao, C.H., Yang, C.W., Hwang, T.: Dynamic quantum secret sharing protocol based on GHZ state. Quantum Inf Process 13(8), 1907–1916 (2014)
Ito, M., Saito, A., Nishizeki, T.: Secret sharing scheme realizing general access structure. Electronics and Communications in Japan (Part III: Fundamental Electronic Science) 72(9), 56–64 (1989)
Roy, S., Mukhopadhyay, S.: Device-independent quantum secret sharing in arbitrary even dimensions. Phys. Rev. A 100, 012319 (2019)
Liao, Q., Liu, H., Zhu, L., et al.: Quantum secret sharing using discretely modulated coherent states. Phys. Rev. A 103(3), 032410 (2021)
Yang, C.W., Tsai, C.W.: Efficient and secure dynamic quantum secret sharing protocol based on bell states. Quantum Inf Process 19(5), 162 (2020)
Wang, N., Zhang, X., Zhang, X., et al.: \((t, n)\) threshold quantum secret sharing using rotation operation. Int. J. Theor. Phys. 61(6), 1–19 (2022)
Wang, J., Li, L., Peng, H., Yang, Y.: Quantum-secret-sharing scheme based on local distinguishability of orthogonal multiqudit entangled states. Phys. Rev. A 95(2), 022320 (2017)
Bai, C.M., Zhang, S., Liu, L.: Quantum secret sharing for a class of special hypergraph access structures. Quantum Inf Process 21(3), 1–17 (2022)
Senthoor, K., Sarvepalli, P.K.: Theory of communication efficient quantum secret sharing. IEEE Trans. Inf. Theory. 68(5), 3164–3186 (2022)
Gallager, R.: Low-density parity-check codes. IRE Trans. Inf. Theory. 8(1), 21–28 (1962)
Ryan, W., Lin, S.: Channel codes: classical and modern. Cambridge university press, (2009)
Massey, J.L.: Minimal codewords and secret sharing //Proceedings of the 6th joint Swedish-Russian international workshop on information theory, pp. 276-279 (1993)
Long, G.L., Liu, X.S.: Theoretically efficient high-capacity quantum-key-distribution scheme. Phys. Rev. A 65, 032302 (2002)
Li, C.Y., Zhou, H.Y., Wang, Y., Deng, F.G.: Secure quantum key distribution network with Bell states and local unitary operations. Chin. Phys. Lett. 22, 1049 (2005)
Feng, Y., Deng, S., Wang, L., et al.: Minimum distances of three families of low-density parity-check codes based on finite geometries. Front. Math. China 11, 279–289 (2016)
Tavakoli, A., Herbauts, I., Zukowski, M., Bourennane, M.: Secret sharing with a single d-level quantum system. Phys. Rev. A 92, 030302(R) (2015)
Karimipour, V., Asoudeh, M., Gheorghiu, V., Looi, S.Y., Griffiths, R.B.: Quantum secret sharing and random hopping: using single states instead of entanglement. Phys. Rev. A 92, 030301(R) (2015)
Cao, H., Ma, W.: \((t, n)\) threshold quantum state sharing scheme based on linear equations and unitary operation. IEEE Photon. J. 9(1), 1–7 (2017)
Bai, C.M., Zhang, S., Liu, L.: Verifiable quantum secret sharing scheme using d-dimensional GHZ state. Int. J. Theor. Phys. 60, 3993–4005 (2021)
Qin, H., Dai, Y.: Verifiable \((t, n)\) threshold quantum secret sharing using d-dimensional Bell state. Inf. Process. Lett. 116(5), 351–355 (2016)
Acknowledgements
We want to express our gratitude to anonymous referees for their valuable and constructive comments. This work supported by the National Natural Science Foundation of China under Grant No.12301590, the Natural Science Foundation of Hebei Province under Grant No.A2022210002 and No.A2021210027 and the Department of Education of Hebei Province under Grant No.QN2020196.
Author information
Authors and Affiliations
Contributions
Chen-Ming Bai: Conceptualization, Methodology, Investigation, Supervision, Writing original draft. Yanan Feng and Sujuan Zhang: Discussing, Validation, Writing- review. Lu Liu: Discussing, Writing review.
Corresponding author
Ethics declarations
Competing of interest
The authors declare no competing interests.
Declaration of Interest Statement
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Bai, CM., Feng, Y., Zhang, S. et al. Verifiable Quantum Secret Sharing Scheme Based on LDPC Codes. Int J Theor Phys 63, 6 (2024). https://doi.org/10.1007/s10773-023-05533-3
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10773-023-05533-3