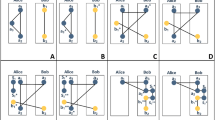
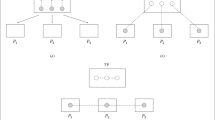
Abstract
We design a novel high-efficient quantum key agreement protocol with entanglement measure, whose security and high efficiency are guaranteed. In the proposed quantum key agreement protocol, we just utilize the Bell states and two-particle states as quantum resources, and just utilize Bell measurement and the classical binary coding to generate the final shared secret key. Which reduces the quantum sources and improves the efficiency of the proposed quantum key agreement protocol. Besides, we provide the security analyses of the proposed QKA protocol, including the robustness and the attacks of participants. Analyses demonstrate that the proposed QKA protocol with entanglement measure is robust and it can resist the most attacks. In addition, we compare our protocol with typical QKA protocols, and the results show that our protocol is high-efficient. Furthermore, the proposed novel QKA protocol with entanglement measure can be implemented with existing physical technologies.

Similar content being viewed by others
References
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.: Quantum cryptography [J]. Rev. Mod. Phys. 74(1), 145 (2002)
Dubbers, D., Stöckmann, H.J.: Quantum informatics [M]. In: Quantum Physics: The Bottom-Up Approach, pp. 159–164. Springer, Berlin, Heidelberg (2013)
Flügge, S.: Practical Quantum Mechanics [M]. Springer Science & Business Media (2012)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing [J]. In: Proceedings of IEEE International Conference on Computers, Systems, and Signal Processing Bangalore, India, pp. 175–179 (1984)
Zhou, N.R., Wang, L.J., Gong, L.H., Zuo, X.W., Liu, Y.: Quantum deterministic key distribution protocols based on teleportation and entanglement swapping [J]. Opt. Commun. 284(19), 4836–4842 (2011)
Liao, S.K., Cai, W.Q., Liu, W.Y., Zhang, L., Li, Y., Ren, J.G., Yin, J., Shen, Q., Cao, Y., Li, Z.P., Li, F.Z., Chen, X.W., Sun, L.H., Jia, J.J., Wu, J.C., Jiang, X.J., Wang, J.F., Huang, Y.M., Wang, Q., et al.: Satellite-to-ground quantum key distribution [J]. Nature. 549(7670), 43–47 (2017)
Mehic, M., Niemiec, M., Rass, S., Ma, J., Peev, M., Aguado, A., Martin, V., Schauer, S., Poppe, A., Pacher, C., Voznak, M.: Quantum key distribution: a networking perspective [J]. ACM Comput. Surv. (CSUR). 53(5), 1–41 (2020)
Basso Basset, F., Valeri, M., Roccia, E., Muredda, V., Poderini, D., Neuwirth, J., Spagnolo, N., Rota, M.B., Carvacho, G., Sciarrino, F., Trotta, R.: Quantum key distribution with entangled photons generated on demand by a quantum dot [J]. Sci. Adv. 7(12), eabe6379 (2021)
Zhou, N.R., Zeng, G.H., Xiong, J.: Quantum key agreement protocol [J]. Electron. Lett. 40(18), 1149–1150 (2004)
Chong, S.K., Hwang, T.: Quantum key agreement protocol based on BB84 [J]. Opt. Commun. 283(6), 1192–1195 (2010)
Yang, Y.G., Gao, S., Li, D., Zhou, Y.H., Shi, W.M.: Two-party quantum key agreement over a collective noisy channel [J]. Quantum Inf. Process. 18(3), 1–17 (2019)
Proietti, M., Ho, J., Grasselli, F., Barrow, P., Malik, M., Fedrizzi, A.: Experimental quantum conference key agreement [J]. Sci. Adv. 7(23), eabe0395 (2021)
Bennett, C.H., Brassard, G., Crépeau, C., Jozsa, R., Peres, A., Wootters, W.K.: Teleporting an unknown quantum state via dual classical and Einstein-Podolsky-Rosen channels [J]. Phys. Rev. Lett. 70(13), 1895 (1993)
Bouwmeester, D., Pan, J.W., Mattle, K., Eibl, M., Weinfurter, H., Zeilinger, A.: Experimental quantum teleportation [J]. Nature. 390(6660), 575–579 (1997)
Luo, Y.H., Zhong, H.S., Erhard, M., Wang, X.L., Peng, L.C., Krenn, M., Jiang, X., Li, L., Liu, N.L., Lu, C.Y., Zeilinger, A., Pan, J.W.: Quantum teleportation in high dimensions [J]. Phys. Rev. Lett. 123(7), 070505 (2019)
Hillery, M., Bužek, V., Berthiaume, A.: Quantum secret sharing [J]. Phys. Rev. A. 59(3), 1829 (1999)
Hsu, J.L., Chong, S.K., Hwang, T., Tsai, C.W.: Dynamic quantum secret sharing [J]. Quantum Inf. Process. 12(1), 331–344 (2013)
Sutradhar, K., Om, H.: Efficient quantum secret sharing without a trusted player [J]. Quantum Inf. Process. 19(2), 1–15 (2020)
Lunghi, T., Kaniewski, J., Bussieres, F., Houlmann, R., Tomamichel, M., Kent, A., Gisin, N., Wehner, S., Zbinden, H.: Experimental bit commitment based on quantum communication and special relativity [J]. Phys. Rev. Lett. 111(18), 180504 (2013)
Adlam, E., Kent, A.: Device-independent relativistic quantum bit commitment [J]. Phys. Rev. A. 92(2), 022315 (2015)
Wang, C., Deng, F.G., Li, Y.S., Liu, X.S., Long, G.L.: Quantum secure direct communication with high-dimension quantum superdense coding [J]. Phys. Rev. A. 71(4), 044305 (2005)
Zhu, F., Zhang, W., Sheng, Y., Huang, Y.: Experimental long-distance quantum secure direct communication [J]. Sci. Bull. 62(22), 1519–1524 (2017)
Zhang, W., Ding, D.S., Sheng, Y.B., Zhou, L., Shi, B.S., Guo, G.C.: Quantum secure direct communication with quantum memory [J]. Phys. Rev. Lett. 118(22), 220501 (2017)
Qi, Z., Li, Y., Huang, Y., Feng, J., Zheng, Y., Chen, X.: A 15-user quantum secure direct communication network [J]. Light Sci. Appl. 10(1), 1–8 (2021)
Curty, M., Santos, D.J.: Quantum authentication of classical messages [J]. Phys. Rev. A. 64(6), 062309 (2001)
Portmann, C.: Quantum authentication with key recycling [C]. In Annual International Conference on the Theory and Applications of Cryptographic Techniques, pp. 339–368. Springer, Cham (2017)
Sikeridis, D., Kampanakis, P., Devetsikiotis, M.: Post-quantum authentication in TLS 1.3: a performance study [J]. Cryptology ePrint Archive (2020)
Qian, Y., Gui, C., Liu, B., Huang, W., Xu, B.J.: Quantum identity authentication based on round robin differencial phase shift communication line [J]. Int. J. Theor. Phys. 61(2), 1–12 (2022)
Zeng, G., Keitel, C.H.: Arbitrated quantum-signature scheme [J]. Phys. Rev. A. 65(4), 042312 (2022)
Zou, X.F., Qiu, D.W.: Security analysis and improvements of arbitrated quantum signature schemes [J]. Phys. Rev. A. 82(4), 042325 (2010)
Zhang, L., Sun, H.W., Zhang, K.J., Jia, H.Y.: An improved arbitrated quantum signature protocol based on the key-controlled chained CNOT encryption [J]. Quantum Inf. Process. 16(3), 1–15 (2017)
Feng, Y., Shi, R., Shi, J., Zhou, J., Guo, Y.: Arbitrated quantum signature scheme with quantum walk-based teleportation [J]. Quantum Inf. Process. 18(5), 1–21 (2019)
Diffie, W., Hellman, M.E.: New directions in cryptography [J]. IEEE Trans. Inf. Theory. 22(6), 644 (1976)
Hsueh, C. C., Chen, C. Y.: Quantum key agreement protocol with maximally entangled states [C]. In: Proceedings of the 14th Information Security Conference, pp. 236–242. National Taiwan University of Science and Technology, Taipei (2004)
Shukla, C., Alam, N., Pathak, A.: Protocols of quantum key agreement solely using bell states and bell measurement [J]. Quantum Inf. Process. 13(11), 2391–2405 (2014)
Murta, G., Grasselli, F., Kampermann, H., Bruß, D.: Quantum conference key agreement: a review [J]. Adv. Quantum Technol. 3(11), 2000025 (2020)
Horodecki, K., Winczewski, M., Das, S.: Fundamental limitations on the device-independent quantum conference key agreement [J]. Phys. Rev. A. 105(2), 022604 (2022)
Gao, H., Zhou, R.G.: Multi-party quantum key agreement protocol based on G-like states and χ+ states [J]. Int. J. Theor. Phys. 61(2), 1–13 (2022)
He, W.T., Wang, J., Zhang, T.T., Alzahrani, F., Hobiny, A., Alsaedi, A., Hayat, T., Deng, F.G.: High-efficient three-party quantum key agreement protocol with quantum dense coding and bell states [J]. Int. J. Theor. Phys. 58(9), 2834–2846 (2019)
Ghosh, S., Kar, G., Roy, A., Sen, A., Sen, U.: Distinguishability of bell states [J]. Phys. Rev. Lett. 87(27), 277902 (2001)
Wang, P., Sun, Z.W., Sun, X.Q.: Multi-party quantum key agreement protocol secure against collusion attacks [J]. Quantum Inf. Process. 16(7), 170 (2017)
Zhao, X.Q., Zhou, N.R., Chen, H.Y., Gong, L.H.: Multiparty quantum key agreement protocol with entanglement swapping [J]. Int. J. Theor. Phys. 58(2), 436–450 (2019)
Iqbal, H., Krawec, W.O.: Semi-quantum cryptography [J]. Quantum Inf. Process. 19(3), 1–52 (2020)
Zou, X.F., Qiu, D.W., Li, L.Z., Wu, L.H., Li, L.J.: Semiquantum-key distribution using less than four quantum states [J]. Phys. Rev. A. 79(5), 052312 (2009)
Cabello, A.: Quantum key distribution in the Holevo limit [J]. Phys. Rev. Lett. 85(26), 5635 (2000)
Acknowledgements
This work is supported by the National Natural Science Foundation of China (Grant Nos.61976232 and 51978675).
Funding
This work was supported by the National Natural Science Foundation of China (Grant Nos.61976232 and 51978675).
Author information
Authors and Affiliations
Contributions
All authors contributed to the study conception and design. The analyses and design were performed by Xing-Qiang Zhao, Hai Wan, and Lv-Zhou Li. The first draft of the manuscript was written by Xing-Qiang Zhao and all authors commented on previous versions of the manuscript. All authors read and approved the final manuscript.
Corresponding authors
Ethics declarations
Competing Interests
The authors have no relevant financial or non-financial interests to disclose.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhao, XQ., Wan, H. & Li, LZ. High-efficient Quantum Key Agreement Protocol with Entanglement Measure. Int J Theor Phys 61, 183 (2022). https://doi.org/10.1007/s10773-022-05166-y
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10773-022-05166-y