Abstract
We propose the unidimensional continuous-variable quantum key distribution(UDCVQKD) protocol based on the basis-encoding of Gaussian modulated coherent states. the UDCVQKD protocol disregards the necessity in one of the quadrature modulations in coherent states. On that basis, we propose our scheme by encoding the secret keys on the either randomly selected measurement bases: the phase quadrature (X) or the amplitude quadrature (P), in order to slightly weaken the effects of reconciliation efficiency and channel excess noise compare to the present UCVQKD protocol. The new protocol with a view to simplify the precedent unidimensional protocols in the decoding procedure, meanwhile ensure the security of the quantum communication.




Similar content being viewed by others
References
Huang, P., Huang, J., Wang, T., Li, H., Huang, D., Zeng, G.: Robust continuous-variable quantum key distribution against practical attacks. Phys. Rev. A 95, 052302 (2017)
Madsen, L.S., Usenko, V.C., Lassen, M., Filip, R., Andersen, U.L.: Continuous Variable Quantum key Distribution with Modulated Entangled States, p 1083. Nature Communications, London (2012)
Jouguet, P., Kunz-Jacques, S., Diamanti, E.: Analysis of imperfections in practical continuous-variable quantum key distribution. Phys. Rev. A 86, 032309 (2012)
Weedbrook, C., Pirandola, S., Ralph, T.: Continuous-variable quantum key distribution using thermal states. Phys. Rev. A 86, 022318 (2012)
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. Mod. Phys. 74, 145 (2002)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers Systems and Signal Processing, pp. 176–178 (1984)
Lütkenhaus, N.: Security against individual attacks for realistic quantum key distribution. Phys. Rev. A 61, 052304 (2000)
Waks, E., Zeevi, A., Yamamoto, Y.: Security of quantum key distribution with entangled photons against individual attacks. Phys. Rev. A 65, 052310 (2002)
Antonio, A., Brunner, N., Gisin, N., Massar, S., Pironio, S., Scarani, V.: Device-Independent Security of quantum cryptography against collective attacks. Phys. Rev. Lett. 98, 230501 (2007)
Grosshans, F.: Collective attacks and unconditional security in continuous variable quantum key distribution. Phys. Rev. Lett. 94, 020504 (2005)
Mertz, M., Kampermann, H., Bratzik, S., Dagmar, B.: Secret key rates for coherent attacks. Phys. Rev. A 87, 012315 (2013)
Furrer, F., Franz, T., Berta, M., Leverrier, A., Scholz, V.B., Tomamichel, M., Werner, R.F.: Continuous variable quantum key distribution: Finite-key analysis of composable security against coherent attacks. Phys. Rev. Lett. 109, 100502 (2014)
Lütkenhaus, N.: Security against eavesdropping in quantum cryptography. Phys. Rev. A 54, 97 (1996)
Leverrier, A., Grosshans, F., Grangier, P.: Finite-size analysis of a continuous-variable quantum key distribution. Phys. Rev. A 81, 062343, 2 (2010)
Jouguet, P., Kunz-Jacques, S., Leverrier, A.: Long-distance continuous-variable quantum key distribution with a Gaussian modulation. Phys. Rev. A 84, 062317 (2011)
Pirandola, S., Braunstein, S.L., Lloyd, S.: Characterization of collective Gaussian attacks and security of coherent-state quantum cryptography. Phys. Rev. Lett. 101, 200504 (2008)
Navascues, M., Grosshans, F., Acin, A.: Optimalityof gaussian attacks in Continuous-Variable quantum cryptography. Phys. Rev. Lett. PRL 97, 190502 (2006)
Kumar, R., Qin, H., Alléaume, R.: Coexistence of continuous variable QKD with intense DWDM classical channels. New J. Phys. 17, 043027 (2015)
Grosshans, F., Assche, G.V., Wenger, J., Brouri, R., Cerf, N.J., Grangier, P.: Quantum key distribution using gaussian-modulated coherent states. Nature 421, 238 (2003)
Shen, Y., Peng, X., Yang, J., Guo, H.: Continuous-variable quantum key distribution with Gaussian source noise. Phys. Rev. A 83, 052304 (2011)
Huang, D., Huang, P., Li, H., Wang, T., Zhou, Y., Zeng, G.: Field demonstration of a continuous-variable quantum key distribution network. Opt. Lett. 41, 3511 (2016)
Martinez-Mateo, J., Elkouss, D., Martin, V.: Key reconciliation for high performance quantum key distribution. Sci. Rep. 3, 1576 (2013)
Weedbrook, C., Pirandola, S., García-Patrón, R., Cerf, N.J., Ralph, T.C., Shapiro, J.H., Lloyd, S.: Gaussian quantum information. Rev. Mod. Phys. 84(2), 621 (2012)
Usenko, V.C., Grosshans, F.: Unidimensional continuous-variable quantum key distribution. Phys Rev. A 92, 062337 (2015)
Zhang, H., Ruan, X., Wu, X.: Plug-and-play unidimensional continuous-variable quantum key distribution. Quantum Inf Process 18(5) (2019)
Usenko, V.C.: Unidimensional continuous-variable quantum key distribution using squeezed states. Phys. Rev. A 98(3), 032321 (2018)
liao, Q., Guo, Y., Xie, C., Huang, D., Huang, P., Zeng, G.: Composable security of unidimensional continuous-variable quantum key distribution. Quantum Inf. Process 17(5), 113 (2018)
Huang, P., Huang, J., Zhang, Z., Zeng, G.: Quantum key distribution using basis encoding of Gaussian-modulated coherent states. Phys. Rev. A 97, 042311 (2018)
Gessner, M., Pezze, L., Smerzi, A.: Efficient entanglement criteria for discrete, continuous, and hybrid variables. Phys. Rev. A 94(2), 020101 (2016)
Huang, D., Huang, P., Lin, D., Zeng, G.: Long-distance continuous-variable quantum key distribution by controlling excess noise. Sci. Rep. 6, 19201 (2016)
Brádler, K., Weedbrook, C.: Security proof of continuous-variable quantum key distribution using three coherent states. Phys. Rev. A97, 022310 (2018)
Navascués, M., Acín, A.: Security bounds for continuous variables quantum key distribution. Phys. Rev. Lett. 94, 020505 (2008)
Lodewyck, J., Bloch, M.: Quantum key distribution over 25 km with an all-fiber continuous-variable system. Phy. Rev. A 76, 042305 (2007)
Tobias, G., Vitus, H., Jrg, D., Fabian, F., Torsten, F., Christoph, P., Werner, R.F., Roman, S.: Implementation of continuous-variable quantum key distribution with composable and one-sided-device-independent security against coherent attacks. Nat. Commun. 6, 8795 (2015)
Nielsen, M.A., Chuang, I.L.: Quantum Computation and Quantum Information. Cambridge University Press, Cambridge (2000)
Grosshans, F., Cerf, N.J.: Continuous-Variable Quantum cryptography is secure against Non-Gaussian attacks. Phys. Rev. Lett. 92, 047905 (2004)
Scarani, V., Bechmann-Pasquinucci, H., Nicolas, J.C., Dušek, M., Lütkenhaus, N., Peev, M.: The security of practical quantum key distribution. Rev. Mod. Phys. 81 (2009)
Thearle, O., Assad, S.M., Symul, T.: Estimation of output-channel noise for continuous-variable quantum key distribution. Phys. Rev. A 93(4), 042343 (2016)
Acknowledgments
This work is supported by the National Nature Science Foundation of China (Grant No.61801522), and National Nature Science Foundation of Hunan Province, China (Grant No. 2019JJ40352).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
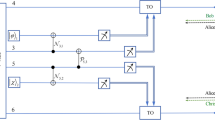
In the BEUD CVQKD protocols, Alice sends the single modulated key information through the lossy and noisy channel to Bob. We focus on the Gaussian attacks in this paper, in which we assume the parameters εx = 𝜖p = ε as the channel excess noise, we suppose that Eve would replace the quantum channel with a perfect displacement with no noise and lose, then she entangle ρb0 with her own states ∣ψE〉 and resends to Bob as camouflage, so that the entangled ρb0 would be the same as the state that passed through the noisy and lossy channel. Suppose that Bob uses homodyne detection with the electronics noise v and efficiency η, then the quadratures received by Bob can be calculated as
Where Xex(Pex), δXv(δPv), δXel(δPel) are generated from homodyne detection and denoted to the channel excess noise, shot noise and electronic noise, respectively. where\( \left \langle {X_{ex}^{2}} \right \rangle \) = \( \left \langle P_{ex}^{2} \right \rangle \) = εc,\( \left \langle {X_{v}^{2}} \right \rangle \) = \( \left \langle {P_{v}^{2}} \right \rangle \) = 1, and\( \left \langle \delta X_{el}^{2} \right \rangle \) = \( \left \langle \delta P_{el}^{2} \right \rangle \) = v in shot noise units, respectively.
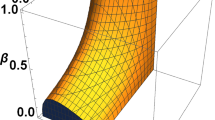
After identify the quadrature of the output mode in proposed scheme, we will calculate the QBER of Alice’s decoding according to Bob’s measurement results. Because of the symmetry of the jugement rule for either X or P quadratures, we neglect the unmodulated quadrature and just focus on the case of XA > PA for simplicity. Accroding to (18), the inequality \({{\upbeta }_{A}^{x}}X_{B}<C_{A}\) and \({{\upbeta }_{A}^{p}}P_{B}>C_{A}\) can be expanded to [28].
We set M = XA − PA, \(\text {N}_{\text {x}}=-2\delta X_{ex}-\frac {2}{\sqrt {\eta T}}(\delta X_{v}+\delta X_{el})\) and \(\text {N}_{\text {p}}=-2\delta \text {P}_{\text {ex}}-\frac {2}{\sqrt {\eta T}}(\delta P_{v}+\delta P_{el})\), the variables follow the normal distribution as
where \({\sigma _{m}^{2}}=2V_{M}\) and \({\sigma _{n}^{2}}=4\left (\frac {\varepsilon _{c}\eta T+1+v}{\eta T}\right )\), The QBER between Alice and Bob can be derived as
where \(\text {erf}(x)={{\int \limits }_{0}^{x}}e^{-t^{2}}dt\) is the error function.
Rights and permissions
About this article
Cite this article
Guo, L., Ran, Q., Zhao, W. et al. Unidimensional Continuous-variable Quantum Key Distribution Based on Basis-encoding Coherent States Protocol. Int J Theor Phys 59, 1730–1741 (2020). https://doi.org/10.1007/s10773-020-04439-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-020-04439-8