Abstract
The noiseless linear amplifier(NLA) can probabilistically amplify the amplitude of the coherent state while retaining the initial level of noise. It is widely proposed and discussed to enhance various CVQKD protocols. In the previous work, when analyzing the security of the NLA-based CVQKQ protocol, they usually included the impact of NLA in a set of equivalent parameters. In this article, we develop this equivalent method and propose a new one to analyze the protocol with NLA which simplifies the computational complexity. In particular, we have further considered the effect of NLA on entanglement parameter of the EPR state. Then by using our proposed method, we first obtain the secret key rate of the NLA-enhanced CVQKD system with imperfect detection. The results show that the NLA can also improve the transmission distance of CVQKD protocols with imperfect detection by equivalent \(20\log _{10}g\) dB of losses.






Similar content being viewed by others
References
Scarani, V., Bechmann-Pasquinucci, H., Cerf, N.J., Dušek, M., Lütkenhaus, N., Peev, M.: The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301–1350 (2009)
La Cour-Harbo, A., Jensen, A.: Wavelets and the lifting scheme. In: Encyclopedia of Complexity and Systems Science, pp. 10007–10031. Springer (2009)
Gong, L.-H., Li, J.-F., Zhou, N.-R.: Continuous variable quantum network dialogue protocol based on single-mode squeezed states. Laser Phys. Lett. 15(10), 105204 (2018)
Gong, L., Tian, C., Li, J., Zou, X.: Quantum network dialogue protocol based on continuous-variable ghz states. Quantum Inf. Process 17(12), 331 (2018)
Zhao, W., Guo, Y., Zhang, L., Huang, D.: Phase noise estimation using bayesian inference for continuous-variable quantum key distribution. Optics express 27(3), 1838–1853 (2019)
Guo, Y., Xie, C., Liao, Q., Zhao, W., Zeng, G., Huang, D.: Entanglement-distillation attack on continuous-variable quantum key distribution in a turbulent atmospheric channel. Phys. Rev. A 96(2), 022320 (2017)
Grosshans, F., Grangier, P.: Continuous variable quantum cryptography using coherent states. Phys. Rev. Lett. 88(5), 057902 (2002)
Grosshans, F., Van Assche, G., Wenger, J., Brouri, R., Cerf, N.J., Grangier, P.: Quantum key distribution using gaussian-modulated coherent states. Nature 421(6920), 238 (2003)
Renner, R., Cirac, J.I.: de finetti representation theorem for infinite-dimensional quantum systems and applications to quantum cryptography. Phys. Rev. Lett. 102(11), 110504 (2009)
García-Patrón, R., Cerf, N.J.: Unconditional optimality of gaussian attacks against continuous-variable quantum key distribution. Phys. Rev. Lett. 97, 190503 (2006)
Navascués, M., Grosshans, F., Acín, A.: Optimality of gaussian attacks in continuous-variable quantum cryptography. Phys. Rev Lett. 97, 190502 (2006)
Pirandola, S., Braunstein, S.L., Lloyd, S.: Characterization of collective gaussian attacks and security of coherent-state quantum cryptography. Phys. Rev. Lett. 101, 200504 (2008)
Leverrier, A., Grangier, P.: Simple proof that gaussian attacks are optimal among collective attacks against continuous-variable quantum key distribution with a gaussian modulation. Phys. Rev. A 81, 062314 (2010)
Leverrier, A., García-Patrón, R., Renner, R., Cerf, N.J.: Security of continuous-variable quantum key distribution against general attacks. Phys. Rev. Lett. 110, 030502 (2013)
Leverrier, A.: Security of continuous-variable quantum key distribution via a gaussian de finetti reduction. Phys. Rev. Lett. 118, 200501 (2017)
Qi, B., Zhu, W., Qian, L., Lo, H.-K.: Feasibility of quantum key distribution through a dense wavelength division multiplexing network. New J. Phys. 12(10), 103042 (2010)
Cerf, N.J., Grangier, P.: From quantum cloning to quantum key distribution with continuous variables: a review. JOSA B 24(2), 324–334 (2007)
Weedbrook, C., Pirandola, S., García-Patrón, R., Cerf, N.J., Ralph, T.C., Shapiro, J.H., Lloyd, S.: Gaussian quantum information. Rev. Mod. Phys. 84(2), 621 (2012)
Huang, D., Huang, P., Lin, D., Zeng, G.: Long-distance continuous-variable quantum key distribution by controlling excess noise. Sci. Rep. 6, 19201 (2016)
Ferreyrol, F., Barbieri, M., Blandino, R., Fossier, S., Tualle-Brouri, R., Grangier, P.: Implementation of a nondeterministic optical noiseless amplifier. Phys. Rev. Lett. 104, 123603 (2010)
Ferreyrol, F., Blandino, R., Barbieri, M., Tualle-Brouri, R., Grangier, P.: Experimental realization of a nondeterministic optical noiseless amplifier. Phys. Rev. A 83, 063801 (2011)
Xiang, G.-Y., Ralph, T.C., Lund, A.P., Walk, N., Pryde, G.J.: Heralded noiseless linear amplification and distillation of entanglement. Nat. Photonics 4(5), 316 (2010)
Xu, B., Tang, C., Chen, H., Zhang, W., Zhu, F.: Improving the maximum transmission distance of four-state continuous-variable quantum key distribution by using a noiseless linear amplifier. Phys. Rev. A 87, 062311 (2013)
Walk, N., Lund, A.P., Ralph, T.C.: Nondeterministic noiseless amplification via non-symplectic phase space transformations. New J. Phys. 15(7), 073014 (2013)
Guo, Y., Li, R., Liao, Q., Zhou, J., Huang, D.: Performance improvement of eight-state continuous-variable quantum key distribution with an optical amplifier. Phys. Lett. A 382(6), 372–381 (2018)
Skornia, C., von Zanthier, J., Agarwal, G.S., Werner, E., Walther, H.: Nonclassical interference effects in the radiation from coherently driven uncorrelated atoms. Phys. Rev. A 64(6), 063801 (2001)
Caves, C.M.: Quantum limits on noise in linear amplifiers. Phys. Rev. D 26(8), 1817 (1982)
Levenson, J.A., Abram, I., Rivera, T.H., Grangier, P.H.: Reduction of quantum noise in optical parametric amplification. JOSA B 10(11), 2233–2238 (1993)
Fossier, S., Diamanti, E., Debuisschert, T., Tualle-Brouri, R., Grangier, P.: Improvement of continuous-variable quantum key distribution systems by using optical preamplifiers. J. Phys. B Atomic Mol. Phys. 42(11), 114014 (2009)
Ralph, T.C., Lund, A.P.: Nondeterministic noiseless linear amplification of quantum systems. arXiv Quant. Phys. 1110(1), 155–160 (2009)
Chrzanowski, H.M., Walk, N., Assad, S.M., Janousek, J., Hosseini, S., Ralph, T.C., Symul, T., Lam, P.K.: Measurement-based noiseless linear amplification for quantum communication. Nat. Photonics 8(4), 333 (2014)
Li, Z., Zhang, Y., Wang, X., Xu, B., Peng, X., Guo, H.: Non-gaussian postselection and virtual photon subtraction in continuous-variable quantum key distribution. Phys. Rev. A 93(1), 012310 (2016)
Blandino, R., Leverrier, A., Barbieri, M., Etesse, J., Grangier, P., Tualle-Brouri, R.: Improving the maximum transmission distance of continuous-variable quantum key distribution using a noiseless amplifier. Phys. Rev. A 86, 012327 (2012)
Zhang, Y., Li, Z., Weedbrook, C., Marshall, K., Pirandola, S., Yu, S., Guo, H.: Noiseless linear amplifiers in entanglement-based continuous-variable quantum key distribution. Entropy 17(7), 4547–4562 (2015)
Li, C., Miao, R., Gong, X., Guo, Y., He, G.: Performance improvement of two-way quantum key distribution by using a heralded noiseless amplifier. Int. J. Theor. Phys. 55(4), 2199–2211 (2016)
Bai, D., Huang, P., Ma, H., Wang, T., Zeng, G.: Performance improvement of plug-and-play dual-phase-modulated quantum key distribution by using a noiseless amplifier. Entropy 19(10), 546 (2017)
Leverrier, A., Grangier, P.: Unconditional security proof of long-distance continuous-variable quantum key distribution with discrete modulation. Phys. Rev. Lett. 102, 180504 (2009)
Leverrier, A., Grosshans, F., Grangier, P.: Finite-size analysis of a continuous-variable quantum key distribution. Phys. Rev. A 81, 062343 (2010)
Acknowledgments
This work was supported by the National key research and development program (Grant No. 2016YFA0302600) and the National Natural Science Foundation of China (Grants No. 61332019, 61671287, 61631014).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
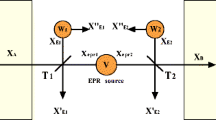
Appendix A: Acquisition of the Equivalent Entanglement Parameter
In this appendix, we discuss the acquisition of the equivalent entanglement parameter λt. As we know, if we trace out one of the two output modes of a two-mode squeezed state which has an equivalent parameter λ, we obtain a thermal state ρ. And the state ρ can be decomposed on an ensemble of coherent states using the P function,
where \(P(\alpha )=\frac {1-\lambda ^{2}}{\pi \lambda ^{2}}e^{-\frac {1-\lambda ^{2}}{\lambda ^{2}}|\alpha |^{2}}=Ae^{-\frac {1-\lambda ^{2}}{\lambda ^{2}}|\alpha |^{2}}\). The above equation can be used to EB scheme, where one output mode of a two-mode squeezed state is sent to Bob through the channel, and P(α) is the probability that the coherent state |α〉 is transmitted.
In channel, the coherent state |α〉 is attenuated and simultaneously affected by the channel excess noise, which we can then record as \(|\alpha ^{\prime }\rangle \). Here we can obtain the condition that \(|\alpha ^{\prime }|^{2}=T|\alpha |^{2}+T\epsilon \), where ϵ is the variance of the channel excess noise. And then the state \(|\alpha ^{\prime }\rangle \) is amplified and selected by the NLA. Here we only care about the selection effect since we only wants to find the equivalent parameter λt of the EPR state, and we can describe this effect using (3). Substituting \(|\alpha ^{\prime }\rangle \) into the (3), we can calculate the successfully amplified probability \(P_{sel}(\alpha )=\eta ^{N}e^{-(1-g^{2})|\alpha ^{\prime }|^{2}}\). This probability is equivalent to pre-screening our EPR state, since only the successful amplified case is reserved.
Considering the pre-screening effect of the NLA, the output mode of the EPR state that is sent to Bob can be rewritten as
For the new thermal state \(\rho ^{\prime }\), its corresponding entanglement parameter λt should satisfy the condition that
And using it we can find the equivalent entanglement parameter λt as follows,
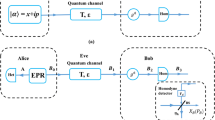
Appendix B: Acquisition of the Channel Equivalent Parameter
In this appendix, we detail the acquisition of the channel equivalent parameter Tt and ϵt. And they can be obtained from the following equation which describes the NLA’s influence on a displaced input thermal state \(\hat \rho (\lambda _{0})\) and the NLA’s output state \(\hat \rho ^{\prime }\) can be described as
where β stands for the displacement of the thermal state, the parameter \(\widetilde g = g\frac {{1-{\lambda _{0}^{2}}}}{1-g^{2}{\lambda _{0}^{2}}}\), g is the gain of the NLA, λ0 is the parameter of the input thermal state \(\hat \rho (\lambda _{0})=(1-{\lambda _{0}^{2}}){\sum }_{n=0}^{\infty }\lambda _{0}^{2n}|n\rangle \langle n|\), and the \(\hat \rho ^{\prime }\) is the state we get at the other end of the NLA. This equation means that an input thermal state \(\hat \rho (\lambda _{0})\) displaced by β = βx + iβy will be changed by the NLA to another state \(\hat \rho ^{\prime }\), \(\hat \rho ^{\prime }\) is proportional to \((1-g^{2}{\lambda _{0}^{2}}){\sum }_{n=0}^{\infty }{(g\lambda _{0})}^{2n}|n\rangle \langle n|\), and its displacement is proportional to \(\widetilde g\beta \).
The above equation describes the NLA’s amplification effect on the transmitted thermal state in channel. In the quantum channel a transmitted coherent state along with the excess noise acts as a thermal state. If a NLA is added, it amplifies the thermal state. What we want to find is an equivalent channel to generate the amplified thermal state without the NLA.
First, we consider the change of the state when we modulate nothing. In this condition VA is zero, the variance of the input thermal state ρ(λch) equals to the sum of the excess noise and shot noise, so we can find that
After NLA’s amplification, the parameter λch will be changed to gλch. And according to (24), \(\lambda _{ch}^{2}=\frac {T\epsilon }{2+T\epsilon }\), we find the first function describing the changes of the thermal state,
Then we only consider the state that is modulated by Alice and ignore the noise. Always a coherent state is generated by displacing a vacuum state. After a coherent state transmitted through the channel, the excess noise changes this displaced vacuum state to a displaced thermal state. If the displaced value we modulated is β = βx + iβy, under the effect of the NLA, it changes to \(\widetilde g\beta \) according to (23). The amplification of the states’s amplitude will change the variance of the state received by Bob. Through the NLA, the variance of the transmitted coherent state TV (λ) will be changed to \({\widetilde g}^{2}TV(\lambda )\). Without considering the noise, we can get the second equation describing the changes of the thermal state, here \(\lambda _{ch}^{2}=\frac {T\epsilon }{2+T\epsilon }\),
Last, we consider the total thermal state at Bob’s device. In the quantum channel \(\hat \rho (\lambda _{tot})=(1-\lambda _{tot}^{2}){\sum }_{n=0}^{\infty }\lambda _{tot}^{2n}|n\rangle \langle n|\), using the same method we can know the NLA will change the parameter λtot to gλtot, the third equation can be expressed as
Generally speaking, using the three Eqs. (25), (26), (27) above, we can find three corresponding equivalent parameters. But actually, using Eqs. (25), (26) we can deduce the Eq. (27). It means that just considering the effect of NLA only two equivalent parameters can be found. In the previous works, they make mistakes when finding the Eq. (27). So, wrongly effective parameters are deduced, and the solutions don’t match the fact.
In fact, just considering the successfully amplified cases, only two effective parameters can be found, and the effective parameter λt should be found from method we proposed in Appendix A. And the two parameters can be expressed as follows,
Through the equations above, the parameters Tt an ϵt can be calculated easily. The NLA’s linear amplification effect is included in the (28) when the NLA successfully runs. Together with the (22) in Apendix A, they gives us the three effective parameters. When we calculate with the secret key rate, we can just using the parameters λtTt and ϵt instead of λ, T and ϵ, even with the imperfect detection device added.
Rights and permissions
About this article
Cite this article
Li, Y., Huang, P., Li, D. et al. Security Analysis of Practical Continuous-Variable Quantum Key Distribution Using a Heralded Noiseless Amplifier. Int J Theor Phys 58, 2392–2406 (2019). https://doi.org/10.1007/s10773-019-04131-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-019-04131-6