Abstract
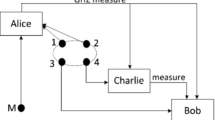
In this paper, a quantum proxy blind signature scheme based on controlled quantum teleportation is proposed. This scheme uses a genuine five-qubit entangled state as quantum channel and adopts the classical Vernam algorithm to blind message. We use the physical characteristics of quantum mechanics to implement delegation, signature and verification. Security analysis shows that our scheme is valid and satisfy the properties of a proxy blind signature, such as blindness, verifiability, unforgeability, undeniability.

Similar content being viewed by others
References
Diffie, W., Hellman, M.: New directions in cryptography. IEEE Trans. Inf. Theory. 22, 644–654 (1976)
Merkle, R.: Authentication, and public key systems. Stanford University (1979)
William, S.: Cryptography and Network Security: Principles and Practice, 5nd edn. Prentice Hall, New York (2010)
Shor, P. W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Sci. Statist comput. 26, 1484–1509 (1997)
Gottesman, D., Chuang, I.: Quantum digital signatures. arXiv:quant-ph/0105032 (2001)
Barnum, H., Crepeau, C., Gottesman, D., Smith, A., Tapp, A.: Proceedings of the 43th Annual IEEE Symposium on Foundations of Computer Science, pp 449–458 (2002)
Zeng, G. H., Keitel, C. H.: Arbitrated quantum-signature scheme. Phys. Rev. A 65, 042312 (2002)
Zeng, G. H.: Reply to “ comment on ‘ Arbitrated quantum-signature scheme’ ”. Phys. Rev. A 78, 016301 (2008)
Lee, H., Hong, C., Kim, H., et al.: Arbitrated quantum signature scheme with message recovey. Phys. Lett. A 321(5-6), 295–300 (2004)
Wen, X. J., Liu, Y., Zhang, P. Y.: Digital multi-signature protocol based on teleportation. Wuhan Univ. J. Nat. Sci. 12(1), 29–32 (2007)
Wen, X. J., Liu, Y., Zhou, N. R.: Secure quantum telephon. Opt. Commun. 275(1), 278–282 (2007)
Li, Q., Chan, W. H., Long, D. Y.: Arbitrated quantum signature scheme using Bell states. Phys. Rev. A 79(5), 054307 (2009)
Zhang, K. J., Zhang, W. W., Li, D.: Improving the security of arbitrated quantum signature gainst the forgery attack. Quantum Inf. Process. 12(8), 2655–2699 (2013)
Chaum, D.: Blind Signature for Untraceable Payments Proceeding of CRTPTO’82, pp 199–203. Plenum Publishing (1982)
Wen, X. J., Niu, X., Ji, L.: A weak blind signature scheme based on quantum cryptography. Opt. Commun. 282(4), 666–669 (2008)
Su, Q., Huang, Z., Wen, Q. Y., et al.: Quantum blind signature based on two-state vector forMalism. Opt. Commun. 283, 4408–4410 (2010)
Yin, X. R., Ma, W. P., Liu, W. Y.: A blind quantum signature scheme with χ-type entangled states. Int. J. Theoy. Phys. 51, 455–461 (2012)
Mambo, M., Usuda, K., Okamoto, E.: Proxy Signatures for Delegating Signing Operation Proceedings of the 3rd ACM Conference on Computer and Communications Security, pp 48–57, New Delhi (1966)
Cao, H. J., Huang, J., et al.: A quantum proxy signature scheme based on genuine five-qubit entangled state. Int. J. Theor. Phys 53, 3095–3100 (2014)
Xu, G. B.: Novel quantum proxy signature without entanglement. Int. J. Theor. Phys. 54, 2605–2612 (2015)
Tian, J. H., Zhang, J. Z., Li, Y. P.: Quantum Multi-proxy Blind Signature Scheme Based on Genuine Four-Qubit Entangled State. Int. J. Theor. Phys. 55, 809–816 (2016)
Vernam, G.: Cipher printing telegraph systems for secret wire and radio telegraphic communication (1955)
Shor, P. W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441–444 (2000)
Mayers, D.: Unconditional security in quantum cryptography. J. Assoc.: Comput. Math. 48(1), 351–406 (2001)
Lo, H. K.: A simple proof of the unconditional security in quantum key distribution. J. Phys. A.: Math. Gen. 34, 6957 (2001)
Inamon, H., Lutkenhaus, N., Mayers, D.: Unconditional security of practical quantum key distribution. Eur. Phys. J. D 41(3), 599–627 (2007)
Deng, F. G., Long, G. L., Liu, X. S.: Two-step quantum direct communication using the Einstein-podolsky-Rosen pair block. Phys. Rev. A 68, 042317 (2003)
Deng, F. G., Long, G. L.: Secure direct communication with a quantum one-time pad. Phys. Rev. A 69, 052319 (2004)
Cai, Q. Y., Li, B. W.: Deterministic secure communication without using entanglement, vol. 21 (2004)
Guo, W., Zhang, J. Z., Li, Y. P., An, W.: Multi-proxy Strong Blind Quantum Signature Scheme. Int. J. Theor. Phys. 55(8), 3524–3536 (2016)
Wang, T. Y., Cai, X. Q., Zhang, R. L.: Security of a sessional blind signature based on quantum cryptograph. Quantum Inf. Process. 13(8), 1677–1685 (2014)
Cai, X. Q., Zheng, Y. H., Zhang, R. L.: Cryptanalysis of a batch proxy quantum blind signature scheme. Int. J. Theor. Phys. 53(9), 3109–3115 (2014)
Wang, T. Y., Cai, X. Q., Ren, Y. L., Zhang, R. L.: Security of quantum digital sinatures for classical messages. Sci. Rep. 5, 9231 (2015)
Wang, T. Y., Wen, Q. Y., Zhu, F. C.: Cryptanalysis of multipart quantum secret sharing with Bell states and Bell measurements. Opt. Commun. 284(6), 1711–1713 (2011)
Acknowledgments
This work is supported by the National Natural Science Foundation of China (Grant No.61402275, 61402015, 61273311), the Natural Science Foundation of Shaanxi Province (Grant No.2015JM6263, 2016JM6069), and the Fundamental Research Funds for the Central Universities(Grant No.GK201402004).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zeng, C., Zhang, JZ. & Xie, SC. A Quantum Proxy Blind Signature Scheme Based on Genuine Five-Qubit Entangled State. Int J Theor Phys 56, 1762–1770 (2017). https://doi.org/10.1007/s10773-017-3322-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-017-3322-x