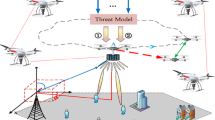
Abstract
Today, the use of Unmanned aerial vehicles (UAVs) technology has made significant progress due to its widespread use. UAVs are widely used in agriculture, commercial, military, civilian, and environmental applications. Therefore, for better efficiency, the UAV must be able to communicate effectively through the communication of the UAV system with the UAV and other communication of the UAV with the network infrastructure through the communication of the UAV with the infrastructure. In particular, security issues are a serious concern in such networks because the top-secret information exchanged between UAVs is prone to various attacks such as Sybil, blackhole and Flooding attacks. This paper proposes a method called SID-UAV that is resistant to malicious UAVs that threaten UAV to UAV communications. The SID-UAV method uses a self-matching system that detects the safest path between UAVs. This method includes various phases, including the decision-making phase, the path discovery and investigation phase, the destructive UAV response phase, and the information database registration phase. Also, in the SID-UAV method, three types of modules of route investigation, decision module and defense module are considered. Each of these modules is distributed in different parts of UAV networks and has sub-modules. These sub-modules have their own tasks and to perform and process information quickly, it is connected to the knowledge base to quickly record information and use the stored information. The performance of the SID-UAV method in NS-3 has been evaluated and tested. The evaluation results show the superiority of SID-UAV method over BRUIDS, SFA and SUAS-HIS methods in Packet Delivery Ratio (PDR), Packet Lost Ratio (PLR), Average False Positive (AFP), Average False Negative (AFN) and Average Detection Ratio (ADR).
Similar content being viewed by others
Data Availability
The data that support the findings of this study are available from the corresponding author upon reasonable request.
Code availability
All code for data analysis associated with the current submission is available from the corresponding author upon reasonable request.
References
Abdalla, A.S., Powell, K., Marojevic, V., Geraci, G.: UAV-assisted attack prevention, detection, and recovery of 5G networks. IEEE Wirel. Commun. 27(4), 40–47 (2020)
Chamola, V., Kotesh, P., Agarwal, A., Gupta, N., & Guizani, M.: A comprehensive review of unmanned aerial vehicle attacks and neutralization techniques. Ad Hoc Networks, 111, 102324 (2021)
Kumari, A., Gupta, R., Tanwar, S., Kumar, N.: A taxonomy of blockchain-enabled softwarization for secure UAV network. Comput. Commun. 161, 304–323 (2020)
Faraji-Biregani, M., Fotohi, R.: Secure communication between UAVs using a method based on smart agents in unmanned aerial vehicles. J. Supercomput. 77(5), 5076–5103 (2021)
Singh, M.M., Dutta, N., Singh, T.R., Nandi, U.: A Technique to Detect Wormhole Attack in Wireless Sensor Network Using Artificial Neural Network. In Evolutionary Computing and Mobile Sustainable Networks, pp. 297–307. Springer, Singapore (2020)
Fu, H., Liu, Y., Dong, Z., Wu, Y.: A Data Clustering Algorithm for Detecting Selective Forwarding Attack in Cluster-Based Wireless Sensor Networks. Sensors 20(1), 23 (2020)
Tourani, R., Torres, G., & Misra, S. (2020, September). PERSIA: A PuzzlE-based InteReSt FloodIng Attack Countermeasure. In Proceedings of the 7th ACM Conference on Information-Centric Networking (pp. 117–128)
Schluter, J., Peled, J. U., Taylor, B. P., Markey, K. A., Smith, M., Taur, Y., ..., Xavier, J. B.: The gut microbiota is associated with immune cell dynamics in humans. Nature. 588(7837), 303–307 (2020)
Wang, G., Lee, B., Ahn, J., Cho, G.: A UAV-assisted CH election framework for secure data collection in wireless sensor networks. Futur. Gener. Comput. Syst. 102, 152–162 (2020)
Wang, Q., Dai, H.N., Li, X., Shukla, M.K., Imran, M.: Artificial noise aided scheme to secure UAV-assisted Internet of Things with wireless power transfer. Comput. Commun. 164, 1–12 (2020)
Ch, R., Srivastava, G., Gadekallu, T.R., Maddikunta, P.K.R., Bhattacharya, S.: Security and privacy of UAV data using blockchain technology. Journal of Information Security and Applications 55, 102670 (2020)
Xu, W., Zhang, H., Cao, X., Deng, R., Li, H., Zhang, J.: Securing wireless relaying communication for dual unmanned aerial vehicles with unknown eavesdropper. Inf. Sci. 546, 871–882 (2021)
Alladi, T., Chamola, V., Kumar, N.: PARTH: A two-stage lightweight mutual authentication protocol for UAV surveillance networks. Comput. Commun. 160, 81–90 (2020)
Sedjelmaci, H., Boudguiga, A., Jemaa, I.B., Senouci, S.M.: An efficient cyber defense framework for UAV-Edge computing network. Ad Hoc Netw. 94, 101970 (2019)
Hong, W., Jianhua, L., Chengzhe, L., Zhe, W.: A provably secure aggregate authentication scheme for unmanned aerial vehicle cluster networks. Peer-to-Peer Networking and Applications 13(1), 53–63 (2020)
Condomines, J.P., Zhang, R., Larrieu, N.: Network intrusion detection system for UAV ad-hoc communication: From methodology design to real test validation. Ad Hoc Netw. 90, 101759 (2019)
Mitchell, R., Chen, R.: Adaptive intrusion detection of malicious unmanned air vehicles using behavior rule specifications. IEEE Transactions on Systems, Man, and Cybernetics: Systems 44(5), 593–604 (2013)
Sedjelmaci, H., Senouci, S.M.: Cyber security methods for aerial vehicle networks: taxonomy, challenges and solution. J. Supercomput. 74(10), 4928–4944 (2018)
Fotohi, R.: Securing of Unmanned Aerial Systems (UAS) against security threats using human immune system. Reliab. Eng. Syst. Saf. 193, 106675 (2020)
Balamurugan, N.M., Mohan, S., Adimoolam, M., John, A., Wang, W.: DOA tracking for seamless connectivity in beamformed IoT-based drones. Computer Standards & Interfaces 79, 103564 (2022)
Srivastava, G., Deepa, N., Prabadevi, B., & Reddy M, P. K. (2021, January). An ensemble model for intrusion detection in the internet of softwarized things. In Adjunct proceedings of the 2021 international conference on distributed computing and networking (pp. 25–30)
Wang, J., Jin, C., Tang, Q., Xiong, N., & Srivastava, G.: Intelligent ubiquitous network accessibility for wireless-powered mec in uav-assisted b5g. IEEE Transactions on Network Science and Engineering (2020)
Kumar, R., Kumar, P., Tripathi, R., Gupta, G.P., Gadekallu, T.R., Srivastava, G.: Sp2f: A secured privacy-preserving framework for smart agricultural unmanned aerial vehicles. Comput. Netw. 187, 107819 (2021)
Zhang, H., He, X., Dai, H.: Secure UAV communication networks via friendly jamming and bandwidth allocation. In IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS) (pp. 894–899). IEEE (2020)
Kuo, Y.T., Wei, H.Y.: Reliable two-hop device-to-device communications for UAVs. In 2019 IEEE VTS Asia Pacific Wireless Communications Symposium (APWCS) (pp. 1–5). IEEE (2019)
Vanitha, N., Ganapathi, P.: Traffic analysis of UAV networks using enhanced deep feed forward neural networks (EDFFNN). In Handbook of Research on Machine and Deep Learning Applications for Cyber Security (pp. 219–244). IGI Global (2020)
Zaminkar, M., Sarkohaki, F., Fotohi, R.: A method based on encryption and node rating for securing the RPL protocol communications in the IoT ecosystem. Int. J. Commun Syst 34(3), e4693 (2021)
Zhou, Y., Pan, C., Yeoh, P.L., Wang, K., Elkashlan, M., Vucetic, B., Li, Y.: Secure communications for UAV-enabled mobile edge computing systems. IEEE Trans. Commun. 68(1), 376–388 (2019)
Fotohi, R., Nazemi, E., Aliee, F.S.: An agent-based self-protective method to secure communication between UAVs in unmanned aerial vehicle networks. Vehicular Communications. 26, 100267 (2020)
Zaminkar, M., Fotohi, R.: SoS-RPL: securing internet of things against sinkhole attack using RPL protocol-based node rating and ranking mechanism. Wirel. Pers. Commun. 114(2), 1287–1312 (2020)
Li, Y., Zhang, R., Zhang, J., Yang, L.: Cooperative jamming via spectrum sharing for secure UAV communications. IEEE Wireless Communications Letters 9(3), 326–330 (2019)
Jamali, S., Fotohi, R.: DAWA: Defending against wormhole attack in MANETs by using fuzzy logic and artificial immune system. J. Supercomput. 73(12), 5173–5196 (2017)
Li, Y., Zhang, R., Zhang, J., Gao, S., Yang, L.: Cooperative jamming for secure UAV communications with partial eavesdropper information. IEEE Access 7, 94593–94603 (2019)
Li, B., Fei, Z., Zhang, Y., Guizani, M.: Secure UAV communication networks over 5G. IEEE Wirel. Commun. 26(5), 114–120 (2019)
Funding
This study has received no funding from any organizations.
Author information
Authors and Affiliations
Contributions
Reza Fotohi: Formal analysis, Conceptualization, Methodology, Data curation, Investigation, Validation, Writing—original draft.
Masoud Abdan: Data curation, Methodology, Writing—review & editing, Supervision.
Sanaz Ghasemi: Formal analysis, Data curation, Methodology, Conceptualization, Writing—review & editing, Supervision.
Corresponding author
Ethics declarations
Conflicts of interest
All of the authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Fotohi, R., Abdan, M. & Ghasemi, S. A Self-Adaptive Intrusion Detection System for Securing UAV-to-UAV Communications Based on the Human Immune System in UAV Networks. J Grid Computing 20, 22 (2022). https://doi.org/10.1007/s10723-022-09614-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10723-022-09614-1