Abstract
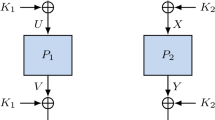
We consider the so-called Encrypted Davies–Meyer (EDM) construction, which turns a permutation P on \(\{0,1\}^n\) into a function from \(\{0,1\}^n\) to \(\{0,1\}^n\) defined as \(P(P(x)\oplus x)\). A similar construction using two independent permutations, namely \(P'(P(x)\oplus x)\), was previously analyzed by Cogliati and Seurin (Advances in cryptology—CRYPTO 2016 (Proceedings, Part I). LNCS, vol 9814, pp. 121–149, 2016) who showed that when P and \(P'\) are secret and random, then any black-box adversary needs at least roughly \(2^{2n/3}\) queries to distinguish the construction from a uniformly random function from \(\{0,1\}^n\) to \(\{0,1\}^n\). In this paper, we focus on the single-permutation variant of the construction. Our main result is that the PRF-security of the single-permutation EDM construction is also (at least) roughly \(2^{2n/3}\), in the sense that any black-box adversary needs at least this number of queries to distinguish the construction from a uniformly random function. This yields the first PRP-to-PRF conversion method which uses a single permutation, does not shrink the original domain nor range of the permutation, and provides security beyond the birthday bound.
Similar content being viewed by others
Notes
Actually the security bound for the single-key version is slightly worse than for the two-key version since it has a term \(O(nq/2^{2n/3})\).
Recall that for an attainable transcript, one has \(\Pr [T_\mathrm{id}=\tau ]>0\).
References
Bellare M., Desai A., Jokipii E., Rogaway P.: A concrete security treatment of symmetric encryption. In: Symposium on Foundations of Computer Science - FOCS ’97, pp. 394–403. IEEE Computer Society (1997).
Bellare M., Impagliazzo R.: A tool for obtaining tighter security analyses of pseudorandom function based constructions, with applications to PRP to PRF conversion. IACR Cryptology ePrint Archive, Report 1999/024 (1999). http://eprint.iacr.org/1999/024.
Bellare M., Rogaway P.: The security of triple encryption and a framework for code-based game-playing proofs. In: Vaudenay S. (ed.) Advances in Cryptology–EUROCRYPT 2006, vol. 4004, pp. 409–426. LNCSSpringer, New York (2006).
Bellare M., Krovetz T., Rogaway P.: Luby-Rackoff backwards: increasing security by making block Ciphers non-invertible. In: Nyberg K. (ed.) Advances in Cryptology–EUROCRYPT ’98, vol. 1403, pp. 266–280. LNCSSpringer, New York (1998).
Bernstein D.J.: Stronger security bounds for Wegman-Carter-Shoup authenticators. In: Cramer R. (ed) Advances in Cryptology—EUROCRYPT 2005. LNCS vol. 3494, pp. 164–180. Springer, New York (2005).
Bhattacharya S., Nandi M.: A note on the chi-square method: a tool for proving cryptographic security. Cryptogr. Commun. (2018). https://doi.org/10.1007/s12095-017-0276-z.
Chen S., Steinberger J.: Tight security bounds for key-alternating ciphers. In: Nguyen P.Q., Oswald E. (eds.) Advances in Cryptology–EUROCRYPT 2014, vol. 8441, pp. 327–350. LNCSSpringer, New York (2014).
Chen S., Lampe R., Lee J., Seurin Y., Steinberger J.P.: Minimizing the two-round even-Mansour Cipher. In: Garay J.A., Gennaro R. (eds.) Advances in Cryptology–CRYPTO 2014 (Proceedings, Part I), vol. 8616, pp. 39–56. LNCSSpringer, New York (2014).
Cogliati B., Seurin Y.: EWCDM: an efficient, beyond-birthday secure, nonce-misuse resistant MAC. In: Robshaw M., Katz J. (eds.) Advances in Cryptology–CRYPTO 2016 (Proceedings, Part I), vol. 9814, pp. 121–149. LNCSSpringer, New York (2016).
Cogliati B., Lampe R., Patarin J.: The indistinguishability of the XOR of \(k\) permutations. In: Cid C., Rechberger C. (eds.) Fast Software Encryption–FSE 2014, vol. 8540, pp. 285–302. LNCSSpringer, New York (2014).
Dai W., Hoang V.T., Tessaro S.: Information-theoretic Indistinguishability via the Chi-squared method. In: Katz J., Shacham H. (eds.) Advances in Cryptology–CRYPTO 2017 (Proceedings, Part III), vol. 10403, pp. 497–523. LNCSSpringer, New York (2017).
Hall C., Wagner D., Kelsey J., Schneier B.: Building PRFs from PRPs. In: Krawczyk H. (ed.) Advances in Cryptology–CRYPTO ’98, vol. 1462, pp. 370–389. LNCSSpringer, New York (1998).
László B.: The Fourier transform and equations over finite Abelian Groups: an introduction to the method of trigonometric sums. Lecture Notes (December 1989). http://people.cs.uchicago.edu/~laci/reu02/fourier.pdf.
Lucks S.: The sum of PRPs is a secure PRF. In: Preneel B. (ed.) Advances in Cryptology–EUROCRYPT 2000, vol. 1807, pp. 470–484. LNCSSpringer, New York (2000).
Mandal A., Patarin J., Nachef V.: Indifferentiability beyond the birthday bound for the Xor of two public random permutations. In: Gong G., Gupta K.C. (eds.) Progress in Cryptology–INDOCRYPT 2010, vol. 6498, pp. 69–81. LNCSSpringer, New York (2010).
Mennink B., Neves S.: Encrypted Davies-Meyer and its dual: towards optimal security using mirror theory. In: Katz J., Shacham H. (eds.) Advances in Cryptology–CRYPTO 2017 (Proceedings, Part III), vol. 10403, pp. 556–583. LNCSSpringer, New York (2017).
Mennink B., Preneel B.: On the XOR of multiple random permutations. In: Malkin T., Kolesnikov V., Lewko A.B., Polychronakis M. (eds.) Applied cryptography and network security–ACNS 2015, vol. 9092, pp. 619–634. LNCSSpringer, New York (2015).
Michael L., Charles R.: How to construct pseudorandom permutations from pseudorandom functions. SIAM J. Comput. 17(2), 373–386 (1988).
Michael M., Eli U.: Probability and Computing-Randomized Algorithms and Probabilistic Analysis. Cambridge University Press, Cambridge (2005).
Minaud B., Seurin Y.: The iterated random permutation problem with applications to cascade encryption. In: Gennaro R., Robshaw M. (eds.) Advances in Cryptology–CRYPTO 2015 (Proceedings, Part I), vol. 9215, pp. 351–367. LNCSSpringer, New York (2015).
Oded G., Shafi G., Silvio M.: How to construct random functions. J. ACM 33(4), 792–807 (1986).
Patarin J.: Introduction to mirror theory: analysis of systems of linear equalities and linear non equalities for cryptography. IACR Cryptology ePrint Archive, Report 2010/287 (2010). http://eprint.iacr.org/2010/287.
Patarin J.: Security in \(O(2^n)\) for the Xor of two random permutations: proof with the standard \(H\) technique. IACR Cryptology ePrint Archive, Report 2013/368 (2013). http://eprint.iacr.org/2013/368.
Patarin J.: Pseudorandom permutations based on the DES scheme. In: Cohen G.D., Charpin P. (eds.) EUROCODE ’90, vol. 514, pp. 193–204. LNCSSpringer, New York (1990).
Patarin J.: A proof of security in \(O(2^n)\) for the Xor of two random permutations. In: Safavi-Naini R. (ed.) Information Theoretic Security–ICITS 2008, vol. 5155, pp. 232–248. LNCSSpringer, New York (2008).
Patarin J.: The ”Coefficients H” technique. In: Avanzi R.M., Keliher L., Sica F. (eds.) Selected Areas in Cryptography–SAC 2008, vol. 5381, pp. 328–345. LNCSSpringer, New York (2008).
Shoni G., Shay G., Ben M.: How many queries are needed to distinguish a truncated random permutation from a random function? J. Cryptology 31(1), 162–171 (2018).
Shoup V.: On fast and provably secure message authentication based on universal hashing. In: Koblitz N. (ed.) Advances in Cryptology–CRYPTO ’96, vol. 1109, pp. 313–328. LNCSSpringer, New York (1996).
Steinberger J.: Counting solutions to additive equations in random sets. ArXiv Report 1309.5582 (2013). http://arxiv.org/abs/1309.5582.
Wegman M.N., Larry C.: New hash functions and their use in authentication and set equality. J. Comput. Syst. Sci. 22(3), 265–279 (1981).
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by T. Iwata.
Appendix: Basics of discrete Fourier analysis
Appendix: Basics of discrete Fourier analysis
We recall some classical results on Fourier analysis over the abelian group \(\mathbb {Z}_2^n\), taken from [8]. In the following, given a subset \(S\subset \{0,1\}^n\), we denote \(\mathbb {1}_S:\{0,1\}^n\rightarrow \{0,1\}\) the characteristic functions of S, namely \(\mathbb {1}_S(x)=1\) if \(x\in S\) and \(\mathbb {1}_S(x)=0\) if \(x\notin S\). Given two functions \(f,g:\{0,1\}^n\rightarrow \mathbb {R}\), we denote
the inner product of f and g, and, for all \(x\in \{0,1\}^n\), we denote
the convolution of f and g. Given \(\alpha \in \{0,1\}^n\), we denote \(\chi _{\alpha }:\{0,1\}^n \rightarrow \{\pm 1\}\) the character associated with \(\alpha \) defined as
The all-one character \(\chi _0\) is called the principal character. All other characters \(\chi \ne 1\) corresponding to \(\alpha \ne 0\) are called non-principal characters. The set of all characters forms a group for the pointwise product operation \((\chi _{\alpha }\chi _{\beta })(x)=\chi _{\alpha }(x)\chi _{\beta }(x)\) and one has \(\chi _{\alpha }\chi _{\beta }=\chi _{\alpha \oplus \beta }\).
Given a function \(f:\{0,1\}^n\rightarrow \mathbb {R}\) and \(\alpha \in \{0,1\}^n\), the Fourier coefficient of f corresponding to \(\alpha \) is
The coefficient corresponding to \(\alpha =0\) is called the principal Fourier coefficient, all the other ones are called non-principal Fourier coefficients. Note that for a set \(S\subseteq \{0,1\}^n\) one has
namely the principal Fourier coefficient of \(\mathbb {1}_S\) is equal to the relative size of the set. We will also use the following three classical results, holding for any functions \(f,g,:\{0,1\}^n\rightarrow \mathbb {R}\), any \(\alpha \in \{0,1\}^n\), and any \(S\subseteq \{0,1\}^n\):
Rights and permissions
About this article
Cite this article
Cogliati, B., Seurin, Y. Analysis of the single-permutation encrypted Davies–Meyer construction. Des. Codes Cryptogr. 86, 2703–2723 (2018). https://doi.org/10.1007/s10623-018-0470-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10623-018-0470-9