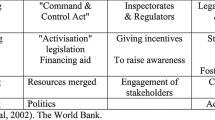
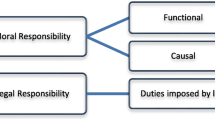
Abstract
This article makes a threefold contribution to the literature on security pluralization in the European Union (EU). Firstly, it maps the existing EU level security strategies, their accompanying action plans and implementation reports in order to identify and critically asses the prevailing conceptual frameworks – public-private partnerships and resilience – evoked by EU policy-makers when it comes to the contributions of the private sector in the provision of security. Secondly, it explores a hitherto overlooked conceptual framework for analyzing the contributions of private businesses in the provision of security in the EU (and beyond): political corporate social responsibility. Thirdly, it surveys the key challenges of the growing role of private businesses in the provision of security (responsibilization, depoliticization, and commodification) which are important reminders that no matter what conceptual framework one prefers, the engagement of private businesses in the provision of security is always bound to raise a number of profound dilemmas. This in turn implies the need for (re-)consideration of the more traditional regulatory frameworks in order to safeguard important public goods and/or values.
Similar content being viewed by others
Notes
They considered only contributions by companies that are 1.) political (in the sense that they involve activities that “work towards the creation and implementation of collectively binding rules and norms related to the provision of collective goods”); 2.) intentional (e.g. not mere by-products of other business activities); 3.) voluntary; and that 4.) “directly and/or indirectly address the level of violence in an environment characterized by imminent, on-going or only very recently terminated interactions of physical violence.” ([87], pp. 11–13)
References
European Council (2010). Internal security strategy for the European Union. http://www.consilium.europa.eu/uedocs/cms_data/librairie/PDF/QC3010313ENC.pdf. Accessed 14 April 2014.
Beck, U. (1992). Risk society: towards a new modernity. London: Sage.
Garland, D. (2001). The culture of control. Oxford: Oxford University Press.
Abrahamsen, R., & Williams, M. C. (2011). Security beyond the state: private security in international politics. Cambridge: Cambridge University Press.
Shearing, C., & Wood, J. (2003). Nodal governance, democracy, and the new “denizens”. Journal of Law and Society, 30(3), 400–419.
Wood, J., & Dupont, B. (2006). Democracy, society and the governance of security. Cambridge: Cambridge University Press.
Krahmann, E. (2004). Security governance and networks: new theoretical perspectives in transatlantic security. Cambridge Review of International Affairs, 18(1), 15–29.
Webber, M., Croft, S., Howorth, J., Terriff, T., & Krahmann, E. (2004). The governance of European security. Review of International Studies, 30(1), 3–26.
Boerzel, T. A., & Risse, T. (2006). Public-private partnerships: effective and legitimate tools of transnational governance. In E. Grande & L. W. Pauly (Eds.), Complex sovereignty (pp. 195–216). Toronto: Toronto University Press.
Gill, P. (2006). Not just joining the dots but crossing the borders and bridging the voids: constructing security networks after 11 September 2001. Policing & Society, 16(1), 27–49.
Den Boer, M., Hillerbrand, C., & Nölke, A. (2008). Legitimacy under pressure: the European web of counter-terrorism networks. Journal of Common Market Studies, 46(1), 101–124.
Ballentine, K., & Sherman, J. (2003). The political economy of armed conflict: beyond greed and grievance. Boulder, CO: Lynne Rienner Publishers.
Berdal, M., & Malone, D. M. (2000). Greed and grievance: economic agendas in civil wars. Boulder, CO: Lynne Rienner.
Klare, M. T. (2001). Resource wars: the new landscape of global conflict. New York: Owl Books.
Musah, A.-F. (2002). Privatization of security, arms proliferation and the process of state collapse in Africa. Development and Change, 33(5), 911–933.
Avant, D. (2004). The market for force: the consequences of privatizing security. Cambridge: Cambridge University Press.
Chesterman, S., & Lehnardt, C. (2007). From mercenaries to market: the rise and regulation of private military companies. Oxford: Oxford University Press.
Jäger, T., & Kümmel, G. (2007). Private military and security companies: chances, problems, pitfalls and prospects. VS Verlag für Sozialwissenschaften.
Ortiz, C. (2010). Private armed forces and global security: a guide to the issues. Santa Barbara, Denver, Oxford: Praeger.
Percy, S. (2007). Morality and regulation. In S. Chesterman & C. Lehnard (Eds.), From mercenaries to market: the rise and regulation of private military companies (pp. 11–28). Oxford: Oxford University Press.
Singer, P. W. (2003). Corporate warriors: the rise of the privatized military industry. Ithaca and London: Cornell University Press.
Loader, I., & Walker, N. (2007). Civilizing security: policing and political community in a global era. Cambridge: Cambridge University Press.
Verhage, A. (2008). Between the hammer and the anvil? The anti-money laundering-complex and its interactions with the compliance industry. Crime, Law and Social Change, 52, 9–32.
Verkuil, P. R. (2007). Outsourcing sovereignty. Cambridge: Cambridge University Press.
Krahmann, E. (2008). Security: collective good or commodity? European Journal of International Relations, 14(3), 379–404.
Eriksen, E. O. (2011). Governance between expertise and democracy: the case of European security. Journal of European Public Policy, 18(8), 1169–1189.
Bigo, D., Bonelli, L., Guittet, E., Olsson, C., & Tsoukala, A. (2006). Illiberal practices of liberal regimes: the (in)security games. Paris: L’Harmattan.
European Council (2008). Revised strategy on terrorist financing. http://register.consilium.europa.eu/doc/srv?l=EN&f=ST%2011778%202008%20REV%201. 11778/1/08. Accessed 14 April 2014.
European Council (2011). EU action plan on combating terrorism. http://register.consilium.europa.eu/doc/srv?l=EN&f=ST%2015893%202010%20REV%201. 15893/1/10. Accessed 14 April 2014.
European Commission (2014). For an open and secure global maritime domain: elements for a European Union maritime security strategy. http://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=CELEX:52014JC0009&from=EN. JOIN(2014) 9 final. Accessed 14 April 2014.
European Council (2007). Specific programme: Preventing and combating crime (2007–2013). http://eurlex.europa.eu/LexUriServ/LexUriServ.do?uri=CELEX:32007D0125:EN:NOT. Accessed 14 April 2014.
Council of the European Union (2009). The Stockholm programme - An open and secure Europe serving and protecting the citizens. http://www.se2009.eu/polopoly_fs/1.26419!menu/standard/file/Klar_Stockholmsprogram.pdf. Accessed 1 February 2010.
European Council (2004). EU drugs strategy (2005–2012). .http://europa.eu/legislation_summaries/justice_freedom_security/combating_drugs/c22569_en.htm. Accessed 14 April 2014
European Commission (2012). Security industrial policy. http://eur-lex.europa.eu/LexUriServ/LexUriServ.do?uri=COM:2012:0417:FIN:EN:PDF. COM(2012) 417 final. Accessed 14 April 2014.
European Commission (2013a). Cybersecurity strategy of the European Union. http://ec.europa.eu/dgs/home-affairs/e-library/documents/policies/organized-crime-and-human-trafficking/cybercrime/docs/join_2013_1_en.pdf. JOIN(2013) 1 final. Accessed 14 April 2014.
European Council (2003a). European security strategy. http://www.consilium.europa.eu/uedocs/cmsUpload/78367.pdf. Accessed 14 April 2014.
European Commission (2008). Report on the implementation of the European Security Strategy. http://www.consilium.europa.eu/ueDocs/cms_Data/docs/pressdata/EN/reports/104630.pdf. S407/08. Accessed 14 April 2014.
European Council (2003b). Strategy against the proliferation of weapons of mass destruction. http://register.consilium.europa.eu/pdf/en/03/st15/st15708.en03.pdf. 15708/03. Accessed 14 April 2014.
European Council (2005). Strategy for the external dimension of JHA: global freedom, security and justice. http://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=CELEX:52005DC0491&from=EN. COM/2005/0491 final. Accessed 14 April 2014.
Council of the European Union (2005). European counter-terrorism strategy. http://register.consilium.europa.eu/pdf/en/05/st14/st14469-re04.en05.pdf (European Union). Accessed 27 January 2007.
Parsons, W. (1995). Public policy: an introduction to the theory and practice of policy analysis. Northampton, MA: Edward Elgar.
Bossong, R. (2008). The action plan on combating terrorism: a flawed instrument of EU security governance. Journal of Common Market Studies, 46(1), 27–48.
European Commission (2005). The Hague Programme: Ten priorities for the next five years. http://europa.eu/rapid/pressReleasesAction.do?reference=MEMO/05/153&format=HTML&aged=0&language=EN&guiLanguage=en (European Union). Accessed 1 August 2006.
Bossong, R., & Wagner, B. (2016). A typology of cybersecurity and public-private partnerships in the context of the EU. Crime, Law and Social Change. doi:10.1007/s10611-016-9653-3.
Carrapico, H., & Farrand, B. (2016). ‘Dialogue, partnership and empowerment for network and information security’: the changing role of the private sector from regulation adopters to regulation shapers. Crime, Law and Social Change. doi:10.1007/s10611-016-9652-4.
ENISA (2014a). About ENISA. http://www.enisa.europa.eu/about-enisa. Accessed 24 June 2014.
ENISA (2014d). Public private partnerships (PPPs). http://www.enisa.europa.eu/activities/Resilience-and-CIIP/public-private-partnership/public-private-partnerships-ppps. Accessed 24 June 2014.
ENISA (2014c). Good practice guide on cooperative models for effective PPPs. http://www.enisa.europa.eu/activities/Resilience-and-CIIP/public-private-partnership/national-public-private-partnerships-ppps/good-practice-guide-on-cooperatve-models-for-effective-ppps. Accessed 24 June 2014.
European Commission (2009). Protecting Europe from large scale cyber-attacks and disruptions: Enhancing preparedness, security and resilience. http://eur-lex.europa.eu/LexUriServ/LexUriServ.do?uri=COM:2009:0149:FIN:EN:PDF. COM(2009) 149 final. Accessed 14 April 2014.
ENISA (2014b). European Public Private Partnership for Resilience (EP3R). http://www.enisa.europa.eu/activities/Resilience-and-CIIP/public-private-partnership/european-public-private-partnership-for-resilience-ep3r. Accessed 24 June 2014.
Brinkerhoff, D. W., & Brinkerhoff, J. M. (2011). Public-private partnerships: perspectives on purposes, publicness, and good governance. Public Administration and Development, 31(1), 2–14.
Cabral, S., Lazzarini, S. G., & Furquim de Azevedo, P. (2010). Private operation with public supervision: evidence of hybrid modes of governance in prisons. Public Choice, 145(1–2), 281–293.
Hart, O. (2003). Incomplete contracts and public ownership: remarks, and an application to public-private partnerships. Economic Journal, 113(486), 69–76.
Hodge, G., & Greve, C. (2007). Public-private partnerships: an international performance review. Public Administration Review, 67, 545–558.
Osborne, S. P. (2000). Public-private partnerships: theory and practice in international perspective. London: Routledge.
Minow, M. (2003). Public and private partnerships. Accounting for the new religion. Harvard Law Review, 116(1), 1229–1270.
Collier, S. J., & Lakoff, A. (2008). The vulnerability of vital systems: how critical infrastructure became a security problem. In M. D. Cavelty & K. S. Kristensen (Eds.), Securing 'the Homeland': critical infrastructure, risk and (in)security (pp. 17–39). London: Routledge.
Bursh, N. E., & Givens, A. D. (2012). Public-private partnerships in homeland security: opportunities and challenges. Homeland Security Affairs, 8(18), 1–23.
Petersen, K. L. (2008). Risk, responsibility and roles redefined: is counterterrorism a corporate responsibility? Cambridge Review of International Affairs, 21(3), 403–420.
Dempsey, J. S. (2011). Introduction to private security. Belmont, CA: Wadsworth.
Bures, O. (2015). Political corporate social responsibility: including high politics? Journal of Business Ethics, 129(3), 689–703.
Linder, S. H., & Rosenau, P. V. (2000). Mapping the terrain of the public-private policy partnership. In P. V. Rosenau (Ed.), Public-private policy partnerships. Cambridge: MIT Press.
Lee, E. (2009). Homeland security and private sector business: Corporation’s role in critical infrastructure protection. New York: CRC PRess.
Kristensen, K. S. (2008). ‘The absolute protection of our citizens’: critical infrastructure protection and the practice of security. In M. D. Cavelty & K. S. Kristensen (Eds.), Securing ‘the Homeland’: critical infrastructure, risk and (in)security (pp. 63–83). London: Routledge.
Bures, O. (2013). Public-private partnerships in the fight against terrorism? Crime, Law and Social Change, 60(4), 429–455.
European Commission (2013b). New approach to the European Programme for Critical Infrastructure Protection. http://ec.europa.eu/energy/infrastructure/doc/critical/20130828_epcip_commission_staff_working_document.pdf. Accessed 30 May 2014.
Dunn-Cavelty, M., & Kristensen, K. S. (2008). Securing ‘the Homeland’: ciritical infrastructure, risk and (in)security. London: Routledge.
The National Commission on Terrorist Attacks upon the United States. (2004). The 9/11 commission report. http://govinfo.library.unt.edu/911/report/index.htm. Accessed 21. November 2008.
Pursiainen, C. (2009). The challenge for European critical infrastructure protection. European Integration, 31(6), 721–739.
De Bruijne, M., & Van Eeten, M. (2007). Systems that should have failed: critical infrastructure protection in an institutionally fragmented environment. Journal of Contingencies & Crisis Management, 15(1), 18–29.
Joseph, J. (2013). Resilience as embedded neoliberalism: a governmentality approach. Resilience: International Policies, Practices and Discourses, 1(1), 38–52.
Brenna, J., & Mattice, L. (2014). How to add resiliency to your risk management strategy. Security Magazine. http://www.securitymagazine.com/articles/85461-how-to-add-resiliency-to-your-risk-management-strategy. Accessed 26 June 2014.
Chandler, D. (2013). International statebuilding and the ideology of resilience. Politics, 33(4), 276–286.
Bara, C., & Brönnimann, G. (2011). Resilience: trends in policy and research. Crisis and Risk Network (CRN) Focal Report 6. http://mercury.ethz.ch/serviceengine/Files/ISN/134314/ipublicationdocument_singledocument/39e12b8c-34e1-4fd0-a9a4-45a260c21b22/en/CRN-Focal-Report-6-Resilience.pdf. Accessed 23 July 2013.
Bourbeau, P. (2013). Resiliencism: premises and promises in securitisation research. Resilience: International Policies, Practices and Discourses, 1(1), 3–17.
Walker, J., & Cooper, M. (2011). Genealogies of resilience: from systems ecology to the political economy of crisis adaptation. Security Dialogue, 42(2), 143–160.
Petersen, K. L. (2013). The corporate security professional: a hybrid agent between corporate and national security. Paper presented at the annual meeting of the ISA's 54th Annual Convention, San Francisco, CA, USA, April 6, 2013. Retrieved 30.5.2013, from http://files.isanet.org/ConferenceArchive/41b0823857654c71ae63da45c4d6c257.pdf.
Ougaard, M. (2010). Introducing busines and global governance. In M. Ougaard & A. Leander (Eds.), Business and global governance (pp. 1–36). Abingdon: Routledge.
Scherer, A. G., & Palazzo, G. (2011). The new political role of business in a globalized world: a review of a new perspective on CSR and its implications for the firm, governance and democracy. Journal of Management Studies, 48(4), 899–931.
Whelan, G. (2012). The political perspective of corporate social responsibility: a critical research agenda. Business Ethics Quarterly, 22(4), 709–737.
Moon, J., & Crane, A. (2005). Corporate citizenship: toward an extended theoretical conceptualization. Academy of Management Review, 30(1), 166–179.
Moon, J., Crane, A., & Matten, D. (2005). Can corporations be citizens? Corporate citizenship as a metaphor for business participation in society. Business Ethics Quarterly, 15(3), 429–453.
Matten, D., & Moon, J. (2008). “Implicit” and “explicit” CSR: a conceptual framework for a comparative understanding of corporate social responsibility. Academy of Management Review, 33(2), 404–424.
Bures, O. (2012). Private actors in the fight against terrorist financing: efficiency versus effectiveness. Studies in Conflict and Terrorism, 35(10), 712–732.
Vlcek, W. (2006). Acts to combat the financing of terrorism: common foreign and security policy at the European court of justice. European Foreign Affairs Review, 11, 491–507.
Scherer, A. G., Palazzo, G., & Matten, D. (2009). Introduction to the special issue: globalization as a challenge for business responsibilities. Business Ethics Quarterly, 19(3), 327–347.
Deitelhoff, N., & Wolf, K. D. (2010). Corporate security responsibility: corporate governance contributions to peace and security in zones of conflict. Basingstoke: Palgrave Macmillan.
Wolf, K. D., Deitelhoff, N., & Engert, S. (2007). Corporate security responsibility: towards a conceptual framework for a comparative research agenda. Cooperation and Conflict, 42(3), 294–320.
Acknowledgments
The author gratefully acknowledges the financial support by Metropolitan University Prague under research scheme no. VVZ 34-04.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Bures, O. Contributions of private businesses to the provision of security in the EU: beyond public-private partnerships. Crime Law Soc Change 67, 289–312 (2017). https://doi.org/10.1007/s10611-016-9650-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10611-016-9650-6