Abstract
An efficient variant of the recent sea horse optimizer (SHO) called SHO-OBL is presented, which incorporates the opposition-based learning (OBL) approach into the predation behavior of SHO and uses the greedy selection (GS) technique at the end of each optimization cycle. This enhancement was created to avoid being trapped by local optima and to improve the quality and variety of solutions obtained. However, the SHO can occasionally be vulnerable to stagnation in local optima, which is a problem of concern given the low diversity of sea horses. In this paper, an SHO-OBL is suggested for the tackling of genuine and global optimization systems. To investigate the validity of the suggested SHO-OBL, it is compared with nine robust optimizers, including differential evolution (DE), grey wolf optimizer (GWO), moth-flame optimization algorithm (MFO), sine cosine algorithm (SCA), fitness dependent optimizer (FDO), Harris hawks optimization (HHO), chimp optimization algorithm (ChOA), Fox optimizer (FOX), and the basic SHO in ten unconstrained test routines belonging to the IEEE congress on evolutionary computation 2020 (CEC’20). Furthermore, three different design engineering issues, including the welded beam, the tension/compression spring, and the pressure vessel, are solved using the proposed SHO-OBL to test its applicability. In addition, one of the most successful approaches to data transmission in a wireless sensor network that uses little energy is clustering. In this paper, SHO-OBL is suggested to assist in the process of choosing the optimal power-aware cluster heads based on a predefined objective function that takes into account the residual power of the node, as well as the sum of the powers of surrounding nodes. Similarly, the performance of SHO-OBL is compared to that of its competitors. Thorough simulations demonstrate that the suggested SHO-OBL algorithm outperforms in terms of residual power, network lifespan, and extended stability duration.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
An optimization issue is one that has to find the optimum solution in order to satisfy a set of restrictions while also achieving the optimal score for its target pattern. Prior to the advent of heuristic optimization, several mathematical and practical problems were often solved using classical optimization techniques, such as the Newton approach and the gradient descent approach. When dealing with large-scale, high-dimensional, nonlinear complex issues, these techniques, however, have a tendency to trap into local optimums or even make it harder to solve them under increasingly complicated multicoupling restrictions [1, 2].
Many nature-inspired strategies have recently been developed to address complex nonlinear problems. This is because solving real-world difficulties with traditional optimization approaches takes a long time and is not adequately addressed. Nature-inspired approaches, often known as swarm intelligence algorithms, are created by simulating biological organisms. For example, Eberhart and Kennedy suggested particle swarm optimization (PSO) in 1995, motivated by the social attitudes of a swarm of fish and birds [3], and optimization of the ant colony (ACO) was proposed based on mimicking the mobility of actual ants between nests and food resources [4], while the artificial bee colony (ABC) was motivated by bee communities [5]. Similarly, the grasshopper optimization algorithm (GOA) emulates the social forces between locust individuals in nature [6], and the gorilla troops optimizer (GTO) method replicates gorilla troop collective life and social intelligence [7]. Furthermore, the hunger games search (HGS) approach was inspired by hunger-driven activities and animal behavioral choices [8], and the snake optimizer (SO) mimics the unique mating behaviors of snakes. If there is enough food and the temperature is low, each snake (male or female) struggles to find the best mate [9]. Ultimately, Fick’s law optimization (FLA) simulated Fick’s first rule of diffusion, which states that molecules tend to diffuse from higher to lower concentration locations [10].
Fortunately, several metaheuristic algorithms (MAs) have been developed to address various optimization problems in numerous disciplines. In general, MAs are a group of approaches motivated by nature that use specific chaotic agents [11]. Clearly, randomness is a crucial property of MAs [12], which indicates that the solutions acquired in each cycle differ in likelihood and can be found in any part of the search region. In contrast to conventional optimization approaches, they do not ensure that each iteratively plausible option improves, yet they have a strong facility to evade the local solution, which is advantageous to explore and obtain the global solution via multi-agent parallel cycles. Therefore, MAs do not rely on knowledge of the function gradient and have no rigid constraints on convexity and differentiability. Furthermore, MAs are not affected by an individual’s initial positions. MAs have emerged as a family of effective substitutes for canonical optimization techniques for solving difficult large-scale multi-objective issues due to their simple heuristic principles and implementation techniques. MAs have been used successfully in berth allocation [13], feature selection [14], multi-objective optimization [15], and many other domains in recent years.
Generally, tackling optimization issues involves a list of strategic steps. Initially, the arguments for the issue must be chosen and then it may be determined whether the issue is continuous or discrete. The limitations placed on the arguments must also be realized since they distinguish between constrained and unconstrained optimization issues [16]. Lastly, since single-target and multi-target issues are both categories of optimization difficulties [17], it is important to investigate and take into account the issue targets. Depending on the identified arguments patterns, limitations, and number of targets, an appropriate MA could be chosen and used to handle the difficulties.
Despite the fact that there are several effective MAs in the literature that solve various optimization challenges, there are some limitations, such as insufficient diversification and intensification ability, a minor balance between diversification and intensification, ineffectiveness for issues whose derivation is uncertain or computationally expensive, and the most common local optimum entrapment. This prompted researchers to make certain changes to current MAs in order to prevent these drawbacks, particularly local optima trapping. Local escaping operator (LEO) [18], opposition-based learning (OBL) [19], Lévy flights (LF) [20], gradient search rule (GSR) [21], greedy selection (GS) [22], dimensional learning hunting (DLH) [23], and genetic operators (crossover and mutation) [24] are only a few useful methods in the literature to increase the reliability of the solutions gained and to avoid local optima trapping.
The sea-horse optimizer (SHO) [25] is a modern swarm intelligence MA inspired by sea horses’ natural mobility, predation, and breeding pursuits of sea horses. SHO simulates various movement patterns, as well as the potential predation process of sea horses. The movements of a sea horse are classified as spirally floating impacted by the action of marine vortices or drifting following current waves. It then replicates the success or failure of the sea horse in capturing prey with a specific probability. In addition, SHO is meant to produce children while retaining the positive information of the male parent, which is favorable to increasing population variety. In this article, SHO is combined with OBL [26] and GS [27] tactics to strengthen the searchability of SHO and prevent the issue of local optimum trapping. OBL is one of the most beneficial techniques to improve the searchability of MAs [28]. OBL was recently applied in [29] to improve the efficiency of MAs. OBL has reappreciated the candidate solutions generated by a stochastic iteration strategy, as well as their inverse solutions situated in opposing regions of the search space. Compared to a randomly sampled pair of solutions, the OBL strategy has many bio-inspired optimizations combined with it [30]. These optimizations include the cuckoo optimization algorithm [31], the shuffled complex evolution algorithm [32], the PSO [33], the fireworks algorithm [34], and the shuffled frog algorithm [35]. The elephant herding optimization (EHO) algorithm has been improved in [36] to handle the multithresholding problem using OBL learning and the dynamic Cauchy mutation (DCM). The authors of [37] also improved the harmony search algorithm (HS) using OBL. Furthermore, in [38], OBL is used to improve the equilibrium optimization algorithm in image segmentation using multilevel thresholding.
The no-free-lunch (NFL) theory [39] claims that no optimization technique can logically address all the current issues in optimization-related aspects in the literature. Because of this, this concept is regarded as one of the most important fundamental drivers for researchers to suggest new optimization techniques and update those already in place to improve their searchability. In other words, when all aspects of optimization are taken into account, techniques in this field perform similarly on the mean. The rapidly increasing number of optimization approaches that have been suggested during the past ten years has somewhat inspired by this idea.
This paper suggests an updated version of SHO with OBL and GS strategies called sea-horse optimizer-opposition-based learning (SHO-OBL). The OBL strategy is integrated into the predation phase of the SHO to allow sea horses to get closer to the prey and increase their chances of reaching the prey’s preferred position. Also, it is advantageous for enhancing the essential search mechanisms of the SHO-OBL and consequently avoiding local optima entrapment. After determining the new positions of sea horses in the predation phases, the OBL strategy is used to obtain the opposite positions and subsequently compute the fitness values for these two groups of new positions and survive the best to the next phase (breeding phase). Furthermore, the GS strategy of the differential evolution (DE) algorithm [40], which supports the survival concept of the fittest, is applied with some probability here. According to this technique, the most superior fresh sea horses can be strengthened for future iterations, while the least superior ones are ignored. This technique confirms the randomness of SHO-OBL. By introducing the GS technique into SHO-OBL, search powers are improved because each pioneer sea horse can live and then transmit its observed knowledge to other hunter sea horses during the later stages of the search. It is also helpful in stabilizing important diversification and intensification tendencies, allowing SHO-OBL convergence for higher-quality solutions. In general, these two enhancements are made to find more premium solutions to optimization difficulties.
In conclusion, the following are the paper’s significant contributions:
-
The original contribution for this paper is modifying a very recent optimization algorithm called the sea-horse optimizer (SHO) by using efficient strategies such as opposition-based learning (OBL) and greedy selection (GS).
-
The modified SHO, called sea-horse optimizer-based OBL (SHO-OBL), is suggested to address genuine optimization issues.
-
The efficacy of the proposed SHO-OBL is verified using the CEC’20 test platform, three real-world engineering design issues, and the cluster head selection issue in wireless sensor networks (WSNs).
-
The suggested SHO-OBL is superior to SHO and other rivals, according to statistical findings on the CEC’20 test platform and real-world engineering issues.
-
Furthermore, the simulation results on the cluster head selection issue in WSNs demonstrated the super capability of the suggested SHO-OBL in terms of rationalizing the use of residual power, prolonging the network lifespan, and extending the stability period compared to SHO and other competitors.
The remainder of the paper is arranged as follows: The literature is reviewed in Sect. 2. The methodologies used are described in Sect. 3. The recommended SHO-OBL is introduced in Sect. 4. The results of the experiment on CEC’20 are detailed in Sect. 5. The challenge of selecting a cluster head in wireless sensor networks is addressed in Sect. 7. The conclusions and some recommendations for further study are presented in Sect. 8.
2 Literature review
Opposition-based learning (OBL) is commonly utilized in MAs, either as the primary key of motivation for the algorithm or as a tool to improve algorithm performance due to its superior ability to boost the stochastic optimization algorithm’s intensification (exploitation) capability and thus avoid the trap of a local optimum solution. Furthermore, OBL can improve the quality of resource search in uncertain contexts [19]. Several works on MAs and OBL may be found in the literature. The work in [41], for example, introduces OBLGOA, a novel copy of the GOA that relies on the OBL method to address optimization routines of evaluation and engineering problems. The suggested OBLGOA is divided into two phases: The initial phase uses the OBL method to produce the primary population and its inverse; and the other phase employs OBL as a further process to alter the GOA agents in each cycle. Six groups of tests are conducted to investigate the reliability of the suggested OBLGOA, which includes 23 evaluation routines and four engineering issues. The findings of the suggested method outperformed other powerful methods in this domain, according to the experiments. Finally, the acquired findings demonstrated that, compared to powerful methods, the OBLGOA method may deliver competitive results in optimization engineering challenges. The OBL strategy outlined in [29] tries to improve the efficiency of MA. OBL is pertinent to nominee solutions developed by a stochastic cycle scheme and their inverse solutions discovered in opposing parts of the search region that are closer to the global solution (optimum) than a stochastic solution. The OBL tactic has been joined with numerous biomotivated optimization approaches, resulting in lower anticipated distances to the optimum than stochastically chosen solution pairs [30, 42]. For example, in [31], the OBL was utilized to upgrade the CH-EOBCCS cuckoo optimization method. In this approach, the population was altered by combining the OBL strategy with a chaotic variant of the cuckoo search algorithm (CS).
In [32], Fuqing et al. introduced SCE-OBL, an upgrade to the shuffled complex evolution (SCE) algorithm according to OBL, which was used to address the scheduling issue with convolution flow shops, with OBL employed to establish starting agents. To improve the diversification of the ABC algorithm, Zhao et al. suggested the OBL artificial bee colony algorithm (OBL-ABC) [43]. In this investigation, the opposite solutions were computed for the employed bee and the spectator bee. PSO was enhanced by the OBL technique described in [33], in which the OBL was integrated into the modifying step to improve the experiences of the particles and the collective information of the swarm. Gao et al. [44] developed an improved HS that relies on the OBL method to improve the mutation problem, and this methodology was applied to tackle 24 global optimization benchmark routines, as well as the best wind generator architecture. Radha et al. [45] provided an update of the differential evolution method using chaotic and OBL tactics, with the OBL generating the initial population and the chaotic approach updating the mutation parameter. In [34], Gong et al. suggested an upgraded copy of the fireworks technique, in which the OBL was employed to develop secondary agents and force them to jump into newons. In [35], four variants of the shuffling frog learning algorithm (SFL) were suggested, the OBL was used at the initiation level and the differences in the generation of the jumping stage between the four versions were analyzed. To speed up the convergence indication towards the optimum, the method of jointly checking of nominee solution and its opposite is used in optimization issues.
Furthermore, the adaptive hybrid dandelion optimizer, also known as DETDO, was also proposed in [46] as an improvement to the Dandelion Optimizer (DO) by combining three strategies: adaptive tent chaotic mapping, differential evolution (DE) strategy, and adaptive t-distribution perturbation to address the drawbacks of weak DO development, easy fall into local optimum, and slow convergence speed. In [47], a hybrid optimizer dubbed AOA-BSA was proposed to solve the constraints of the Archimedes optimization algorithm (AOA) by substituting its exploitation phase with the exploitation phase of the bird swarm algorithm (BSA). In addition, a transition operator was employed to achieve a high level of balance between exploration and exploitation. Similarly, reference [48] presented a survey on Aquila optimizer (AO), a well-known nature-inspired optimization algorithm developed in 2021 based on Aquila’s prey-grabbing attitude. AO is a population-based, nature-inspired optimization method that has quickly proven its usefulness in the field of complex and nonlinear optimization. As a result, the goal of this study is to present an up-to-date survey on the subject. In [49], the modified beluga whale optimization (mBWO) optimizer was introduced, which included an elite evolution strategy, a randomization control factor, and a transition factor between exploitation and exploitation.
The enhanced jellyfish search algorithm (EJS) was developed, and three improvements were made: adding a sine and cosine learning factors strategy, adding a local escape operator, and applying an OBL and quasi-opposition learning strategy. As a result, increasing, strengthening, and diversifying the population distribution and selecting better individuals from the current and new opposition solutions to participate in the next iteration [50]. The enhanced African vulture optimization algorithm (EAVOA) was proposed in [51] and is based on three different strategies, namely the representative vulture selection strategy, the rotating flying strategy, and the choosing accumulation mechanism, all of which depend on the fundamental AVOA. Furthermore, the artificial ecosystem-based optimization-dwarf mongoose optimization algorithm (AEO-DMOA) was developed in [52] by integrating AEO and DMOA to develop an efficient feature selection (FS) algorithm with better balance between exploration and exploitation. The work in [53] addressed the process of combining two optimization algorithms, atom search optimization (ASO) and particle swarm optimization (PSO), to generate a hybrid algorithm known as hybrid atom search particle swarm optimization (h-ASPSO). ASO is a natural-inspired algorithm that leverages interaction forces and neighbour interaction to direct each atom in the population. PSO, on the other hand, is a swarm intelligence algorithm that employs a population of particles to find the best solution through a social learning process. The suggested method seeks to achieve a balance between exploration and exploitation in order to increase search efficiency.
A novel metaheuristic optimization strategy known as sperm swarm optimization (SSO) was presented in the work in [54]. The movement of sperm to fertilize an egg serves as inspiration for the fundamental principles and ideas of the suggested approach. Sperm swarms in SSO emerge from the Cervix, a region of low temperature. In this direction, sperm look for the Fallopian Tubes, a high-temperature zone where the egg is waiting for the swarm to fertilize it. This zone is thought to be the best option. In order to test the SSO, a number of objective functions representing wireless sensor network quality of services are optimized. These functions are utilized to increase packet throughput and energy efficiency while minimizing end-to-end latency and delay. Moreover, the work in [55] suggested a new hybrid optimization algorithm, HSSOGSA, which combines the gravitational search algorithm (GSA) and SSO. The core principles and ideas behind the suggested algorithm are to combine SSO’s diversification capability with GSA’s diversification capability in order to synthesize the strengths of both algorithms. The CEC’17 suite is used to evaluate the proposed approach’s efficiency. The suggested HSSOGSA is compared with the usual GSA and SSO algorithms. The study’s findings show that the hybrid method outperforms the standard SSO and GSA in terms of escape from local extremes and convergence rate for the majority of benchmark functions in the wide and narrow search space domains. Likewise, the work in [56] presented a new metaheuristic optimization method, the Chernobyl disaster optimizer (CDO). The underlying concepts and principles that guide the suggested strategy were inspired by the Chernobyl nuclear reactor core explosion. The CDO mimics the nuclear radiation process by attaching a human after the nuclear explosion. Basic processes of nuclear explosion and the attachment of a human are carried out, with gamma, beta, and alpha particles included. The CDO is tested by optimizing CEC’17 test bed routines. Furthermore, it is compared to well-known optimization techniques such as SSO and GSA. The experimental results show that it is an efficient and viable option.
Ultimately, an evolutionary crow search algorithm (ECSA) was proposed in [57] to optimize the hyperparameters of artificial neural networks for the diagnosis of chronic illnesses. To address the limitations of the classic crow search algorithm, ECSA incorporates an evolutionary search approach, self-adaptation adaptable flight duration, and an interactive memory mechanism. By preserving population variety, crows’ evolutionary search method and self-adaptive flight length enable them to effectively investigate and exploit problem regions. Furthermore, the study in [58] sought to address the unsatisfactory solutions resulting from binary versions of MAs by proposing an improved binary quantum-based avian navigation optimizer algorithm (IBQANA) for feature subset selection in medical data preparation. The distance-based binary search strategy (DBSS) and the hybrid binary operator (HBO) are two contributions of the proposed IBQANA. Similarly, a novel binary optimizer algorithm called BSMO was presented in [59]. Based on the recently proposed starling murmuration optimizer (SMO), which is highly capable of solving a variety of intricate and technical challenges, it is anticipated that BSMO will similarly successfully identify an optimum subset of attributes. The study in [60] proposed a unique differential evolution (DE) algorithm called the quantum-based avian navigation optimizer algorithm (QANA), which was inspired by migrating birds’ exceptional precision navigation along long-distance aerial itineraries. Furthermore, the study in [61] developed a novel bio-inspired algorithm called the starling murmuration optimizer (SMO) to handle complicated engineering optimization challenges as the most suitable use of MAs. The SMO introduces a dynamic multi-flock structure as well as three new search strategies: spinning, diving, and separating. Depending on the quality of the flocks, the SMO chooses between a diving and whirling technique, striking an equilibrium between intensification and diversity. A variety of benchmark routines with dimensions of 30, 50, and 100 were utilized to test the SMO. The experimental findings demonstrated that, in terms of convergence rate and solution quality, the SMO outperforms other cutting-edge algorithms.
However, a brief series of studies related to cluster head selection challenges in wireless sensor networks (WSNs) employing MAs is described below. In [62], a hybrid Grey wolf and crow search optimization algorithm-based optimal cluster head selection (HGWCSOA-OCHS) method was presented to increase the network lifespan expectation by focussing on latency reduction, distance decrease between nodes, and power stability. The GWO was hybridized with the CSO to address the challenge of precocious convergence, which hinders it from effectively discovering the search zone. This integration of the GWO and CSO approaches into the CH selection procedure maintains the equilibrium between the degree of diversification and intensification in the search zone. The suggested results of the HGWCSOA-OCHS scheme were compared with tested CH selection techniques with ABC, FA, firefly cyclic GWO (FCGWO) and GWO. By equalizing the proportion of active and inactive sensor nodes in the network, the suggested HGWCSOA-OCHS strategy confirmed reduced energy usage and increased network lifespan expectancy. In [63], an efficient tunicate swarm butterfly optimization algorithm (TSBOA) was devised to choose CHs to achieve reliable data delivery between sensor nodes. The suggested TSBOA was created by combining the tunicate swarm algorithm and the butterfly optimization method. As a result, the CH was chosen based on objective parameters such as inter-cluster distance, intra-cluster distance, node energy usage, anticipated energy, connection lifespan, and latency. The deep long- and short-term memory classifier was used to forecast the energy by taking into account the preliminary energy of the nodes. The suggested TSBOA outperformed utilizing criteria such as superfluity energy and packet generation (throughput), which were 0.1118 J and 82.101 percent, respectively.
In [64], a novel strategy is described to extend the life of the network based on an enhanced PSO, which is a metaheuristic method to select the target nodes. The proposed procedure considers both power economy and delivery distance, and relay nodes are employed to reduce the CHs’ arbitrary power usage. The suggested procedure produces superior dispersed sensors and a well-balanced clustering structure, which increases the network’s lifespan. The suggested procedure was compared to comparable procedures by adjusting a variety of factors, such as network space size, number of nodes, and base station position. The simulation results demonstrated that the suggested procedure exceeds other comparable procedures in a variety of conditions. Therefore, to choose the best meeting places, a new method called PSO-based selection (PSOBS) was proposed in [65]. Using PSO, the suggested technique was able to locate optimal or near-optimal rendezvous places for efficient network resource management. In the suggested technique, the weight magnitude was generated for each sensor node according to the number of data packets received from other sensor nodes. The suggested technique was compared with the weighted rendezvous planning-based selection (WRPBS) technique in terms of validation measures like power usage, throughput, hop count, and number of rendezvous spots. The simulation results revealed that PSOBS outperformed WRPBS, but had a higher packet loss rate. The study in [66] developed an energy-efficient CH selection approach based on WOA clustering (WOA-C). As a result, the suggested approach helps to select CHs that are power-sensitive according to an objective pattern that takes into account the superfluity power of the node and the total number of surrounding nodes. The stability of the general approach suggested, power efficiency, throughput, and network longevity were assessed. Additionally, the effectiveness of WOA-C was validated compared to other common modern routing mechanisms such as the low energy adaptive clustering hierarchy (LEACH). Numerous simulations proved the higher efficiency of the suggested algorithm in terms of residual power, network lifetime, and extended stability duration.
3 Materials and methodologies
This section looks at the materials and processes required to develop the suggested approach. The standard SHO and its architecture are elucidated, as are certain essential notions of the OBL and GS strategies.
3.1 Sea-horse optimizer (SHO)
The SHO consists of three key phases: mobility, predation, and breeding. To balance between diversification (exploration) and intensification (exploitation), local and global search techniques are proposed for the social attitudes of mobility and predation, respectively. The breeding attitude is activated after the first two attitudes have been completed. These mathematical models would be expressed and discussed in depth as follows:
3.1.1 Mobility phase
The various mobility routines of sea horses roughly match the normal distribution randn(0, 1). To compensate for the performance of diversification and intensification, \(R_1\) = 0 is used as a trim indicator, half for local mining and the other half for global search. Therefore, the mobility patterns of sea horses can be classified into two types:
Type 1 The spiral motion of the sea horse is in tandem with the maelstrom in the sea. Although the normal random score \(R_1\) falls to the right of the trim indicator, it mainly shows the local intensification of the SHO. The spiral motion of the sea horses leads them to the elite \(P_{elite}\) (optimal solution). The Lévy flight (L) [67], in particular, is used to model the mobility step size of sea horses, which is beneficial for the sea horse with a great likelihood of traversing to other spots in early cycles while preventing an arbitrary local amplification of SHO. At the same time, the spiral-flowing mode of the sea horse continuously adjusts the rotation angle to reinforce the neighbourhoods of existing local solutions. In this scenario, the novel location of a sea horse can be stated numerically as follows:
where P is the location of the sea horse, \(x_c = \eta * \cos (\theta )\), \(y_c = \eta * \sin (\theta )\) and \(z_c = \eta * \theta\) indicate the 3D axes of the coordinates \((x_c\), \(y_c, z_c)\) in spiral motion, respectively, which are beneficial for altering the locations of sea horses. \(\eta\) = a * \(e^{\theta b}\) indicates the stem lengths determined by the logarithmic helical coefficients a and b. \(\theta\) is a chaotic value within the scope of [0, 2\(\pi\)]. \({\text {L}}(z_c)\) is the mechanism of L allocation and is calculated using the Eq. (2) [67].
In Eq. (2), \(\lambda\) is a chaotic esteem in the scope of [0, 2]. c is a fixed constant of 0.01. q and m are chaotic values in the scope of [0, 1]. \(\sigma\) is determined by Eq. 3.
Type 2 Brownian motion of the sea horse with sea waves. While \(R_1\) is placed on the left edge of the trim indicator, the action of drifting is used to diversify the SHO. In this scenario, the search procedure is essential to prevent the SHO from getting to the local end point. Brownian motion is used to emulate an additional travel length of the sea horse to advance its diversification in the search region. The mathematical representation of this category is as follows:
where l is a constant operator. \(\beta _t\) is the chaotic motion operator of the Brownian motion, which is a chaotic score that follows the standard normal allocation in the core. Mathematically, it is given by Eq. (5) [68].
Generally, to get the updated location of the sea horse in the cycle it, these two types can be formulated as follows:
where \(R_1 = randn()\) is a normal chaotic operator.
3.1.2 Predation phase
Success and failure are the two possible consequences for the sea horse when feeding on zooplankton and tiny crustaceans. Given that there is a high probability that the sea horse will succeed in catching prey, the chaotic operator \(R_2\) of the SHO is created to distinguish among these consequences and is set at a crucial esteem of 0.1. The success of the predation process indicates the SHO’s capacity for intensification because the elite reveals, to some extent, the public location of the prey. If \(R_2>\) 0.1, it indicates that the sea horse was successful in predating; that is, the sea horse sneaked up on the prey (the elite), outran the prey, and eventually caught it. Otherwise, when the predation process fails, both respond more slowly than usual, suggesting that the sea horse is likely to start searching the area. This predation attitude can be expressed mathematically as follows:
where \(P_{\text{ new } }^1(it)\) indicates the new location of the sea horse after the mobility phase in the cycle it. \(R_2\) is a chaotic operator, which falls under the scope of [0, 1]. \(\delta\) decreases gradually with cycles to modify the length of the moving step of the sea horse for shooting prey, as determined by Eq. (8).
where \(T_{max}\) indicates the maximum number of cycles.
3.1.3 Breeding phase
The population (individuals) is divided into male and female categories according to their fitness scores. It is worth noting that, because male sea horses are in charge of reproducing, the SHO selects half of the individuals with the highest fitness scores as fathers and the other half as mothers. This divide will promote the inheritance of positive traits among fathers and mothers for the following generation, while avoiding the overallocation of novel solutions. The short mathematical formula for sea-horses’ task assignment is
where \(P_{\text{ sort } }^2\) indicates all \(P_{\text{ new } }^2\) in increasing order of fitness scores. \({\textbf {Fathers}}\) and \({\textbf {Mothers}}\) indicate male and female individuals, respectively.
To create new offspring, random mating occurs between males and females. Each couple of sea horses is supposed to produce only one offspring in order to drive the SHO implement easily. The expression of the \(i^{\text{ th }}\) offspring is as follows:
where \(R_3\) is a chaotic operator in the scope of uniform distribution. i is a positive integer in the scope of [1, individuals/2]. \(P_i^{\text{ Father }}\) and \(P_i^{\text {Mother }}\) indicate randomly chosen agents from male and female individuals, respectively.
3.2 Opposition-based learning (OBL)
The OBL is a beneficial search technique to prevent candidate solutions from becoming stale [26]. The fundamental concept of the OBL, which Tizhoosh [29] introduced, enhances the utility of the search mechanism as an exploitation tool. In MAs, convergence typically occurs instantaneously while the primary solutions are close to the optimal target; otherwise, late convergence is anticipated. In this case, the OBL technique produced better results taking into account opposing search zones that were closer to the global optimum. The OBL explores the search region traversing both directions. In these two instances, one of the original solutions is applied, while the opposing solution specifies the other direction. The OBL then selects the best option from all available options [69].
-
Opposition operator: The concept of opposite operators can be clarified by illustrating OBL. An opposition-based operator can be obtained as follows: Suppose that \(E_0\) is a real operator with scope: \(E_0 \in [G, H]\). The opposite operator of \(E_0\) is demonstrated by Eq. (11) [69].
$$\begin{aligned} \bar{E}_0=G+H-E_0 \end{aligned}$$(11)Furthermore, the opposite operator in the dimension zone is demonstrated by Eqs. (12) and (13)
$$\begin{aligned} E= & {} E_1, E_2, E_3, \ldots \ldots , E_D \end{aligned}$$(12)$$\begin{aligned} \bar{E}= & {} \left[ \bar{E}_1, \bar{E}_2, \bar{E}_3, \ldots , \bar{E}_D\right] \end{aligned}$$(13)The estimation of all dimensions in \(\bar{E}\) is computed using Eq. (14)
$$\begin{aligned} \bar{E}_k=G_k+H_k-E_k \text{ where } k=1,2,3, \ldots , D \end{aligned}$$(14) -
Optimization based on opposition: In the optimization procedure, the equivalent solution \(E_0\) relating to the fitness pattern replaces the opposing solution \(\bar{E_0}\). If \(f\left( E_0\right)\) is better than \(f\left( \bar{E}_0\right)\), then \(E_0\) does not modify, conversely, \(E_0=\bar{E}_0\). Therefore, the solutions are altered with respect to the optimal score of E and \(\bar{E}\) [70].
3.3 Greedy selection (GS)
The DE algorithm’s GS strategy is included in the proposed SHO-OBL to ensure that superior solutions are maintained in future generations (it prevents superior solutions from being lost in subsequent optimization cycles). In other words, this tactic promotes the survival of the fittest concept and is applied under a certain probability, p. The most superior sea horses in each cycle can be further upgraded for future cycles, whereas the least superior sea horses are discarded. This tactic can be expressed mathematically as follows:
where s and p are random operators inside the uniform distribution [0, 1], \(f(P_i^{old})\) is the fitness score of the old location \(P_i^{old}\), and \(P_i^{new}\) indicates the new location determined by the SHO-OBL after applying the mobility, predation, and breeding phases. The operator p in Eq. (15) acquires a chaotic value in each cycle within the scope of [0, 1]. This feature supports SHO-OBL’s random nature. By injecting GS tactics into SHO-OBL, search abilities are upgraded, and each pioneer sea horse has a higher chance of survival, and then shares the knowledge it acquires with other hunters throughout the subsequent stages of the search. Furthermore, encouraging SHO-OBL to focus on higher-quality solutions will enable the stabilization of desirable diversification and intensification indicators.
4 The SHO-OBL algorithm
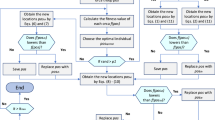
This section discusses in great detail the development of the suggested SHO-OBL to solve different optimization difficulties. The SHO-OBL model is depicted in detail in the flow chart in Fig. 1. The OBL is employed in the suggested technique to accelerate the convergence of the SHO-OBL towards the optima. OBL is a local search approach that seeks to alleviate the downsides of chaotic populations while increasing the algorithm’s convergence by increasing the variety of its solutions. As a result, the smaller stages allow the entire search to thoroughly scan the prospective region. The suggested SHO-OBL approach has been described in further depth in the following phases:
-
1.
Initialization phase SHO-OBL begins with initializing the locations of the sea horses. Assuming that each sea horse symbolizes a candidate solution in the issue search region, the whole population of sea horses (indicated by Seahorses) can be described as follows:
$$\begin{aligned} Seahorses =\left[ \begin{array}{ccc} p_1^1 &{} \cdots &{} p_1^{\text{ D }} \\ \vdots &{} \ddots &{} \vdots \\ p_{\text{ n }}^1 &{} \cdots &{} x_{\text{ n }}^{\text{ D }} \end{array}\right] \end{aligned}$$(16)where D indicates the scale of the solution and n is the population length. Each solution is picked chaotically among the minimum and maximum bounds of the issue, indicated by \(l_b\) and \(u_b\), respectively. The expression of the \(i{th}\) individual \(P_i\) in the search region is
$$\begin{aligned} \begin{aligned}&P_i=\left[ p_i^1, \ldots , p_i^{\text{ D } }\right] \\&p_i^j= \text{ rand } * \left( u_b^j-l_b^j\right) +l_b^j \end{aligned} \end{aligned}$$(17)where rand indicates the uniform distribution [0, 1]. \(p_i^j\) indicates the scale jth in the \(i{th}\) solution. i is a positive index in the scope of [1, n] and j is a positive index in the scope of [1, D]. \(l_b^j\) and \(u_b^j\) depict the minimum and maximum bounds of the jth solution of the dedicated issue.
-
2.
Mobility phase During the mobility phase, the sea horse coils its tail around an algal stem (or leaf). The sea horse performs spiral movements at this time because the stems display spiral floating changes around the roots of algae as a result of the influence of marine vortices. Brownian motion also occurs when the sea horse is suspended upside down from drifting algae or other items and travels randomly with the waves. The SHO-OBL employs Eq. (6) mathematically.
-
3.
Predation phase During the predation phase, sea horses use the unique shape of their heads to sneak up on prey and capture it with up to a success rate of 90%. Equation (7) is used mathematically by the SHO-OBL.
-
4.
OBL phase The OBL approach is applied here to identify the opposite solution to each solution found in the preceding step (predation phase). The OBL approach notion is then used to determine the \(Opposite_i\) dimension vector for each solution in the predation population using Eq. (18). Subsequently, the fitness score for each pair of solutions (solution from the predation phase and its opposite from the OBL phase) is evaluated and survives the best to the nest phase (breeding phase).
$$\begin{aligned} Opposite_i=l_b^j+u_b^j-P_i, i \in 1,2, \ldots , n \end{aligned}$$(18)where \(Opposite_i\) is a solution that preserves dimension vectors by employing the OBL approach, and \(l_b^j\) and \(u_b^j\) are the minimum and maximum limits of the motif jth of a dimension vector P.
-
5.
Breeding phase In the breeding phase, male and female sea horses breed by chaotically mating to create new offspring, helping the offspring inherit certain good traits from their parents (Fathers and Mothers). The SHO-OBL algorithm applies Eq. (10).
-
6.
GS phase After applying the previous phases, the SHO-OBL algorithm performs the GS approach using Eq. (15). Consequently, the most superior sea horses of the current generation can be kept and passed on to the next generation.
-
7.
Final phase The suggested algorithm selects the best solution (\(P_{elite}\)) with respect to the better fitness scores.
In summary, these phases help sea horses adjust to their surroundings and develop well. The suggested SHO-OBL approach is fundamentally motivated by the aforementioned phases. Therefore, these phases formed our encouragement to suggest this reinforced optimizer through mathematical formulations.
4.1 The implementation process of SHO-OBL
The pseudo-code of the suggested SHO-OBL algorithm is illustrated in Algorithm 1. The implementation process of the SHO-OBL begins the population initialization by developing a set of chaotic solutions. After the sea horse population is altered by Eqs. (6) and Eq. (7). Equation (18) is employed to identify the opposite solution to each solution found in the predation phase (OBL phase). Subsequently, Eq. (10) is calculated to breed the offspring and, finally, Eq. (15) is utilized to perform the GS phase. A new population is composed of the offspring and the previous updated sea horses. However, the size of this new population is 1.5n. To prevent the population from expanding without limit, each solution in the new population is calculated. Solutions are sorted ascending order from top to bottom according to fitness scores, and the first n sea horses are iteratively chosen as the new population for the next evolutionary process.
4.2 Computational complexity
The complexity of an algorithm is a significant indicator to hypothetically measure its optimization performance. The time complexity of the proposed algorithm is explained further in the following:
-
Consumes \(O(n * D)\) time to initialize the population of solutions, where D indicates the scale of the solution and n is the length of the population. O(n) is necessary to compute the fitness score of each solution.
-
Throughout cycles, computing the fitness score of each solution is \(O(T_{max} * n)\) time, where \(T_{max}\) is the highest degree of cycles.
-
In SHO-OBL, the mobility phase, predation phase, OBL phase, breeding phase, and GS phase of solutions require \(O(T_{max} * n * D)\) time.
Consequently, the overall time complexity of the suggested SHO-OBL algorithm is \(O(T_{max} * n * D)\).
5 Experimental results and discussion on CEC’20 test suite
This section shows the validity investigation and experimentation of the developed SHO-OBL algorithm on 10 common benchmark test beds. Numerous benchmark test procedures, along with parameter settings and statistical evaluation measures, are described in full below. The effectiveness is contrasted with that of other renowned MAs. The tests were carried out using Matlab software version R2014a on a computer with a 64-bit Core i7 processor operating at 3.20 GHz and 8 GB of primary memory.
5.1 Parameter configurations
Table 1 displays the parameter configurations applied during the trials for each of the competing algorithms. The issue scale or dimension (D), the individual number (n), and the highest degree of cycles (\(T_{max}\)) have been set to 10, 30, and 1000 accordingly. Each benchmark issue is given 30 independent runs (NR) of each algorithm considered for statistical analysis. Furthermore, the parameters of each algorithm are left at their default values for adequate practice, as indicated in [71], to reduce the likelihood of better parametrization bias.
5.2 Statistical assessment indicators
The following evaluation indicators are applied to gauge the viability and effectiveness of the developed SHO-OBL algorithm:
-
1.
Mean: the arithmetic mean of fitness scores acquired by the algorithm after a certain number of NR. It is computed by
$$\begin{aligned} Mean = \frac{{\mathop \sum \nolimits _{e = 1}^{NR} \left( {{f_e}} \right) }}{NR} \end{aligned}$$(19) -
2.
Standard deviation (SD): the fluctuation in fitness scores acquired after implementing the algorithm NR times. It is computed by
$$\begin{aligned} SD = \sqrt{\frac{1}{NR-1} \varSigma _{e=1}^{NR}\left( f_{e}-M e a n\right) ^{2}} \end{aligned}$$(20) -
3.
Best: the lowest fitness score acquired after implementing the algorithm NR times (in case of minimization optimization issue). It is computed by
$$\begin{aligned} Best = \mathop {\min }\limits _{1 \le e \le NR} {f_e} \end{aligned}$$(21) -
4.
Worst: the highest fitness score obtained after implementing the algorithm NR times (in case of minimization optimization issue). It is computed by
$$\begin{aligned} Worst = \mathop {\max }\limits _{1 \le e \le NR} {f_e} \end{aligned}$$(22)where \({f_e}\) is the best fitness score acquired at run e.
5.3 CEC’20 analysis
Ten CEC’20 benchmark routines are used to evaluate the suggested SHO-OBL [72]. The procedure iterates 1000 times for each benchmark routine, simulating 30 independent running times on a scale of 10. Unimodal, multimodal, hybrid, and composite routines are the four main categories of benchmark evaluation routines. The DE [73], GWO [74], MFO [75], SCA [76], FDO [77], HHO [78], ChOA [79], FOX [80], and basic SHO [25] approaches are compared to SHO-OBL in this respect.
An overview of the numerous benchmarking procedures employed is provided below: Initially, the global optimum of the unimodal routine F1 is utilized to compare the potential for intensification of the suggested SHO-OBL with that of rival MAs. The SHO-OBL competes admirably with the equivalent MAs, as shown in Table 2. Due to the positive effects of incorporating OBL methodology, the SHO-OBL achieves the best routine F1 result and has a good intensification on the scale of the tested issue. Second, for multimodal routines F2-F4, there are generally more local optima than for unimodal routines. The number of multimodal routines increases enormously with the scale of the issue. Thus, benchmark routines of this kind are quite helpful in evaluating the ability of contrasted MAs to diversify. The results in Table 2 for the routines F2-F4 demonstrate that SHO-OBL has nearly flawless diversification capabilities. The SHO-OBL consistently performs best in a number of benchmarking issues. This accomplishment is the result of the comprehensive diversification techniques used by the SHO-OBL, which reflect the desired global optimum’s attitude. Finally, the hybrid arithmetical (F5-F7) and composite (F8-F10) routines represent a collection of the most challenging issues that are utilized to test the diversification and intensification balancing abilities, as well as the escape mechanism from local optima entrapment for the suggested SHO-OBL and competitive MAs. The outcomes that are reported in Table 2 for routines F5-F10 show that SHO-OBL is effective because, compared to other competing MAs, it provides superior outcomes and performance in terms of the Mean and SD statistics for \(D=10\).
5.3.1 Diversification and intensification analysis
Consider Fig. 2, which depicts the arithmetic mean of the suggested SHO-OBL’s diversification and intensification stages based on Eq. (23), for a better understanding of the suggested SHO-OBL’s diversification and intensification balancing capabilities. As seen by the curves in Fig. 2, the SHO-OBL generates good intensification rates for calculating the global optima. Moreover, the SHO-OBL maintains a reasonable balance between the stages of intensification and diversification, and has a strong probability of escaping local optima.
where Median (\(P^j\)) is the statistical median esteem of the jth scale of all sea horses with the number n and \(P_{i}^{j}\) is the jth scale of \(i{th}\) sea horse. \(Diff_j\) is the arithmetic mean diversity esteem for scale j. This scale-wise diversity is then averaged (\(Diff^{it}\)) on all the D scales for cycle it and \(it = 1, 2, \dots , T_{max}\). Once sea horses diversity is determined for \(T_{max}\), the ability to quantify how much of the search mechanism was intensificative and how much was diversifiative is now available. The estimation of the diversification/intensification proportion is provided by
where \(Diff_{high}\) is the highest diversity obtained in all \(T_{max}\).
In this regard, Table 2 shows that, compared to rival MAs, the suggested SHO-OBL is the correct choice for the six benchmark routines (F5-F10). This finding implies that SHO-OBL can successfully balance the stages of intensification and diversification. The vector P was updated using the pulling capacity of the adaptive delineation. Some cycles focus on diversification (|P| \(\ge\)1), while others concentrate on intensification (|P| < 1).
5.3.2 Boxplot analysis
The boxplot analysis can visualize the attributes of data distribution. A boxplot of outcomes for each approach and routine is presented in Fig. 3 to aid in understanding the distribution of outcomes because this category of routines is associated with a significant number of local minima. Boxplots are a great tool for displaying quartile-based data distributions. The minimum and maximum data points of the algorithm, which make up the whisker’s edges, are also its lowest and highest data points. The lower quartile and higher quartile are shown by the corners of the rectangles. A small boxplot suggests strong data agreement. The results of a boxplot with ten routines (belonging to CEC’20) are shown in Fig. 3 for D = 10. For most routines, the boxplots of the suggested SHO-OBL approach have the minimum scores and are relatively narrow when compared to the distributions of the other approaches. The recommended SHO-OBL approach performs better than the other alternative approaches on the bulk of the test routines, but only on F2 and F10 does it exhibit restricted performance. This is due to the OBL approach influence, which causes algorithm individuals to suddenly travel in the opposite direction and for a specific length of time in the search space, particularly during the OBL phase. This results in a variety of mutations in the algorithm’s best fitness ratings, which negatively impact the standard deviation of these scores (data distributions). It is true that the OBL approach helps the algorithm find the search space extremely effectively and avoid local optima entrapment (excellent intensification ability), leading to the achievement of optimal fitness routine scores, but occasionally in a large boxplot, as shown in the cases of F2 and F10.
5.3.3 Convergence analysis
The convergence curve displays the best scores each competing algorithm received for the fitness pattern under consideration at time t (\(t = 1, 2, \dots , T_{max}\)), for all competing algorithms. As a result, it reveals which competing algorithm can reach the optimal solution quickly (convergence speed), and as a result, the chosen algorithm will be the best. The convergence curve is particularly crucial because it provides a visual representation of how well competing MAs can minimize or maximize the fitness pattern. The analysis of MA convergence rates is aided by this investigation. The convergence curves of the suggested SHO-OBL and other rivals are shown in Fig. 4 for 1000 cycles and 30 independent runs.
The convergence curves of the suggested SHO-OBL and their rivals for the CEC’20 routines are shown in Fig. 4. The suggested solution reached a stable position for all of the routines taken into consideration (F1-F10). This indicates that the proposed approach is convergent. The suggested method also yields the minimum solutions and is currently the fastest for the majority of routines. Because of its speedy convergence to a close-optimal solution, the suggested SHO-OBL is a possible MA for addressing issues that need quick computing, such as online optimization issues.
5.3.4 Qualitative analysis
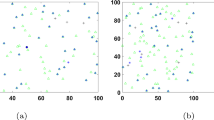
This investigation was carried out on the scales of sea horses in 10 well-known routines, with the primary goal of observing SHO-OBL’s behavioral optimization capacity. The number of individuals and the highest degree of cycles were set at 30 and 1000, respectively. Figure 5 shows the qualitative measurements of SHO-OBL for dealing with partial unimodal, multimodal, hybrid, and composite routines of CEC’20. The topological structures of test routines from a two-dimensional perspective are described in the first column. The last three columns are the investigation indicators, which include the search history, the trajectory of the first sea horse on the first scale, and the average fitness of all sea horses.
The location distribution of all sea horses during the iterative process can be seen in the search history, with the red rot signifying the SHO-OBL obtained global optimum solution. Many individuals cluster around the global optimum in unimodal routines, as is clearly seen in the second column of Fig. 5. However, for multimodal routines, the majority of individuals are dispersed throughout the entire search space near various local optima. The suggested SHO-OBL algorithm can benefit from local re-intensification for unimodal routines in order to increase accuracy. The decentralized form displays the variety of sea horses across the entire region and the conflict between several local optimum scores in terms of multimodal routines.
The primary exploratory attitude of the individual is reflected in the first-dimensional trajectory of the first sea horse. In the early cycles, the curve swings dramatically, as illustrated in the third column of Fig. 5, but in the late cycles the vibration’s magnitude tends to be slowly perceived. The adjustments in the curve ensure that SHO-OBL gradually shifts from a process of global diversification to one of local intensification. The brief duration of the oscillation state in unimodal procedures suggests that SHO-OBL converges quickly. The oscillation stage in multimodal routines typically lasts for a long period, even outstripping 60% - 70% of the iterative process, which demonstrates the SHO-OBL’s strength for global diversification.
The mean fitness history provides the average target score of all sea horses in each cycle. It mostly serves as a reflection of the population’s overall inclination to evolve. It is evident from the fourth column of Fig. 5 that the whole population advances from the first level to the final. The average fitness scores tend to drop as a result of the sea horses’ continuous updating. For unimodal routines, the curve abruptly declines just at the start of the cycle. Following the sharp decline, the variability in the curve’s tangent slope approaches stability. This illustrates how SHO-OBL converges to a value that is close to optimal in early cycles and then improves intensification accuracy. Multimodal routines, on the other hand, have higher curve rates. The curve’s amplitude drops as the number of cycles rises, suggesting global diversification in the premature levels of SHO-OBL and local intensification in the latter levels.
In conclusion, after these investigations, it was found that the proposed SHO-OBL has the following merits compared to other competitors: higher local intensification capability, excellent convergence accuracy, and strong algorithm stability and resilience. In detail, a thorough search for the elite in the predation phase and a long-term spiral motion search affected by a vortex can guarantee the intensification of the searching agents for the global optimal. Additionally, SHO-OBL performs well in terms of global optimization and is adept at avoiding local extremums thanks to the merged OBL phase. Consequently, SHO-OBL still competes with the most recent or state-of-the-art MAs and has high convergence accuracy and good robustness. Also, the second mechanism of the mobility phase reflects both the population diversity of the progeny’s offspring and the global diversification caused by Brownian motion. However, the OBL mechanism also has limitations in that it can only search for one opposite point in the opposition space. Therefore, it could be inefficient in some situations, e.g., if the domain and search space of a problem are symmetrical. Moreover, the embedded OBL and GS strategies may negatively affect the time complexity cost, as they cost the algorithm two additional steps in each optimization cycle.
6 Optimization engineering challenges
Despite the fact that previous findings strongly suggest that the proposed SHO-OBL can address genuine problems with greater effectiveness than SHO and other competitors, three genuine structural challenges, including welded beam design, tension/compression spring design, and pressure vessel design, are used to demonstrate the reliability of the proposed SHO-OBL in addressing such engineering issues with unidentified search spaces. These tasks are used to compare the proposed SHO-OBL with rival algorithms. As a result, there are specific constraints in engineering design challenges and a handling technique should be used to meet them. In the literature, there are different restriction management techniques, including penalty routines (e.g., annealing, adaptive, static, dynamic, and death penalty routines) [16]. As a consequence, in this study, the death penalty routine is used to address various restrictions on engineering design issues. The death penalty procedure automatically removes inapplicable choices throughout the optimization method by advising the MAs (thereby decreasing the big fitness score). The major merits of this technology are its low computational cost and simplicity. The death penalty routine is used when dealing with engineering design restraints. The efficacy of the proposed SHO-OBL is compared to that of nine familiar MAs, including DE, GWO, MFO, SCA, FDO, HHO, ChOA, FOX, and SHO.
6.1 Welded beam design
The target function of the welded beam design issue is suggested in [81] to minimize the fabrication cost of the welded beam. The cost of a welded beam design like the one depicted in Fig. 6 is minimized while keeping certain limits in mind. The bending stress in the beam \((\theta )\), the shear stress \((\tau )\), the buckling load (Pc), and the end deflection of the beam \((\delta )\) are all optimization constraints in this issue. The thickness of the weld (h), the length of the clamping bar (l), the height of the bar (t), and the thickness of the bar (b) are the four optimization variables. The mathematical description of this issue is given in Appendix A.
The acquired optimization outcomes, as shown in Table 3, show that the proposed SHO-OBL can effectively address the welded beam issue with the best outcomes by lowering its cost. The statistical findings in Table 4 were acquired in 30 independent runs for the proposed SHO-OBL and the competing algorithms, with \(T_{max}\) set to 1000. It is apparent that SHO-OBL can effectively discover the best design at the lowest cost.
6.2 Tension/compression spring design
The major goal of this engineering design issue is to make the tension/compression spring as light as feasible stated in [82]. Figure 7 shows a schematic example of the tension/compression spring issue. Surge frequency, shear stress, and deflection limitations must all be met in the ideal design. Wire diameter (d), mean coil diameter (D), and the number of active coils (N) are the three optimization variables. The mathematical description of this issue is formulated in Appendix B.
Table 5 shows the acquired optimization outcomes, indicating that the proposed SHO-OBL has accomplished the excellent outcomes in addressing this issue by minimizing the tension/compression spring weight. Table 6 demonstrates the statistical data acquired for the competing methods during 30 independent runs, with \(T_{max}\) = 1000.
6.3 Pressure vessel design
The target function of the pressure vessel design issue reduces the overall cost of the cylindrical pressure vessel (forming, material, and welding) [83]. Figure 8 depicts a schematic model of the tension/compression spring issue. The thickness of the shell \((T_s)\), the thickness of the head \((T_h)\), the inner radius (R), and the length of the cylindrical section without taking into consideration the head (L) are the four optimization variables. The mathematical description of this issue is formulated in Appendix C.
The acquired optimization outcomes are reported in Table 7, demonstrating that the suggested SHO-OBL produced the excellent outcomes in addressing this issue by decreasing the overall cost of the cylindrical pressure vessel (forming, material, and welding). Table 8 shows the statistical data acquired for the proposed SHO-OBL and other competitors over 30 independent runs, with \(T_{max} = 1000.\)
7 Clustering challenge in WSNs
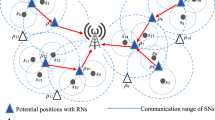
Wireless sensor networks (WSNs) are a new technology that has seen a steady increase in its applications. This is due to its implementations in the environment, surveillance, and biosphere tracking. Recent advances in infrastructure frameworks have helped connect the world through intelligent networks, advanced layout, smart cities, and intelligent transportation [84]. The Internet of Things (IoT), in which sensor nodes form a crucial task, is a common component in these systems, which are subsequently intimately integrated with information and communication technologies. A typical WSN is made up of many tiny, low-cost, low-power sensor nodes (SN) and at least one base station (BS) [85]. The target of WSN is to scan at least one characteristic of a particular scope, known as the zone of fascination or the detecting region. Significant needs for WSN include energy economy, versatility, and correspondence range. The majority of sensors have nonrechargeable batteries, and once they are put in the zone of events, they work until the batteries are depleted. It is not practical to exchange the batteries in the sensor nodes because they are regularly deployed in hostile or remote environments. Although WSNs utilize energy in a variety of ways, data transmission accounts for the lion’s share of this consumption. Therefore, one of the main challenges in extending the system’s life is designing an energy-efficient protocol for WSN. Moreover, the system scale may have an impact on longevity. The system’s dependability becomes increasingly important as the scale increases. Several tactics have been suggested for extending the sensor network’s lifespan. One of the most significant approaches to manage power consumption in WSN is clustering [86], and a hierarchical structure design provides a reliable solution to the challenges of network longevity and immutability. The network is separated into numerous levels and given a hierarchical architecture design in which different nodes perform different functions. The WSN’s sensing region is divided into various groups known as clusters. Each of these clusters consists of a single cluster head (CH) and cluster members (CM) (see Fig. 9). The CH first collects data from each CM and then collects the data. Subsequently, it transmits the compiled data to the distant BS. Moreover, the BS is linked to either a private or public network. There are many advantages to this clustering strategy. At first, it helps to remove extraneous data from the CH level itself. resulting in a reduction in energy use for each node as a result of the decreased data transmission. Second, there is a major improvement in the network’s scalability. Additionally, because sensor nodes communicate with their CH directly, it also saves bandwidth by reducing the amount of duplicate messages sent among sensor nodes. CH-selection is an optimization issue that also happens to be NP-hard [87]. Techniques for canonical optimization fail when the network is enlarged. A new swarm intelligence optimization technique called SHO-OBL works well for NP-hard situations. Additionally, it has noteworthy diversification and intensification properties that promote speedy convergence and the capacity to avoid local minima, provides excellent solutions, and is simple to implement. In this paper, the selection of CHs in WSNs is optimized using the SHO-OBL algorithm, a potent optimization algorithm. The algorithm aids in effectively choosing the CHs from among the sensor nodes while considering their remaining power. An algorithm is thoroughly assessed to demonstrate its dominance over other competing algorithms.
7.1 Network paradigm
The network paradigm is regarded as a free-space paradigm. It has a sender and a receiver that are separated by a distance. The amplifier devices can also be found at Tx and Rx. The following WSN attributes are assumed:
-
Sensor nodes are planted at random and remain immobile.
-
Nodes are uniform and have a finite amount of power.
-
BS is static and can be placed either indoors or outdoors in the service region.
-
Each node collects data regularly and constantly has some data to forward.
-
Nodes have no idea where they are positioned or where other nodes are positioned.
-
The nodes self-organize and do not require monitoring after implementation.
-
Data fusion is employed to decrease the overall quantity of transmitted data.
-
Each node has the ability to act as a CH.
All of the above traits and constraints apply to the WSN scenario under consideration for simulation. The distance among the BS and other nodes can be calculated by comparing the received signal strength. As a result, it does not require any further system with position facilities, such as GPS. A node also accedes to the cluster whose CH is closest to it.
7.2 Power paradigm
In this paper, the power paradigm is designed according to the first-order radio model described in [88]. In this type, the sender must energize radio equipment and a power amplifier, which uses power. Similarly, the receiver uses power to energize the radio equipment on its side. Additionally, the node’s power consumption is proportional to the amount of data delivered and the distance travelled. Because of the alleviation with distance, a power loss paradigm with \(Dist^2_{ij}\) for comparatively low distances and \(Dist^4_{ij}\) for higher distances is utilized, where \(Dist_{ij}\) is the distance among sensor nodes i and j. The reproduction distance Dist is therefore compared to a threshold distance \(Dist_0\), and while the reproduction distance Dist is smaller than \(Dist_0\), the power consumption of a node is equivalent to \(Dist^2\), otherwise it is equivalent to \(Dist^4\) [88]. Equation (25) provides the total power used by a node to transmit a l-bit data packet.
where \(En_{\text{ ele }}\) indicates the power consumption per bit for sender or receiver device. \(En_{\text{ ele }}\) depends on various factors such as the modulation technique, electronic coding, and emission of the pulse. Amplifier power for free-space is \(\varepsilon _{\text {fs}}\) and for multi-path paradigm, it is \(\varepsilon _{\text {mp}}\) which relies on sender amplifier paradigm. The power utilized by the receiver while accepting 1-bit of data is determined by Eq. (26).
7.3 Objective function
A fitness function directs the CH selection. In the SHO-OBL optimization, the fitness function is critical to the investigation of the prey component. The node’s characteristics, including its number of neighbours and remaining power \(En_{residual}\), contribute to this. According to Eq. (27) [89], the fitness function is given:
where the \(\alpha _1\) and \(\alpha _2\) are random operators inside the uniform distribution [0, 1]. Number\(\left( \text {CH}_i\right)\) is the collection of all neighboring nodes surrounding a specific \(\text {CH}_i\), and the \(\text {CH}_{\text {Energy}}\) is the neighbor node’s remaining power magnitude. According to the maximal optimization issue, the optimal option is the one with the highest fitness score; as a result, the highlighted node will have sufficient remaining power and a sufficient number of surrounding nodes to become the \(\text {CH}\).
7.4 Simulation environment
In MATLAB 2014a, the suggested algorithm was simulated and the outcomes were shown. The system specification included an Intel Core i7 processor, 8 GB of RAM, and Windows 10. The emulations were run several times with different stipulations, such as the number of nodes and CHs. The detecting area of the network was considered to be 500 x 500 \(m^2\). The first simulations are being run on WSN #1, which has 200 sensor nodes and 20 CHs. The simulations were then reiterated on WSN #2 with 400 sensor nodes and 40 CHs and on WSN #3 with 600 sensor nodes and 60 CHs. The BS location was also altered for various instances. The BS was located inside the detecting area at (250,250) in the first instance, at the edge of the detecting area at (500,500) in the second instance, and outside the detecting area at (250,600) in the third instance. The algorithm was run 20 times, and the average of the resulting data instances was utilized to depict the findings. The algorithm was evaluated with a population size of 30 individuals. Table 9 lists the many simulation arguments that were explored.
7.5 Simulations and analysis
The emulations were performed according to numerous factors and under various circumstances. For each network instance, the simulations’ findings and analyses are demonstrated. The SHO-OBL algorithm was tested in various scenarios. Between 200 and 600 nodes made up the total, and 20–60 CH were present. Three alternative situations were presented: WSN #1 includes 200 nodes and 20 CHs; WSN #2 includes 400 nodes and 40 CHs; and WSN #3 includes 600 nodes and 60 CHs. For performance comparisons, several MAs were also put to the test under comparable circumstances. Utilizing WSN #1 as the default WSN scenario, DE, GWO, MFO, SCA, FDO, HHO, ChOA, FOX, and SHO were contrasted with the suggested SHO-OBL algorithm. Here, the power usage of several MAs techniques varies based on the location of the CH and the BS. Tables 10, 11, and 12 report the power usage rates for each considered network scenario with different locations of the BS (center, corner, and outside) after determining the optimal location for the CH node by comparative MAs, it is clear from these tables that when the location of the BS moves away from the center of the detecting area, the power usage rate increases, also in most cases in all the considered network scenarios the suggested SHO-OBL algorithm achieves the lowest power rate comparing to other algorithms for example in WSN #2 at BS Corner the power rates for DE, GWO, MFO, SCA, FDO, HHO, ChOA, FOX, SHO, and SHO-OBL are 194.68 J, 193.23 J, 181.34 J, 185.47 J, 170.42 J, 176.32 J, 194.57 J, 192.37 J, 175.12 J, and 166.42 J respectively. It is clear that the suggested SHO-OBL algorithm records the lowest rate of 166.42 J; this may be because the suggested SHO-OBL algo rithm takes the node’s power into account before choosing it as a CH. The SHO-OBL algorithm has a powerful search mechanism that comes from integrating OBL and GS tactics into its main search mechanism. As a result, the algorithm selects the optimal location for the CH node.
In WSN #1, which includes 200 nodes and 20 CHs, Fig. 10 shows the power usage rates of the sensor network utilizing various MAs strategies for the central (250,250), corner (500,500), and outside (250,600) BS locations. Because the suggested SHO-OBL algorithm takes the node’s power into account before choosing it as the CH, it performs better. Also, as the nodes communicate to the closest CH, less power is used. Additionally, larger networks with more CHs are used in the simulations. The BS location can be found in a variety of locations, including the center (250,250), the corners (500,500), and the outside (500,600). The comparative MAs were applied to compare how much power was consumed in various scenarios. The CHs were adjusted from 20 to 60 in accordance with the sensor nodes, which ranged from 200 to 600. The total power used by different MAs under various circumstances is displayed in Figs. 11 and 12 for WSN #2 and WSN #3 respectively.
The amount of power consumed in each scenario varies depending on the MA. The power performance of DE, GWO, MFO, SCA, FDO, HHO, ChOA, FOX, SHO, and SHO-OBL decreases as the network size grows. However, when the node count increases, the suggested SHO-OBL approach performs significantly better. Furthermore, the recommended SHO-OBL approach exceeds all existing algorithms in terms of stability and independence from BS location. Because the BS location is frequently unknown in real-time applications, an algorithm whose performance is independent of the BS location is highly sought, which is exactly what the suggested approach provides.
8 Conclusion and future work
The OBL and GS strategies are combined with SHO to create SHO-OBL, an upgraded copy of SHO. By strengthening the algorithm’s local searchability (intensification capability) and reinforcing its opportunity to evade becoming trapped in local optima, the quality of acquired solutions can be raised. The suggested SHO-OBL is used to address various optimization issues and is validated in ten CEC’20 test patterns and three engineering design issues, including the welded beam, the tension/compression spring and the pressure vessel. Additionally, the issue of CH selection in WSNs is also dealt with using it. Comparisons are made between the suggested SHO-OBL and DE, GWO, MFO, SCA, FDO, HHO, ChOA, FOX and the basic SHO. The test results on the CEC’20 investigation platform and engineering design issues showed that the proposed SHO-OBL has outperformed the basic SHO and other rivals in providing high-quality solutions. Subsequently, by producing low power consumption rates, the suggested SHO-OBL offered the greatest performance in addressing the issue of CH selection in WSNs. The SHO-OBL can eventually be used to address additional issues such as image processing, data mining, industrial tasks, and data clustering. Additionally, multi-objective versions can be added to the SHO-OBL algorithm to address multi-objective optimization issues.
Data availibility statement
Data sharing is not applicable to this article as no data sets were generated or analyzed during the current study.
References
Saha, C., Das, S., Pal, K., Mukherjee, S.: A fuzzy rule-based penalty function approach for constrained evolutionary optimization. IEEE Trans. Cybern. 46(12), 2953–2965 (2014)
Houssein, E.H., Sayed, A.: Dynamic candidate solution boosted beluga whale optimization algorithm for biomedical classification. Mathematics 11(3), 707 (2023)
Kennedy, J., Eberhart, R.: Particle swarm optimization. In: Proceedings of ICNN’95—international conference on neural networks, vol. 4, pp. 1942–1948. IEEE (1995)
Dorigo, M., Di Caro, G.: Ant colony optimization: a new meta-heuristic. In: Proceedings of the 1999 congress on evolutionary computation-CEC99 (Cat. No. 99TH8406), vol. 2, pp. 1470–1477. IEEE (1999)
Karaboga, D., et al.: An idea based on honey bee swarm for numerical optimization. Technical report, Technical report-tr06, Erciyes university, engineering faculty, computer (2005)
Saremi, S., Mirjalili, S., Lewis, A.: Grasshopper optimisation algorithm: theory and application. Adv. Eng. Softw. 105, 30–47 (2017)
Abdollahzadeh, B., Gharehchopogh, F.S., Mirjalili, S.: Artificial gorilla troops optimizer: a new nature-inspired metaheuristic algorithm for global optimization problems. Int. J. Intell. Syst. 36(10), 5887–5958 (2021)
Yang, Y., Chen, H., Heidari, A.A., Amir H, G.: Hunger games search: visions, conception, implementation, deep analysis, perspectives, and towards performance shifts. Expert Syst. Appl. 177, 114864 (2021)
Hashim, F.A., Hussien, A.G.: Snake optimizer: a novel meta-heuristic optimization algorithm. Knowl. Based Syst. 242, 108320 (2022)
Hashim, F.A., Mostafa, R.R., Hussien, A.G., Mirjalili, S., Sallam, K.M.: Fick’s law algorithm: a physical law-based algorithm for numerical optimization. Knowl. Based Syst. 260, 110146 (2023)
Spall, J.C.: Introduction to Stochastic Search and Optimization: Estimation, Simulation, and Control. Wiley, New York (2005)
Hoos, H.H.: Stochastic Local Search: Foundations and Applications. Elsevier, Amsterdam (2004)
Prencipe, L.P., Marinelli, M.: A novel mathematical formulation for solving the dynamic and discrete berth allocation problem by using the bee colony optimisation algorithm. Appl. Intell. 51, 4127–4142 (2021)
Alweshah, M.: Solving feature selection problems by combining mutation and crossover operations with the monarch butterfly optimization algorithm. Appl. Intell. 51(6), 4058–4081 (2021)
Goodarzian, F., Kumar, V., Ghasemi, P.: A set of efficient heuristics and meta-heuristics to solve a multi-objective pharmaceutical supply chain network. Comput. Ind. Eng. 158, 107389 (2021)
Coello, C.A.C.: Theoretical and numerical constraint-handling techniques used with evolutionary algorithms: a survey of the state of the art. Comput. Methods Appl. Mech. Eng. 191(11–12), 1245–1287 (2002)
Marler, R.T., Arora, J.S.: Survey of multi-objective optimization methods for engineering. Struct. Multidiscip. Optim. 26(6), 369–395 (2004)
Ahmadianfar, I., Bozorg-Haddad, O., Chu, X.: Gradient-based optimizer: a new metaheuristic optimization algorithm. Inf. Sci. 540, 131–159 (2020)
Mahdavi, S., Rahnamayan, S., Deb, K.: Opposition based learning: a literature review. Swarm Evol. Comput. 39, 1–23 (2018)
Houssein, E.H., Saad, M.R., Hashim, F.A., Shaban, H.: Lévy flight distribution: a new metaheuristic algorithm for solving engineering optimization problems. Eng. Appl. Artif. Intell. 94, 103731 (2020)
Ypma, T.J.: Historical development of the Newton–Raphson method. SIAM Rev. 37(4), 531–551 (1995)
Zhou, Z., Li, F., Zhu, H., Xie, H., Abawajy, J.H., Chowdhury, M.U.: An improved genetic algorithm using greedy strategy toward task scheduling optimization in cloud environments. Neural Comput. Appl. 32(6), 1531–1541 (2020)
Nassef, A.M., Houssein, E.H., Helmy, B.E., Rezk, H.: Modified honey badger algorithm based global MPPT for triple-junction solar photovoltaic system under partial shading condition and global optimization. Energy 254, 124363 (2022)
Houssein, E.H., Neggaz, N., Hosney, M.E., Mohamed, W.M., Hassaballah, M.: Enhanced Harris Hawks optimization with genetic operators for selection chemical descriptors and compounds activities. Neural Comput. Appl. 33(20), 13601–13618 (2021)
Zhao, S., Zhang, T., Ma, S., Wang, M.: Sea-horse optimizer: a novel nature-inspired meta-heuristic for global optimization problems. Appl. Intell 53, 11833–11860 (2022)
Aarts, E., Aarts, E.H.L., Lenstra, J.K.: Local Search in Combinatorial Optimization. Princeton University Press, Princeton (2003)
Bergey, P.K., Ragsdale, C.: Modified differential evolution: a greedy random strategy for genetic recombination. Omega 33(3), 255–265 (2005)
Rojas-Morales, N., Rojas, M.-C.R., Ureta, E.M.: A survey and classification of opposition-based metaheuristics. Comput. Ind. Eng. 110, 424–435 (2017)
Tizhoosh, H.R.: Opposition-based learning: a new scheme for machine intelligence. In: International conference on computational intelligence for modelling, control and automation and international conference on intelligent agents, web technologies and internet commerce (CIMCA-IAWTIC’06), vol. 1, pp. 695–701. IEEE (2005)
Hongpei, X., Erdbrink, C.D., Krzhizhanovskaya, V.V.: How to speed up optimization? Opposite-center learning and its application to differential evolution. Procedia Comput. Sci. 51, 805–814 (2015)
Li, J., Chen, T., Zhang, T., Li, Y.X.: A cuckoo optimization algorithm using elite opposition-based learning and chaotic disturbance. J. Softw. Eng. 10(1), 16–28 (2016)
Zhao, F., Zhang, J., Wang, J., Zhang, C.: A shuffled complex evolution algorithm with opposition-based learning for a permutation flow shop scheduling problem. Int. J. Comput. Integr. Manuf. 28(11), 1220–1235 (2015)
Shang, J., Sun, Y., Li, S., Liu, J.-X., Zheng, C.-H., Zhang, J.: An improved opposition-based learning particle swarm optimization for the detection of SNP–SNP interactions. BioMed Res. Int. (2015). https://doi.org/10.1155/2015/524821
Gong, C.: Opposition-based adaptive fireworks algorithm. Algorithms 9(3), 43 (2016)
Ahandani, M.A., Alavi-Rad, H.: Opposition-based learning in shuffled frog leaping: an application for parameter identification. Inf. Sci. 291, 19–42 (2015)
Chakraborty, F., Roy, P.K., Nandi, D.: Oppositional elephant herding optimization with dynamic Cauchy mutation for multilevel image thresholding. Evol. Intel. 12, 445–467 (2019)
Sarkhel, R., Das, N., Saha, A.K., Nasipuri, M.: An improved harmony search algorithm embedded with a novel piecewise opposition based learning algorithm. Eng. Appl. Artif. Intell. 67, 317–330 (2018)
Dinkar, S.K., Deep, K., Mirjalili, S., Thapliyal, S.: Opposition-based Laplacian equilibrium optimizer with application in image segmentation using multilevel thresholding. Expert Syst. Appl. 174, 114766 (2021)
Wolpert, D.H., Macready, W.G.: No free lunch theorems for optimization. IEEE Trans. Evol. Comput. 1(1), 67–82 (1997)
Storn, R., Price, K.: Differential evolution—A simple and efficient heuristic for global optimization over continuous spaces. J. Global Optim. 11(4), 341–359 (1997)
Ewees, A.A., Abd Elaziz, M., Houssein, E.H.: Improved grasshopper optimization algorithm using opposition-based learning. Expert Syst. Appl. 112, 156–172 (2018)
Ibrahim, R.A., Oliva, D., Ewees, A.A., Lu, S.: Feature selection based on improved runner-root algorithm using chaotic singer map and opposition-based learning. In: Neural Information Processing: 24th International Conference, ICONIP 2017, Guangzhou, China, November 14–18, 2017, Proceedings, Part V 24, pp. 156–166. Springer, Berlin (2017)
Zhao, J., Lv, L., Sun, H.: Artificial bee colony using opposition-based learning. In: Genetic and Evolutionary Computing: Proceeding of the Eighth International Conference on Genetic and Evolutionary Computing, October 18–20, 2014, Nanchang, China, pp. 3–10. Springer, Berlin (2015)
Gao, X.Z., Wang, X., Ovaska, S.J., Zenger, K.: A hybrid optimization method of harmony search and opposition-based learning. Eng. Optim. 44(8), 895–914 (2012)
Thangaraj, R., Pant, M., Chelliah, T.R., Abraham, A.: Opposition based chaotic differential evolution algorithm for solving global optimization problems. In: 2012 Fourth World Congress on Nature and Biologically Inspired Computing (NaBIC), pp. 1–7. IEEE (2012)
Gang, H., Zheng, Y., Abualigah, L., Hussien, A.G.: Detdo: an adaptive hybrid dandelion optimizer for engineering optimization. Adv. Eng. Inform. 57, 102004 (2023)
Hashim, F.A., Khurma, R.A., Albashish, D., Amin, M., Hussien, A.G.: Novel hybrid of AOA–BSA with double adaptive and random spare for global optimization and engineering problems. Alex. Eng. J. 73, 543–577 (2023)
Sasmal, B., Hussien, A.G., Das, A., Dhal, K.G.: A comprehensive survey on aquila optimizer. Arch. Comput. Method. Eng. 30, 4449–4476 (2023)
Hussien, A.G., Khurma, R.A., Alzaqebah, A., Amin, M., Hashim, F.A.: Novel memetic of beluga whale optimization with self-adaptive exploration–exploitation balance for global optimization and engineering problems. Soft Comput. 27, 13951–13989 (2023)
Gang, H., Wang, J., Li, M., Hussien, A.G., Abbas, M.: EJS: multi-strategy enhanced jellyfish search algorithm for engineering applications. Mathematics 11(4), 851 (2023)
Zheng, R., Hussien, A.G., Qaddoura, R., Jia, H., Abualigah, L., Wang, S., Saber, A.: A multi-strategy enhanced African vultures optimization algorithm for global optimization problems. J. Comput. Design Eng. 10(1), 329–356 (2023)
Al-Shourbaji, I., Kachare, P., Fadlelseed, S., Jabbari, A., Hussien, A.G., Al-Saqqar, F., Abualigah, L., Alameen, A.: Artificial ecosystem-based optimization with dwarf mongoose optimization for feature selection and global optimization problems. Int. J. Comput. Intell. Syst. 16(1), 1–24 (2023)
Izci, D., Ekinci, S., Hussien, A.G.: Effective PID controller design using a novel hybrid algorithm for high order systems. PLoS ONE 18(5), e0286060 (2023)
Shehadeh, H.A., Ahmedy, I., Idris, M.Y.I.: Sperm swarm optimization algorithm for optimizing wireless sensor network challenges. In: Proceedings of the 6th International Conference on Communications and Broadband Networking, pp. 53–59 (2018)
Shehadeh, H.A.: A hybrid sperm swarm optimization and gravitational search algorithm (HSSOGSA) for global optimization. Neural Comput. Appl. 33(18), 11739–11752 (2021)
Shehadeh, H.A.: Chernobyl disaster optimizer (CDO): a novel meta-heuristic method for global optimization. Neural Comput. Appl. 35(15), 10733–10749 (2023)
Zamani, H., Nadimi-Shahraki, M.H.: An evolutionary crow search algorithm equipped with interactive memory mechanism to optimize artificial neural network for disease diagnosis. Biomed. Signal Process. Control 90, 105879 (2024)
Fatahi, A., Nadimi-Shahraki, M.H., Zamani, H.: An improved binary quantum-based avian navigation optimizer algorithm to select effective feature subset from medical data: a Covid-19 case study. J. Bionic Eng. (2023). https://doi.org/10.1007/s42235-023-00433-y
Nadimi-Shahraki, M.H., Varzaneh, Z.A., Zamani, H., Mirjalili, S.: Binary starling murmuration optimizer algorithm to select effective features from medical data. Appl. Sci. 13(1), 564 (2022)
Zamani, H., Nadimi-Shahraki, M.H., Gandomi, A.H.: Qana: quantum-based avian navigation optimizer algorithm. Eng. Appl. Artif. Intell. 104, 104314 (2021)
Zamani, H., Nadimi-Shahraki, M.H., Gandomi, A.H.: Starling murmuration optimizer: a novel bio-inspired algorithm for global and engineering optimization. Comput. Methods Appl. Mech. Eng. 392, 114616 (2022)
Subramanian, P., Sahayaraj, J.M., Senthilkumar, S., Alex, D.S.: A hybrid grey wolf and crow search optimization algorithm-based optimal cluster head selection scheme for wireless sensor networks. Wireless Pers. Commun. 113(2), 905–925 (2020)
Daniel, J., Francis, S.F.V., Velliangiri, S.: Cluster head selection in wireless sensor network using tunicate swarm butterfly optimization algorithm. Wireless Netw. 27(8), 5245–5262 (2021)
Zhou, Y., Wang, N., Xiang, W.: Clustering hierarchy protocol in wireless sensor networks using an improved PSO algorithm. IEEE Access 5, 2241–2253 (2016)
Tabibi, S., Ghaffari, A.: Energy-efficient routing mechanism for mobile sink in wireless sensor networks using particle swarm optimization algorithm. Wireless Pers. Commun. 104(1), 199–216 (2019)
Jadhav, A.R., Shankar, T.: Whale optimization based energy-efficient cluster head selection algorithm for wireless sensor networks. arXiv preprint arXiv:1711.09389 (2017)
Mantegna, R.N.: Fast, accurate algorithm for numerical simulation of levy stable stochastic processes. Phys. Rev. E 49(5), 4677 (1994)
Einstein, A.: Investigations on the Theory of the Brownian Movement. Courier Corporation, North Chelmsford (1956)
Tubishat, M., Idris, N., Shuib, L., Abushariah, M.A.M., Mirjalili, S.: Improved SALP swarm algorithm based on opposition based learning and novel local search algorithm for feature selection. Expert Syst. Appl. 145, 113122 (2020)
Abd Elaziz, M., Oliva, D., Xiong, S.: An improved opposition-based sine cosine algorithm for global optimization. Expert Syst. Appl. 90, 484–500 (2017)
Arcuri, A., Fraser, G.: Parameter tuning or default values? An empirical investigation in search-based software engineering. Empir. Softw. Eng. 18(3), 594–623 (2013)
Mohamed, A.W., Hadi, A.A., Mohamed, A.K., Awad, N.H.: Evaluating the performance of adaptive gaining sharing knowledge based algorithm on CEC 2020 benchmark problems. In: 2020 IEEE Congress on Evolutionary Computation (CEC), pp. 1–8. IEEE (2020)
Das, S., Suganthan, P.N.: Differential evolution: a survey of the state-of-the-art. IEEE Trans. Evol. Comput. 15(1), 4–31 (2010)
Mirjalili, S., Mirjalili, S.M., Lewis, A.: Grey wolf optimizer. Adv. Eng. Softw. 69, 46–61 (2014)
Mirjalili, S.: Moth-flame optimization algorithm: a novel nature-inspired heuristic paradigm. Knowl. Based Syst. 89, 228–249 (2015)
Mirjalili, S.: SCA: a sine cosine algorithm for solving optimization problems. Knowl. Based Syst. 96, 120–133 (2016)
Abdullah, J.M., Ahmed, T.: Fitness dependent optimizer: inspired by the bee swarming reproductive process. IEEE Access 7, 43473–43486 (2019)
Heidari, A.A., Mirjalili, S., Faris, H., Aljarah, I., Mafarja, M., Chen, H.: Harris hawks optimization: algorithm and applications. Future Gener. Comput. Syst. 97, 849–872 (2019)
Khishe, M., Mosavi, M.R.: Chimp optimization algorithm. Expert Syst. Appl. 149, 113338 (2020)
Mohammed, H., Rashid, T.: Fox: a fox-inspired optimization algorithm. Appl. Intell. 53(1), 1030–1050 (2023)
Coello, C.A.C.: Use of a self-adaptive penalty approach for engineering optimization problems. Comput. Ind. 41(2), 113–127 (2000)
Dhiman, G., Kumar, V.: Spotted hyena optimizer: a novel bio-inspired based metaheuristic technique for engineering applications. Adv. Eng. Softw. 114, 48–70 (2017)
Kannan, B.K., Kramer, S.N.: An augmented lagrange multiplier based method for mixed integer discrete continuous optimization and its applications to mechanical design. J. Mech. Des. 116(2), 405–411 (1994)
Mainetti, L., Patrono, L., Vilei, A.: Evolution of wireless sensor networks towards the internet of things: a survey. In: SoftCOM 2011, 19th International Conference on Software, Telecommunications and Computer Networks, pp. 1–6. IEEE (2011)
Mundada, M.R., Kiran, S., Khobanna, S., Varsha, R.N., George, S.A.: A study on energy efficient routing protocols in wireless sensor networks. Int. J. Distrib. Parallel Syst. (IJDPS) 3, 311–330 (2012)
Sadouq, Z.A., El Mabrouk, M., Essaaidi, M.: Conserving energy in WSN through clustering and power control. In: 2014 Third IEEE International Colloquium in Information Science and Technology (CIST), pp. 402–409. IEEE (2014)
Abdul Latiff, N.M., Tsimenidis, C.C., Sharif, B.S.: Energy-aware clustering for wireless sensor networks using particle swarm optimization. In: 2007 IEEE 18th International Symposium on Personal, Indoor and Mobile Radio Communications, pp. 1–5. IEEE (2007)
Heinzelman, W.R., Chandrakasan, A., Balakrishnan, H.: Energy-efficient communication protocol for wireless microsensor networks. In: Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, pp. 10–pp. IEEE (2000)
Al-Aboody, N.A., Al-Raweshidy, H.S.: Grey wolf optimization-based energy-efficient routing protocol for heterogeneous wireless sensor networks. In: 2016 4th International Symposium on Computational and Business Intelligence (ISCBI), pp. 101–107. IEEE (2016)
Funding
Open access funding provided by The Science, Technology & Innovation Funding Authority (STDF) in cooperation with The Egyptian Knowledge Bank (EKB). The authors have not disclosed any funding.
Author information
Authors and Affiliations
Contributions
EHH: supervision, software, methodology, conceptualization, formal analysis, investigation, visualization, data curation, writing—review and editing. MRS: software, resources, writing—original draft. EÇ: methodology, conceptualization, formal analysis, investigation, data curation, writing—review and editing. GH: formal analysis, investigation, data curation, writing—review and editing. AAA: supervision. HH: methodology, conceptualization, formal analysis, investigation, data curation, writing—review and editing. All authors read and approved the final paper.
Corresponding author
Ethics declarations
Conflicts of interest
The authors declare that there is no conflict of interest.
Human and animal rights
This article does not contain studies with human participants or animals carried out by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Houssein, E.H., Saad, M.R., Çelik, E. et al. An enhanced sea-horse optimizer for solving global problems and cluster head selection in wireless sensor networks. Cluster Comput (2024). https://doi.org/10.1007/s10586-024-04368-9
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10586-024-04368-9