Abstract
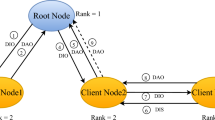
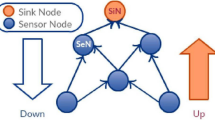
The Low Power and Lossy Networks (LLNs) in the Internet of Things environment comprising constrained embedded devices have particular routing requirements that are well satisfied by the IPv6 Routing Protocol for Low Power and Lossy Networks (RPL). However, RPL is susceptible to several routing attacks. Worst Parent Attack (WPA) is an attack against RPL in which a malicious node intentionally chooses a sub-optimal path to the root node to forward its data packets. The result of which is sub-optimized performance and improper utilization of network resources of the IoT-LLNs. This paper proposes an efficient enhancement of the existing RPL protocol to make it resilient to the Worst Parent Attack. The proposed Enhanced RPL builds upon RPL and is henceforth named ERPL. The proposed ERPL achieves its objective by reducing the candidate set of parent nodes to an optimal parent set in the topological construction process. Thus, ERPL ensures that nodes choose a parent from a set of optimal nodes and makes IoT-LLNs resilient to WPA. We compare ERPL and RPL under normal and WPA scenarios. The comparison proves that ERPL, apart from providing security against the Worst Parent Attacks, also outperforms RPL in terms of energy consumption, packet delivery ratio, network convergence, and overall network overhead.









Similar content being viewed by others
Data availability
The data used in this research work is generated from the Cooja simulator available in Contiki Operating System, which is open source and publicly available. The method used for data generation is explained in the papers.
Change history
23 August 2022
A Correction to this paper has been published: https://doi.org/10.1007/s10586-022-03721-0
References
Dohler, M., Barthel, D., Watteyne, T., Winter, T.: Routing requirements for urban low-power and lossy networks. In: RFC 5548 2009 May
Heidari, A., Jabraeil Jamali, M.A., Jafari Navimipour, N., Akbarpour, S.: Internet of things offloading: ongoing issues, opportunities, and future challenges. Int. J. Commun. Syst. 33(14), e4474 (2020)
Sadrishojaei, M., Navimipour, N.J., Reshadi, M., Hosseinzadeh, M.: A new preventive routing method based on clustering and location prediction in the mobile internet of things. IEEE Internet Things J. 8, 10652–10664 (2021)
Sefati, S.S., Navimipour, N.J.: A QoS-aware service composition mechanism in the Internet of things using a hidden Markov model-based optimization algorithm. IEEE Internet Things J. 8, 15620 (2021)
Winter, T., Thubert, P., Brandt, A., Hui, J., Kelsey, R., Pister, K., Struik, R., Vasseur, J.P., Alexander, R.: RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks, In RFC 6550, March (2012)
Kim, H.-S., Ko, J., Culler, D.E., Paek, J.: Challenging the IPv6 routing protocol for low-power and lossy networks (RPL): a survey. IEEE Commun. Surv. Tutor. 19(4), 2502–25 (2017)
Almusaylim, Z.A., Alhumam, A., Jhanjhi, N.Z.: Proposing a secure RPL based internet of things routing protocol: a review. Elsevier Ad Hoc Netw. 101, 102096 (2020)
Mayzaud, A., Badonnel, R., Chrisment, I.: A taxonomy of attacks in RPL-based internet of things. Int. J. Netw. Secur. 18(3), 459–473 (2016)
Neerugatti, V., Reddy, A.R.: Artificial intelligence-based technique for detection of selective forwarding attack in rpl-based internet of things networks. In: Emerging Research in Data Engineering Systems and Computer Communications, pp. 67–77. Springer, Singapore (2019)
Pu, C.: Sybil attack in RPL-based internet of things: analysis and defenses. IEEE Internet Things J. 7(6), 4937–49 (2020)
Agiollo, A., Conti, M., Kaliyar, P., Lin, T., Pajola, L.: DETONAR: detection of routing attacks in RPL-based IoT. IEEE Trans. Netw. Serv. Manag. 18, 1178 (2021)
Ghahramani, M., Javidan, R., Shojafar, M., Taheri, R., Alazab, M., Tafazolli, R.: RSS: an energy-efficient approach for securing IoT service protocols against the DoS attack. IEEE Internet Things J. 8(5), 3619–35 (2020)
Sahay, R., Geethakumari, G., Modugu, K.: Attack graph—based vulnerability assessment of rank property in RPL-6LOWPAN in IoT, IEEE 4th World Forum on Internet of Things (WF-IoT), pp. 308–313, 5–8 February (2018)
Kamble, A., Malemath, V.S., Patil, D.: Security attacks and secure routing protocols in RPL-based Internet of Things: Survey. In: IEEE 2017 International Conference on Emerging Trends & Innovation in ICT (ICEI), pp. 33–39, 3 February (2017)
Kharrufa, H., Al-Kashoash, H.A., Kemp, A.H.: RPL-based routing protocols in IoT applications: a review. IEEE Sens. J. 19(15), 5952–67 (2019)
Kritsis, K., Papadopoulos, G.Z., Gallais, A., Chatzimisios, P., Theoleyre, F.: A tutorial on performance evaluation and validation methodology for low-power and lossy networks. IEEE Commun. Surv. Tutor. 20(3), 1799–825 (2018)
Ghaleb, B., Al-Dubai, A.Y., Ekonomou, E., Alsarhan, A., Nasser, Y., Mackenzie, L.M., Boukerche, A.: A survey of limitations and enhancements of the ipv6 routing protocol for low-power and lossy networks: a focus on core operations. IEEE Commun. Surv. Tutor. 21(2), 1607–35 (2018)
Kamgueu, P.O., Nataf, E., Ndie, T.D.: Survey on RPL enhancements: a focus on topology, security and mobility. Elsevier Comput. Commun. 120, 10–21 (2018)
Le, A., Loo, J., Lasebae, A., Vinel, A., Chen, Y., Chai, M.: The impact of rank attack on network topology of routing protocol for low-power and lossy networks. IEEE Sens. J. 13(10), 3685–92 (2013)
Raoof, A., Matrawy, A., Lung, C.-H.: Routing attacks and mitigation methods for RPL-based internet of things. IEEE Commun. Surv. Tutor. 21(2), 1582–1606 (2018)
Levis, P., Clausen, T., Hui, J., Gnawali, O., Ko, J.: The Trickle Algorithm. In: RFC 6206, March (2011)
Rai, KK., Asawa, K.: Impact analysis of rank attack with spoofed IP on routing in 6LoWPAN network, In IEEE 2017 10th International Conference on Contemporary Computing (IC3), pp. 1–5, 10 Aug (2017)
Semedo, F., Moradpoor, N., Rafiq, M.: Vulnerability assessment of objective function of RPL protocol for Internet of Things. In: Proceedings of the ACM 11th International Conference on Security of Information and Networks, pp. 1–6, Sep (2018)
Sahay, R., Geethakumari, G., Modugu, K., Mitra, B.: Detection of misappropriation attacks in RPL-6LOWPAN in IoT using neural networks. In: IEEE 2018 Symposium Series in Computational Intelligence, pp. 1715–1722, 18–21 Nov (2018)
Seth, AD., Biswas, S., Dhar, AK.: Detection and verification of decreased rank attack using round-trip times in RPL-based 6LoWPAN networks. In: IEEE 2020 International Conference on Advanced Networks and Telecommunications Systems (ANTS), pp. 1–6, 14 Dec (2020)
Said, A.M, Yahyaoui, A., Yaakoubi, F., Abdellatif, T.: Machine learning based rank attack detection for smart hospital infrastructure. In: Springer 2020 International Conference on Smart Homes and Health Telematics, pp. 28–40, 24 June (2020)
Airehrour, D., Gutierrez, J.A., Ray, S.K.: SecTrust-RPL: a secure trust-aware RPL routing protocol for Internet of Things. Elsevier Future Gen. Comput. Syst. 93, 860–76 (2019)
Zaminkar, M., Fotohi, R.: SoS-RPL: securing internet of things against sinkhole attack using RPL protocol-based node rating and ranking mechanism. Springer Wirel. Personal Commun. 114, 1287–312 (2020)
Prathapchandran, K., Janani, T.: A trust aware security mechanism to detect sinkhole attack in RPL-based IoT environment using random forest-RFTRUST. Elsevier Comput. Netw. 198, 108413 (2021)
Glissa, G., Rachedi, A., Meddeb, A.: A secure routing protocol based on RPL for Internet of Things. In: IEEE 2016 Global Communications Conference (GLOBECOM), pp. 1–7, 4 Dec (2016)
Dvir, A., Buttyan, L.: VeRA-version number and rank authentication in rpl, IEEE 8th International Conference on Mobile Adhoc and Sensor Systems (MASS), pp. 709–714, 17 Oct (2011)
Perrey, H., Landsmann, M., Ugus, O.man, Schmidt, T.C., Wählisch, M.: TRAIL: topology authentication in RPL. arXiv preprint arXiv:1312.0984 (2013)
Raoof, A., Lung, CH., Matrawy, A.: Introducing network coding to RPL: the chained secure mode (CSM). In; IEEE 2020 19th International Symposium on Network Computing and Applications (NCA), pp. 1–4, 24 Nov (2020)
Karmakar, S., Sengupta, J., Bit, S.D.: LEADER: low overhead rank attack detection for securing RPL based IoT. In: IEEE International Conference on COMmunication Systems & NETworkS (COMSNETS), pp. 429–437, Jan (2021)
Sahay, R., Geethakumari, G., Mitra, B.: A feedforward neural network based model to predict sub-optimal path attack in IoT-LLNs. In: IEEE 2020 20th IEEE/ACM International Symposium on Cluster, Cloud and Internet Computing (CCGRID), pp.400–409, 11 May (2020)
Canbalaban, E., Sen, S.: A cross-layer intrusion detection system for RPL-based internet of things. In: Proceeding of the Springer International Conference on Ad-Hoc Networks and Wireless, pp. 214–227, 19 Oct (2020)
Djedjig, N., Tandjaoui, D., Medjek, F., Romdhani, I.: Trust-aware and cooperative routing protocol for IoT security. Elsevier J. Inf. Secur. Appl. 52, 102467 (2020)
Preeth, S.S., Dhanalakshmi, R., Kumar, R., Si, S.: Efficient parent selection for RPL using ACO and coverage based dynamic trickle techniques. J. Ambient Intell. Hum. Comput. 31, 1–5 (2019)
Royaee, Z., Mirvaziri, H., Bardsiri, A.K.: Designing a context-aware model for RPL load balancing of low power and lossy networks in the internet of things. Springer J. Ambient Intell. Hum. Comput. 12(2), 2449–68 (2021)
Le, A., Loo, J., Chai, K.K., Aiash, M.: A specification-based IDS for detecting attacks on RPL-based network topology. Information 7(2), 25 (2016)
Simoglou, G., Violettas, G., Petridou, S., Mamatas, L.: Intrusion detection systems for RPL security: a comparative analysis. Elsevier Comput. Secur. 104, 102219 (2021)
Lamaazi, H., Benamar, N.: A comprehensive survey on enhancements and limitations of the RPL protocol: a focus on the objective function. Elsevier Ad Hoc Netw. 96, 102001 (2020)
Zikria, Y.B., Afzal, M.K., Ishmanov, F., Kim, S.W., Yu, H.: A survey on routing protocols supported by the Contiki Internet of things operating system. Elsevier Future Gen. Comput. Syst. 82, 200–19 (2018)
Clark, B.N., Colbourn, C.J., Johnson, D.S., Unit disk graphs: Unit disk graph. Discret. Math. 86, 165–177 (1990)
Tsvetkov, T., Klein, A.: RPL: IPv6 routing protocol for low power and lossy networks. Network 59, 59–66 (2011)
Author information
Authors and Affiliations
Contributions
RS conceptualized, developed, and executed the idea. GG verified the idea. RS wrote the manuscript. The manuscript was reviewed, edited, and finalized by GG, RS and BM.
Corresponding author
Ethics declarations
Funding
This research is not funded.
Conflict of interest
The authors declare no conflict of Interest.
Code availability
Code will be made available on request.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
The original online version of this article was revised: The authors G. Geethakumari and Barsha Mitra affiliation has been corrected.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Sahay, R., Geethakumari, G. & Mitra, B. Mitigating the worst parent attack in RPL based internet of things. Cluster Comput 25, 1303–1320 (2022). https://doi.org/10.1007/s10586-021-03528-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-021-03528-5