Abstract
Blockchain Technology (BT) has the potential to revolutionize supply chain management by providing transparency, but it also poses significant environmental and security challenges. BT consumes energy and emits carbon gases, affecting its adoption in Supply Chains (SCs). The substantial energy demand of blockchain networks contributes to carbon emissions and sustainability risks. Moreover, for secure and reliable transactions, mutual authentication needs to be established to address security concerns raised by SC managers. This paper proposes a tri-objective optimization model for the simultaneous design of the SC-BT network, considering a two-step authentication process. The model considers transparency caused by BT members, emissions of BT, and costs related to BT and SC design. It also takes into account uncertainty conditions for participating BT members in the SC and the range of transparency, cost, and emission targets. To solve the model, a Branch and Efficiency (B&E) algorithm equipped with BT-related criteria is developed. The algorithm is implemented in a three-level SC and produces cost-effective and environmentally friendly outcomes. However, the adoption of BT in the SC can be costly and harmful to the environment under uncertain conditions. It is worth mentioning that implementing the proposed algorithm from our article in a three-level SC case study can result in a significant cost reduction of over 16% and an emission reduction of over 13%. The iterative nature of this algorithm plays a vital role in achieving these positive outcomes.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
The concept of Supply Chain (SC) refers to a group of entities involved in upstream and downstream flows from the source to the customer, encompassing finance, information, product, and service (Talaeizadeh et al., 2023). Supply Chain Management (SCM) involves the integration of businesses to coordinate planning activities and integrate information systems (Gharaei et al., 2023a; Larson & Rogers, 1998). Supply Chain Network Design (SCND) is a critical planning problem in SCM that aims to find the optimal configuration based on one or more criteria, considering the activities of SC elements such as suppliers, manufacturers, distributors, etc. (Gharaei et al., 2023b; Govindan et al., 2017). SC encounters significant issues related to traceability, access to information, security, and privacy. One emerging technology that has shown promise in addressing these problems is Blockchain Technology (BT) (Xu et al., 2021).
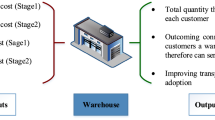
Blockchain is a public digital ledger consisting of blocks containing transactions confirmed by a mathematical algorithm. Miners calculate this algorithm, producing a unique hash value for each block. Each block contains encrypted data in the form of a hash value. Notably, each block contains its own hash value and the previous block's hash value. Therefore, any change or data manipulation of blocks requires changing not only that block's hash value but also the hash values of other blocks. As the number of blocks increases, the uploaded information increases, reducing the chances of data manipulation by attackers and increasing blockchain transparency (Maity et al., 2021). Figure 1 illustrates how physical flow actions recorded immutably in blockchain network through digital technologies such as quick response codes, radio-frequency identification, and digital signatures can improve SC efficiency and reliability. Blockchain adoption in SC mitigates risks such as lack of transparency in exchanges between buyers and sellers, complex settlement processes, and intermediaries' presence (Kamilaris et al., 2019).
Digital and blockchain counterparts of the SC (Kamilaris et al., 2019)
A survey of SC leaders in 2019 demonstrated the importance of adopting BT in SC. 40% of SC leaders planned to invest in BT, and 46% planned to invest in the Internet of Things (IoT) (Placek, 2019). BT is an agreed solution among companies to track shipments during the COVID-19 pandemic, retrieve and manage data, and prevent fraud in SC-related activities (Khan et al., 2022). Until BT adoption in SC, SC members cannot hold their suppliers accountable for the quality of their products, particularly in the food industry where suppliers who provide contaminated goods should not be supported (Niu et al., 2021). The adoption of BT in the SC can improve the transparency and sustainability of SC as security and traceability, the technical characteristics of BT, can play an important role as an enabler for such improvement (Bai et al., 2022). BT is reliable and decentralized, making it ideal for diverse business transactions. It is particularly useful for SCM due to its secure data handling, increased visibility, product traceability, digitalization, and disintermediation. However, proper design methodologies are necessary for successful adoption since BT is still in its early stages (Gölcük, 2022).
Currently, the utilization of BT in SC, logistics, and operations management is experiencing a significant surge. However, there are two major challenges that researchers have generally overlooked while focusing more on the strengths of BT applications. The application of BT can create risks regarding sustainability and security. Specifically, BT consumes energy and produces carbon gas in a non-negligible way, especially when miners calculate mathematical algorithms. This contradicts global sustainable efforts and agreements such as the Paris Agreement regarding climate change (Jiang et al., 2021). To address these concerns, BT must establish a structure for mutual authentication to ensure the security and reliability of transactions. This will prevent not only the disclosure of transaction details to third parties but also the manipulation of messages during transmission between the sender and receiver. A two-step authentication process is used to establish mutual communication between the transaction parties. As illustrated in Fig. 2, both the digital signature of the sender (merchant) and the digital signature of the receiver (customer) are validated by the blockchain system. Digital signatures prove that the message has been approved by the owner of the address. During the two-step authentication process, the sender sends both the message and the message authentication code (encrypted message) to the receiver. The receiver investigates the manipulation of the received message by comparing the sender's message and the decrypted message. Messages can contain information such as address, amount, and time (Kim & Kim, 2022). Since BT validates both digital signatures based on two-step authentication, it ensures not only integrity (no data tampering during transmission) but also non-repudiation of completed transactions (by sender or receiver).
Two-step authentication (Kim & Kim, 2022)
BT can significantly enhance SC authentication and validation processes (Di Vaio & Varriale, 2020). While it offers advancements, traditional quality audits remain essential at each stage to establish comprehensive transactional records. This technology enables faster transactions and ensures more reliable records, providing transparency, authenticity, visibility, trust, and security for all SC participants. Real-time tracking allows precise product location and delivery estimates, facilitating seamless data sharing among SC entities. The two-step authentication design employs cryptographic techniques to establish multiple layers of defense for communicating nodes (Komninos et al., 2007). This design is devised to mitigate potential malicious attacks effectively. The efficacy of this procedure is assessed, leading to the identification of the most promising protocols tailored for such security-sensitive environments. Nodes within the blockchain network can also function as members of the SC. Specifically, certain entities participating in the SC are integrated into the blockchain framework with a two-step approach for enhanced security. This concept, which emphasizes bolstering blockchain security, represents a novel area yet to be extensively explored in SC literature. Given the nascent stage of blockchain application within the SC domain, the notion of securing blockchain through a two-step process is groundbreaking and warrants significant attention.
Despite being a hot topic among researchers, there is currently limited research on the adoption of BT in SC management, planning, and design, particularly from an optimization perspective. As mentioned in Goli et al. (2023), direct shipping to customers from distribution centers or manufacturing plants can enhance flexibility in the SC. To enable this, an IoT system is utilized for simultaneous management of direct and indirect deliveries. The IoT application also supports a more efficient and sustainable Supply Chain Network Design (SCND). However, it is important to consider that implementing IoT incurs additional costs for the SC. Prajapati et al. (2022) presented a mixed-integer non-linear programming model that aims to maximize profit by considering total costs in forward logistics, virtual SC costs, total selling prices, and total costs related to reverse logistics, for closed-loop Supply Chain Planning (SCP) in which BT is adopted. Xia et al. (2021) proposed a mixed-integer programming model that aims to minimize battery-related and travel costs in the drone routing problem by introducing transparent fleet sharing based on BT adoption as a solution to increase industry synergy while paying attention to economic and environmental performance. Maity et al. (2021) presented an optimization model for a five-level sausage SC that aims to minimize batch dispersion in a situation where demand is stochastic. They examined the adoption of BT in the SC from the perspective of transparency, and their results showed that as the number of blocks increases, the transparency of BT increases because it becomes more difficult for an attacker to manipulate the data of multiple blocks. De Carvalho et al. (2022) presented a mixed-integer quadratic programming model that adopts BT in the flower SC with the objective of maximizing net profit by recording transport time information using BT. Babaei et al. (2023a) proposed a bi-objective optimization model for simultaneous SC-BT network design that considers maximizing transparency due to BT adoption and minimizing costs, including traditional SC costs and BT deployment costs.
Goli (2023) emphasized the role of BT in the design of the SC due to the ability to increase investment speed and settle accounts of SC members immediately after the product is sold. In this regard, he provided a multi-objective Mixed-Integer Linear Programming (MILP) model based on blockchain network cash flow, change in SC debts, change in net equity, SC profit without considering cash flow, total deposits made to the blockchain network for processing blocks of information, and the total lost revenue of the SC to consider financial flow through BT in closed-loop SCP. The Covid-19 pandemic has highlighted the need to address an omni-channel strategy in SC, and Babaei et al. (2022a) and Babaei et al. (2023b) evaluated distribution network configuration based on cost, service, and transparency criteria resulting from BT adoption through the development of Data Envelopment Analysis (DEA) models. Yadav and Singh (2022) developed an MILP model that minimizes the costs of procurement (purchase, order, transportation, and holding processes) and the cost of BT based on the number of blocks created and authenticated due to concerns about transparency, traceability, and immutable information in procurement problems in the SC. Lastly, Babaei et al. (2023c) presented a bi-objective optimization model based on traffic congestion and SC costs that integrates the problem of production and distribution planning with BT by recording information related to the links between the levels of the SC in the blockchain network.
As discussed in this section, the adoption of BT in SCM is necessary for traceability, transparency, improvement of SC-related activities performances, and product authentication. However, researchers have focused more on the strengths of BT adoption in SCM, while security and environmental issues pose detrimental challenges to its adoption. The literature on SC and BT integration has not adequately addressed these challenges, leading to several research gaps:
-
i.
Inadequate attention to the two-step authentication process to improve security in blockchain-enabled SCM,
-
ii.
Insufficient addressing of the detrimental challenges of adopting BT in SCM, such as carbon emissions,
-
iii.
Lack of an optimization model for the simultaneous design of the blockchain network and SC based on transparency, emission, and security,
-
iv.
Neglecting to examine the impact of uncertainty in BT on carbon emissions,
-
v.
Not considering an efficient algorithm to solve blockchain-enabled SC mathematical models based on cost, service, transparency, and emission criteria.
To fill these research gaps, this paper provides the following contributions to the literature:
-
I.
Use of two-step authentication in BT to allow both members of the SCM involved in the transaction to validate,
-
II.
Consideration of carbon emissions based on the operations of BT in the SCM,
-
III.
Provision of a tri-objective optimization model based on transparency (due to the increase in the number of blocks), emission (due to the computational complexity and members involved in the BT), and cost (traditional SC costs such as installation, production, transportation, etc., and BT deployment cost),
-
IV.
Consideration of uncertainty conditions through stochastic programming on the number of blocks and investigation of its effects on carbon emissions,
-
V.
Development of a novel B&E algorithm based on transparency, cost, service, and emission.
The integration of BT into SCM holds significant promise for enhancing traceability, transparency, and overall performance of SC activities, as well as facilitating product authentication. However, while existing literature has predominantly emphasized the strengths of BT adoption in SCM, critical challenges relating to security and environmental sustainability have been inadequately addressed. Consequently, several notable research gaps have emerged within this domain. There exists a notable lack of emphasis on enhancing security within blockchain-enabled SCM, particularly in the context of implementing a two-step authentication process to bolster transaction security. Such a process is crucial for ensuring that both parties involved in a transaction within the SC can effectively validate the authenticity of the transaction. Insufficient attention has been given to addressing the adverse environmental impacts associated with the adoption of BT in SCM, particularly concerning carbon emissions. As sustainability becomes an increasingly pressing concern, it is imperative to explore strategies for mitigating the carbon footprint associated with blockchain-enabled SC operations. Furthermore, the absence of a comprehensive optimization model that simultaneously considers the design of the blockchain network and SC configuration represents another significant research gap. Such a model should integrate considerations of transparency, emission reduction, and security, thereby enabling more efficient decision-making processes within the SC context. Moreover, the impact of uncertainty inherent in BT on carbon emissions has been largely overlooked in existing literature. Addressing this gap necessitates the development of stochastic programming approaches that can account for uncertainty in factors such as the number of blocks within the blockchain network and its implications for carbon emissions. There is a dearth of efficient algorithms tailored to solving mathematical models that incorporate BT within the SC, accounting for criteria such as cost, service quality, transparency, and emission reduction. Developing such algorithms is essential for optimizing SC operations and ensuring alignment with overarching sustainability objectives.
To address these critical research gaps, this paper contributes to the existing literature in several key ways. It proposes the implementation of a two-step authentication process within BT to enhance transaction security within the SC. It introduces considerations of carbon emissions associated with blockchain-enabled SCM operations. It presents a tri-objective optimization model that integrates transparency, emission reduction, and cost considerations. It explores the implications of uncertainty in BT on carbon emissions through stochastic programming techniques. Lastly, it introduces a novel B&E algorithm that optimizes SC operations based on multiple criteria including transparency, cost, service quality, and emission reduction. Through these contributions, this paper aims to address the identified research gaps and advance the understanding and implementation of BT within SCM.
The rest of this article is organized as follows: In Sect. 2, we present a proposed model for the simultaneous design of the SC and the blockchain network. In Sect. 3, we provide deterministic and linear counterparts of the proposed model. In Sect. 4, we develop the B&E algorithm and solve the multi-objective optimization model through Fuzzy Goal Programming (FGP). In Sect. 5, we numerically analyze the presented model based on the research literature. In Sect. 6, we discuss managerial implications, and finally, in Sect. 7, we mention the conclusion, research limitations, and future research opportunities.
2 Problem statement
The adoption of BT in SCM is necessary for several important reasons, including improving quality, reducing costs, shortening delivery time, reducing risk, and increasing trust (Helo & Hao, 2019). Furthermore, adopting BT in the SC can improve the transparency of the SC (Chod et al., 2020). However, challenges related to security, energy consumption, and carbon emissions may influence the decision to adopt BT in the SC. As the optimization of SC design and operations is of great interest to both academic and industrial fields due to the potential economic benefits and coordination of SC members, it is necessary to consider vital issues related to energy and environment in the optimization and design of the SC (Garcia & You, 2015).
The purpose of this paper is to integrate SCND with BT adoption to enhance blockchain benefits and address blockchain challenges. As illustrated in Fig. 3, our SC network consists of three levels, including plants, warehouses, and customers. The locations of customers and plants are known, while a number of candidate warehouses should be selected based on criteria related to transparency, cost, emissions, and service level. Transportation activities between the levels of the SC incur both fixed and variable costs, depending on the transported quantities. Based on customer demand, plants produce goods and send them to warehouses through the connection links. Then, warehouses transport the goods to customers. However, not all customer demands may be satisfied in this SC.
The links between the SC levels and the production level are capacitated. Therefore, our proposed SC involves making decisions related to installation, allocation, production, and transportation. We enhance the traditional SC depicted in Fig. 3 by adopting BT. As stated by Maity et al. (2021), with the increase in the number of blocks, the blockchain network (the encrypted and digital counterpart of the traditional SC) becomes more transparent. When the number of blocks increases, attackers find it harder to manipulate the data because not only the data of the attacked block but also the data of its previous blocks must be changed. To put it another way, every block in a blockchain includes its own unique identifier, known as its hash value, as well as the hash value of the preceding block. So, suppose we have a four-block chain and someone tries to manipulate Block 2. This would involve tampering with the recorded hash value in Block 3, and then changing the hash value of Block 3 in Block 4. Therefore, increasing transparency requires increasing the number of blocks. Transparency is considered based on the probability of observing failures until the first success according to the negative binomial distribution and the probability of failure according to Eq. (1). The important point here is who is responsible for generating the block and who the participants in the BT are. As stated in Liu et al. (2021) and Babaei et al. (2023a), SC members can be considered as responsible participants in the BT. In this way, SCND and blockchain network influence each other, so that with the increase of the members responsible for the block generation process, the blockchain network becomes decentralized and transparent. For this reason, our paper seeks to maximize transparency through the application of BT in the SC. The notations of all formulas are reported in Table 1.
Although SCP is strengthened through the adoption of BT from the perspective of transparency, emissions, and security must be included in this planning to manage the undesirable impacts of BT adoption in the SC. As the number of participants increases, the calculation algorithm in BT and the consensus process become more complex and require more energy consumption and emission generation. Therefore, we intend to design the SC network in such a way that the blockchain counterpart tries to minimize the emissions caused by the participants in the blockchain network.
In our study, we delve into enhancing the traditional SC by integrating BT. This integration is rooted in the understanding that BT brings about increased transparency within the SC network. The essence of this lies in the structure of blockchain networks, where the proliferation of blocks strengthens the system's transparency. Each block within the blockchain contains a unique hash value along with the hash value of the preceding block. Consequently, any attempt to tamper with data within a block necessitates altering not only the targeted block but also all preceding blocks, making data manipulation more challenging for potential attackers. Transparency quantification involves assessing the probability of observing failures until the first success, employing methodologies such as the negative binomial distribution and the probability of failure. Furthermore, the responsibility for block generation and the participation of SC members in the blockchain network play pivotal roles in decentralization and transparency enhancement. Our study aims to maximize transparency in the SC by leveraging BT integration. This endeavor is underpinned by the understanding that a higher number of participating SC members in BT bolsters the network's transparency, thereby making data manipulation more challenging for potential attackers.
While the integration of BT enhances transparency within the SC, it is imperative to consider the implications for emissions and security. As the number of participants in the blockchain network increases, the complexity of calculation algorithms and consensus processes escalates, resulting in higher energy consumption and emissions.
The objective functions outlined in our study serve specific purposes:
-
First objective function aims to maximize transparency by increasing the number of SC members participating in BT. A higher value of this objective function implies heightened failure rates for potential attackers.
-
Second objective function focuses on minimizing both traditional SC costs (e.g., production, transportation) and BT-related costs (e.g., deployment of blockchain systems with two-step authentication).
-
Third objective function is dedicated to minimizing emissions resulting from blockchain participant activities.
On the other hand, to improve the security of the BT adopted in the SC, it is necessary to deploy a two-step authentication process in the BT system. So, the member of the SC enabled with BT performs the authentication stage twice. As shown in Fig. 4, when both the sender and receiver are authenticated, the concept of security emerges because only those two have access to the exchanged message and cannot deny it. Therefore, we consider the members of the SC who participate in the blockchain network with a structure containing a two-step authentication process. It is worth mentioning that these participating members can only exist in the block generation process if both authentication steps are verified. According to the mentioned explanations, the traditional SC presented in Fig. 3 becomes transparent through the BT adoption advantage. Meanwhile, the challenges of BT adoption in SC are managed by considering environmental and security concerns. The multi-objective optimization model presented in our paper is given in Formulas (2–30). The relevant notations are provided in Table 1.
Two-step authentication process for blockchain system (Kim & Kim, 2022)
It is worth noting that the primary difference between two-step verification and two-step authentication is the number of parties responsible for confirming the necessary steps to complete a transaction. With two-step verification, a single entity or person is accountable for verifying both steps, while with two-step authentication, two independent entities or participants are required to confirm the transaction's steps. Given the decentralized nature of blockchain, it is more appropriate to use two-step authentication as it offers an added layer of security, involving multiple parties in verifying the transaction's steps.
Now, the model is given as follows:
subject to
As the first objective function, Eq. (2) maximizes transparency through the number of SC members participating in the BT. As the value of this objective function increases, the attacker's failures increase, because the attacker can hardly manipulate the data of all members (by raising the number of participants). Eq. (3), as the second objective function, minimizes traditional SC costs (such as production, transportation, and installation) and BT costs (deployment of a blockchain system with two-step authentication). The third objective function or Eq. (4) minimizes the emissions caused by the joining of participants in the blockchain network. Constraints (5–7) determine the production quantities of goods in plants and the upper and lower limits of production. Constraint (8) balances the flow between plant-warehouse and warehouse-customer. Constraints (9) and (10) indicate the maximum capacities of plant-warehouse and warehouse-customer links. Constraints (11) and (12) show the relationship between installation and assignment variables. The capacity of each warehouse is shown by Constraints (13) and (14). Constraints (15) and (16) show the unmet demand and its maximum allowed. Constraint (17) creates a connection between the physical SC and the BT equipped with a two-step authentication process. Constraints (18) and (19) state that in authentication, both sender and receiver are verified. Constraints (20) and (21) show the participants in the blockchain based on the respective levels of plant-warehouse and warehouse-customer. Constraints (22) and (23) determine the relationship between the physical allocation and the participants in the BT. Constraints (24) and (25) guarantee that participants in the blockchain go through two-step authentication. Constraint (26) shows the minimum two-step authentication processes in the blockchain system. Constraints (27) and (28) deploy the two-step authentication processes in the blockchain system. Constraints (29) and (30) show decision variables.
3 Reformulation
The model presented in Formulas (2–30) is non-linear, as the decision variables related to two-step authentication are multiplied together. Furthermore, the number of participants in the BT is considered non-deterministic in the model. Hence, the presented model is non-deterministic. The linear counterpart of the model is provided in Sect. 3.1, while the deterministic counterpart is given in Sect. 3.2.
Linearization and deterministic reformulation are crucial techniques employed in optimization problems to tackle non-linearities and uncertainties within the problem formulation (i.e., Formulas (2–30)). In the context of a blockchain-based authentication system, where binary variables dictate the validation of sender and receiver, these techniques become instrumental. Linearization primarily addresses the non-linearities arising from the multiplication of binary variables (two-step authentication), which lead to non-linear constraints within the model. To overcome this, a new variable and some constraints are introduced to linearize these expressions. By transforming the product of binary variables into a linear form, the model is rendered linear, facilitating easier computation and optimization. On the other hand, uncertain reformulation deals with uncertainties inherent in certain parameters of the system. Here, chance constraint programming is adopted to account for the uncertainty surrounding the parameter indicating the minimum number of warehouses participating in the blockchain. By employing chance constraint programming, the model evaluates the probability of satisfying the uncertain constraint. This is vital for assessing the reliability and robustness of the system, particularly in scenarios where uncertainty can significantly impact the outcome.
3.1 Linearized counterpart
When the two-step authentication process is complete, the sender and receiver (\({m}_{j}^{s2},{c}_{j}^{s1}\)) are both validated by the blockchain system. These two variables are binary, and the multiplication of these variables causes the non-linearity of Constraints (17), (20–21), and (24–26). Constraints (31–34) are presented to linearize these constraints. Thus, the linear version of the presented model (Formulas (2–30)) is derived from Constraints (31–34), where the product of two binary variables is transformed into a linear form via a common linearization technique (Asghari et al., 2022).
3.2 Deterministic counterpart
Immaturity and non-compliance with standards make organizations uncertain about adopting BT (Herold et al., 2022). Additionally, issues related to the production and transfer of blocks in BT are also associated with uncertainty. Based on this, the SCs that adopt the BT are subject to uncertainty (Babaei et al., 2023a). However, few researchers have provided research on the integration of SC and BT regarding uncertainty conditions. In the realm of SCM, the adoption of BT presents both promise and uncertainty. Factors such as the technology's immaturity and non-standardized practices engender a sense of apprehension among organizations considering its implementation. Moreover, the intricate processes involved in block production and transfer add further layers of uncertainty to the equation. Consequently, enterprises venturing into the integration of SCs and BT find themselves navigating through uncharted territory, fraught with ambiguity and risk. Despite the palpable uncertainty surrounding SC and BT integration, scholarly discourse on how to effectively address uncertainty in this context remains scant. Recognizing this gap, our study employs Chance Constraint Programming as a strategic approach to contend with the uncertainties inherent in the integration process. This method allows us to systematically evaluate the likelihood of meeting uncertain constraints, providing insights crucial for decision-making amidst ambiguity. Central to our modeling approach is the treatment of key parameters, such as the minimum number of warehouses participating in the blockchain (represented by π), as stochastic variables. This decision stems from empirical observations suggesting a probabilistic nature to the involvement of warehouses in blockchain networks (Babaei et al., 2023a, 2023b, 2023c, 2023d, 2023e, 2023f). Building upon this understanding, we assume that the distribution of π follows a normal distribution. Furthermore, such an assumption facilitates the incorporation of uncertainty within the chance constraint programming framework. By embracing stochastic modeling and employing a normal distribution assumption for π, our model captures the inherent uncertainties surrounding SC and BT integration. This holistic approach not only enhances the robustness of our analyses but also provides a nuanced understanding of the implications of uncertainty on SC operations. Thus, our study contributes to bridging the gap in research on uncertainty in SC and BT integration while offering valuable insights for practitioners grappling with the complexities of modern SCM.
In this research, chance constraint programming is used to consider uncertainty conditions for \(\pi \). According to Babaei et al., (2023a, 2023b, 2023c, 2023d, 2023e, 2023f), we assume that this parameter follows a normal distribution. Chance constraint programming examines the probability of a satisfaction level for the uncertain constraint (Cooper et al., 2002; Jiang & Guan, 2016). The higher the level of constraint satisfaction, the higher the consumption of resources (such as cost) in SC and BT integration. The deterministic counterpart of Constraint (26) is shown in Eq. (35). In this equation, \(\widetilde{\pi }\) represents stochastic conditions regarding \(\pi \).
4 Solution methods
The B&E algorithm is used to solve the model presented in Formulas (2–30) in order to measure the solutions based on cost, service level, BT, and emissions criteria. Additionally, our multi-objective optimization model is transformed into a single-objective model through fuzzy goal programming. In SubSect. 4.1, we discuss the developed B&E algorithm, and in SubSect. 4.2, we address the solution method for multi-objective programming.
4.1 Developed B&E Algorithm
DEA is one of the important decision-making tools that connects the category of data analysis with mathematical optimization. The function of a DEA model is to evaluate the peer DMUs through input and output criteria. Outputs are the products obtained from the consumption of resources (inputs) (Cooper et al., 2007). DEA models are widely used in SCP, inventory management and transportation planning (Babaei et al., 2021a, 2021b, 2023d, 2023e; Hahn et al., 2021; Izadikhah et al., 2021; Saen et al., 2022). Grigoroudis et al. (2014) introduced the B&E algorithm to generate efficient and optimal solutions. In an iterative process, this algorithm refines the solutions obtained from the SC optimization model through the DEA model so that the most efficient solutions are used for subsequent iterations in the optimization model. Later, this algorithm, which has a great ability to save SCP in terms of cost, was further developed and refined by other researchers (Babaei et al., 2022b, 2023f; Petridis et al., 2017). In this paper, we use the B&E algorithm to optimize the solutions derived from Formulas (2–30) efficiently. Our B&E algorithm operates according to the DEA model presented in Babaei et al. (2023a) (shown in Formulas (36–42)). Objective function (36) maximizes the efficiency of DMUs, Constraint (36) obtains the efficiency value for each DMU, Constraint (38) sets the weighted sum of the inputs data equal to one, Constraint (39) determines the amount of inefficiency for each DMU, Constraint (40) guarantees that the efficiency value of each DMU is at most equal to one, and Constraints (41) and (42) show the signs of the decision variables.
subject to
The efficiency scores of the SC members are measured by Formulas (36–42) based on the criteria mentioned in Fig. 5. In this research, customers and plants are known, but the establishment of warehouses is a decision under the authority of the optimization model. Evaluation criteria are not limited to the usual cost and service criteria. Evaluation criteria include:
-
I.
Common criteria (such as transportation and installation costs, and service related to the number of customers and shipping quantity),
-
II.
Innovative criteria (based on BT).
Our innovative criteria are not biased towards BT adoption. The innovative criteria consider both the benefits, such as transparency resulting from BT adoption in SC, and the challenges, such as environmental emissions resulting from BT adoption.
To treat the problem, an algorithm illustrated in Fig. 6 is offered which tries to efficiently solve the model described earlier. The Main Problem (MP) involves solving Formulas (1)-(29). The optimal solutions obtained from this process are then evaluated based on the criteria mentioned in Fig. 5, which involves using Formulas (36–42). The evaluation process is carried out via two methods—one that utilizes common criteria coupled with the beneficial BT criterion (transparency), and the other with the challenging criteria of BT (environmental concern). The efficiency scores of these optimal solutions are measured during the evaluation process. According to the decision-maker's preference, solutions deemed efficient by Eq. (43) are included in the MP. In simpler terms, the MP is transformed into the Revised Problem (RP) through efficiency cuts, wherein the optimization model (i.e., Formulas (2–30)) is executed only among the efficient solutions.
The algorithm performs an iterative process to optimize solutions efficiently. The algorithm includes termination conditions that are based on interaction with the decision-maker, and are as follows:
-
I.
If the solution space for the RP is not feasible, the decision-maker can accept the optimal solution from the previous iteration, and the algorithm will terminate. Or, If the solution space is infeasible, the decision-maker can reduce the acceptance level of efficiency to allow for more optimal solutions to be included,
-
II.
If the objective function values do not change within two consecutive iterations, the algorithm will terminate,
-
III.
If the number of optimal solutions obtained is less than the desired threshold set by the decision-maker, the algorithm will terminate,
-
IV.
If the number of iterations has reached the desired amount set by the decision-maker, the algorithm will terminate.
The algorithm engages with the decision maker, and one key aspect of this interaction is evident in the termination condition. It is important to note that while the algorithm is interactive, it doesn't overwhelm the decision maker. Instead, it only requires limited information from them, such as setting certain parameters like the termination condition (e.g., the number of iterations needed to conclude the algorithm) and recognizing the decision-making unit as an efficient entity (with a minimum required efficiency).
One of the main concerns for managers in SCP is the cost factor. Therefore, the cost of adopting BT in the SC increases the intensity of this concern. In other words, a significant obstacle faced by SC managers regarding the adoption of BT in the SC is the cost factor. Through a Proposition and a Corollary, it is demonstrated that the proposed algorithm is capable of cost-effective planning for the integration of the SC and BT. Another concern of SC managers is their social responsibility regarding the environmental effects of adopting BT in the SC. The following explanation illustrates that the proposed algorithm is not only cost-effective but also environmentally friendly.
Proposition
In the proposed algorithm, iteration "\(t+1\)" is more cost-effective than iteration "\(t\)".
Proof
Iteration "\(t+1\)" has an additional constraint compared to iteration "t", which is the efficiency cut. This constraint eliminates inefficient warehouses from the feasible space, leading to the elimination of establishment and allocation decision variables. As a result, the costs associated with the eliminated decision variables are no longer considered in the proposed model. Thus, the solution of iteration "\(t+1\)" becomes more cost-effective than the solution of iteration "\(t\)".
Corollary 1
The proposed algorithm can adopt BT in the SC in a cost-effective manner.
Proof
The proposed algorithm removes inefficient solutions from the feasible region, resulting in a reduction of the total cost of deploying BT in the SC according to the proposition.
Corollary 2
The proposed algorithm can adopt BT in the SC in an environmentally friendly manner.
Proof
According to the proposition, the proposed algorithm prevents inefficient communication between levels of the SC in the blockchain platform and therefore minimizes unnecessary environmental emissions.
It is important to highlight that the developed algorithm effectively narrows down the feasible space with each iteration, resulting in reduced resource consumption and decreased computational complexity and time in subsequent iterations (as per the aforementioned proposition). Moreover, the algorithm ensures consideration of the exact solutions in different instances. Consequently, it possesses the aforementioned dual advantages when compared to other solving algorithms.
4.2 Fuzzy goal programming
One of the most widely used approaches in solving multi-objective planning is goal programming (GP). In GP for objective functions, aspiration levels are set. GP aims to minimize the deviations of the objective functions from the aspiration levels. In this way, the multi-objective model becomes a single-objective model, which is the objective function of the single-objective model related to the minimization of deviations (Charnes & Cooper, 1977). Determining the exact level of aspiration by the decision-maker is difficult. For this purpose, Tiwari et al. (1987) considered aspiration levels in a fuzzy manner. In other words, aspiration levels have upper and lower limits. In this programming, the objective functions become membership functions. Thus, the counterpart of the multi-objective model is the single-objective model whose objective function is to maximize the weighted sum of membership functions. The approach of Tiwari et al. (1987) has been used in various fields such as SC, transportation, allocation and multi-agent systems (Babaei et al., 2023c; Morri et al., 2023; Kargar et al., 2020). The fuzzy goal programming (FGP) counterpart of Formulas (2–30) is given in Formulas (44–49). Objective function (44) maximizes the weighted sum of membership functions (related to triple objective functions). Constraints (45) and (46) show the upper and lower bounds of the membership functions. The membership function related to transparency maximization, the membership function related to cost minimization and the membership function related to the minimization of the environmental effects of BT are defined in constraints (47–49). Other constraints are in accordance with the constraints of the proposed model.
subject to
5 Results and analysis
To demonstrate the numerical aspect of the proposed model, we applied it to an example taken from Petridis et al. (2017). The example involves a three-level SC structure consisting of 5 plants, 20 candidate warehouses, and 5 customers. According to Petridis et al., the production limits are set between 5000 and 8000 units, and the link capacity between the levels is set at 500. The service level is specified as 0.68. Relevant data such as production costs (cf. Table 5), fixed and variable transportation costs between plants and warehouses (cf. Table 6), fixed and variable transportation costs between warehouses and customers (cf. Table 7), initial inventory, capacity coefficients, and installation costs (cf. Table 8), as well as demand (cf. Table 9), as reported by Petridis et al. (2017), are available. The algorithm is allowed to run for a maximum of 2 iterations according to Petridis et al. (2017) and Babaei et al. (2023a). For the real case study, parameters are set in accordance with Petridis et al. (2017) and Babaei et al. (2023a). Based on the findings by Babaei et al. (2023a), the probability of the attacker's success is determined to be 0.33. The emission coefficients are adjusted based on Fig. 3 in Jiang et al. (2021), which represents emissions resulting from the adoption of BT. The computational results are presented in Fig. 7. The results indicate that the second iteration is more cost-effective than the first iteration, thereby validating the Proposition and Corollary. In the second iteration, there is a decrease in emissions. Hence, this algorithm allows for control over the cost and emissions associated with the adoption of BT in the SC. However, it should be noted that the second iteration results in reduced transparency. As depicted in Fig. 7, the second iteration notably diminished the feasible space and consequently lowered the cost. Furthermore, it is worth mentioning that the solution time for the first iteration is 0.281s, while for the second iteration, it is reduced to 0.109s, indicating a decrease in time taken by the latter. Moreover, it is noteworthy that the results derived from this algorithm were exactly calculated using Win32 25.1.2 GAMS software.
The highest percentage reductions are observed in the cost objective function (16.85%), the emission objective function (13.45%), and the transparency objective function (6.01E-05%), respectively. As a result, this algorithm offers significant cost-effectiveness and environmental friendliness, albeit with a minor decrease in transparency.
The evaluator model (Formulas (36–42)) takes into account common criteria (cost and services) to calculate the efficiency scores of the warehouses. There are two scenarios considered in the model: one with the advantage of adopting BT (transparency due to the increase in the number of participants) and one with the challenge of adopting BT (environmental emission caused by computational operations). The efficiency scores of warehouses can be found in Table 2. When considering the advantage of BT adoption, it allows for better differentiation between warehouses in terms of efficiency scores. The final efficiency score for each warehouse is determined by aggregating the geometric mean of efficiency scores based on the challenge and advantage of BT adoption. By using this evaluator model, the number of warehouses can be reduced by 40% in the simultaneous planning of SC and BT (from 20 to 12 warehouses). This reduction is highly significant for SC managers, considering that the establishment of warehouses falls within the realm of strategic decisions.
Figure 8 shows the Coefficient of Variation (CV) of the values of the objective functions related to transparency, cost, and emissions when increasing the weights associated with the membership functions, ranging from 0.5 to 3. The highest CV is observed for emissions, followed by cost and transparency. This result indicates that addressing environmental concerns heavily relies on the attention of SC managers. Moreover, our proposed model and algorithm can adequately incorporate both environmental and cost considerations for SC managers.
By utilizing our model and algorithm, SC managers can assess the significance and weights of membership functions based on their specific concerns. It is important to note that Fig. 8 allows SC managers to identify which goal is most influenced by their decisions (see Fig. 9).
Transparency, cost, and environmental emissions may be affected by increasing uncertainty regarding the minimum number of participants in BT. From a scientific point of view, as the variance associated with the uncertainty parameter \(Var\left(\widetilde{ \pi }\right)\) increases, there are initially no changes in transparency, cost, and emissions. However, with a further increase in the variance related to the uncertainty parameter, transparency increases. As transparency increases, more participants join the blockchain. Consequently, both the cost and emissions also increase. Therefore, the impact of uncertainty results in an improvement in transparency but a deterioration in cost and emissions. Therefore, SC managers should understand that while controlling uncertainty in BT can enhance transparency, it may also worsen other concerns such as cost and the environment.
According to Fig. 10, the proposed algorithm's first iteration has a more decentralized blockchain network and more participants compared to the second iteration's network. This result is consistent with Fig. 7.
Subsequent iterations are less transparent but more cost-effective than earlier iterations. Therefore, SC managers need to find a compromise between transparency and cost to achieve their SC's goals. While the first iteration resulted in a more decentralized blockchain network, the second iteration focused on both transparency and cost simultaneously. The presented optimization model indicates that the output of the second iteration is based on both cost and transparency.
In Fig. 11, the effectiveness of evaluation models based on advantages and challenges is compared. The advantage-based model demonstrates greater efficacy in identifying inefficient units, whereas the challenge-based model results in higher variance in warehouse efficiency scores. Consequently, each of these two methods offers its own approach to evaluating the decision-making units (warehouses), and the aim is to integrate the evaluation strengths of both through the geometric mean. This endeavor seeks to establish a comprehensive and well-informed decision-making environment for SC managers.
6 Discussion
The SC is a network that includes businesses, society, and activities involved in the production and delivery of goods and services. It encompasses suppliers, manufacturers, distributors, warehouses, retailers, and customers. Despite the coordination and cooperation between the components in the SC, traditional SCs often suffer from inefficiencies, lack of transparency, and security issues. This is where BT comes in as a potential and innovative solution to these problems. BT can provide a secure, transparent, traceable, and decentralized platform for recording and tracking transactions in the SC. Today, several real-world companies have implemented BT. Here are some examples:
-
WalmartFootnote 1: Walmart has partnered with IBM to develop a blockchain-based system for tracing food products from farm to store.
-
MaerskFootnote 2: Maersk, the world's largest container shipping company, has collaborated with IBM to create a blockchain-based platform for managing global trade. However, the financial expectations of implementing blockchain in this industry have not been fully met.
-
De BeersFootnote 3: De Beers, the diamond mining company, has launched a blockchain-based platform called ‘’Tracr’’ to trace diamonds from mine to retailer.
-
NestleFootnote 4: Nestle has partnered with OpenSC, a blockchain platform, to track the SC of its palm oil products.
Despite its potential benefits, there are still some important challenges associated with adopting BT in the SC. One of the main challenges is cost. Deploying a blockchain-based system can be expensive, especially for small and medium-sized businesses and SCs. Another challenge is the environmental impact of BT. Blockchain networks require a significant amount of energy to operate, which could contribute to carbon emissions and climate change. In addition, regulations, security, interoperability of platforms, adoption strategies, and the novelty of BT create conditions of uncertainty for participants (companies) in the blockchain network, making businesses hesitant to use this technology. In our article, we present the new B&E algorithm that integrates BT into the SC. This algorithm provides a solution for the mentioned challenges. It takes into account the uncertainty conditions for adopting BT in the SC. Furthermore, the proposed algorithm is both cost-effective and environmentally friendly. It considers the transparency provided by using BT in the SC, the costs associated with traditional SC and the deployment of BT, as well as the environmental emissions resulting from adopting BT in the SC. The actions that SC managers can take based on the results of our article are summarized in Table 3.
Utilizing our iterative algorithm reduces costs, enhances transparency, and minimizes emissions. The evaluator model, which incorporates the transparency factor alongside cost and service factors, determines the efficiency of SC members with greater differentiation power. The management and control of environmental emissions heavily rely on the decisions made by SC managers and their priorities. Uncertain conditions in BT adoption lead to increased transparency, costs, and environmental emissions. As the iterations of the proposed algorithm progress, the blockchain network becomes more cost-effective and environmentally friendly. Considering the promising future of BT in SC, companies and SCs should carefully consider the challenges of SCP in addition to the benefits of utilizing BT. Therefore, our proposed algorithm can assist SC managers in implementing BT in the SC in a more transparent, cost-effective, and environmentally friendly manner.
As mentioned before, in our research, we have identified several critical gaps in the current approaches to adopting BT in SCM. These gaps include inadequate attention to security measures such as two-step authentication, insufficient consideration of environmental impacts like carbon emissions, and a lack of comprehensive optimization models for designing blockchain networks in conjunction with SCs. To address these gaps, we have developed a multi-objective optimization model presented in Formulas (2–30). This model aims to balance transparency, cost-effectiveness, and environmental sustainability within the SCM context. Objective functions within the model encompass maximizing transparency, minimizing traditional SCM costs and BT deployment costs, and reducing emissions associated with joining the blockchain network. We utilize advanced optimization techniques such as linearization and uncertain reformulation to address complexities and uncertainties inherent in SCM and BT integration. Linearization helps handle non-linear constraints arising from two-step authentication, while uncertain reformulation addresses uncertainties surrounding parameters like the minimum number of warehouses participating in the blockchain. Our evaluation criteria extend beyond traditional metrics to encompass both common criteria (e.g., transportation costs, service levels) and innovative criteria related to BT adoption. These innovative criteria consider both the advantages, such as enhanced transparency, and challenges, such as increased environmental emissions. Through computational analysis, we demonstrate the efficacy of our proposed algorithm in balancing transparency, cost, and emissions. Subsequent iterations of the algorithm show improvements in cost-effectiveness and environmental friendliness, albeit with some reduction in transparency. Additionally, our evaluator model facilitates decision-making by assessing the efficiency of SCM members based on various criteria, including transparency and environmental impact. By incorporating transparency considerations, we enable SC managers to make more informed decisions regarding BT adoption. Furthermore, we highlight the importance of addressing uncertainty in BT adoption, as it can impact transparency, cost, and emissions. SC managers must understand the trade-offs involved, as increasing transparency may lead to higher costs and emissions in uncertain environments. Ultimately, our proposed algorithm offers SC managers a systematic approach to implementing BT in SCM, considering transparency, cost-effectiveness, and environmental sustainability. By navigating the challenges and benefits of BT adoption, companies can enhance their SCM processes in a transparent, cost-effective, and environmentally friendly manner.
While our paper addresses the challenges of applying blockchain in SC, such as security, cost, and environmental concerns, and endeavors to propose models for designing blockchain-based SCs to tackle these challenges, it is important to note that the scope of challenges associated with blockchain adoption is broader. These include scalability and fault tolerance, establishment of new business frameworks and models, decentralized intelligence, management of massive erroneous or irrelevant data, cost considerations, computation on encrypted data, privacy protection, integration of multi-platform services, synchronization and integration across multiple chains, addressing black box effects and inefficiencies, ensuring system resilience, achieving functional completeness, implementing middleware solutions, effective self-adaptive measures against tampering, mitigating quantum attacks, standardization, managing risks and detecting fraud, defining lifecycle responsibilities and roles, performance expectations, efficiency in data mining, consensus mechanisms, balancing complexity and security, and integrating blockchain with other systems (Su et al., 2023).
7 Conclusion and outlook
BT is a distributed ledger that provides stakeholders with equal access to real-time information about the SC. By creating transparency in recording information, tracking goods, and improving security against manipulation and hacking, the adoption of BT in the SC offers many benefits. However, the cost of deploying BT and its resulting emissions are concerns for SC managers. Ignoring these challenges and solely focusing on the benefits poses a significant threat to organizations seeking to adopt BT in the SC. This research presented a novel solution for SCP that addresses transparency, cost, and emissions simultaneously. A tri-objective optimization model for SCP and its integration with BT was developed, considering the uncertainties surrounding BT adoption. These uncertainties arise from factors such as regulations, security, adoption, and technical issues. To treat the developed model, a novel B&E algorithm was introduced, which took into account not only cost and services but also transparency and environmental concerns. This algorithm generated optimal and efficient solutions for SCP and its integration with BT. The results demonstrated that our algorithm enables the adoption of BT in the three-level SC in a cost-effective and environmentally friendly manner. However, the uncertainties associated with BT adoption made it a costly and environmentally harmful endeavor.
Adopting BT in SCP and design is a novel and relatively unexplored issue, presenting both challenges and advantages for researchers. The limitations of this research include the lack of access to studies that address the simultaneous design of SCP and blockchain networks, as well as the scarcity of organizations with sufficient experience in applying BT in the SC. However, the innovation of integrating BT and SC, along with its growing popularity among researchers, managers, and SC decision-makers, are among the notable advantages of this research. The authors also identify opportunities to further develop their models by considering BT implementation in SCs with multiple levels, as well as the application of their proposed algorithm in SCs involved in industries such as food, medicine, and valuable goods. Further exploration can be undertaken to validate the robustness and effectiveness of our model by conducting comparative assessments against alternative algorithms. This comparative analysis would provide insights into the relative strengths and weaknesses of our approach, offering valuable validation and refinement opportunities. Moreover, to enhance the practical applicability and relevance of our findings, it is crucial to validate our models through real-world implementation across various industries. By applying our proposed methodologies in different industrial settings, the researcher can assess their performance under varied operational conditions, thereby validating their utility and generalizability beyond specific contexts. This empirical validation process would not only bolster the credibility of our study but also provide actionable insights for industry practitioners seeking to adopt similar approaches in their SCM systems.
One avenue for future research involves embracing other emerging technologies to revolutionize the SC, such as artificial intelligence and edge computing. These suggestions have the potential to significantly enhance SC data processing. Moreover, exploring the synergies between various emerging technologies presents an important opportunity to extend the current study.
Data availability
Discussed in Sect. 5.
Notes
References
Asghari, M., Fathollahi-Fard, A. M., Mirzapour Al-e-hashem, S. M. J., & Dulebenets, M. A. (2022). Transformation and linearization techniques in optimization: A state-of-the-art survey. Mathematics, 10(2), 283.
Babaei, A., Hatami-Marbini, A., Khedmati, M., & Akbari Jokar, M. R. (2021b). Cooperation among supply chain agents–a novel use of inventory models in DEA.
Babaei, A., Khedmati, M., & Akbari Jokar, M. R. (2021a). Proposing a new method for transportation planning considering traffic congestion. Advances in Industrial Engineering, 55(1), 27–46.
Babaei, A., Khedmati, M., & Akbari Jokar, M. R. (2023f). A new branch and efficiency algorithm for an optimal design of the supply chain network in view of resilience, inequity and traffic congestion. Annals of Operations Research, 321(1–2), 49–78.
Babaei, A., Khedmati, M., Akbari Jokar, M. R., & Tirkolaee, E. B. (2023b). Designing an integrated blockchain-enabled supply chain network under uncertainty. Scientific Reports, 13(1), 3928.
Babaei, A., Khedmati, M., & Jokar, M. R. A. (2022b). A branch and efficiency algorithm to design a sustainable two-echelon supply chain network considering traffic congestion and uncertainty. Environmental Science and Pollution Research, 30, 1–31.
Babaei, A., Khedmati, M., & Jokar, M. R. A. (2023a). A novel algorithm for evaluating the configurations of omni-channel distribution network considering transparency and consensus formation. International Journal of Shipping and Transport Logistics, 16(1–2), 170–193.
Babaei, A., Khedmati, M., & Jokar, M. R. A. (2023c). A new model for production and distribution planning based on data envelopment analysis with respect to traffic congestion, Blockchain technology and uncertain conditions. Annals of Operations Research. https://doi.org/10.1007/s10479-023-05349-8
Babaei, A., Khedmati, M., Jokar, M. R. A., & Babaee Tirkolaee, E. (2022a). Performance evaluation of omni-channel distribution network configurations considering green and transparent criteria under uncertainty. Sustainability, 14(19), 12607.
Babaei, A., Khedmati, M., Jokar, M. R. A., & Tirkolaee, E. B. (2023d). An integrated decision support system to achieve sustainable development in transportation routes with traffic flow. Environmental Science and Pollution Research, 30, 1–16.
Babaei, A., Khedmati, M., Jokar, M. R. A., & Tirkolaee, E. B. (2023e). Sustainable transportation planning with traffic congestion and uncertain conditions. Expert Systems with Applications, 227, 119792.
Bai, C., Quayson, M., & Sarkis, J. (2022). Analysis of Blockchain’s enablers for improving sustainable supply chain transparency in Africa cocoa industry. Journal of Cleaner Production, 358, 131896.
Charnes, A., & Cooper, W. W. (1977). Goal programming and multiple objective optimizations: Part 1. European Journal of Operational Research, 1(1), 39–54.
Chod, J., Trichakis, N., Tsoukalas, G., Aspegren, H., & Weber, M. (2020). On the financing benefits of supply chain transparency and blockchain adoption. Management Science, 66(10), 4378–4396.
Cooper, W. W., Deng, H., Huang, Z., & Li, S. X. (2002). Chance constrained programming approaches to technical efficiencies and inefficiencies in stochastic data envelopment analysis. Journal of the Operational Research Society, 53(12), 1347–1356.
Cooper, W. W., Seiford, L. M., & Tone, K. (2007). Data envelopment analysis: a comprehensive text with models, applications, references and DEA-solver software (p. 489). Springer.
De Carvalho, P. R., Naoum-Sawaya, J., & Elhedhli, S. (2022). Blockchain-Enabled supply chains: An application in fresh-cut flowers. Applied Mathematical Modelling, 110, 841–858.
Di Vaio, A., & Varriale, L. (2020). Blockchain technology in supply chain management for sustainable performance: Evidence from the airport industry. International Journal of Information Management, 52, 102014.
Garcia, D. J., & You, F. (2015). Supply chain design and optimization: Challenges and opportunities. Computers & Chemical Engineering, 81, 153–170.
Gharaei, A., Amjadian, A., Shavandi, A., & Amjadian, A. (2023a). An augmented Lagrangian approach with general constraints to solve nonlinear models of the large-scale reliable inventory systems. Journal of Combinatorial Optimization, 45(2), 78.
Gharaei, A., Karimi, M., & Hoseini Shekarabi, S. A. (2023b). Vendor-managed inventory for joint replenishment planning in the integrated qualitative supply chains: Generalised benders decomposition under separability approach. International Journal of Systems Science: Operations & Logistics, 10(1), 1962428.
Gölcük, İ. (2022). An interval type-2 fuzzy axiomatic design method: A case study for evaluating blockchain deployment projects in supply chain. Information Sciences, 602, 159–183.
Goli, A. (2023). Integration of Blockchain-enabled closed-loop supply chain and robust product portfolio design. Computers & Industrial Engineering, 179, 109211.
Goli, A., Babaee Tirkolaee, E., Golmohammadi, A. M., Atan, Z., Weber, G. W., & Ali, S. S. (2023). A robust optimization model to design an IoT-based sustainable supply chain network with flexibility. Central European Journal of Operations Research. https://doi.org/10.1007/s10100-023-00870-4
Govindan, K., Fattahi, M., & Keyvanshokooh, E. (2017). Supply chain network design under uncertainty: A comprehensive review and future research directions. European Journal of Operational Research, 263(1), 108–141.
Grigoroudis, E., Petridis, K., & Arabatzis, G. (2014). RDEA: A recursive DEA based algorithm for the optimal design of biomass supply chain networks. Renewable Energy, 71, 113–122.
Hahn, G. J., Brandenburg, M., & Becker, J. (2021). Valuing supply chain performance within and across manufacturing industries: A DEA-based approach. International Journal of Production Economics, 240, 108203.
Helo, P., & Hao, Y. (2019). Blockchains in operations and supply chains: A model and reference implementation. Computers & Industrial Engineering, 136, 242–251.
Herold, D. M., Saberi, S., Kouhizadeh, M., & Wilde, S. (2022). Categorizing transaction costs outcomes under uncertainty: A blockchain perspective for government organizations. Journal of Global Operations and Strategic Sourcing, 15(3), 431–448.
Izadikhah, M., Azadi, M., Toloo, M., Hussain, F., & K. (2021). Sustainably resilient supply chains evaluation in public transport: A fuzzy chance-constrained two-stage DEA approach. Applied Soft Computing, 113, 107879.
Jiang, R., & Guan, Y. (2016). Data-driven chance constrained stochastic program. Mathematical Programming, 158(1–2), 291–327.
Jiang, S., Li, Y., Lu, Q., Hong, Y., Guan, D., Xiong, Y., & Wang, S. (2021). Policy assessments for the carbon emission flows and sustainability of Bitcoin blockchain operation in China. Nature Communications, 12(1), 1–10.
Kamilaris, A., Fonts, A., & Prenafeta-Boldύ, F. X. (2019). The rise of blockchain technology in agriculture and food supply chains. Trends in Food Science & Technology, 91, 640–652.
Kargar, B., Pishvaee, M. S., Jahani, H., & Sheu, J. B. (2020). Organ transportation and allocation problem under medical uncertainty: A real case study of liver transplantation. Transportation Research Part E: Logistics and Transportation Review, 134, 101841.
Khan, H. H., Malik, M. N., Konečná, Z., Chofreh, A. G., Goni, F. A., & Klemeš, J. J. (2022). Blockchain technology for agricultural supply chains during the COVID-19 pandemic: Benefits and cleaner solutions. Journal of Cleaner Production, 347, 131268.
Kim, S. I., & Kim, S. H. (2022). E-commerce payment model using blockchain. Journal of Ambient Intelligence and Humanized Computing, 13(3), 1673–1685.
Komninos, N., Vergados, D. D., & Douligeris, C. (2007). A two-step authentication framework for mobile ad hoc networks. China Communications Journal, 4(1), 28–39.
Larson, P. D., & Rogers, D. S. (1998). Supply chain management: Definition, growth and approaches. Journal of Marketing Theory and Practice, 6(4), 1–5.
Liu, X., Barenji, A. V., Li, Z., Montreuil, B., & Huang, G. Q. (2021). Blockchain-based smart tracking and tracing platform for drug supply chain. Computers & Industrial Engineering, 161, 107669.
Maity, M., Tolooie, A., Sinha, A. K., & Tiwari, M. K. (2021). Stochastic batch dispersion model to optimize traceability and enhance transparency using Blockchain. Computers & Industrial Engineering, 154, 107134.
Morri, N., Hadouaj, S., & Said, L. B. (2023). Fuzzy logic based multi-objective optimization of a multi-agent transit control system. Memetic Computing, 15(1), 71–87.
Niu, B., Shen, Z., & Xie, F. (2021). The value of blockchain and agricultural supply chain parties’ participation confronting random bacteria pollution. Journal of Cleaner Production, 319, 128579.
Petridis, K., Dey, P. K., & Emrouznejad, A. (2017). A branch and efficiency algorithm for the optimal design of supply chain networks. Annals of Operations Research, 253, 545–571.
Placek, M. (2019). Supply chain investments in blockchain worldwide 2018–2019. Statista (visited on 30/4/2023). https://www.statista.com/statistics/1095144/global-supply-chain-blockchain-investment/
Prajapati, D., Jauhar, S. K., Gunasekaran, A., Kamble, S. S., & Pratap, S. (2022). Blockchain and IoT embedded sustainable virtual closed-loop supply chain in E-commerce towards the circular economy. Computers & Industrial Engineering, 172, 108530.
Saen, R. F., Karimi, B., & Fathi, A. (2022). Assessing the sustainability of transport supply chains by double frontier network data envelopment analysis. Journal of Cleaner Production, 354, 131771.
Su, D., Zhang, L., Peng, H., Saeidi, P., & Tirkolaee, E. B. (2023). Technical challenges of blockchain technology for sustainable manufacturing paradigm in Industry 4.0 era using a fuzzy decision support system. Technological Forecasting and Social Change, 188, 122275.
Talaeizadeh, A. A., Amjadian, A., Hashemi-Petroodi, S. E., & Moon, I. (2023). Supply chain coordination based on mean-variance risk optimisation: Pricing, warranty, and full-refund decisions. International Journal of Systems Science: Operations & Logistics, 10(1), 2249808.
Tiwari, R. N., Dharmar, S., & Rao, J. (1987). Fuzzy goal programming—an additive model. Fuzzy Sets and Systems, 24(1), 27–34.
Xia, Y., Zeng, W., Xing, X., Zhan, Y., Tan, K. H., & Kumar, A. (2021). Joint optimisation of drone routing and battery wear for sustainable supply chain development: a mixed-integer programming model based on blockchain-enabled fleet sharing. Annals of Operations Research, 1–39.
Xu, P., Lee, J., Barth, J. R., & Richey, R. G. (2021). Blockchain as supply chain technology: Considering transparency and security. International Journal of Physical Distribution & Logistics Management, 51(3), 305–324.
Yadav, S., & Singh, S. P. (2022). Modelling procurement problems in the environment of blockchain technology. Computers & Industrial Engineering, 172, 108546.
Funding
The author did not receive any funding from any organization.
Author information
Authors and Affiliations
Contributions
Conceptualization: AB, EBT; Methodology: AB; Formal analysis and investigation: SSA; Validation: EBT, SSA; Writing—original draft preparation: AB, EBT; Writing—review and editing: EBT, SSA; Resources: AB, EBT; Supervision: EBT.
Corresponding authors
Ethics declarations
Conflict of interest
The author does not have any pertinent financial or non-financial affiliations to report.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Babaei, A., Tirkolaee, E.B. & Ali, S.S. Innovative supply chain network design with two-step authentication and environmentally-friendly blockchain technology. Ann Oper Res (2024). https://doi.org/10.1007/s10479-024-05950-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10479-024-05950-5