Abstract
Writing correct programs for weak-memory models such as the C11 memory model is challenging because of the weak consistency guarantees these models provide. The first program logics for the verification of such programs have recently been proposed, but their usage has been limited thus far to manual proofs. Automating proofs in these logics via first-order solvers is non-trivial, due to features such as higher-order assertions, modalities and rich permission resources. In this paper, we provide the first encoding of a weak-memory program logic using existing deductive verification tools. Our work enables, for the first time, the (unbounded) verification of C11 programs at the level of abstraction provided by the program logics; the only necessary user interaction is in the form of specifications written in the program logic and, in rare cases, ghost operations. We tackle three recent program logics: Relaxed Separation Logic and two forms of Fenced Separation Logic, and show how these can be encoded using the Viper verification infrastructure. In doing so, we illustrate several novel encoding techniques which could be employed for other logics. Our work is implemented, and has been evaluated on examples from existing papers as well as the Facebook open-source Folly library.

















Similar content being viewed by others
Notes
For a general introduction to these reasoning challenges and issues in defining the model itself, we refer the reader to [43].
i.e. verifying all program behaviours, without bounding the number of threads, loop iterations, heap size and so on.
By convention, we use math-font variables for meta/logical variables and those from source programs (e.g. in \(\textsf {Uninit}(l)\); we use corresponding code-font variables for the Viper variables corresponding to these source-level variables (e.g. in

 .
.Viper macros can be defined for assertions or statements, and are syntactically expanded (and their arguments substituted) on use.
A
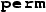 expression yields the permission fraction held for a field or predicate instance.
expression yields the permission fraction held for a field or predicate instance.For historical reasons, in our artefact examples, the
 macro is actually called
macro is actually called
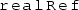 ; we renamed this subsequently due to potential confusion with the notion of the “real heap” employed in Sect. 4.2.
; we renamed this subsequently due to potential confusion with the notion of the “real heap” employed in Sect. 4.2.In the RSL logics, extended CAS proof rules are also supported (e.g. in the “Appendix” of FSL\({+}{+}\) [14]) allowing the specification of a different access mode for when a CAS operation fails; we omit this for simplicity, and use the same access mode for both cases. An extension would be straightforward, but this flexibility has not yet appeared necessary for any examples.
Instead of distinguishing the two cases via the value of the
 field, it would also be possible to introduce another field to represent \(\textsf {RMWAcq}\) assertions.
field, it would also be possible to introduce another field to represent \(\textsf {RMWAcq}\) assertions.
References
Abdulla, P.A., Atig, M.F., Jonsson, B., Leonardsson, C.: Stateless model checking for POWER. In: CAV 2016 Proceedings Part II, pp. 134–156 (2016). https://doi.org/10.1007/978-3-319-41540-6_8
Abdulla, P.A., Atig, M.F., Bouajjani, A., Ngo, T.P.: The benefits of duality in verifying concurrent programs under TSO. CoRR (2017). arXiv:1701.08682
Alglave, J., Cousot, P.: Ogre and Pythia: an invariance proof method for weak consistency models. In: POPL 2017, pp. 3–18. ACM, New York, NY, USA, POPL (2017). https://doi.org/10.1145/3009837.3009883
Barnett, M., Chang, B.Y.E., DeLine, R., Jacobs, B., Leino, K.R.M.: Boogie: a modular reusable verifier for object-oriented programs. In: Proceedings of the 4th International Conference on Formal Methods for Components and Objects, pp. 364–387. Springer, Berlin, FMCO’05 (2006). https://doi.org/10.1007/11804192_17
Bobot, F., Filliâtre, J.C., Marché, C., Paskevich, A.: Why3: shepherd your herd of provers. In: Boogie 2011: First International Workshop on Intermediate Verification Languages, Wrocław, Poland, pp. 53–64 (2011). http://proval.lri.fr/publications/boogie11final.pdf
Bornat, R., Calcagno, C., O’Hearn, P., Parkinson, M.: Permission accounting in separation logic. In: Proceedings of POPL’05, pp. 259–270. ACM, New York, NY, USA (2005). https://doi.org/10.1145/1040305.1040327
Bouajjani, A., Derevenetc, E., Meyer, R.: Checking and enforcing robustness against TSO. In: ESOP 2013, pp. 533–553. Springer, Berlin, ESOP’13 (2013). https://doi.org/10.1007/978-3-642-37036-6_29
Boyland, J.: Checking Interference with Fractional Permissions, vol. 2694, pp. 55–72. Springer, Berlin (2003)
Chlipala, A.: Mostly-automated verification of low-level programs in computational separation logic. In: Proceedings of the 32nd ACM SIGPLAN Conference on Programming Language Design and Implementation, pp. 234–245. ACM, New York, NY, USA, PLDI’11 (2011). https://doi.org/10.1145/1993498.1993526
Cohen, E., Dahlweid, M., Hillebrand, M., Leinenbach, D., Moskal, M., Santen, T., Schulte, W., Tobies, S.: VCC: A Practical System for Verifying Concurrent C, pp. 23–42. Springer, Berlin (2009). https://doi.org/10.1007/978-3-642-03359-9_2
Cuoq, P., Kirchner, F., Kosmatov, N., Prevosto, V., Signoles, J., Yakobowski, B.: Frama-C. In: SEFM, pp. 233–247. Springer, Berlin (2012). https://doi.org/10.1007/978-3-642-33826-7_16
Dan, A., Meshman, Y., Vechev, M., Yahav, E.: Effective abstractions for verification under relaxed memory models. In: VMCAI 2015, pp. 449–466. Springer, Berlin (2015). https://doi.org/10.1007/978-3-662-46081-8_25
Doko, M., Vafeiadis, V.: A program logic for C11 memory fences. VMCAI, Springer, Lecture Notes in Computer Science 9583, 413–430 (2016)
Doko, M., Vafeiadis, V.: Tackling real-life relaxed concurrency with FSL++. In: ESOP 2017, pp. 448–475. Springer, Berlin (2017)
Facebook Folly: Reader–writer spinlock implementation (2018). https://github.com/facebook/folly/blob/master/folly/RWSpinLock.h
Heule, S., Leino, K.R.M., Müller, P., Summers, A.J.: Abstract read permissions: fractional permissions without the fractions. VMCAI, Springer, Lecture Notes in Computer Science 7737, 315–334 (2013)
Jacobs, B.: Verifying TSO programs. CW Reports CW660, Department of Computer Science, KU Leuven, (2014). https://lirias.kuleuven.be/handle/123456789/452373
Jacobs, B., Smans, J., Piessens, F.: A quick tour of the VeriFast program verifier. APLAS, Springer, LNCS 6461, 304–311 (2010)
Kaiser, J.O., Dang, H.H., Dreyer, D., Lahav, O., Vafeiadis, V.: Strong logic for weak memory: reasoning about release-acquire consistency in Iris. In: ECOOP 2017, Schloss Dagstuhl–Leibniz, LIPIcs, vol. 74, pp. 17:1–17:29, (2017). https://doi.org/10.4230/LIPIcs.ECOOP.2017.17, http://drops.dagstuhl.de/opus/volltexte/2017/7275
Kokologiannakis, M., Lahav, O., Sagonas, K., Vafeiadis, V.: Effective stateless model checking for C/C++ concurrency. In: PACMPL, vol. 2(POPL), pp. 17:1–17:32 (2018). https://doi.org/10.1145/3158105, https://doi.org/10.1145/3158105
Krebbers, R., Jung, R., Bizjak, A., Jourdan, J.H., Dreyer, D., Birkedal, L.: The essence of higher-order concurrent separation logic. In: ESOP, pp. 696–723, Springer, New York, Inc., New York, NY, USA (2017). https://doi.org/10.1007/978-3-662-54434-1_26, https://doi.org/10.1007/978-3-662-54434-1_26
Lahav, O.: Verification under causally consistent shared memory. SIGLOG News 6(2), 43–56 (2019). https://doi.org/10.1145/3326938.3326942
Leino, K.R.M.: Dafny: an automatic program verifier for functional correctness. In: Proceedings of LPAR’10, pp. 348–370, Springer, Berlin (2010). http://dl.acm.org/citation.cfm?id=1939141.1939161
Leino, K.R.M., Müller, P.: A basis for verifying multi-threaded programs. In: Castagna, G. (ed.) ESOP, Springer-Verlag, LNCS, vol. 5502, pp. 378–393 (2009)
Müller, P., Schwerhoff, M., Summers, A.J.: Automatic verification of iterated separating conjunctions using symbolic execution. CAV, Springer-Verlag, LNCS 9779, 405–425 (2016)
Müller, P., Schwerhoff, M., Summers, A.J.: Viper: a verification infrastructure for permission-based reasoning. In: Jobstmann, B., Leino, K.R.M. (eds.) VMCAI, Springer-Verlag, LNCS, vol. 9583, pp. 41–62 (2016)
O’Hearn, P.W., Reynolds, J.C., Yang, H.: Local reasoning about programs that alter data structures. In: Proceedings of CSL’01, pp. 1–19. Springer, London, UK (2001). http://dl.acm.org/citation.cfm?id=647851.737404
Online Appendix: Viper-encoded examples (2019). http://viper.ethz.ch/onlineappendix-rsl-encoding/
Parkinson, M.J., Summers, A.J.: The relationship between separation logic and implicit dynamic frames. Log. Methods Comput. Sci. 8(3:01), 1–54 (2012)
Reynolds, J.C.: Definitional interpreters for higher-order programming languages. In: ACM Annual Conference—Volume 2, pp. 717–740. ACM, ACM’72 (1972)
Reynolds, J.C.: Separation logic: a logic for shared mutable data structures. In: LICS, IEEE Computer Society Press (2002)
RSL Front-End: RSL to Viper Front-End; TACAS 2018 Artifact Version (2018). https://figshare.com/articles/RSL_to_Viper_Front_end/5900233
RSL Front-End Zip Files: RSL to Viper Front-End Zip Files (updated since TACAS 2018; Windows, Linux, Mac versions available) (2019). https://www.pm.inf.ethz.ch/research/viper/prototype-rsl-encoding.html
Rust Library: ARC (Atomic Reference Counting) (2019). https://doc.rust-lang.org/std/sync/struct.Arc.html
Sergey, I., Nanevski, A., Banerjee, A.: Mechanized verification of fine-grained concurrent programs. In: Proceedings of PLDI’15, pp. 77–87. ACM, New York, NY, USA (2015). https://doi.org/10.1145/2737924.2737964
Smans, J., Jacobs, B., Piessens, F.: Implicit dynamic frames. ACM Trans Program Lang Syst 34(1), 2:1–2:58 (2012)
Summers, A.J., Drossopoulou, S.: A formal semantics for isorecursive and equirecursive state abstractions. ECOOP, Springer, LNCS 7920, 129–153 (2013)
Summers, A.J., Müller, P.: Automating deductive verification for weak-memory programs. Tools and Algorithms for the Construction and Analysis of Systems (TACAS), LNCS, pp. 190–209. Springer, Berlin (2018)
Summers, A.J., Müller, P.: Automating deductive verification for weak-memory programs (extended version) (2018)
Travkin, O., Wehrheim, H.: Verification of concurrent programs on weak memory models. In: Sampaio, A., Wang, F. (eds.) Theoretical Aspects of Computing (ICTAC). Lecture Notes in Computer Science, vol. 9965, pp. 3–24. Springer, Berlin (2016)
Turon, A., Vafeiadis, V., Dreyer, D.: GPS: navigating weak memory with ghosts, protocols, and separation. In: OOPSLA, pp. 691–707. ACM (2014)
Vafeiadis, V.: Personal communication (2016)
Vafeiadis, V., Narayan, C.: Relaxed separation logic: a program logic for C11 concurrency. In: OOPSLA, pp. 867–884. ACM (2013)
Xu, F., Fu, M., Feng, X., Zhang, X., Zhang, H., Li, Z.: A practical verification framework for preemptive OS kernels. In: CAV Proceedings Part II, Springer International Publishing, Cham, pp. 59–79 (2016). https://doi.org/10.1007/978-3-319-41540-6_4
Acknowledgements
We are grateful to Viktor Vafeiadis and Marko Doko for many explanations of the RSL logics and helpful discussions about our encoding. We thank Christiane Goltz for her work on the prototype tool, and Malte Schwerhoff for implementing additional features. We thank Marco Eilers for his assistance with the online appendix, and Arshavir Ter-Gabrielyan for automating our artefact assembly for various operating systems. We also thank Andrei Dan, Lucas Brutschy, Malte Schwerhoff and the anonymous TACAS 2018 and STTT Special Issue reviewers for feedback on earlier versions of this work.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Summers, A.J., Müller, P. Automating deductive verification for weak-memory programs (extended version). Int J Softw Tools Technol Transfer 22, 709–728 (2020). https://doi.org/10.1007/s10009-020-00559-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10009-020-00559-y






 .
.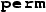 expression yields the permission fraction held for a field or predicate instance.
expression yields the permission fraction held for a field or predicate instance. macro is actually called
macro is actually called
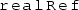 ; we renamed this subsequently due to potential confusion with the notion of the “real heap” employed in Sect.
; we renamed this subsequently due to potential confusion with the notion of the “real heap” employed in Sect.  field, it would also be possible to introduce another field to represent
field, it would also be possible to introduce another field to represent