Abstract
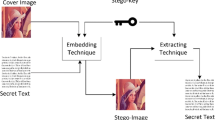
In this paper, we present a robust and imperceptible image steganography (IS) scheme for covert communication. A substantial literature presented on IS is distortion based that radically affects image imperceptibility. These schemes conceal secret information in LSBs or MSBs of cover image by using simple or random substitution. The usage of LSBs and MSBs makes these schemes vulnerable to malicious attacks like Chi-square attack and sample pair attack, and specifically, the MSBs affect the imperceptibility of cover image. Additionally, these schemes endure low capacity as large numbers of cover image pixels are required for hiding even low volume of information. The proposed IS scheme is distortion free as the negligible PVD of cover and secret image is utilized for information hiding. In contrast to LSB- or MSB-based information hiding schemes, we proposed FEM method that compares the entropy of frequencies of secret and cover image for information hiding. In fact, the elevated rate of FEM leads to high imperceptibility and capacity. Moreover, the proposed scheme uses multilayer approach that has layered transformations to frequency domain for improved robustness. Experimental investigation demonstrates that the proposed scheme has better PSNR and BPP with enhanced robustness and imperceptibility in contrast to existing schemes.














Similar content being viewed by others
References
Akhtar N, Johri P et al. (2013) Enhancing the security and quality of LSB based image steganography. In: IEEE 5th international conference on computational intelligence and communication networks, pp 385–390
Akhtar N, Johri P et al. (2014) An improved inverted LSB image steganography. In: IEEE international conference on issues and challenges in intelligent computing techniques, pp 749–755
Al-Jaber A, Sabri K (2010) Information hiding without changing the cover image. Int Arab J Inf Technol 2(1):1–4
Arora K, Gandhi G (2014) Enhanced steganography using K-matrix. Int J Comput Sci Eng 2(6):50–53
Ashwin S, Ramesh J et al. (2012) Novel and secure encoding and hiding techniques using image steganography: a survey. In: IEEE international conference on emerging trends in electrical engineering and energy management, pp 171–177
Bansal K, Singh A (2012) Use of textual compression in steganography & cryptography. Int J Innov Res Dev 1(8):109–115
Bing F, Xiansan Z (2009) Information hiding technique in most significant bit of still image. In: IEEE international conference image analysis & signal processing, pp 1–3
Biswas S, Nag A et al. (2012) an image steganography technique using X-box mapping. In: IEEE-international conference on advances in engineering, science and management, pp 709–713
Bukhari RH, Sarfaraz A, Khan A (2018) Python: a critical analysis of programing languages for novices. Sci Int 30(3):327–331
Changder S, Samima S et al. (2013) Secure key based image realization steganography. In: Proceedings of the IEEE second international conference on image information processing, pp 377–382
Dagadita M, Slusanschi E et al. (2013) Data hiding using steganography. In: Parallel and distributed computing IEEE 12th international symposium, pp 159–166
Dagar S (2014) highly randomized image steganography using secret keys. In: IEEE international conference on recent advances and innovations in engineering, pp 1–5
Gu C, Cao X (2012) Research on information hiding technology. In: IEEE 2nd international conference consumer electronics. Communications and networks, pp 2035–2037
Jain R, Singh B (2014) Multistage three layers image steganography using LSB with enhanced security. Int J Emerg Technol Adv Eng 4(6):387–392
Janeyulu S, Prasad M et al (2009) A novel information hiding technique for security by using image steganography. J Theoret Appl Inf Technol 8(1):35–39
Juneja M, Sandhu P (2014) Improved LSB based steganography techniques for color images in spatial domain. Int J Netw Secur 16(4):366–376
Karim S, Rahman M et al. (2011) A new approach for LSB based image steganography using secret key. In: Proceedings of IEEE 14th international conference on computer and information technology, pp 22–24
Kaur G, Kaur K (2013) Digital watermarking and other data hiding techniques. Int J Innov Technol Explor Eng 2(5):181–183
Kaur K, Kour G (2013) Implementing LSB on image watermarking. Int J Adv Res Comput Commun Eng 2(8):3130–3134
Kaur S, Bansal S et al. (2014) Steganography and classification of image steganography techniques. In: IEEE International conference on computing for sustainable global development, pp 870–875
Kavipriya P, Sangeetha M (2014) Color secret image encryption and share generation for multiple-secret threshold visual cryptography. Int J Eng Res Appl 4(2):26–28
Keshari S, Modani S et al. (2011) Weighted fractional fourier transform based image steganography. In: IEEE international conference on recent trends in information systems, pp 214–217
Khadim U, Khan A, Ahmad B, Khan A (2015) Information hiding in text to improve performance for word document. Int J Technol Res 3(3):50–55
Khan A (2014) Joint ownership verification for digital text. Adv Comput Sci Appl (ACSA) 3(4):525–531
Khan A (2015a) Comparative analysis of watermarking techniques. Sci Int 27(6):6091–6096
Khan A (2015b) Robust textual steganography. J Sci 4(4):426–434
Khan A, Sarfaraz A (2017) Vetting the security of mobile applications. Sci Int 29(2):361–365
Khan A, Sarfaraz A (2018) Practical guidelines for securing wireless local area networks (WLANs). Int J Secur Appl 12(3):19–28
Khan A, Sohaib M, Amjad FM (2016) High-capacity multi-layer framework for highly robust textual steganography. Sci Int 28(5):4451–4457
Kumar S, Sharma V (2013) A new approach to hide text in images using steganography. Int J Adv Res Comput Sci Softw Eng 3(4):701–708
Mousa H (2013) Secured steganography algorithm based random function. In: 8th IEEE international conference on computer engineering & systems, pp 228–232
Pandya M, Joshi H et al (2013) A novel digital watermarking algorithm using random matrix image. Int J Comput Appl 61(2):18–21
Ridzoň R, Kanocz T et al. (2010) Using DCT coefficients flipping for information hiding in still images. In: 20th IEEE international conference radio elektronika, pp 1–4
Sachdeva S, Kumar A et al. (2012) Colour image steganography based on modified quantization table. In: Second IEEE international conference on advanced computing & communication technologies , pp 309–314
Saravanan D, Doni A et al (2013) Image information hiding: an survey. SIJ Trans Comput Sci Eng Appl 1(1):1–5
Schalkoff RJ (1989) Digital image processing and computer vision. Wiley, New York, pp 1–489
Shelke M, Dongre M et al (2014) Comparison of different techniques for steganography in images. Int J Appl Innov Eng Manag 3(2):171–176
Singleton N (2011) Computerized image processing for forgery prevention. In: First international conference on innovative computing information & control, pp 459–462
Thakre K, Chitaliya N (2014) Dual image steganography for communicating high security information. Int J Soft Comput Eng 4(3):7–12
Thampi S (2008) Information hiding techniques: a tutorial review. Network security and cryptography, arXiv preprint arXi, pp 1–20
Thangadurai K, Devi G et al. (2014) An analysis of LSB based image steganography techniques. In: IEEE international conference on computer communication and informatics, pp 1–4
Tiwari R, Sahoo G (2012) Some new methodologies for image hiding using steganographic techniques, Arxiv Preprint Arxiv, pp 25–31
Tso H, Lou D (2010) Information hiding method using sharing images. In: IEEE fourth international conference on genetic and evolutionary computing, pp 642–645
Utareja S, Patel K et al (2013) A survey of information hiding techniques. Int J Emerg Technol Adv Eng 3(1):347–350
Vijaya P (2012) Secure data hiding algorithm using encrypted secret message. Int J Sci Res Publ 2(6):1–4
Yongping Z (2011) Image information hiding technique based on frequency hopping and 2D-DWT. In: IEEE international conference on computer science and automation engineering, pp 461–464
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors have no conflict of interest upon this article.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Communicated by V. Loia.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Khan, A., Sarfaraz, A. Novel high-capacity robust and imperceptible image steganography scheme using multi-flipped permutations and frequency entropy matching method. Soft Comput 23, 8045–8056 (2019). https://doi.org/10.1007/s00500-018-3441-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-018-3441-1