Abstract
We present practical attacks on OCB2. This mode of operation of a blockcipher was designed with the aim to provide particularly efficient and provably secure authenticated encryption services, and since its proposal about 15 years ago it belongs to the top performers in this realm. OCB2 was included in an ISO standard in 2009. An internal building block of OCB2 is the tweakable blockcipher obtained by operating a regular blockcipher in \({\text {XEX}}^*\) mode. The latter provides security only when evaluated in accordance with certain technical restrictions that, as we note, are not always respected by OCB2. This leads to devastating attacks against OCB2’s security promises: We develop a range of very practical attacks that, amongst others, demonstrate universal forgeries and full plaintext recovery. We complete our report with proposals for (provably) repairing OCB2. As a direct consequence of our findings, OCB2 is currently in a process of removal from ISO standards. Our attacks do not apply to OCB1 and OCB3, and our privacy attacks on OCB2 require an active adversary.














Similar content being viewed by others
Notes
By Krovetz, http://web.cs.ucdavis.edu/~rogaway/ocb/code-2.0.htm.
ISO document Draft Amendment ISO/IEC 19772:2009/DAM 1:2019 lists OCB2 as a deprecated scheme. The document is currently available at https://www.iso.org/standard/77459.html.
We do not employ a dedicated symbol for the ciphertext space but instead use the symbol \(\mathcal{M}\) for both messages and ciphertexts.
We clarify that the PRIV-CCA notion does not imply the AUTH notion, and in particular not AE. To see this, modify any PRIV-CCA secure scheme by augmenting the ciphertext space by one additional ciphertext that always decrypts to some fixed message, independently of the used key, nonce, and associated data. This modified scheme provides PRIV-CCA but not AUTH.
In that paper the mode was actually referred to as OCB1; what we call OCB1 was referred to as OCB in [35].
The attack does not require knowledge of the contents of blocks \(M[1],\ldots ,M[m-2]\), but does depend on their sum \(M[1]\oplus \cdots \oplus M[m-2]\).
See Fig. 1 for an example: Our notation \(\mathcal {E}_E(N,A,M)\) suggests that the mode’s key is the access to E and its inverse; the key K does not appear at this level of abstraction.
The number of pairs can be fewer than \(m+1\) if collisions occur. This happens, however, only with negligible probability.
The technique of first learning value L in order to then attack the security of OCB was already explored in prior work. While Ferguson [12] recovered L from collisions arising during the encryption of very long messages, Vaudenay and Vizár [43] achieved L-recovery in a setting that is not nonce-respecting. Notably, [43] observed that learning L suffices to recover arbitrary blockcipher mappings.
An equivalent mode for OCB3 is called \(\mathrm {\Theta }\text {CB}3\) [24].
We note that the constant 9.5 in \( \mathbf{Adv} ^{ \textsf {tsprp}}_{{\text {XEX}}^*_{\mathsf P}}({\mathcal {B}}_\pm )\) in (7) was improved to 4.5 in [30].
Recent work on AEAD combiners [33] suggests operating multiple AEAD schemes and combining their results, with the effect that the result is secure if at least one of the ingredient schemes is. This approach might be interesting if the unproven methods proposed here are used.
We caution that this change might not be sufficient. Our results from Sect. 4.4 indicate that more plaintexts and ciphertexts have to be rejected: on the encryptor’s side all messages with \(M[m-1]=\texttt {len}(0^{n-s})\) for some \(s=1,\ldots ,n\), and on the decryptor’s side all ciphertexts that would result in \(M^*[m-1]=\texttt {len}(0^{n-s})\) for some \(s=1,\ldots ,n\). We are still investigating which conditions would be necessary/sufficient for security.
References
E. Andreeva, A. Bogdanov, A. Luykx, B. Mennink, N. Mouha, K. Yasuda, How to securely release unverified plaintext in authenticated encryption, in Sarkar, P., Iwata, T. (eds.) ASIACRYPT 2014, Part I. LNCS, vol. 8873, Dec 7–11, (Springer, Heidelberg, Germany, Kaoshiung, Taiwan, R.O.C., 2014), pp. 105–125
K. Aoki, K. Yasuda, The security of the OCB mode of operation without the SPRP assumption, in Susilo, W., Reyhanitabar, R. (eds.) ProvSec 2013. LNCS, vol. 8209, Oct 23–25, (Springer, Heidelberg, Germany, Melaka, Malaysia, 2013), pp. 202–220
T. Ashur, O. Dunkelman, A. Luykx, Boosting authenticated encryption robustness with minimal modifications, in Katz, J., Shacham, H. (eds.) CRYPTO 2017, Part III. LNCS, vol. 10403, Aug 20–24, 2017 (Springer, Heidelberg, Germany, Santa Barbara, CA, USA, 2017), pp. 3–33
Z. Bao, J. Guo, T. Iwata, K. Minematsu, ZOCB and ZOTR: Tweakable blockcipher modes for authenticated encryption with full absorption. IACR Trans. Symm. Cryptol. 2019(2), 1–54 (2019)
M. Bellare, A. Desai, E. Jokipii, P. Rogaway, A concrete security treatment of symmetric encryption, in 38th FOCS, Oct 19–22 (IEEE Computer Society Press, Miami Beach, Florida, 1997), pp. 394–403
M. Bellare, P. Rogaway, D. Wagner, The EAX mode of operation, in Roy, B.K., Meier, W. (eds.) FSE 2004. LNCS, vol. 3017, Feb 5–7, (Springer, Heidelberg, Germany, New Delhi, India, 2004), pp. 389–407
T. Beyne, Y.L. Chen, C. Dobraunig, B. Mennink, Elephant. Tech. rep., National Institute of Standards and Technology (2019), https://csrc.nist.gov/Projects/lightweight-cryptography/round-2-candidates
J. Black, M. Cochran, MAC reforgeability, in Dunkelman, O. (ed.) FSE 2009. LNCS, vol. 5665, Feb 22–25 (Springer, Heidelberg, Germany, Leuven, Belgium, 2009), pp. 345–362
J. Black, P. Rogaway, A block-cipher mode of operation for parallelizable message authentication, in Knudsen, L.R. (ed.) EUROCRYPT 2002. LNCS, vol. 2332, Apr 28 – May 2 (Springer, Heidelberg, Germany, Amsterdam, The Netherlands, 2002), pp. 384–397
R. Bost, O. Sanders, Trick or tweak: On the (in)security of OTR’s tweaks, in Cheon, J.H., Takagi, T. (eds.) ASIACRYPT 2016, Part I. LNCS, vol. 10031, Dec 4–8 (Springer, Heidelberg, Germany, Hanoi, Vietnam, 2016), pp. 333–353
P. Donescu, V.D. Gligor, D. Wagner, A note on NSA’s Dual Counter Mode of encryption (2001), http://www.cs.berkeley.edu/~daw/papers/dcm-prelim.ps
N. Ferguson, Collision attacks on OCB. Comments to NIST (2002), https://csrc.nist.gov/CSRC/media/Projects/Block-Cipher-Techniques/documents/BCM/Comments/general-comments/papers/Ferguson.pdf
C. Forler, E. List, S. Lucks, J. Wenzel, Reforgeability of authenticated encryption schemes, in Pieprzyk, J., Suriadi, S. (eds.) ACISP 17, Part II. LNCS, vol. 10343, Jul 3–5 (Springer, Heidelberg, Germany, Auckland, New Zealand, 2017), pp. 19–37
R. Granger, P. Jovanovic, B. Mennink, S. Neves, Improved masking for tweakable blockciphers with applications to authenticated encryption, in Fischlin, M., Coron, J.S. (eds.) EUROCRYPT 2016, Part I. LNCS, vol. 9665, May 8–12 (Springer, Heidelberg, Germany, Vienna, Austria, 2016), pp. 263–293
A. Inoue, T. Iwata, K. Minematsu, B. Poettering, Cryptanalysis of OCB2: Attacks on authenticity and confidentiality, in Boldyreva, A., Micciancio, D. (eds.) CRYPTO 2019, Part I. LNCS, vol. 11692, Aug 18–22 (Springer, Heidelberg, Germany, Santa Barbara, CA, USA, 2019), pp. 3–31
A. Inoue, T. Iwata, K. Minematsu, B. Poettering, Cryptanalysis of OCB2: Attacks on authenticity and confidentiality. Cryptology ePrint Archive, Report 2019/311 (2019), https://eprint.iacr.org/2019/311
A. Inoue, K. Minematsu, Cryptanalysis of OCB2. Cryptology ePrint Archive, Report 2018/1040 (2018), https://eprint.iacr.org/2018/1040
A. Inoue, K. Minematsu, Parallelizable authenticated encryption with small state size, in Paterson, K.G., Stebila, D. (eds.) SAC 2019. LNCS, vol. 11959, Aug 12–16 (Springer, Heidelberg, Germany, Waterloo, ON, Canada, 2019), pp. 618–644
ISO: Information Technology—Security techniques—Authenticated encryption, ISO/IEC 19772:2009. International Standard ISO/IEC 19772 (2009)
ISO/IEC JTC 1/SC 27: STATEMENT ON OCB2.0—Major weakness found in a standardised cipher scheme (2019-01-09, press release), https://www.din.de/blob/321470/da3d9bce7116deb510f6aded2ed0b4df/20190107-press-release-19772-2009-1st-ed-ocb2-0-data.pdf
T. Iwata, Plaintext recovery attack of OCB2. Cryptology ePrint Archive, Report 2018/1090 (2018), https://eprint.iacr.org/2018/1090
T. Iwata, K. Kurosawa, OMAC: One-key CBC MAC. In: Johansson, T. (ed.) FSE 2003. LNCS, vol. 2887, Feb 24–26 (Springer, Heidelberg, Germany, Lund, Sweden, 2003), pp. 129–153
T. Iwata, K. Ohashi, K. Minematsu, Breaking and repairing GCM security proofs, in Safavi-Naini, R., Canetti, R. (eds.) CRYPTO 2012. LNCS, vol. 7417, Aug 19–23 (Springer, Heidelberg, Germany, Santa Barbara, CA, USA, 2012), pp. 31–49
T. Krovetz, P. Rogaway, The software performance of authenticated-encryption modes, in Joux, A. (ed.) FSE 2011. LNCS, vol. 6733, Feb 13–16 (Springer, Heidelberg, Germany, Lyngby, Denmark, 2011), pp. 306–327
T. Krovetz, P. Rogaway, The OCB Authenticated-Encryption Algorithm. IRTF RFC 7253 (2014)
M. Liskov, R.L. Rivest, D. Wagner, Tweakable block ciphers, in Yung, M. (ed.) CRYPTO 2002. LNCS, vol. 2442, Aug 18–22 (Springer, Heidelberg, Germany, Santa Barbara, CA, USA, 2002), pp. 31–46
B. Mennink, XPX: Generalized tweakable Even-Mansour with improved security guarantees, in Robshaw, M., Katz, J. (eds.) CRYPTO 2016, Part I. LNCS, vol. 9814, Aug 14–18 (Springer, Heidelberg, Germany, Santa Barbara, CA, USA, 2016), pp. 64–94
K. Minematsu, Parallelizable rate-1 authenticated encryption from pseudorandom functions, in Nguyen, P.Q., Oswald, E. (eds.) EUROCRYPT 2014. LNCS, vol. 8441, May 11–15 (Springer, Heidelberg, Germany, Copenhagen, Denmark, 2014), pp. 275–292
K. Minematsu, S. Lucks, H. Morita, T. Iwata, Attacks and security proofs of EAX-prime, in Moriai, S. (ed.) FSE 2013. LNCS, vol. 8424, Mar 11–13 (Springer, Heidelberg, Germany, Singapore, 2014), pp. 327–347
K. Minematsu, T. Matsushima, Generalization and Extension of \(\text{XEX}^{*}\) Mode. IEICE Transactions 92-A(2), 517–524 (2009)
M. Nandi, Forging attacks on two authenticated encryption schemes COBRA and POET, in Sarkar, P., Iwata, T. (eds.) ASIACRYPT 2014, Part I. LNCS, vol. 8873, Dec 7–11 (Springer, Heidelberg, Germany, Kaoshiung, Taiwan, R.O.C., 2014), pp. 126–140
B. Poettering, Breaking the confidentiality of OCB2. Cryptology ePrint Archive, Report 2018/1087 (2018), https://eprint.iacr.org/2018/1087
B. Poettering, P. Rösler, Combiners for AEAD. IACR Trans. Symm. Cryptol. 2020(1), 121–143 (2020), https://doi.org/10.13154/tosc.v2020.i1.121-143
P. Rogaway, Authenticated-encryption with associated-data, in Atluri, V. (ed.) ACM CCS 2002, Nov 18–22 (ACM Press, Washington, DC, USA, 2002), pp. 98–107
P. Rogaway, Efficient instantiations of tweakable blockciphers and refinements to modes OCB and PMAC, in Lee, P.J. (ed.) ASIACRYPT 2004. LNCS, vol. 3329, Dec 5–9 (Springer, Heidelberg, Germany, Jeju Island, Korea, 2004), pp. 16–31
P., Rogaway, Efficient Instantiations of Tweakable Blockciphers and Refinements to Modes OCB and PMAC. Full version of [35] (2004), http://www.cs.ucdavis.edu/~rogaway/papers/
P. Rogaway, Nonce-based symmetric encryption, in Roy, B.K., Meier, W. (eds.) FSE 2004. LNCS, vol. 3017, Feb 5–7 (Springer, Heidelberg, Germany, New Delhi, India, 2004), pp. 348–359
P. Rogaway, On the Role Definitions in and Beyond Cryptography, in Maher M.J. (ed.) Advances in Computer Science - ASIAN 2004. Higher-Level Decision Making. ASIAN 2004. Lecture Notes in Computer Science, vol. 3321, (Springer, Berlin, Heidelberg, 2004)
P. Rogaway, M. Bellare, J. Black, T. Krovetz, OCB: A block-cipher mode of operation for efficient authenticated encryption, in Reiter, M.K., Samarati, P. (eds.) ACM CCS 2001, Nov 5–8 (ACM Press, Philadelphia, PA, USA, 2001), pp. 196–205
Y. Sasaki, Y. Todo, K. Aoki, Y. Naito, T. Sugawara, Y. Murakami, M. Matsui, S. Hirose, Minalpher (A submission to CAESAR), https://info.isl.ntt.co.jp/crypt/minalpher/files/minalpherv11.pdf
W. Schroé, B. Mennink, E. Andreeva, B. Preneel, Forgery and subkey recovery on CAESAR candidate iFeed, in Dunkelman, O., Keliher, L. (eds.) SAC 2015. LNCS, vol. 9566, Aug 12–14 (Springer, Heidelberg, Germany, Sackville, NB, Canada, 2016), pp. 197–204
Z. Sun, P. Wang, L. Zhang, Collision attacks on variant of OCB mode and its series, in Inscrypt. LNCS, vol. 7763 (Springer, 2012), pp. 216–224
S. Vaudenay, D. Vizár, Can Caesar beat Galois? - Robustness of CAESAR candidates against nonce reusing and high data complexity attacks, in Preneel, B., Vercauteren, F. (eds.) ACNS 18. LNCS, vol. 10892, Jul 2–4 (Springer, Heidelberg, Germany, Leuven, Belgium, 2018), pp. 476–494
Acknowledgements
The authors would like to thank Phil Rogaway for his response to our findings. We further thank officials of ISO SC 27, in particular Chris Mitchell, for feedback and suggestions. We also would like to thank the reviewers of the Journal of Cryptology, and the reviewers of CRYPTO 2019, for their useful comments and thorough reviews. We further appreciate the comments of Eamonn Postlethwaite on an early version of this article.
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by Serge Vaudenay
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
A preliminary version of this article was presented at CRYPTO 2019 [15] (https://doi.org/10.1007/978-3-030-26948-7_1). The full version is available at [16] (https://eprint.iacr.org/2019/311).
Appendices
A. Brief History of This Paper
A frequent question we have received is how we came to find the flaws, and how they lead to the devastating attacks. The current article is based on three prior ones [17, 21, 32] that appeared in late 2018 on the IACR ePrint archive. That OCB2 might be flawed was first identified by the authors of [17] when they re-examined the proofs of OCB2 for educational purposes and searched for potential improvements. Instead, they came to find a seemingly tiny crack in the proof that they first tried to fix as they strongly believed OCB2 was a secure design, but after several tries they ended up with existential and (near-)universal forgeries. Only two weeks after these findings became public (in [17]), the author of the second ePrint article [32] announced an IND-CCA vulnerability and first steps toward plaintext recovery, and again three days later, the author of the third ePrint article [21] announced full plaintext recovery. This series of happenings is a good example of “attacks only get better” and how seemingly minor error conditions can rapidly grow to nullify the security of a renowned scheme.
B. Left-Out Details of OCB2
We complete our OCB2 description from Sect. 3 by specifying the details of the PMAC and \(\texttt {len}\) functions. For the former, see Fig. 15. The latter takes a string \(X\in \{0,1\}^{\le n}\) and encodes its lengths |X| as per \(\texttt {len}(X)=0^{n-8}\Vert \ell _X\), where \(\ell _X\) denotes the standard binary encoding of |X|. For example, \(\texttt {len}(0^n)\) for \(n=128\) is \(0^{120}10^7\).
C. Proof of OCB2f
We first prove the privacy bound. Let \( \mathbf{Adv} ^{ \textsf {cpa}}_{\mathbb {PMAC}_{\widetilde{{\textsf {P}}}}, {\textsf {R}}}(\mathcal{A})\) denote the PRF advantage of \(\mathbb {PMAC}_{\widetilde{{\textsf {P}}}}\) for CPA-adversary \(\mathcal{A}\). Rog04 showed that it is bounded by \({0.5q^2}/{2^n}\) for \(\mathcal{A}\) with q queries. Then, we have
for \(\mathcal{B}\) and \(\mathcal{C}\) using \(\sigma _{\text {priv}}\) CPA queries. Here, the first inequality follows from the fact that possible tweak values of \({\text {XE}}\) and \({\text {XEX}}\) in \({\text {OCB2f}}\) are distinct and \(\mathcal{A}\) is tag-respecting. The last inequality follows from (7) and the aforementioned bound of \(\mathbb {PMAC}\), and that the last term of (9) is zero as well as \(\mathrm {\Theta }\text {CB2}\) as shown by Rog04.
For the authenticity bound, we have
for \(\mathcal{B}_\pm \) using \(\sigma _{\text {auth}}\) CCA queries and \(\mathcal{C}_\pm \) using \(\sigma _{\text {auth}}\) CPA queries. Here, the first inequality follows from the same reason as the case of privacy bound, and the second follows from an improved CCA bound of \({\text {XEX}}^*\) [30] and \(\mathbb {PMAC}\) bound.
All that remains is to prove that \( \mathbf{Adv} ^{ \textsf {auth}}_{\mathrm {\Theta }\text {CB2f}'_{\widetilde{{\textsf {P}}}}}({\mathcal {A}}_\pm )\) (the last term of (10)) is at most \(q_v(2/2^n + 2/2^\tau )\). We first prove the case of \(q_v=1\). Let \((N_i, A_i, M_i, C_i, T_i)\) for \(i=1,\ldots ,q\) be the tuples obtained by q encryption queries and let \((N', A', C', T')\) be the decryption query. Let \(T^{*}\) denote the valid tag corresponding to \((N', A', C')\). Without loss of generality, we assume the decryption query is made after all the encryption queries. We need to consider the following cases for \((N', A', C', T')\).
-
1.
\(N' \notin \{N_{1}, \ldots , N_{q}\}\)
Since the tag (\(T^*\)) computation is done by TURP taking a new tweak, \(T^{*}\) is completely random. Thus, the forging probability is \(1/2^{\tau }\).
-
2.
\(1\le \exists \alpha \le q\), \(N' = N_{\alpha }\), \(C' = C_\alpha \), \(A' \ne A_{\alpha }\)
Let \(|C'|_n = |C_\alpha |_n = m_c\). We have subcases:
-
(a)
Let \(A'=\varepsilon \) and \(A_{\alpha } \ne \varepsilon \). Then,
$$\begin{aligned} T^{*} = \texttt {msb}_{\tau }(\widetilde{{\textsf {P}}}^{*, 0, N_{\alpha }, m_c, 1}(\Sigma _{\alpha })) = T_{\alpha } \oplus \texttt {msb}_{\tau }({\textsf {R}}(A_{\alpha })) \end{aligned}$$holds. The adversary has to guess \(\texttt {msb}_{\tau }({\textsf {R}}(A_{\alpha }))\) to forge \(T^{*}\). Thus, the forging probability is \(1/2^{\tau }\).
-
(b)
Let \(A'\ne \varepsilon \), \(A' = A_{j}\) for some \(j \in \{1, \ldots , q\}\) and \(A_{j} \ne A_{\alpha }\). We have
$$\begin{aligned} T^{*}&= \texttt {msb}_{\tau }(\widetilde{{\textsf {P}}}^{*, 0, N_{\alpha }, m_c, 1}(\Sigma _{\alpha }) \oplus {\textsf {R}}(A_{j})). \end{aligned}$$To correctly guess \(T^{*}\), the adversary needs to guess \(\texttt {msb}_{\tau }({\textsf {R}}(A_{j}))\), thus the forging probability is \(1/2^{\tau }\).
-
(c)
Let \(A'\ne \varepsilon \) and \(A'\notin \{A_{1}, \ldots , A_{q}\}\). We have
$$\begin{aligned} T^{*}&= \texttt {msb}_{\tau }(\widetilde{{\textsf {P}}}^{*, 0, N_{\alpha }, m_c, 1}(\Sigma _{\alpha }) \oplus {\textsf {R}}(A')). \end{aligned}$$The same as (b): the adversary needs to guess \(\texttt {msb}_{\tau }({\textsf {R}}(A'))\), thus the forging probability is \(1/2^{\tau }\).
-
(a)
-
3.
\(1\le \exists \alpha \le q\), \(N' = N_{\alpha }\), \(C' \ne C_\alpha \), \(|C'|_n = |C_\alpha |_n = m_c\)
In this case, the adversary learns \(T_{\alpha }=\texttt {msb}_{\tau }(\widetilde{{\textsf {P}}}^{*, 0, N', m_c, 1}(\Sigma _{\alpha }) \oplus {\textsf {R}}(A_{\alpha }))\) from encryption queries. The TURP \(\widetilde{{\textsf {P}}}^{*, 0, N', m_c, 1}\) is invoked again at the decryption query to produce \(T^*\). The case \(A' \ne A_{\alpha }\) can be analyzed in the same way as Case 2. Thus, we assume \(A' = A_{\alpha }\) in this case. Let \(\Sigma ^{*}\) and \(M^{*}\) denote the valid values of the checksum and plaintext corresponding to \((N', C')\). We define \(Z_{\alpha } :=(N_\alpha , A_\alpha , M_\alpha , C_\alpha , T_\alpha )\), and we can bound the forging probability as follows:
$$\begin{aligned} {\mathrm{Pr}}[T' = T^{*} | Z_{\alpha }] \le {\mathrm{Pr}}[T' = T^{*} | \Sigma ^{*}\ne \Sigma _\alpha , Z_\alpha ] + {\mathrm{Pr}}[\Sigma ^{*}=\Sigma _\alpha | Z_{\alpha }] \end{aligned}$$(11)-
(a)
For \(1 \le \exists i \le m_c\) and \(\forall j \in \{1, \ldots , m_c\} \setminus \{i\}\), we assume \(C'[i] \ne C_{\alpha }[i]\), \(C'[j] = C_{\alpha }[j]\). We obtain \(\Sigma ^{*} \ne \Sigma _{\alpha }\) because \(M^{*}[i]\ne M_{\alpha }[i]\) holds, and \(M^{*}[j]=M_{\alpha }[j]\) holds for all \(j \in \{1, \ldots , m_c\} \setminus \{i\}\). From (11), we obtain the forging probability as follows.
$$\begin{aligned} {\mathrm{Pr}}[T'=T^{*}|Z_{\alpha }]&\le {\mathrm{Pr}}[T' = T^{*} | \Sigma ^{*}\ne \Sigma _\alpha , Z_\alpha ] + {\mathrm{Pr}}[\Sigma ^{*}=\Sigma _\alpha | Z_{\alpha }]\\&\le \frac{2^{n-\tau }}{2^n-1} \le \frac{2}{2^\tau }. \end{aligned}$$ -
(b)
For \(1 \le \exists i < \exists j \le m_c\), we assume \(C'[i] \ne C_{\alpha }[i]\) and \(C'[j] \ne C_{\alpha }[j]\). We also define \(\Delta M[i] := M^{*}[i] \oplus M_{\alpha }[i] \ne 0^n\) and \(\Delta M[j] := M^{*}[j] \oplus M_{\alpha }[j] \ne 0^n\). As described above, we have
$$\begin{aligned}&{\mathrm{Pr}}[T'=T^{*}|Z_{\alpha }] \\&\le {\mathrm{Pr}}[T' = T^{*} | \Sigma ^{*}\ne \Sigma _\alpha , Z_\alpha ] + {\mathrm{Pr}}[\Sigma ^{*}=\Sigma _\alpha | Z_{\alpha }],\\&\le {\mathrm{Pr}}[T' = T^{*} | \Sigma ^{*}\ne \Sigma _\alpha , Z_\alpha ] + \max _{\forall \delta \in \{0, 1\}^n} {\mathrm{Pr}}[\Delta M[i] \oplus \Delta M[j] = \delta | Z_{\alpha }],\\&\le \frac{2^{n-\tau }}{2^n-1} + \frac{1}{2^n-1} = \frac{2^{n-\tau }+1}{2^n-1} \le \frac{2}{2^\tau } + \frac{2}{2^n}. \end{aligned}$$
-
(a)
-
4.
\(N' = N_{\alpha }\), \(C' \ne C_\alpha \), \(|C'|_n < |C_\alpha |_n\)
Let \(|C'|_n = m_{c'}\) and \(|C_\alpha |_n = m_{c}\). In this case, unlike \(\mathrm {\Theta }\text {CB2}\), \(\widetilde{{\textsf {P}}}^{*,1,N',m_{c'},0}\) is invoked to decrypt \(C'[m_{c'}]\), while \(\widetilde{{\textsf {P}}}^{*,1,N',m_{c'},0}\) is also used in an encryption query. Since the adversary knows \(\widetilde{{\textsf {P}}}^{*,1,N',m_{c'},0}(M_{\alpha }[m_{c'}])\), she can manipulate the last block of plaintext \(M^{*}[m_{c'}]\) if \(M_{\alpha }[m_{c'}] = \texttt {len}(C'[m_{c'}])\). Then, she can control the value of \(\Sigma ^{*}\). Nevertheless, she has to guess \(T^{*}\) without access to \(\widetilde{{\textsf {P}}}^{*,0,N',m_{c'},1}\), which has never been invoked in encryption, since \(m_{c'} \ne m_c\). Therefore, the forging probability is \(1/2^{\tau }\).
-
5.
\(N' = N_{\alpha }\), \(C' \ne C_\alpha \), \(|C'|_n > |C_\alpha |_n\)
As above, the forging probability is \(1/2^{\tau }\).
From these five cases, the bound is \({2}/{2^\tau } + {2}/{2^n}\) for \(q_v=1\). Finally, we apply the standard conversion from single to multiple decryption queries [5] and obtain the bound \(q_v\left( {2}/{2^\tau } + {2}/{2^n}\right) \) for \(q_v\ge 1\). This concludes the proof. \(\square \)
D. Proof of OCB2ff
For the privacy bound, we have
for \(\mathcal{B}\) and \(\mathcal{C}\) using \(\sigma _{\text {priv}}\) CPA queries. Here, the first inequality follows since possible tweak values of \({\text {XE}}\) and \({\text {XEX}}\) in \({\text {OCB2ff}}\) are distinct and \(\mathcal{A}\) is tag-respecting. The last inequality follows from (7) and the bound of \(\mathbb {PMAC}\), and the last term of (12) is zero with the same reasoning as \(\mathrm {\Theta }\text {CB2}\) shown by Rog04.
For the authenticity bound, we have
for \(\mathcal{B}_\pm \) using \(\sigma _{\text {auth}}\) CCA queries and \(\mathcal{C}_\pm \) using \(\sigma _{\text {auth}}\) CPA queries. Note that the algorithm of \({\Theta }\text {CB2ff}'\) is obtained by replacing \(\mathbb {PMAC}\) of \({\Theta }\text {CB2ff}\) with a URF \({\textsf {R}}\).
Then, the first inequality follows from the same reason as the case of privacy bound, and the second follows from an improved CCA bound of \({\text {XEX}}^*\) [30] and \(\mathbb {PMAC}\) bound.
It remains is to prove that \( \mathbf{Adv} ^{ \textsf {auth}}_{{\Theta }\text {CB2ff}'_{\widetilde{{\textsf {P}}}}}({\mathcal {A}}_\pm )\) (the last term of (13)) is at most \(q_v(2/2^n + 2/2^\tau )\).
We first prove the case of \(q_v=1\). We use the same case analysis as \({\Theta }\text {CB2f}\).
-
1.
\(N' \notin \{N_{1}, \ldots , N_{q}\}\)
Since the tag (\(T^*\)) computation is done by TURP taking a new tweak, \(T^{*}\) is completely random. Thus, the forging probability is \(1/2^{\tau }\).
-
2.
\(1\le \exists \alpha \le q\), \(N' = N_{\alpha }\), \(C' = C_\alpha \), \(A' \ne A_{\alpha }\)
Let \(|C'|_n = |C_\alpha |_n = m_c\). The analysis of this case is almost the same as that of Case 2 in Appendix C except for the indices of tweaks. We have subcases:
-
(a)
Let \(A'=\varepsilon \) and \(A_{\alpha } \ne \varepsilon \). Then,
$$\begin{aligned} T^{*} = \texttt {msb}_{\tau }(\widetilde{{\textsf {P}}}^{*, 0, N_{\alpha }, m_c-1, 1, 1}(\Sigma _{\alpha })) = T_{\alpha } \oplus \texttt {msb}_{\tau }({\textsf {R}}(A_{\alpha })) \end{aligned}$$holds. The adversary has to guess \(\texttt {msb}_{\tau }({\textsf {R}}(A_{\alpha }))\) to forge \(T^{*}\). Thus, the forging probability is \(1/2^{\tau }\).
-
(b)
Let \(A'\ne \varepsilon \), \(A' = A_{j}\) for some \(j \in \{1, \ldots , q\}\) and \(A_{j} \ne A_{\alpha }\). We have
$$\begin{aligned} T^{*}&= \texttt {msb}_{\tau }(\widetilde{{\textsf {P}}}^{*, 0, N_{\alpha }, m_c-1, 1, 1}(\Sigma _{\alpha }) \oplus {\textsf {R}}(A_{j})). \end{aligned}$$To correctly guess \(T^{*}\), the adversary needs to guess \(\texttt {msb}_{\tau }({\textsf {R}}(A_{j}))\), thus the forging probability is \(1/2^{\tau }\).
-
(c)
Let \(A'\ne \varepsilon \) and \(A'\notin \{A_{1}, \ldots , A_{q}\}\). We have
$$\begin{aligned} T^{*}&= \texttt {msb}_{\tau }(\widetilde{{\textsf {P}}}^{*, 0, N_{\alpha }, m_c-1, 1, 1}(\Sigma _{\alpha }) \oplus {\textsf {R}}(A')). \end{aligned}$$The same as (b): the adversary needs to guess \(\texttt {msb}_{\tau }({\textsf {R}}(A'))\), thus the forging probability is \(1/2^{\tau }\).
-
(a)
-
3.
\(1\le \exists \alpha \le q\), \(N' = N_{\alpha }\), \(C' \ne C_\alpha \), \(|C'|_n = |C_\alpha |_n = m_c\)
The analysis of this case is exactly the same as that of Case 3 in Appendix C. Thus, the forging probability can be evaluated as \(2/2^\tau + 2/2^n\).
-
4.
\(N' = N_{\alpha }\), \(C' \ne C_\alpha \), \(|C'|_n < |C_\alpha |_n\)
Let \(|C'|_n = m_{c'}\) and \(|C_\alpha |_n = m_{c}\). In the proof of \({\Theta }\text {CB2f}\), we had to take care of the fact that the adversary can control the last block of \(M^{*}\) because the last block of \(C'\) is decrypted by TURP which has been invoked in the \(\alpha \)-th encryption query. In the case of \({\Theta }\text {CB2ff}\), however, we do not have to care such a case since TURP to decrypt \(C'[m_{c'}]\) takes a new tweak and the adversary cannot control \(M^{*}[m_{c'}]\) at all. Moreover, she has no information about \(\widetilde{{\textsf {P}}}^{*, 1, N', m_{c'}-1, 1, 1}\) which produces \(T^{*}\), since \(m_{c'} \ne m_{c}\). Therefore, the forging probability is \(1/2^{\tau }\).
-
5.
\(N' = N_{\alpha }\), \(C' \ne C_\alpha \), \(|C'|_n > |C_\alpha |_n\) As above, the forging probability is \(1/2^{\tau }\).
From these five cases, the bound is \({2}/{2^\tau } + {2}/{2^n}\) for \(q_v=1\). Finally, we apply the standard conversion from single to multiple decryption queries [5] and obtain the bound \(q_v\left( {2}/{2^\tau } + {2}/{2^n}\right) \) for \(q_v\ge 1\). This concludes the proof. \(\square \)
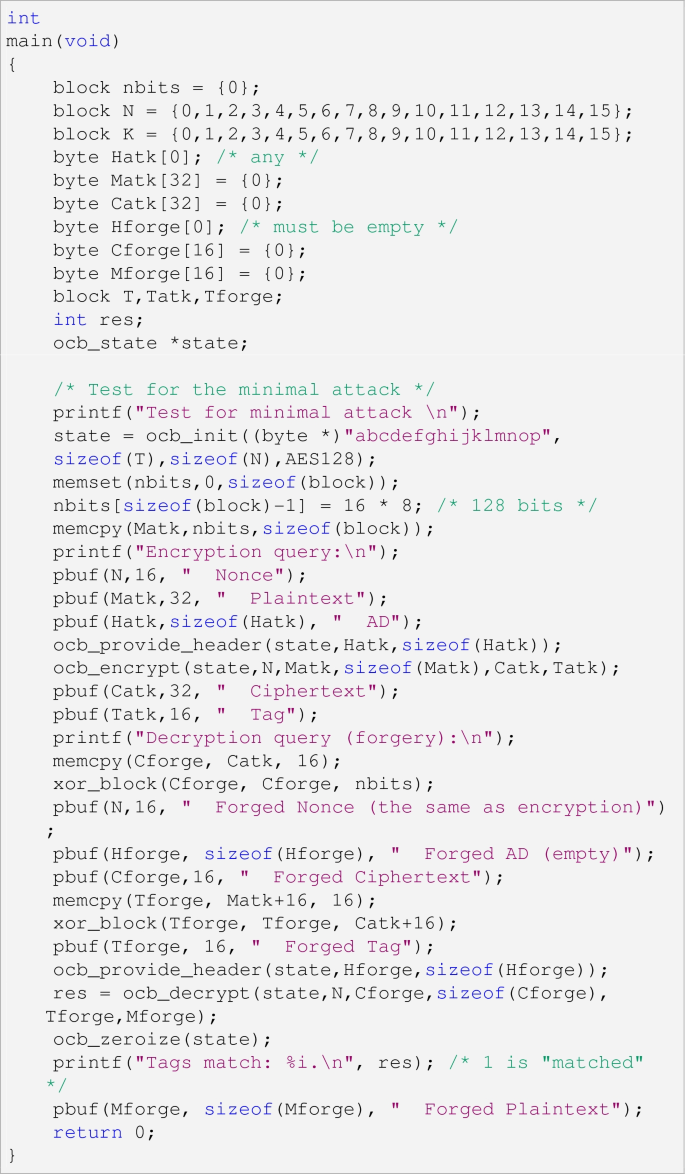
E. Code Example for Minimal Forgery Attack
-
1.
Retrieve OCB2 reference code from http://web.cs.ucdavis.edu/~rogaway/ocb/code-2.0.htm and AES reference code (rijndael-alg-fst.c).
-
2.
Change the \(\texttt {main}\) routine of ocb.c to the following snippet:
Rights and permissions
About this article
Cite this article
Inoue, A., Iwata, T., Minematsu, K. et al. Cryptanalysis of OCB2: Attacks on Authenticity and Confidentiality. J Cryptol 33, 1871–1913 (2020). https://doi.org/10.1007/s00145-020-09359-8
Received:
Revised:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00145-020-09359-8






