Abstract
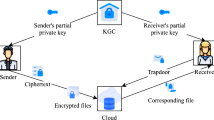
Nowadays, users prefer to encrypt their sensitive data before outsourcing it to the cloud. although, performing the encryption assures the data privacy, but it jeopardizes the search functionality. Public key encryption with keyword search (PEKS) is a potential solution for addressing this problem. However, most PEKS schemes are either inefficient, or susceptible to some type of attack(s) (i.e. inside keyword guessing attack, outside keyword guessing attack, ...etc.). Therefore, we propose a sustainable certificateless authenticated encryption system with keyword search scheme. To the best of our knowledge, the proposed scheme considers the multi-trapdoor indistinguishability in the certificateless primitive. Moreover, a thorough security analysis shows that our scheme also guarantees the security against both online and offline keyword guessing attacks. Finally, based on the performance analysis results, we find that the suggested scheme is efficient and outperforms the other schemes.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
If a scheme guarantees the multi-trapdoor indistinguishability (MT-IND), then this implies that the scheme also guarantees trapdoor indistinguishability (TD-IND).
- 2.
We execute each operation 10000 times, collect the timing of each execution, then we calculate the average of the running time.
References
Boneh, D., Di Crescenzo, G., Ostrovsky, R., Persiano, G.: Public key encryption with keyword search. In: Cachin, C., Camenisch, J.L. (eds.) EUROCRYPT 2004. LNCS, vol. 3027, pp. 506–522. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-540-24676-3_30
Baek, J., Safavi-Naini, R., Susilo, W.: Public key encryption with keyword search revisited. In: Gervasi, O., Murgante, B., Laganà, A., Taniar, D., Mun, Y., Gavrilova, M.L. (eds.) ICCSA 2008. LNCS, vol. 5072, pp. 1249–1259. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-69839-5_96
Byun, J.W., Rhee, H.S., Park, H.-A., Lee, D.H.: Off-line keyword guessing attacks on recent keyword search schemes over encrypted data. In: Jonker, W., Petković, M. (eds.) SDM 2006. LNCS, vol. 4165, pp. 75–83. Springer, Heidelberg (2006). https://doi.org/10.1007/11844662_6
Rhee, H.S., Park, J.H., Susilo, W., Lee, D.H.: Trapdoor security in a searchable public-key encryption scheme with a designated tester. J. Syst. Softw. 83, 763–771 (2010). https://doi.org/10.1016/J.JSS.2009.11.726
Ma, S., Huang, Q., Zhang, M., Yang, B.: Efficient public key encryption with equality test supporting flexible authorization. IEEE Trans. Inf. Forensics Secur. 10, 458–470 (2015). https://doi.org/10.1109/TIFS.2014.2378592
Fang, L., Susilo, W., Ge, C., Wang, J.: Public key encryption with keyword search secure against keyword guessing attacks without random oracle. Inf. Sci. 238, 221–241 (2013). https://doi.org/10.1016/J.INS.2013.03.008
Peng, Y., Cui, J., Peng, C., Ying, Z.: Certificateless public key encryption with keyword search. China Commun. 11, 100–113 (2014). https://doi.org/10.1109/CC.2014.7004528
Wu, T.Y., Meng, F., Chen, C.M., Liu, S., Pan, J.S.: On the security of a certificateless searchable public key encryption scheme. Adv. Intell. Syst. Comput. 536, 113–119 (2016). https://doi.org/10.1007/978-3-319-48490-7_14
Senouci, M.R., Benkhaddra, I., Senouci, A., Li, F.: An efficient and secure certificateless searchable encryption scheme against keyword guessing attacks. J. Syst. Archit. 119, 102271 (2021). https://doi.org/10.1016/J.SYSARC.2021.102271
Huang, Q., Li, H.: An efficient public-key searchable encryption scheme secure against inside keyword guessing attacks. Inf. Sci. 403–404, 1–14 (2017). https://doi.org/10.1016/J.INS.2017.03.038
Wu, L., Zhang, Y., Ma, M., Kumar, N., He, D.: Certificateless searchable public key authenticated encryption with designated tester for cloud-assisted medical internet of things. Annales des Telecommunications/Ann. Telecommun. 74, 423–434 (2019). https://doi.org/10.1007/S12243-018-00701-7
He, D., Ma, M., Zeadally, S., Kumar, N., Liang, K.: Certificateless public key authenticated encryption with keyword search for industrial internet of things. IEEE Trans. Ind. Inform. 14, 3618–3627 (2018). https://doi.org/10.1109/TII.2017.2771382
Zhang, Y.L., Wen, L., Zhang, Y.J., Wang, C.F.: Deniably authenticated searchable encryption scheme based on blockchain for medical image data sharing. Multimed. Tools Appl. 79, 27075–27090 (2020). https://doi.org/10.1007/S11042-020-09213-W
Ma, M., He, D., Khan, M.K., Chen, J. Certificateless searchable public key encryption scheme for mobile healthcare system. Comput. Electr. Eng. 65, 413–424 (2018). https://doi.org/10.1016/J.COMPELECENG.2017.05.014
Wu, B., Wang, C., Yao, H.: Security analysis and secure channel-free certificateless searchable public key authenticated encryption for a cloud-based internet of things. PLOS ONE 15, e0230722 (2020). https://doi.org/10.1371/JOURNAL.PONE.0230722
Qin, B., Chen, Y., Huang, Q., Liu, X., Zheng, D.: Public-key authenticated encryption with keyword search revisited: Security model and constructions. Inf. Sci. 516, 515–528 (2020). https://doi.org/10.1016/J.INS.2019.12.063
Yang, G., Guo, J., Han, L., Liu, X., Tian, C.: An improved secure certificateless public-key searchable encryption scheme with multi-trapdoor privacy. Peer-to-Peer Network. Appl. 15, 503–515 (2022). https://doi.org/10.1007/S12083-021-01253-9
Senouci, M.R., Benkhaddra, I., Senouci, A., Li, F.: A provably secure free-pairing certificateless searchable encryption scheme. Telecommun. Syst. (2022). https://doi.org/10.1007/s11235-022-00912-3
Al-Riyami, S.S., Paterson, K.G.: Certificateless public key cryptography. In: Laih, C.-S. (ed.) ASIACRYPT 2003. LNCS, vol. 2894, pp. 452–473. Springer, Heidelberg (2003). https://doi.org/10.1007/978-3-540-40061-5_29
PBC library - pairing-based cryptography. https://crypto.stanford.edu/pbc/
Keylength - NIST report on cryptographic key length and cryptoperiod (2020). https://www.keylength.com/en/4/
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Senouci, M.R., Senouci, A., Li, F. (2024). A Pairing-Based Certificateless Authenticated Searchable Encryption with MTI Guarantees. In: Yang, H., Lu, R. (eds) Frontiers in Cyber Security. FCS 2023. Communications in Computer and Information Science, vol 1992. Springer, Singapore. https://doi.org/10.1007/978-981-99-9331-4_29
Download citation
DOI: https://doi.org/10.1007/978-981-99-9331-4_29
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-99-9330-7
Online ISBN: 978-981-99-9331-4
eBook Packages: Computer ScienceComputer Science (R0)