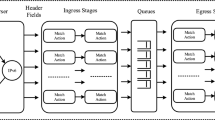
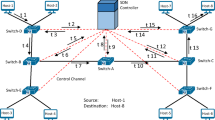
Abstract
In Software-defined network (SDN), the switching devices on the data plane rely on the flow entries issued by controllers to forward packets. Therefore, the correctness of flow entries becomes critical. However, the lack of security mechanism in SDN architecture makes the packet forwarding on the data plane easy to be damaged by malicious flow entries. In this paper, we argue that a malicious controller can easily issue malicious flow entries to hinder packets from being forwarded correctly on the data plane. We present a scheme based on P4 to detect and locate malicious flow entries on the data plane. Moreover, we implement the prototype of our scheme and extensive experiments to show that the proposed scheme can prevent malicious flow entries from damaging the packet forwarding of the data plane with trivial overheads.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Bosshart, P., et al.: P4: programming protocol-independent packet processors. Comput. Commun. Rev. 44(3), 87–95 (2014)
de Castro, M.O.T.: Practical Byzantine fault tolerance. Ph.D. thesis, Massachusetts Institute of Technology, Cambridge, MA, USA (2000)
Comer, D. (ed.): Internetworking with TCP/IP - Principles, Protocols, and Architectures, 4th edn. Prentice-Hall, Upper Saddle River (2000)
Defrawy, K.E., Kaczmarek, T.: Byzantine fault tolerant software-defined networking (SDN) controllers. In: 40th IEEE Annual Computer Software and Applications Conference, COMPSAC Workshops 2016, Atlanta, GA, USA, pp. 208–213 (2016)
Hill, J., Aloserij, M., Grosso, P.: Tracking network flows with P4. In: Proceedings of the 5th IEEE/ACM International Workshop on Innovating the Network for Data-Intensive Science, Dallas, TX, USA, 11 November 2018, pp. 23–32 (2018)
Jin, X., Gossels, J., Rexford, J., Walker, D.: Covisor: a compositional hypervisor for software-defined networks. In: 12th USENIX Symposium on Networked Systems Design and Implementation, NSDI 2015, Oakland, CA, USA, pp. 87–101 (2015)
Khurshid, A., Zhou, W., Caesar, M., Godfrey, B.: Veriflow: verifying network-wide invariants in real time. In: Proceedings of the First Workshop on Hot Topics in Software Defined Networks, HotSDN@SIGCOMM 2012, Helsinki, Finland, pp. 49–54 (2012)
Kreutz, D., Ramos, F.M.V., Veríssimo, P.J.E., Rothenberg, C.E., Azodolmolky, S., Uhlig, S.: Software-defined networking: a comprehensive survey. Proc. IEEE 103(1), 14–76 (2015)
Li, H., Li, P., Guo, S., Nayak, A.: Byzantine-resilient secure software-defined networks with multiple controllers in cloud. IEEE Trans. Cloud Comput. 2(4), 436–447 (2014)
Li, H., Li, P., Guo, S., Yu, S.: Byzantine-resilient secure software-defined networks with multiple controllers. In: IEEE International Conference on Communications, ICC 2014, Sydney, Australia, 10–14 June 2014, pp. 695–700 (2014)
Lin, C., Li, C., Wang, K.: Setting malicious flow entries against SDN operations: attacks and countermeasures. In: IEEE Conference on Dependable and Secure Computing, DSC 2018, Kaohsiung, Taiwan, pp. 1–8 (2018)
Porras, P.A., Cheung, S., Fong, M.W., Skinner, K., Yegneswaran, V.: Securing the software defined network control layer. In: 22nd Annual Network and Distributed System Security Symposium, NDSS 2015, San Diego, California, USA (2015)
Porras, P.A., Shin, S., Yegneswaran, V., Fong, M.W., Tyson, M., Gu, G.: A security enforcement kernel for openflow networks. In: Proceedings of the First Workshop on Hot Topics in Software Defined Networks, HotSDN@SIGCOMM 2012, Helsinki, Finland, pp. 121–126 (2012)
The P4 Language Consortium: P4\(_{16}\) Language Specification. https://p4.org/p4-spec/docs/P4-16-v1.2.0.html
Wen, X., Chen, Y., Hu, C., Shi, C., Wang, Y.: Towards a secure controller platform for openflow applications. In: Proceedings of the Second ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking, HotSDN 2013, The Chinese University of Hong Kong, Hong Kong, China, pp. 171–172 (2013)
Yu, S., Guo, S., Stojmenovic, I.: Fool me if you can: mimicking attacks and anti-attacks in cyberspace. IEEE Trans. Comput. 64(1), 139–151 (2015)
Yu, S., Wang, G., Zhou, W.: Modeling malicious activities in cyber space. IEEE Netw. 29(6), 83–87 (2015)
Zhi, Y., Yang, L., Yu, S., Ma, J.: BQSV: protecting SDN controller cluster’s network topology view based on byzantine quorum system with verification function. In: Vaidya, J., Zhang, X., Li, J. (eds.) CSS 2019. LNCS, vol. 11982, pp. 73–88. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-37337-5_7
Acknowledgement
The research is partly supported by the National Key Research and Development Project (2017YFB0801805), the Science and Technology on Communication Information Security Control Laboratory under Grant No. 6142106180102 and Nation Natutal Science Foundation of China No. 62072359.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Zhi, Y., Yang, L., Yang, G., Zhang, Y. (2020). Protecting the Data Plane of SDN From Malicious Flow Entries Based on P4. In: Yu, S., Mueller, P., Qian, J. (eds) Security and Privacy in Digital Economy. SPDE 2020. Communications in Computer and Information Science, vol 1268. Springer, Singapore. https://doi.org/10.1007/978-981-15-9129-7_4
Download citation
DOI: https://doi.org/10.1007/978-981-15-9129-7_4
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-15-9128-0
Online ISBN: 978-981-15-9129-7
eBook Packages: Computer ScienceComputer Science (R0)