Abstract
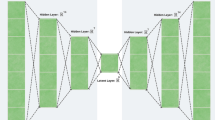
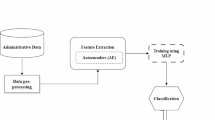
The industry 4.0 and Industrial IoT is leading new industrial revolution. Industrial IoT technologies make more reliable and sustainable products than traditional products in automation industry. Industrial IoT devices transfer data between one another. This concept is need for advanced connectivity and intelligent security services. We focus on the security threat in Industrial IoT. The general security systems enable to detect normal security threat. However, it is not easy to detect anomaly threat or network intrusion or new hacking methods. In the paper, we propose autoencoder (AE) using the deep learning based anomaly detection with invasion scoring for the smart factory environments. We have analysis F-Score and accuracy between the Density Based Spatial Clustering of Applications with Noise (DBSCAN) and the autoencoder using the KDD data set. We have used real data from Korea steel companies and the collected data is general data such as temperature, stream flow, the shocks of machines, and etc. Finally, experiments show that the proposed autoencoder model is better than DBSCAN.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Buczak, A.L., Guven, E.: A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun. Surv. Tutor. 18(2), 1153–1176 (2016)
Byres, E., Lowe, J.: The myths and facts behind cyber security risks for industrial control systems. In: Proceedings of the VDE Kongress, vol. 116 (2004)
Anderson, J.P.: Computer security threat monitoring and surveillance. Technical Report, James P. Anderson Company (1980)
Chandola, V., Banerjee, A., Kumar, V.: Anomaly detection: a survey. ACM Comput. Surv. 41(3), 15 (2009)
Mukkamala, S., Janoski, G., Sung, A.: Intrusion detection using neural networks and support vector machines. In: 2002 Proceedings of the 2002 International Joint Conference on Neural Networks, IJCNN 2002, vol. 2. IEEE (2002)
Tsai, C.-F., et al.: Intrusion detection by machine learning: a review. Expert Syst. Appl. 36(10), 11994–12000 (2009)
An, J., Cho, S.: Variational autoencoder based anomaly detection using reconstruction probability. SNU Data Mining Center, Technical Report (2015)
Shone, N., et al.: A deep learning approach to network intrusion detection. IEEE Trans. Emerg. Top. Comput. Intell. 2(1), 41–50 (2018)
Hinton, G.E., Salakhutdinov, R.R.: Reducing the dimensionality of data with neural networks. Science 313(5786), 504–507 (2006)
KDD Cup 1999. http://kdd.ics.uci.edu/databases/kddcup99/kddcup99.html. Accessed October 2007
Lippmann, R., Haines, Joshua W., Fried, David J., Korba, J., Das, K.: Analysis and results of the 1999 DARPA off-line intrusion detection evaluation. In: Debar, H., Mé, L., Wu, Felix (eds.) RAID 2000. LNCS, vol. 1907, pp. 162–182. Springer, Heidelberg (2000). https://doi.org/10.1007/3-540-39945-3_11
Olusola, A.A., Oladele, A.S., Abosede, D.O.: Analysis of KDD ’99 intrusion detection dataset for selection of relevance features. In: Proceedings of the World Congress on Engineering and Computer Science, vol. 1. (2010)
Özgür, A., Erdem, H.: A review of KDD99 dataset usage in intrusion detection and machine learning between 2010 and 2015. PeerJ PrePrints (2016)
Fawcett, T.: An introduction to ROC analysis. Pattern Recogn. Lett. 27(8), 861–874 (2006)
Abadi, M., et al.: TensorFlow: large-scale machine learning on heterogeneous systems, 2015. tensorflow.org. Accessed 21 Nov 2016
Acknowledgment
This work was supported by the Technology development Program (S2521883) funded by the Ministry of SMEs and Startups (MSS, Korea).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Bae, G., Jang, S., Kim, M., Joe, I. (2019). Autoencoder-Based on Anomaly Detection with Intrusion Scoring for Smart Factory Environments. In: Park, J., Shen, H., Sung, Y., Tian, H. (eds) Parallel and Distributed Computing, Applications and Technologies. PDCAT 2018. Communications in Computer and Information Science, vol 931. Springer, Singapore. https://doi.org/10.1007/978-981-13-5907-1_44
Download citation
DOI: https://doi.org/10.1007/978-981-13-5907-1_44
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-13-5906-4
Online ISBN: 978-981-13-5907-1
eBook Packages: Computer ScienceComputer Science (R0)