Abstract
To avoid multiple number of registrations using multiple passwords and smart-cards, many two-factor multi-server authentication protocols based on RSA have been proposed. However, most of the existing RSA-based multi-server authentication protocols are susceptible to various security attacks, and have high computation complexities. Recently, Amin et al. proposed a two-factor RSA-based robust authentication system for multi-server environments. However, we found that Amin et al.’s protocol cannot resist common modulus attack. To enhance the security, we propose a secure two-factor RSA-based authentication protocol for multi-server environments. The performance and security features of our scheme are also compared with that of the similar existing schemes. The performance and security analysis show that our protocol achieves more security features and has lower computation complexity in comparison with the latest related schemes.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
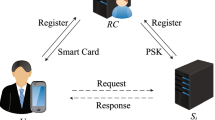
User authentication scheme is essential for implementing the secure communication because it can provide mutual authentication. Two-factor authentication protocols are widely used to ensure secure communication between the remote client and the server. It is a critical task to design a secure and robust two-factor authentication protocols. To ensure the security of client-server communication in single server environment, many authentication protocols using RSA cryptosystem [1,2,3], hash function [1, 4, 5], chaotic map [6, 7] and elliptic curve [8] have been proposed. However, most of these protocols cannot be used in multi-server environments. To address the issue, many authentication protocols for multiple server environments have been designed. The multi-server communications contain three entities: the registration center, the users and multiple application-servers. All the users and application-servers must register themselves to the registration center. The responsibility of application-servers is to provide remote services for the users.
One of the most important aspects in authentication protocol is user anonymity [9, 10]. The adversary shouldn’t obtain user’s identity in many application areas such as wireless sensor network [11], medical system and banking, where the adversary cannot guess or extract user’s identity in the phase of login and authentication.
1.1 Related Work
To achieve strong security as well as lower complexities, the researchers have designed a lot of authentication protocols for multiple servers environments. Liao et al. [12] designed a authentication protocol for multi-server environments. Unfortunately, Hsiang et al. [13] showed that Liao et al.’s protocol cannot withstand several common attacks, and then they improved the identified weaknesses. However, Lee et al. [14] demonstrated that Hsiang et al.’s scheme also have some security issues. To solve these problems, they designed an efficient and enhanced authentication protocol. Unfortunately, Troung et al. [15] demonstrated that their scheme cannot withstand user impersonation and smart-card stolen attacks. To overcome these problems, they designed a secure authentication protocol in [15]. Further, Sood et al. [16] demonstrated that Hsiang et al.’s protocol [13] had different security weaknesses and put forwarded a new authentication protocol. Subsequently, Li et al. [17] showed that Sood et al.’s protocol cannot resist smart-card stolen attack and proposed a new protocol.
Recently, Pippal et al. [18] put forward a new user authentication protocol and claimed that their protocol could resist known attacks. However, He et al. [19] showed that their protocol cannot withstand impersonation attacks. In 2015, Giri et al. [2] put forward a secure protocol based on RSA and showed that their protocol could resist known attacks. Unfortunately, Amin and Biswas [1] pointed out that Giri et al.’s protocol could not against several security attacks, and then they devised a new protocol. However, Arshad et al. [20] demonstrated that [1] was not secure and proposed a new RSA-based authentication protocol.
1.2 Our Contributions
We put forward a secure and efficient two-factor authentication protocol based on RSA signature. Our major contributions are summarized as follows:
-
Firstly, we analyse Amin et al.’s scheme [21] and prove it cannot withstand the common modulus attack.
-
Secondly, we put forward a secure and efficient two-factor authentication protocol using RSA signature for multi-server environment. The new scheme can resist against various attacks.
-
Finally, we analyse the security of our scheme and demonstrate that it is provably secure. Moreover, the performance analysis shows that our scheme is better in terms of communication overheads and computation.
1.3 Organization of the Article
The organization of this paper are described as follows: Sect. 2 analyzes the security problems of [21] and then a secure and efficient two-factor authentication protocol using RSA signature for multi-server environments are proposed in Sect. 3. Section 4 elaborates the security of the new scheme briefly. Furthermore, the comparison with some relevant protocols for efficiency and security are presented Sect. 5. Finally, we draw a conclusion.
2 Security Analysis of Amin et al.’s Scheme
In this section, we analyze the security of [21]. From our analysis, their scheme is insecure against common modulus attack. We present a list of symbols used throughout this article in Table 1. The details are described as follows:
Any of the application server can extract a public key \( e_{j2} \) and it’s public/private key pair \( \left( e_{j1}, d_{j1} \right) \). All the application servers share the public modulu \( \phi \left( n \right) \), where \( n = p *q \), \( \phi \left( n \right) = \left( p-1 \right) \left( q-1 \right) \). It can computes \( e_{j1}d_{j1}\equiv 1\) mod \(\phi \left( n \right) \), \( e_{j1}d_{j1} - 1 = k \phi \left( n \right) \), \( \phi \left( n \right) \mid e_{j1}d_{j1} - 1 \). It can computes \( \left( e_{j1}d_{j1} - 1,e_{j2} \right) = s \) using euclidean algorithm. If \( s = 1 \), there exist some f, g such that \( f\left( e_{j1}d_{j1} - 1 \right) + ge_{j2} = 1 \). So the value of g is the private key corresponding to \( e_{j2} \). If \( s\ne 1 \), suppose that \( t = e_{j1}d_{j1} - 1 / s \), \( \left( e_{j1}d_{j1} - 1 / s, e_{j2} \right) = 1 \). There exist some f, g such that \( ft + ge_{j2} = 1 \) using extended euclidean algorithm. Therefore, \( ge_{j2} \equiv 1\) mod \(\phi \left( n \right) \), the value of g is the private key corresponding to \( e_{j2} \).
Suppose that the adversary dispatches the same message m whose encryption exponents respectively are \(e_{j1} \) and \(e_{j2} \). Suppose further that \( gcd\left( e_{j1}, e_{j2} \right) = 1 \), it can computes \( c_{1} = m^{e_{j1}} \) mod n, \( c_{2} = m^{e_{j2}} \) mod n. There exist some r, s such that \(re_{j1} + se_{j2} = 1 \), \( m = m^{re_{j1} + se_{j2}} = \left( m^{e_{j1}} \right) ^{r}\left( m^{e_{j2}} \right) ^{s} = c_{1}^{r}c_{2}^{s} \) mod n. Therefore, the adversary can get the value of m using \( c_{1}, c_{2}, r, s \).
3 Proposed Protocol
We put forward a secure authentication system for multi-server environment which can withstand the above mentioned security issues. Our scheme consists of three phases: application-server registration phase, user registration phase, verification phase.
3.1 Application-Server Registration Phase
-
\( AS_{j} \) selects two large prime numbers p, q, and computes \( n_{j} = p_{j} \times q_{j} \), \( \phi \left( n_{j} \right) =\left( p_{j}-1 \right) \left( q_{j}-1 \right) \).
-
\( AS_{j} \) chooses a public key \( e_{j} \) \( \left( 1<e_{j}<\phi \left( n_{j} \right) \right) \), where \( gcd\left( \phi \left( n_{j} \right) , e_{j}\right) = 1 \). Then, it computes it’s private key \( d_{j} \equiv e_{j}^{-1} \) mod \(\phi \left( n_{j} \right) \).
-
Finally, \( AS_{j} \) chooses his/her identity \( ID_{j} \) and sends \( \left\langle e_{j}, n_{j}, ID_{j} \right\rangle \) to RC securely.
-
RC computes \( Cer_{j} = h\left( e_{j} \left| \right| ID_{j}\left| \right| n_{j} \right) ^{d} \) and sends \( Cer_{j} \) to \( AS_{j} \).
3.2 User Registration Phase
-
\( U_{i} \) chooses his/her identity \(ID_{i} \) and sends it to RC.
-
After receiving \( \left\langle ID_{i} \right\rangle \), RC computes \( d_{i} = h\left( ID_{i} \right) ^{d} \) mod \( n_{j} \).
-
RC sends \( d_{i} \) to \( U_{i} \) securely.
3.3 Authentication Phase
-
\( U_{i} \) randomly selects a number \( T_{i} \), then it sends \( T_{i} \) to \( AS_{j} \).
-
After receiving \( T_{i} \), \( AS_{j} \) computes \( A_{j} = h\left( T_{i} \right) ^{d_{j}} \). Then, it sends \( \left\langle e_{j}, n_{j},\right. \left. Cer_{j}, A_{j} \right\rangle \) to \( U_{i} \).
-
Upon receiving the message, \( U_{i} \) checks whether \( Cer_{j}^{e} \) mod \( n_{j} = h\left( ID_{j}\right. \left. \left| \right| e_{j}\left| \right| n_{j} \right) \) and \( A_{j}^{e_{j}} = h\left( T_{i} \right) \). If holds, \( U_{i} \) authenticates \( AS_{j} \).
-
\( U_{i} \) chooses three random number \( a_{i}, r, m \) and computes \( PID_{i} = \left( ID_{i} \oplus a_{i} \left| \right| a_{i} \right) ^{e_{j}} \) mod \( n_{j} \), \( R_{i} = h\left( PID_{i} \right) ^{r} \) mod \( n_{j} \), \( x = h\left( m, R_{i} \right) \) and \(S_{i} = d_{i}^{r-x} \). Then, \( U_{i} \) sends \( \left\langle PID_{i}, R_{i}, S_{i}, x \right\rangle \) to \( AS_{j} \).
-
After receiving the message, \( AS_{j} \) computes \( S_{i}^{e_{j}} = h\left( ID_{i} \right) ^{r-x} \), \( PID_{i}^{d_{j}} \) mod \( n_{j} = ID_{i} \oplus a_{i} \left| \right| a_{i} \), \( ID_{i}^{'} = ID_{i} \oplus a_{i} \left| \right| a_{i} \). Then, it checks whether \( S_{i}^{e_{j}}h\left( ID_{i}^{'} \right) ^{x} = R_{i} \). If holds, \( AS_{j} \) authenticates \( U_{i} \).
4 Security Analysis
4.1 Security Proof
In this subsection, according to the formal security model described as [22], we show our protocol is secure as follows.
Theorem 1
If has advantage \( Adv_{P}^{ake}\left( A \right) \) against our scheme running in time \( q_{send} \) Send queries, \( q_{exe} \) Execute queries and \( q_{h} \) Hash queries. Define the security length l and the password space |D|. Then, we can attain: \( Adv_{P}^{ake} \le \frac{q_{h}^{2}}{2^{l-1}} + \frac{\left( q_{send}+q_{exe} \right) ^{2} }{p} + 2q_{h}\cdot Adv_{G}^{DLP}\left( t \right) + \frac{q_{send}}{2^{l-2}} + \frac{2q_{send}}{|D|} \), where \( Adv_{G}^{DLP}\left( t \right) \) denote the probabilistic polynomial time t to breach DLP problem.
Proof: C obtains \( \left( y, g, n \right) \) and intends to compute x satisfying \( g^{x} = y \) mod n using the PPT turingmachine A. C utilizes the hash function as a random oracle and maintains an empty \( H-list \). We define \( G_{i} \) as the sequence of games and \( Suc_{i} \) as A gets b successfully.
Game \( G_{0}\): This game corresponds to the real attack, we have \( Adv_{P}^{ake}\left( A \right) = 2Pr[Suc_{0}] - 1 \).
Game \( G_{1}\): In this game, we imitate the hash oracles \( h\left( \cdot \right) \) by maintaining hash list \( L_{h} \) and the Execute, Reveal, Send, Corrupt and Test oracles are simulated as real attacks (see Figs. 1 and 2). Therefore, we have \(Pr[Suc_{1}] = Pr[Suc_{0}] \).
Game \( G_{2}\): In this game, we imitate all oracles as previous games, except that we will halt all executions under the condition: A collision occurs in the transcript \( \left\langle e_{j}, n_{j}, Cer_{j}, A_{j} \right\rangle \), \( \left\langle PID_{i}, R_{i}, S_{i}, x \right\rangle \). According to the birthday paradox, the probability of the hash oracle collisions is \( \frac{q_{h}^{2}}{2^{l+1}} \). The probability of the transcripts colisions is \( \frac{\left( q_{send}+q_{exe} \right) ^{2} }{2p} \).
Game \( G_{3}\): In this game, we simulate all oracles as previous games, except that we will cancel all executions where in the adversary guess the authentication parameters \( A_{j} \) and \( R_{i} \) without making hash query. Therefore, we have \( Pr\left[ Suc_{3}\right] - Pr \left[ Suc_{2} \right] \le \frac{q_{send}}{2^{l}}\).
Game \( G_{4}\): In this game, we imitate all oracles under the condition that the adversary guess the parameter \( h\left( T_{i} \right) \) successfully without making the related queries. We define \( k = h\left( T_{i} \right) \) to imitate this game.
-
\( AS_{j}\): Search for \( (*,k) \) in \( L_{h} \). This game will be terminated if the information does not exist. Otherwise, compute \( A_{j} = k^{d_{j}} \).
-
\( U_{i}\): Computes \( A_{j}^{e_{j}} \) and checks whether \( A_{j}^{e_{j}} = h\left( T_{i} \right) \). If holds, \( U_{i} \) search for \( \left\langle e_{j}, n_{j}, Cer_{j}, A_{j} \right\rangle \) in the send list.
If A guess the parameter k successfully without making hash quries, this game will succeed. Therefore, we have \( Pr\left[ Suc_{3}\right] - Pr \left[ Suc_{2} \right] \le \frac{q_{send}}{2^{l}} \).
Game \( G_{5}\): We design this game to imitate Discrete logarithm problem. The security of our protocol depends on the Discrete logarithm problem solely: \( R_{i} = h\left( PID_{i} \right) ^{r} \) mod \( n^{j} \).
-
\( U_{i}\): Chooses two random numbers \( a_{i} \) and r. Then calculates: \( PID_{i} = \left( ID_{i} \oplus a_{i} \left| \right| a_{i} \right) ^{e_{j}} \) mod \( n_{j} \), \( S_{i} = d_{i}^{r-x} \). Finally, stores \( \left\{ S_{i}, x \right\} \) into hash list.
-
\( AS_{j}\): Calculates \( S_{i}^{e_{j}} = h\left( ID_{i} \right) ^{r-x} \), \( PID_{i}^{d_{j}} \) mod \( n_{j} = ID_{i} \oplus a_{i} \left| \right| a_{i} \), \( ID_{i}^{'} = ID_{i} \oplus a_{i} \left| \right| a_{i} \). Then stores \( \left\{ S_{i}^{e_{j}}, h\left( ID_{i} \right) ^{x} \right\} \) into hash list.
This game is different from previous games where in the adversary quries \( h\left( \cdot \right) \) on \( g^{x} = y \) mod n. We can obtain DLP secret with \( \frac{1}{q_{h}} \). Hence, we have \( Pr \left[ Suc_{5} \right] - Pr \left[ Suc_{4} \right] \le q_{h}\cdot Adv_{G}^{DLP}\left( t \right) \).
Game \( G_{6}\): In this game, we simulate all oracles as in game \( G_{5} \), except that we will abort the Test query in which A asks a \( h\left( \cdot \right) \) for \( g^{x} = y \) mod n. The probability that A gets the session key is \( \frac{q_{h}^{2}}{2^{l+1}} \). Therefore, we have \( Pr\left[ Suc_{5}\right] - Pr\left[ Suc_{4}\right] \le \frac{q_{h}^{2}}{2^{l+1}} \).
In addition, the probability of off-line dictionary attacks is \( \frac{q_{send}}{|D|} \). Therefore, we can get the conclusion showed in the beginning of this subsection.
4.2 Other Discussions
This subsection shows our scheme is able to withstand various attacks.
-
User impersonation attack: To impersonate as a legal \( U_{i} \), A has to compute a valid message \( \left\langle PID_{i}, R_{i}, S_{i}, x \right\rangle \) during authentication phase, where \( PID_{i} = \left( ID_{i} \oplus a_{i} \left| \right| a_{i} \right) \) mod \( n_{j} \), \( R_{i} = h\left( PID_{i} \right) ^{r} \) mod \( n_{j} \), \( x = h\left( m, R_{i} \right) \) and \(S_{i} = d_{i}^{r-x} \). However, it is infeasible to compute \( PID_{i} \) and \( R_{i} \) without knowing the random number \( a_{i} \) and r. Therefore, our proposed scheme can withstand user impersonation attack.
-
Server impersonation attack: To impersonate as a legal application-server, A has to compute the message \( \left\langle e_{j}, n_{j}, Cer_{j}, A_{j} \right\rangle \), which is to be authenticated by \( U_{i} \), where \( A_{j} = h\left( T_{i} \right) ^{d_{j}} \) and \( Cer_{j} = h\left( e_{j}\left| \right| ID_{j}\left| \right| n_{j} \right) ^{d} \). However, it is infeasible to compute \( A_{j} \) and \( Cer_{j} \) without knowing the private key d of RC. Therefore, our proposed scheme can withstand server impersonation attack.
-
User anonymity: Our proposed scheme can provide anonymity of users. Taking the situation where an adversary can get the message \( d_{i} \), where \( d_{i} = h\left( ID_{i} \right) ^{d} \) mod \( n_{j} \). However, d cannot be known by the adversary. The adversary may also eavesdrop the information \( \left\langle PID_{i}, R_{i}, S_{i}, x \right\rangle \), where \( PID_{i} \) are related to the user’s identity and \( PID_{i} = \left( ID_{i} \oplus a_{i} \left| \right| a_{i} \right) ^{d_{j}} \). As the random \( a_{i} \) cannot be known by the adversary, it is impossible to get the user’s identity from \( PID_{i} \). Therefore, our proposed scheme can provide anonymity of users.
-
Common modulus attacks: In our proposed scheme, the public key and private key of \( AS_{j} \) are generated by the server itself. \( AS_{j} \) computes \( n_{j} = p_{j} \times q_{j} \), \( \phi \left( n_{j} \right) =\left( p_{j}-1 \right) \left( q_{j}-1 \right) \). The modulu of \( n_{j} \) is not same in every application server and the application servers does not share the public modulu. Therefore, our proposed scheme can withstand Common modulus attack.
-
Mutual authentication: In our proposed scheme, \( AS_{j} \) and \( U_{i} \) authenticate each other. \( U_{i} \) authenticates \( AS_{j} \) by checking whether \( Cer_{j}^{e} \) mod \( n_{j} = h\left( ID_{j}\left| \right| e_{j}\left| \right| n_{j} \right) \) and \( A_{j}^{e_{j}} = h\left( T_{i} \right) \). A needs to get \( T_{i} \) to reconstruct \( A_{j} \), however, only a legal \( AS_{j} \) owns the value. \( AS_{j} \) authenticates \( U_{i} \) by checking whether \( S_{i}^{e_{j}}h\left( ID_{i}^{'} \right) ^{x} = R_{i} \). A needs to compute \( PID_{i} \) and r to reconstruct \( R_{i} \), however, only a legal \( U_{i} \) can compute those values. Therefore, \( U_{i} \) and \( AS_{j} \) mutually authenticate and our proposed scheme can provide proper mutual authentication.
-
Smart-card stolen attack: An adversary A can extract the information of smart-card by means of power consumption monitoring technique. Suppose that A obtains the smart card of \( U_{i} \) and extracts the information \( \left\langle d_{i} \right\rangle \), where \( d_{i} = h\left( ID_{i} \right) ^{d_{j}} \) mod \( n_{j} \). From the value, A cannot compute any useful information, because the value is safeguarded with a one-way hash function. Further, A cannot obtain the value of \( d_{j} \). Therefore, our proposed scheme can withstand smart card stolen attacks.
5 Performance Analysis
In this section, we compare the proposed scheme with recent authentication schemes [18, 21, 23,24,25] proposed in terms of security and performance (as shown in Table 2). We use some time complexities to evaluate the computational cost. \( T_{h} \) denotes the cost time for one-way hash operation. \( T_{sym} \) denotes the execution time for symmetric key encryption/decryption operation. \( T_{e} \) denotes the running time for exponentiation operation. \( T_{m} \) denotes the execution time for modular multiplication operation.
We have implemented various cryptographic operations with the MIRACL C/C++ Library [26] on a personal computer with 4G bytes memory and the Windows 7 operating system. It requires Visual C++ 2008, 1024-bit cyclic group, AES for symmetric encryption/decryption, 160-bit prime field \( F_{p} \) and SHA-1 operation. The execution time of these different operations are: 0.0004 ms, 0.1303 ms, 0.0147 ms and 1.8269 ms.
In Table 1, we find that our proposed scheme can withstand known attacks, such as user anonymity, common modulus attacks, mutual authentication, Server impersonation attack. In Tables 3 and 4, we find that computational cost time of our proposed scheme is lower than the schemes in [18, 23] and nearly equal with the schemes in [21, 24, 25].
6 Conclusion
In this paper, we cryptanalyzed Amin et al.’s scheme, and found that their protocol is susceptible to common modulus attack. Then We present a secure and efficient two-factor authentication protocol using RSA signature for multi-server environments. We prove informally that our protocol can withstand different cryptographic attacks. In the proposed scheme, we employ RSA signature to implement the authentication scheme. Our proposed scheme is suitable for deployment in various low-power smart cards, and in particular for the mobile computing networks.
References
Amin, R., Biswas, G.P.: An improved RSA based user authentication and session key agreement protocol usable in TMIS. J. Med. Syst. 39(8), 1–14 (2015)
Giri, D., Maitra, T., Amin, R., Srivastava, P.D.: An efficient and robust RSA-based remote user authentication for telecare medical information systems. J. Med. Syst. 39(1), 1–9 (2015)
Amin, R., Biswas, G.P.: Remote access control mechanism using rabin public key cryptosystem. In: Mandal, J.K., Satapathy, S.C., Sanyal, M.K., Sarkar, P.P., Mukhopadhyay, A. (eds.) Information Systems Design and Intelligent Applications. AISC, vol. 339, pp. 525–533. Springer, New Delhi (2015). https://doi.org/10.1007/978-81-322-2250-7_52
Amin, R., Biswas, G.P.: Cryptanalysis and design of a three-party authenticated key exchange protocol using smart card. Arab. J. Sci. Eng. 40(11), 1–15 (2015)
Islam, S.K.H., Biswas, G.P., Choo, K.K.R.: Cryptanalysis of an improved smartcard-based remote password authentication scheme. Inf. Sci. Lett. 3(1), 35 (2014)
Hafizul Islam, S.K., Khan, M.K., Obaidat, M.S., Bin Muhaya, F.T.: Provably secure and anonymous password authentication protocol for roaming service in global mobility networks using extended chaotic maps. Wirel. Pers. Commun. 84(3), 1–22 (2015)
Hafizul Islam, S.K.: Design and analysis of a three party password-based authenticated key exchange protocol using extended chaotic maps. Inf. Sci. Int. J. 312(C), 104–130 (2015)
Amin, R., Biswas, G.P.: A secure three-factor user authentication and key agreement protocol for TMIS with user anonymity. J. Med. Syst. 39(8), 1–19 (2015)
Hafizul Islam, S.K.: Design and analysis of an improved smartcard-based remote user password authentication scheme. Int. J. Commun. Syst. 29(11), 1708–1719 (2016)
Hafizul Islam, S.K.: A provably secure id-based mutual authentication and key agreement scheme for mobile multi-server environment without ESL attack. Wirel. Pers. Commun. 79(3), 1975–1991 (2014)
Amin, R., Biswas, G.P.: A secure light weight scheme for user authentication and key agreement in multi-gateway based wireless sensor networks. Ad Hoc Netw. 36, 58–80 (2016)
Liao, Y.-P., Wang, S.-S.: A secure dynamic ID based remote user authentication scheme for multi-server environment. Comput. Stand. Interfaces 31(1), 24–29 (2009)
Hsiang, H.-C., Shih, W.-K.: Improvement of the secure dynamic ID based remote user authentication scheme for multi-server environment. Comput. Stand. Interfaces 31(6), 1118–1123 (2009)
Lee, C.-C., Lin, T.-H., Chang, R.-X.: A secure dynamic ID based remote user authentication scheme for multi-server environment using smart cards. Expert Syst. Appl. 38(11), 13863–13870 (2011)
Truong, T.-T., Tran, M.-T., Duong, A.-D.: Robust secure dynamic ID based remote user authentication scheme for multi-server environment. In: Murgante, B., Misra, S., Carlini, M., Torre, C.M., Nguyen, H.-Q., Taniar, D., Apduhan, B.O., Gervasi, O. (eds.) ICCSA 2013. LNCS, vol. 7975, pp. 502–515. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-39640-3_37
Sood, S.K., Sarje, A.K., Singh, K.: A secure dynamic identity based authentication protocol for multi-server architecture. J. Netw. Comput. Appl. 34(2), 609–618 (2011)
Li, X., Xiong, Y., Ma, J., Wang, W.: An efficient and security dynamic identity based authentication protocol for multi-server architecture using smart cards. J. Netw. Comput. Appl. 35(2), 763–769 (2012)
Pippal, R.S., Jaidhar, C.D., Tapaswi, S.: Robust smart card authentication scheme for multi-server architecture. Wirel. Pers. Commun. 72(1), 729–745 (2013)
He, D., Chen, J., Shi, W., Khan, M.K.: On the security of an authentication scheme for multi-server architecture. Int. J. Electr. Secur. Digit. Forensics 5(3/4), 288–296 (2013)
Arshad, H., Rasoolzadegan, A.: Design of a secure authentication and key agreement scheme preserving user privacy usable in telecare medicine information systems. J. Med. Syst. 40(11), 237 (2016)
Amin, R., Islam, S.K., Khan, M.K., et al.: A two-factor RSA-based robust authentication system for multiserver environments. Secur. Commun. Netw. 2017, 15 p. (2017). Article no. 5989151
Ding, W., Ping, W.: Two birds with one stone: two-factor authentication with security beyond conventional bound. IEEE Trans. Dependable Secure Comput. PP(99), 1 (2016)
Yeh, K.-H.: A provably secure multi-server based authentication scheme. Wirel. Pers. Commun. 79(3), 1621–1634 (2014)
Wei, J., Liu, W., Hu, X.: Cryptanalysis and improvement of a robust smart card authentication scheme for multi-server architecture. Wirel. Pers. Commun. 77(3), 2255–2269 (2014)
Li, X., Niu, J., Kumari, S., Liao, J., Liang, W.: An enhancement of a smart card authentication scheme for multi-server architecture. Wirel. Pers. Commun. Int. J. 80(1), 175–192 (2015)
Lili, X., Fan, W.: Cryptanalysis and improvement of a user authentication scheme preserving uniqueness and anonymity for connected health care. J. Med. Syst. 39(2), 10 (2015)
Acknowledgements
The work of was supported by the National Natural Science Foundation of China (Nos. 61501333, 61572379, 61572370, 61772377), and the Natural Science Foundation of Hubei Province of China (Nos. 2015CFA068, 2017CFA007).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2018 Springer International Publishing AG, part of Springer Nature
About this paper
Cite this paper
Xu, Z., He, D., Huang, X. (2018). Secure and Efficient Two-Factor Authentication Protocol Using RSA Signature for Multi-server Environments. In: Qing, S., Mitchell, C., Chen, L., Liu, D. (eds) Information and Communications Security. ICICS 2017. Lecture Notes in Computer Science(), vol 10631. Springer, Cham. https://doi.org/10.1007/978-3-319-89500-0_51
Download citation
DOI: https://doi.org/10.1007/978-3-319-89500-0_51
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-89499-7
Online ISBN: 978-3-319-89500-0
eBook Packages: Computer ScienceComputer Science (R0)