Abstract
We study the Double Coverage (DC) algorithm for the k-server problem in the (h, k)-setting, i.e. when DC with k servers is compared against an offline optimum algorithm with \(h \le k\) servers. It is well-known that DC is k-competitive for \(h=k\). We prove that even if \(k>h\) the competitive ratio of DC does not improve; in fact, it increases up to \(h+1\) as k grows. In particular, we show matching upper and lower bounds of \(\frac{k(h+1)}{k+1}\) on the competitive ratio of DC on any tree metric.
Supported by NWO grant 639.022.211, ERC consolidator grant 617951, NCN grant DEC-2013/09/B/ST6/01538,NSF grants CCF-1115575, CNS-1253218, CCF-1421508, and an IBM Faculty Award.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
Actually [5] shows a slightly stronger upper bound WFA\(_k \le 2h\)OPT\(_h - \)OPT\(_k + \text{ const }\) where OPT\(_k\) and OPT\(_h\) are the optimal cost using k and h servers respectively.
- 2.
If the online algorithm knows h, it can simply disable its \(k-h\) extra servers and be \(2h-1\) competitive (which is slightly better than 2h). However, Koutsoupias (and also us) consider the setting where the online algorithm does not know h.
- 3.
Here, we view the uniform metric as a star graph where requests appear to the leaves. A proof of this result will be given in the full version of the paper.
- 4.
- 5.
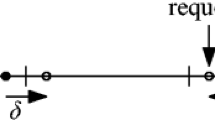
Consider the instance where all servers are at \(x=0\) initially. A request arrives at \(x=2\), upon which both DC and offline move a server there and pay 2. Then a request arrives at \(x=1\). DC moves both servers there and pays 2 while offline pays 1. All servers are now at \(x=1\) and the instance repeats.
- 6.
We remark that this property does not hold (simultaneously) for every offline server, but only for a single fixed offline server y.
References
Bartal, Y., Koutsoupias, E.: On the competitive ratio of the work function algorithm for the k-server problem. Theor. Comput. Sci. 324(2–3), 337–345 (2004)
Borodin, A., El-Yaniv, R.: Online Computation and Competitive Analysis. Cambridge University Press, Cambridge (1998)
Chrobak, M., Karloff, H.J., Payne, T.H., Vishwanathan, S.: New results on server problems. SIAM J. Discrete Math. 4(2), 172–181 (1991)
Chrobak, M., Larmore, L.L.: An optimal on-line algorithm for k-servers on trees. SIAM J. Comput. 20(1), 144–148 (1991)
Koutsoupias, E.: Weak adversaries for the k-server problem. In: Proceedings of the 40th Symposium on Foundations of Computer Science (FOCS), pp. 444–449 (1999)
Koutsoupias, E., Papadimitriou, C.H.: On the k-server conjecture. J. ACM 42(5), 971–983 (1995)
Manasse, M.S., McGeoch, L.A., Sleator, D.D.: Competitive algorithms for server problems. J. ACM 11(2), 208–230 (1990)
Sleator, D.D., Tarjan, R.E.: Amortized efficiency of list update and paging rules. Commun. ACM 28(2), 202–208 (1985)
Young, N.E.: The k-server dual and loose competitiveness for paging. Algorithmica 11(6), 525–541 (1994)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2015 Springer International Publishing Switzerland
About this paper
Cite this paper
Bansal, N., Eliáš, M., Jeż, Ł., Koumoutsos, G., Pruhs, K. (2015). Tight Bounds for Double Coverage Against Weak Adversaries. In: Sanità, L., Skutella, M. (eds) Approximation and Online Algorithms. WAOA 2015. Lecture Notes in Computer Science(), vol 9499. Springer, Cham. https://doi.org/10.1007/978-3-319-28684-6_5
Download citation
DOI: https://doi.org/10.1007/978-3-319-28684-6_5
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-28683-9
Online ISBN: 978-3-319-28684-6
eBook Packages: Computer ScienceComputer Science (R0)