Abstract
Video conferencing systems have become an indispensable part of our world. Using video conferencing systems implies the expectation that online meetings run as smoothly as in-person meetings. Thus, online meetings need to be just as secure and private as in-person meetings, which are secured against disruptive factors and unauthorized persons by physical access control mechanisms.
To show the security dangers of conferencing systems and raise general awareness when using these technologies, we analyze the security of two widely used research and education open-source video conferencing systems: BigBlueButton and eduMEET. Because both systems are very different, we analyzed their architectures, considering the respective components with their main tasks, features, and user roles. In the following systematic security analyses, we found 50 vulnerabilities. These include broken access control, NoSQL injection, and denial of service (DoS). The vulnerabilities have root causes of different natures. While BigBlueButton has a lot of complexity due to many components, eduMEET, which is relatively young, focuses more on features than security. The sheer amount of results and the lack of prior work indicate a research gap that needs to be closed since video conferencing systems continue to play a significant role in research, education, and everyday life.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
- 2.
BigBlueButton 2.4 introduces the media server mediasoup, which replaces Kurento as the default as of 2.5, with a modified media topology.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
This mainly applies to eduMEET, as it allows flexible configuration of the user roles and permissions.
- 11.
We analyzed commit bb46e2d of https://github.com/edumeet/edumeet (branch “develop”), which was later merged into eduMEET 3.5.0-beta.1.
- 12.
This is an array, containing a native JavaScript regular expression object for .*. In EJSON, it is serialized as
 .
. - 13.
- 14.
- 15.
References
8x8, Inc., Vulnerability Disclosure Program Policy (2023). https://hackerone.com/8x8
Ahmed, M.: Hacking Zoom: Uncovering Tales of Security Vulnerabilities in Zoom (2020). https://mazinahmed.net/blog/hacking-zoom/
Altpeter, B.: RCE in Jitsi Meet Electron prior to 2.3.0 due to insecure use of shell.openExternal() (CVE-2020-25019) (2020). https://benjamin-altpeter.de/jitsi-meet-electron-rce-shell-openexternal/
Anthony, T.: Zoom Security Exploit - Cracking private meeting passwords (2020). https://www.tomanthony.co.uk/blog/zoom-security-exploit-crack-private-meeting-passwords/
Thévenet, A.: France digital strategy for education supports the use of digital commons (2023). https://joinup.ec.europa.eu/collection/open-source-observatory-osor/news/france-digital-strategy-education-2
Begen, A.C., Kyzivat, P., Perkins, C., Handley, M.J.: SDP: Session Description Protocol. RFC 8866 (Proposed Standard) (2021). https://www.rfc-editor.org/rfc/rfc8866.txt
BigBlueButton. French Ministry of Education chooses BigBlueButton (2023). https://bigbluebutton.org/2023/01/11/french-ministry-of-education-chooses-bigbluebutton/
Boström, H., Jennings, C., Castelli, F., Bruaroey, J-I.: WebRTC: Real-time communication in browsers. W3C recommendation, W3C (2023). https://www.w3.org/TR/2023/REC-webrtc-20230306/
Bräunlein, F.: MS Teams: 1 feature, 4 vulnerabilities (2021). https://positive.security/blog/ms-teams-1-feature-4-vulns
Böck, H.: File Exfiltration via Libreoffice in BigBlueButton and JODConverter (2020). https://blog.hboeck.de/archives/902-File-Exfiltration-via-Libreoffice-in-BigBlueButton-and-JODConverter.html
Castillo, I.B.: mediasoup v3 Design (2020). https://mediasoup.org/documentation/v3/mediasoup/design/
Davis, R.: Zoom’s Bug Bounty Program: 2021 in Review (2022). https://blog.zoom.us/zoom-bug-bounty-program-2021/
Kasak, D., Callahan, D., Hodgson, M.: Practically-exploitable Cryptographic Vulnerabilities in Matrix (2022). https://matrix.org/blog/2021/09/13/vulnerability-disclosure-key-sharing
Fratric, I.: XMPP Stanza Smuggling or How I Hacked Zoom (2022). https://i.blackhat.com/USA-22/Thursday/US-22-Fratric-XMPP-Stanza-Smuggling.pdf
GÉANT. Build Your Own eduMEET Service (2020). https://web.archive.org/web/20200416162612/https://edumeet.org/build/
heise online. Rheinland-Pfalz: Schulen dürfen Microsoft-Software Teams nicht mehr nutzen [Rhineland-Palatinate: Schools no longer allowed to use Microsoft Teams] (2022). https://www.heise.de/news/Rheinland-Pfalz-Schulen-duerfen-Microsoft-Software-Teams-nicht-mehr-nutzen-7154309.html
Jones, M.B., Bradley, J., Sakimura, N.: JSON Web Token (JWT). RFC 7519 (Proposed Standard) (2015). https://www.rfc-editor.org/rfc/rfc7519.txt. Updated by RFCs 7797, 8725
Keegan, R.: Patched Zoom Exploit: Altering Camera Settings via Remote SQL Injection (2020). https://medium.com/@keegan.ryan/patched-zoom-exploit-altering-camera-settings-via-remote-sql-injection-4fdf3de8a0d
Kelly, S.M.: Zoom’s massive ’overnight success’ actually took nine years. CNN (2020). https://edition.cnn.com/2020/03/27/tech/zoom-app-coronavirus/index.html
Kinugawa, M.: Discord Desktop app RCE (2020). https://mksben.l0.cm/2020/10/discord-desktop-rce.html
Ling, C., Balci, U., Blackburn, J., Stringhini, G.: A first look at Zoombombing. In: 2021 IEEE Symposium on Security and Privacy (SP), pp. 1452–1467 (2021). https://ieeexplore.ieee.org/document/9638984
Marczak, B., Scott-Railton, J.: Move fast and roll your own crypto - a quick look at the confidentiality of zoom meetings (2020). https://citizenlab.ca/2020/04/move-fast-roll-your-own-crypto-a-quick-look-at-the-confidentiality-of-zoom-meetings/
Martin, T., Radzio, M., Sharma, K.: Matrix concepts (2023). https://matrix.org/docs/matrix-concepts
Albrecht, M.R., Celi, S., Dowling, B., Jones, D.: Practically-exploitable Cryptographic Vulnerabilities in Matrix (2022). https://nebuchadnezzar-megolm.github.io/static/paper.pdf
McGrew, D., Rescorla, E.: Datagram Transport Layer Security (DTLS) Extension to Establish Keys for the Secure Real-time Transport Protocol (SRTP). RFC 5764 (Proposed Standard) (2010). https://www.rfc-editor.org/rfc/rfc5764.txt. Updated by RFCs 7983, 9443
Meyer, K.: GÉANT eduMEET service launched early to support communication needs during the COVID-19 lockdown (2020). https://connect.geant.org/2020/06/16/geant-edumeet-service-launched-early-to-support-communication-needs-during-the-covid-19-lockdown
Nettleton, R.: BigBlueButton (2010). https://web.archive.org/web/20100814003302/https://edc.carleton.ca/blog/index.php/2010/06/04/bigbluebutton/
s1r1us and TheGrandPew. Remote Code Execution on Element Desktop Application using Node Integration in Sub Frames Bypass - CVE-2022-23597 (2022). https://blog.electrovolt.io/posts/element-rce/
Sakimura, N., Bradley, J., Jones, M.B., de Medeiros, B., Mortimore, C.: OpenID Connect Core 1.0. OpenID Foundation (2014). https://openid.net/specs/openid-connect-core-1_0-final.html
Schreiber, P., Hoffman-Andrews, J., Grauer, Y.: Videoconferencing Guide (2020). https://videoconferencing.guide/
Sector7. Zoom RCE from Pwn2Own 2021 (2021). https://sector7.computest.nl/post/2021-08-zoom/
Silvanovich, N.: Adventures in Video Conferencing Part 1: The Wild World of WebRTC (2018). https://googleprojectzero.blogspot.com/2018/12/adventures-in-video-conferencing-part-1.html
Silvanovich, N.: Adventures in Video Conferencing Part 2: Fun with FaceTime (2018). https://googleprojectzero.blogspot.com/2018/12/adventures-in-video-conferencing-part-2.html
Silvanovich, N.: Adventures in Video Conferencing Part 3: The Even Wilder World of WhatsApp (2018). https://googleprojectzero.blogspot.com/2018/12/adventures-in-video-conferencing-part-3.html
Silvanovich, N.: Adventures in Video Conferencing Part 4: What Didn’t Work Out with WhatsApp (2018). https://googleprojectzero.blogspot.com/2018/12/adventures-in-video-conferencing-part-4.html
Silvanovich, N.: Adventures in Video Conferencing Part 5: Where Do We Go from Here? (2018). https://googleprojectzero.blogspot.com/2018/12/adventures-in-video-conferencing-part-5.html
Silvanovich, N.: Zooming in on Zero-click Exploits (2022). https://googleprojectzero.blogspot.com//2022/01/zooming-in-on-zero-click-exploits.html
Reuters Staff. Google bans Zoom software from employee laptops. REUTERS (2020). https://www.reuters.com/article/us-google-zoom-idUSKCN21Q32V
Sudhodanan, A., Paverd, A.: Pre-hijacked accounts: an empirical study of security failures in user account creation on the web. In: Proceedings of the 31st USENIX Security Symposium (USENIX Security 2022), pp. 1795–1812, Boston, MA (2022). USENIX Association. https://www.usenix.org/conference/usenixsecurity22/presentation/sudhodanan
Thodupunoori, R.: Part-1 Dive into Zoom Applications (2021). https://rakesh-thodupunoori.medium.com/part-1-dive-into-zoom-applications-d70f3de53ec5
Thodupunoori, R.: Part 2: Dive into Zoom Applications (2021). https://rakesh-thodupunoori.medium.com/part-2-dive-into-zoom-applications-1b01091345c1
Tudor, C.: The Impact of the COVID-19 pandemic on the global web and video conferencing SaaS market. Electronics 11, 2633 (2022)
Vegeris, O.: “Important, Spoofing" - zero-click, wormable, cross-platform remote code execution in Microsoft Teams (2020). https://github.com/oskarsve/ms-teams-rce
Vela, E.: Zoom: XSS in Zoom.us Signup Flow (2020). https://github.com/google/security-research/security/advisories/GHSA-fpgp-vrmv-v8f2/
Vengattil, M., Roulette, J.: Elon Musk’s SpaceX bans Zoom over privacy concerns -memo. REUTERS (2020). https://www.reuters.com/article/us-spacex-zoom-video-commn-idUSKBN21J71H
Website of the conference of ministers of education (Kultusministerkonferenz). Digitale Lernangebote [Digital Learning Tools] (2023). https://www.kmk.org/themen/bildung-in-der-digitalen-welt/distanzlernen.html
Wittmann, L.: Visavid - Datensicherheit im Warteraum [Visavid - Data Security in the Waiting Room]. Medium (2021). https://lilithwittmann.medium.com/visavid-datensicherheit-im-warteraum-77c184c1d58a
Zoom Video Communications, Inc., Vulnerability Disclosure Policy (2021). https://www.zoomgov.com/docs/en-us/vulnerability-disclosure-policy.html
Acknowledgements
We thank our anonymous reviewers for their insightful comments and detailed suggestions. We are also grateful to Sven Hebrok for helpful discussions and contributions in the early stage of this research.
This research was funded by the PRISMA Elite Program of the Department of Computer Science of Paderborn University, and by the research project “North Rhine-Westphalian Experts in Research on Digitalization (NERD II)”, sponsored by the state of North Rhine-Westphalia – NERD II 005-2201-0014.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A Appendix
A Appendix
1.1 A.1 eduMEET
E3: Overwrite Peer Reference. This finding leads to multiple high-impact issues in eduMEET. When a user connects to a room, the server creates a JSON Web Token (JWT) [17], bound to a peer ID generated by the client. The JWT is stored on the server and referenced by a cookie-based session. When a user connects to a room, eduMEET performs two checks. First, the server checks if there is a JWT for the session and if the peer ID is already used by a connected user. The server rejects the connecting peer if the peer ID is already used, but no JWT exists. Otherwise, the server verifies the JWT, i. e., the server checks if the peer ID matches the JWT. In case of a valid JWT, the server treats the user as returning and closes the old connection.
The vulnerability stems from the fact that the server creates a new peer object regardless of whether the JWT matches the peer ID. The peer object (see Sect. 4.3) represents a meeting participant and contains, among other things, a unique peer ID, a room ID, a list of user roles, and a socket for communication. Despite the importance of the JWT validity, in the first step, the server only checks if a peer ID and a JWT exist. Therefore, the peer ID does not have to match the JWT. When an attacker connects to a room with an existing peer ID and a valid session referencing a JWT that does not match the peer ID, the server still creates a new peer object. The server keeps a list of peer objects referenced by their peer IDs. Since the peer ID exists, the server overwrites the existing peer reference. However, the old connection stays open, and the old peer can still participate in the meeting.
To perform an attack, the attacker first joins any meeting. The attacker has a valid peer ID generated by the client and a valid session from the server. The attacker now joins the targeted meeting. Instead of having their client generate a new random peer ID for this connection, the attacker chooses an existing peer ID (see below). To achieve this, they may use the browser developer tools to overwrite the JavaScript variable holding the peer ID their client generated and then join the meeting. The new peer ID does not match the attacker’s JWT anymore. The WebSocket connection of the old peer with the same peer ID is not closed but not referenced anymore. That means the old peer cannot be targeted by moderator actions (E3.2). If the new peer with the same peer ID now leaves the meeting, the UI of all participants changes, and peers with the target peer ID are not visible anymore, but the connection of the old peer is still open. The old peer is invisible in the meeting but can still participate (E3.1), for example, listen to existing streams and read the chat. To exploit the first two scenarios (E3.1 and E3.2), the attacker needs to be the old and new peer at the same time, which they can achieve using two browser instances. In the last scenario (E3.3), the attacker uses the victim’s peer ID to prevent the victim from receiving new media streams. The peer IDs of all participants are known because the server broadcasts them when joining.
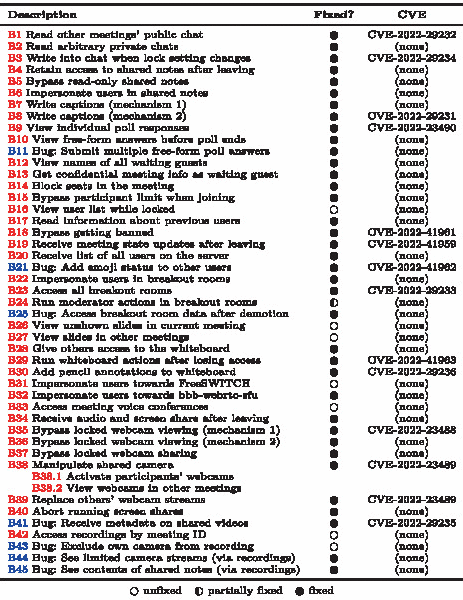
1.2 A.2 Status of Fixes in BigBlueButton
Rights and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Heitmann, N., Siewert, H., Moog, S., Somorovsky, J. (2024). Security Analysis of BigBlueButton and eduMEET. In: Pöpper, C., Batina, L. (eds) Applied Cryptography and Network Security. ACNS 2024. Lecture Notes in Computer Science, vol 14585. Springer, Cham. https://doi.org/10.1007/978-3-031-54776-8_8
Download citation
DOI: https://doi.org/10.1007/978-3-031-54776-8_8
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-54775-1
Online ISBN: 978-3-031-54776-8
eBook Packages: Computer ScienceComputer Science (R0)





 .
.