Abstract
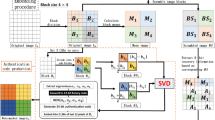
In this paper, we propose a self-embedding fragile image watermarking technique based on Singular Value Decomposition (SVD) and Discrete Cosine Transform (DCT). To improve security and robustness a novel block separation technique is presented in which an input image is divided into non-overlapping blocks and subsequently SVD is applied on each block. Entropy value of the resulting vector of singular values is measured. Mean of entropy of all blocks is considered as a threshold for deciding two sets of blocks. For the first set of blocks, Entropy measures of singular value based authentication codes are generated and for second set of blocks, DCT DC value based authentication codes are obtained for embedding information. To enhance visual quality of watermarked and recovery image DCT based watermark embedding technique is proposed. Experiments have been conducted on gray scale images and it is observed that proposed scheme gives peak signal to noise ratio (PSNR) of 58 dB which ensures high performance in terms of imperceptibility. Experimental results showed that 99% of watermarked blocks are correctly detected during recovery phase. The image tampering is precisely identified and tampered images are recovered with very good quality. To the best of our knowledge the presented fragile image watermarking scheme is superior to all existing scheme.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Walton, S.: Image authentication for a slippery new age. Dr. Dobb’s J. 20(4), 18–22 (1995)
Liu, S.H., Yao, H.X., Gao, W., Liu, Y.L.: An image fragile watermark scheme based on chaotic image pattern and pixel-pairs. Appl. Math. Comput. 185(2), 869–882 (2007)
Prasad, S., Pal, A.K.: A tamper detection suitable fragile watermarking scheme based on novel payload embedding strategy. Multimed. Tools Appl. 79(3–4), 1673–1705 (2019). https://doi.org/10.1007/s11042-019-08144-5
Prasad, S., Pal, A.K.: Hamming code and logistic-map based pixel-level active forgery detection scheme using fragile watermarking. Multimed. Tools Appl. 79(29–30), 20897–20928 (2020). https://doi.org/10.1007/s11042-020-08715-x
Prasad, S., Pal, A.K.: A secure fragile watermarking scheme for protecting integrity of digital images. Iran. J. Sci. Technol. Trans. Electr. Eng. 44(2), 703–727 (2019). https://doi.org/10.1007/s40998-019-00275-7
Dua, M., Suthar, A., Garg, A., Garg, V.: An ILM-cosine transform-based improved approach to image encryption. Complex Intell. Syst. 7(1), 327–343 (2020). https://doi.org/10.1007/s40747-020-00201-z
Nancharla, B.K., Dua, M.: An image encryption using intertwining logistic map and enhanced logistic map. In: 2020 5th International Conference on Communication and Electronics Systems (ICCES), pp. 1309–1314. IEEE (2020)
Dua, M., Wesanekar, A., Gupta, V., Bhola, M., Dua, S.: Differential evolution optimization of intertwining logistic map-DNA based image encryption technique. J. Ambient. Intell. Humaniz. Comput. 11(9), 3771–3786 (2019). https://doi.org/10.1007/s12652-019-01580-z
Gul, E., Ozturk, S.: A novel hash function based fragile watermarking method for image integrity. Multimed. Tools Appl. 78(13), 17701–17718 (2019). https://doi.org/10.1007/s11042-018-7084-0
Abdelhakim, A., Saleh, H.I., Abdelhakim, M.: Fragile watermarking for image tamper detection and localization with effective recovery capability using K-means clustering. Multimed. Tools Appl. 78(22), 32523–32563 (2019)
Singh, D., Singh, S.K.: Effective self-embedding watermarking scheme for image tampered detection and localization with recovery capability. J. Vis. Commun. Image Represent. 38, 775–789 (2016)
Singh, D., Singh, S.K.: DCT based efficient fragile watermarking scheme for image authentication and restoration. Multimed. Tools Appl. 76(1), 953–977 (2015). https://doi.org/10.1007/s11042-015-3010-x
Wang, C., Zhang, H., Zhou, X.: A self-recovery fragile image watermarking with variable watermark capacity. Appl. Sci. 8(4), 548–568 (2018)
Kim, C., Shin, D., Yang, C.-N.: Self-embedding fragile watermarking scheme to restoration of a tampered image using AMBTC. Pers. Ubiquit. Comput. 22(1), 11–22 (2017). https://doi.org/10.1007/s00779-017-1061-x
Chang, C.-C., Lin, C.-C., Su, G.-D.: An effective image self-recovery based fragile watermarking using self-adaptive weight-based compressed AMBTC. Multimed. Tools Appl. 79(33–34), 24795–24824 (2020). https://doi.org/10.1007/s11042-020-09132-w
Molina-Garcia, J., Garcia-Salgado, B.P., Ponomaryov, V., Reyes-Reyes, R., Sadovnychiy, S., Cruz-Ramos, C.: An effective fragile watermarking scheme for color image tampering detection and self-recovery. Signal Process.: Image Commun. 81, 115725 (2020). https://doi.org/10.1016/j.image.2019.115725
Shen, J.-J., Lee, C.-F., Hsu, F.-W., Agrawal, S.: A self-embedding fragile image authentication based on singular value decomposition. Multimed. Tools Appl. 79(35–36), 25969–25988 (2020). https://doi.org/10.1007/s11042-020-09254-1
Ahmadi, S.B.B., Zhang, G., Wei, S.: Robust and hybrid SVD-based image watermarking schemes. Multimed. Tools Appl. 79(1), 1075–1117 (2020)
Singh, A.K.: Improved hybrid algorithm for robust and imperceptible multiple watermarking using digital images. Multimed. Tools Appl. 76(6), 8881–8900 (2016). https://doi.org/10.1007/s11042-016-3514-z
Zear, A., Singh, A.K., Kumar, P.: A proposed secure multiple watermarking technique based on DWT, DCT and SVD for application in medicine. Multimed. Tools Appl. 77(4), 4863–4882 (2016). https://doi.org/10.1007/s11042-016-3862-8
Qi, X., Xin, X.: A singular-value-based semi-fragile watermarking scheme for image content authentication with tamper localization. J. Vis. Commun. Image Represent. 30, 312–327 (2015). https://doi.org/10.1016/j.jvcir.2015.05.006
Li, C., Zhang, A., Liu, Z., Liao, L., Huang, D.: Semi-fragile self-recoverable watermarking algorithm based on wavelet group quantization and double authentication. Multimed. Tools Appl. 74(23), 10581–10604 (2014). https://doi.org/10.1007/s11042-014-2188-7
Klema, V., Laub, A.J.: The singular value decomposition: its computation and some applications. IEEE Trans. Autom. Control 25(2), 164–176 (1980)
Botta, M., Cavagnino, D., Pomponiu, V.: Reversible fragile watermarking for multichannel images with high redundancy channels. Multimed. Tools Appl. 79(35–36), 26427–26445 (2020). https://doi.org/10.1007/s11042-020-08986-4
Hemida, O., Huo, Y., He, H., Chen, F.: A restorable fragile watermarking scheme with superior localization for both natural and text images. Multimed. Tools Appl. 78(9), 12373–12403 (2018). https://doi.org/10.1007/s11042-018-6664-3
Su, G.D., Chang, C.C., Lin, C.C.: Effective self-recovery and tampering localization fragile watermarking for medical images. IEEE Access 8, 160840–160857 (2020). https://doi.org/10.1109/ACCESS.2020.301983216
AlShehri, L., Hussain, M., Aboalsamh, H., Wadood, A.: Fragile watermarking for image authentication using BRINT and ELM. Multimed. Tools Appl. 79(39–40), 29199–29223 (2020). https://doi.org/10.1007/s11042-020-09441-0
Nejati, F., Sajedi, H., Zohourian, A.: Fragile watermarking based on QR decomposition and Fourier transform. Wirel. Pers. Commun. 122(1), 211–227 (2021). https://doi.org/10.1007/s11277-021-08895-1
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Kapre, B.S., Rajurkar, A.M., Guru, D.S. (2022). Self-embedding and Variable Authentication Approach for Fragile Image Watermarking Using SVD and DCT. In: Guru, D.S., Y. H., S.K., K., B., Agrawal, R.K., Ichino, M. (eds) Cognition and Recognition. ICCR 2021. Communications in Computer and Information Science, vol 1697. Springer, Cham. https://doi.org/10.1007/978-3-031-22405-8_29
Download citation
DOI: https://doi.org/10.1007/978-3-031-22405-8_29
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-22404-1
Online ISBN: 978-3-031-22405-8
eBook Packages: Computer ScienceComputer Science (R0)