Abstract
A Zero-Knowledge Proof (ZKP) protocol allows a participant to prove the knowledge of some secret without revealing any information about it. While such protocols are typically executed by computers, there exists a line of research proposing physical instances of ZKP protocols. Up to now, many card-based ZKP protocols for pen-and-pencil puzzles, like Sudoku, have been designed. Those games, mostly edited by Nikoli, have simple rules, yet designing them in card-based ZKP protocols is non-trivial. This is partly due to the fact that the solution should not be leaked during the protocol. In this work, we propose a card-based protocol for Usowan, a Nikoli game. In Usowan, for each room of a puzzle instance, there is exactly one piece of false information. The goal of the game is to detect this wrong data amongst the correct data and also to satisfy the other rules. Designing a card-based ZKP protocol to deal with the property of detecting a liar has never been done. In some sense, we propose a physical ZKP for hiding of a liar.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
A numbered cell whose number is four (or more) is automatically a liar. Indeed, if there are four black cells around a numbered cell, then the numbered cell cannot be connected to other white cells.
- 2.
This means that commitments used in the computation cannot be placed back with its initial value. A non-destructive protocol is called input-preserving (see Sect. 2.3).
- 3.
For a numbered cell in the edge of the board, compute the addition of its three or two neighbors.
- 4.
- 5.
Here, we do not place dummy commitments in the row above the first one and in the column right to the last one because in the expanded grid of size \((p+1)(q+1)\) the row above the first one can be regarded as the last row, i.e., dummy commitments. Thus, we do not need dummy commitments placed in the row above the first one, which also holds for the column right to the last one.
References
https://www.nikoli.co.jp/en/puzzles/usowan.html. Nikoli, Usowan
Abe, Y., Iwamoto, M., Ohta, K.: Efficient private PEZ protocols for symmetric functions. In: Hofheinz, D., Rosen, A. (eds.) TCC 2019. LNCS, vol. 11891, pp. 372–392. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-36030-6_15
Balogh, J., Csirik, J.A., Ishai, Y., Kushilevitz, E.: Private computation using a PEZ dispenser. Theor. Comput. Sci. 306(1–3), 69–84 (2003). https://doi.org/10.1016/S0304-3975(03)00210-X
Boer, B.: More efficient match-making and satisfiability The Five Card Trick. In: Quisquater, J.-J., Vandewalle, J. (eds.) EUROCRYPT 1989. LNCS, vol. 434, pp. 208–217. Springer, Heidelberg (1990). https://doi.org/10.1007/3-540-46885-4_23
Bultel, X., Dreier, J., Dumas, J., Lafourcade, P.: Physical zero-knowledge proofs for Akari, Takuzu, Kakuro and KenKen. In: Demaine, E.D., Grandoni, F. (eds.) Fun with Algorithms. LIPIcs, vol. 49, pp. 8:1–8:20. Schloss Dagstuhl, Dagstuhl (2016). https://doi.org/10.4230/LIPIcs.FUN.2016.8
Bultel, X., et al.: Physical zero-knowledge proof for Makaro. In: Izumi, T., Kuznetsov, P. (eds.) SSS 2018. LNCS, vol. 11201, pp. 111–125. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-03232-6_8
Chien, Y.-F., Hon, W.-K.: Cryptographic and physical zero-knowledge proof: from Sudoku to Nonogram. In: Boldi, P., Gargano, L. (eds.) FUN 2010. LNCS, vol. 6099, pp. 102–112. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-13122-6_12
Dreier, J., Jonker, H., Lafourcade, P.: Secure auctions without cryptography. In: Ferro, A., Luccio, F., Widmayer, P. (eds.) Fun with Algorithms. LNCS, vol. 8496, pp. 158–170. Springer, Cham (2014). https://doi.org/10.1007/978-3-319-07890-8_14
Dumas, J.G., Lafourcade, P., Miyahara, D., Mizuki, T., Sasaki, T., Sone, H.: Interactive physical zero-knowledge proof for Norinori. In: Du, D.Z., Duan, Z., Tian, C. (eds.) Computing and Combinatorics. LNCS, vol. 11653, pp. 166–177. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-26176-4_14
Goldwasser, S., Micali, S., Rackoff, C.: The knowledge complexity of interactive proof-systems. In: STOC 1985, pp. 291–304. ACM, New York (1985). https://doi.org/10.1145/22145.22178
Gradwohl, R., Naor, M., Pinkas, B., Rothblum, G.N.: Cryptographic and physical zero-knowledge proof systems for solutions of Sudoku puzzles. Theory Comput. Syst. 44(2), 245–268 (2009). https://doi.org/10.1007/s00224-008-9119-9
Isuzugawa, R., Miyahara, D., Mizuki, T.: Zero-knowledge proof protocol for Cryptarithmetic using dihedral cards. In: Kostitsyna, I., Orponen, P. (eds.) UCNC 2021. LNCS, vol. 12984, pp. 51–67. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-87993-8_4
Iwamoto, C., Haruishi, M.: Computational complexity of Usowan puzzles. IEICE Trans. Fundamentals E101.A, 1537–1540 (2018). https://doi.org/10.1587/transfun.E101.A.1537
Koch, A., Walzer, S.: Foundations for actively secure card-based cryptography. In: Farach-Colton, M., Prencipe, G., Uehara, R. (eds.) Fun with Algorithms. LIPIcs, vol. 157, pp. 17:1–17:23. Schloss Dagstuhl, Dagstuhl (2021). https://doi.org/10.4230/LIPIcs.FUN.2021.17
Lafourcade, P., Miyahara, D., Mizuki, T., Robert, L., Sasaki, T., Sone, H.: How to construct physical zero-knowledge proofs for puzzles with a “single loop” condition. Theor. Comput. Sci. 888, 41–55 (2021). https://doi.org/10.1016/j.tcs.2021.07.019
Miyahara, D., et al.: Card-based ZKP protocols for Takuzu and Juosan. In: Farach-Colton, M., Prencipe, G., Uehara, R. (eds.) Fun with Algorithms. LIPIcs, vol. 157, pp. 20:1–20:21. Schloss Dagstuhl, Dagstuhl (2021). https://doi.org/10.4230/LIPIcs.FUN.2021.20
Miyahara, D., Sasaki, T., Mizuki, T., Sone, H.: Card-based physical zero-knowledge proof for Kakuro. IEICE Trans. Fundamentals 102-A(9), 1072–1078 (2019). https://doi.org/10.1587/transfun.E102.A.1072
Mizuki, T.: Efficient and secure multiparty computations using a standard deck of playing cards. In: Foresti, S., Persiano, G. (eds.) CANS 2016. LNCS, vol. 10052, pp. 484–499. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-48965-0_29
Mizuki, T., Kugimoto, Y., Sone, H.: Secure multiparty computations using a dial lock. In: Cai, J.-Y., Cooper, S.B., Zhu, H. (eds.) TAMC 2007. LNCS, vol. 4484, pp. 499–510. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-72504-6_45
Mizuki, T., Kugimoto, Y., Sone, H.: Secure multiparty computations using the 15 puzzle. In: Dress, A., Xu, Y., Zhu, B. (eds.) COCOA 2007. LNCS, vol. 4616, pp. 255–266. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-73556-4_28
Mizuki, T., Shizuya, H.: Practical card-based cryptography. In: Fun with Algorithms. LNCS, vol. 8496, pp. 313–324. Springer, Cham (2014). https://doi.org/10.1007/978-3-319-07890-8_27
Mizuki, T., Sone, H.: Six-card secure AND and four-card secure XOR. In: Deng, X., Hopcroft, J.E., Xue, J. (eds.) FAW 2009. LNCS, vol. 5598, pp. 358–369. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-02270-8_36
Moran, T., Naor, M.: Polling with physical envelopes: a rigorous analysis of a human-centric protocol. In: Vaudenay, S. (ed.) EUROCRYPT 2006. LNCS, vol. 4004, pp. 88–108. Springer, Heidelberg (2006). https://doi.org/10.1007/11761679_7
Moran, T., Naor, M.: Split-ballot voting: everlasting privacy with distributed trust. In: Ning, P., di Vimercati, S.D.C., Syverson, P.F. (eds.) ACM Conference on Computer and Communications Security, pp. 246–255. ACM (2007). https://doi.org/10.1145/1315245.1315277
Moran, T., Naor, M.: Basing cryptographic protocols on tamper-evident seals. Theor. Comput. Sci. 411(10), 1283–1310 (2010). https://doi.org/10.1016/j.tcs.2009.10.023
Nishimura, A., Hayashi, Y., Mizuki, T., Sone, H.: Pile-shifting scramble for card-based protocols. IEICE Trans. Fundamentals 101-A(9), 1494–1502 (2018). https://doi.org/10.1587/transfun.E101.A.1494
Robert, L., Miyahara, D., Lafourcade, P., Mizuki, T.: Card-based ZKP for connectivity: applications to Nurikabe, Hitori, and Heyawake. New Gener. Comput. 40, 149–171 (2022). https://doi.org/10.1007/s00354-022-00155-5
Robert, L., Miyahara, D., Lafourcade, P., Libralesso, L., Mizuki, T.: Physical zero-knowledge proof and NP-completeness proof of Suguru puzzle. Inf. Comput. 285, 1–14 (2022). https://doi.org/10.1016/j.ic.2021.104858
Ruangwises, S.: An improved physical ZKP for nonogram. In: Du, D.-Z., Du, D., Wu, C., Xu, D. (eds.) COCOA 2021. LNCS, vol. 13135, pp. 262–272. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-92681-6_22
Ruangwises, S.: Two standard decks of playing cards are sufficient for a ZKP for sudoku. New Gen. Comput. 1–17 (2021). https://doi.org/10.1007/s00354-021-00146-y
Ruangwises, S., Itoh, T.: Physical zero-knowledge proof for numberlink puzzle and k vertex-disjoint paths problem. New Gen. Comput. 39(1), 3–17 (2020). https://doi.org/10.1007/s00354-020-00114-y
Ruangwises, S., Itoh, T.: Physical zero-knowledge proof for Ripple Effect. Theor. Comput. Sci. 895, 115–123 (2021). https://doi.org/10.1016/j.tcs.2021.09.034
Ruangwises, S., Itoh, T.: Physical ZKP for connected spanning subgraph: applications to bridges puzzle and other problems. In: Kostitsyna, I., Orponen, P. (eds.) UCNC 2021. LNCS, vol. 12984, pp. 149–163. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-87993-8_10
Ruangwises, S., Itoh, T.: Securely computing the n-variable equality function with 2n cards. Theor. Comput. Sci. 887, 99–110 (2021). https://doi.org/10.1016/j.tcs.2021.07.007
Ruangwises, S., Itoh, T.: Physical ZKP for Makaro using a standard deck of cards. In: Du, D., et al. (eds.) TAMC 2022, LNCS 13571. Springer, Cham (2022)
Sasaki, T., Miyahara, D., Mizuki, T., Sone, H.: Efficient card-based zero-knowledge proof for Sudoku. Theor. Comput. Sci. 839, 135–142 (2020). https://doi.org/10.1016/j.tcs.2020.05.036
Shinagawa, K., et al.: Secure computation protocols using polarizing cards. IEICE Trans. Fundamentals E99.A(6), 1122–1131 (2016). https://doi.org/10.1587/transfun.E99.A.1122
Shinagawa, K., et al.: Card-based protocols using regular polygon cards. IEICE Trans. Fundamentals 100-A(9), 1900–1909 (2017). https://doi.org/10.1587/transfun.E100.A.1900
Acknowledgements
We thank the anonymous referees, whose comments have helped us to improve the presentation of the paper. This work was supported in part by JSPS KAKENHI Grant Numbers JP21K11881 and JP18H05289. This study was partially supported by the French ANR project ANR-18-CE39-0019 (MobiS5). Other programs also fund to write this paper, namely the French government research program “Investissements d\({}^{\prime }\)Avenir” through the IDEX-ISITE initiative 16-IDEX-0001 (CAP 20-25) and the IMobS3 Laboratory of Excellence (ANR-10-LABX-16-01). Finally, the French ANR project DECRYPT (ANR-18-CE39-0007) and SEVERITAS (ANR-20-CE39-0009) also subsidize this work.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendices
A Mizuki–Sone Copy Protocol [22]
The protocol proceeds as follows.Footnote 4
-
1.
Turn over all face-up cards and put the commitment to a above the four additional cards as follows:

Note that black-to-red represents 0, and red-to-black represents 1 according to Eq. (2).
-
2.
Apply a pile-shifting shuffle as follows:

-
3.
Reveal the two above cards and obtain two commitments to a as follows (note that negating a commitment is easy).
-
(a)
If they are
 , then the four bottom cards are
, then the four bottom cards are
 .
. -
(b)
If they are
 , then the four bottom cards are
, then the four bottom cards are
 .
.
-
(a)
B Input-preserving Five-Card Trick [16]
The sub-protocol proceeds as follows.
-
1.
Add helping cards and swap the two cards of the commitment to a so that we have the negation \(\overline{b}\), as follows:

-
2.
Rearrange the sequence of cards and turn over the face-up cards as:

-
3.
Regarding cards in the same column as a pile, apply a pile-shifting shuffle to the sequence:

-
4.
Reveal all the cards in the above row.
-
(a)
If the resulting sequence is
 (up to cyclic shifts), then \(a\vee b=0\).
(up to cyclic shifts), then \(a\vee b=0\). -
(b)
If it is
 (up to cyclic shifts), then \(a\vee b=1\).
(up to cyclic shifts), then \(a\vee b=1\).
-
(a)
-
5.
After turning over all the face-up cards, apply a pile-shifting shuffle.
-
6.
Reveal all the cards in the bottom row; then, the revealed cards should include exactly one
 .
. -
7.
Shift the sequence of piles so that the leftmost card is the revealed
 and swap the two cards of the commitment to \(\overline{b}\) to restore commitments to a and b.
and swap the two cards of the commitment to \(\overline{b}\) to restore commitments to a and b.
C How to Form a White Polyomino
Before explaining the protocol, we need to describe two crucial sub-protocols first, namely the chosen pile protocol and the 4-neighbour protocol.
1.1 C.1 Chosen Pile Protocol [9]
This protocol allows P to choose a pile of cards without V knowing which one it is. Some operations can be done on this pile while all the commitments are replaced in their initial order.
This protocol is an extended version of the “chosen pile cut” proposed in [14]. Given m piles \(({\textbf {p}}_1,{\textbf {p}}_2,\ldots ,{\textbf {p}}_m)\) with 2m additional cards, the chosen pile protocol enables a prover P to choose the i-th pile \({\textbf {p}}_i\) (without revealing the index i) and revert the sequence of m piles to their original order after applying other operations to \(p_i\).
-
1.
Using \(m-1\)
 and one
and one
 , P places m face-down cards (denoted by row 2) below the given piles such that only the i-th card is
, P places m face-down cards (denoted by row 2) below the given piles such that only the i-th card is
 . We further put m cards (denoted by row 3) below the cards such that only the first card is
. We further put m cards (denoted by row 3) below the cards such that only the first card is
 :
: 
-
2.
Considering the cards in the same column as a pile, apply a pile-shifting shuffle to the sequence of piles.
-
3.
Reveal all the cards in row 2. Then, exactly one
 appears, and the pile above the revealed
appears, and the pile above the revealed
 is the i-th pile (thus P can obtain \({\textbf {p}}_i\)). After this step is invoked, other operations are applied to the chosen pile. Then, the chosen pile is placed back to the i-th position in the sequence.
is the i-th pile (thus P can obtain \({\textbf {p}}_i\)). After this step is invoked, other operations are applied to the chosen pile. Then, the chosen pile is placed back to the i-th position in the sequence. -
4.
Remove the revealed cards, i.e., the cards in row 2. (Note, therefore, that we do not use the card
 revealed in Step 3.) Then, apply a pile-shifting shuffle.
revealed in Step 3.) Then, apply a pile-shifting shuffle. -
5.
Reveal all the cards in row 3. Then, one
 appears, and the pile above the revealed
appears, and the pile above the revealed
 is \({\textbf {p}}_1\). Therefore, by shifting the sequence of piles (such that \({\textbf {p}}_1\) becomes the leftmost pile in the sequence), we can obtain a sequence of piles whose order is the same as the original one without revealing any information about the order of the input sequence.
is \({\textbf {p}}_1\). Therefore, by shifting the sequence of piles (such that \({\textbf {p}}_1\) becomes the leftmost pile in the sequence), we can obtain a sequence of piles whose order is the same as the original one without revealing any information about the order of the input sequence.
1.2 C.2 Sub-protocol: 4-Neighbour Protocol [27]
Given pq commitments placed on a \(p\times q\) grid, a prover P has a commitment in mind, which we call a target commitment. The prover P wants to reveal the target commitment and another one that lies next to the target commitment (without revealing their exact positions). Here, a verifier V should be convinced that the second commitment is a neighbour of the first one (without knowing which one) as well as V should be able to confirm the colours of both the commitments. To handle the case where the target commitment is at the edge of the grid, we place commitments to red (as “dummy” commitments) in the left of the first column and the below of the last row to prevent P from choosing a commitment that is not a neighbour. Thus, the size of the expanded grid is \((p+1)\times (q+1)\).Footnote 5
This sub-protocol proceeds as follows.
-
1.
P and V pick the \((p+1)(q+1)\) commitments on the grid from left-to-right and top-to-bottom to make a sequence of commitments:

-
2.
P uses the chosen pile protocol (Sect. 2) to reveal the target commitment.
-
3.
P and V pick all the four neighbours of the target commitment. Since a pile-shifting shuffle is a cyclic reordering, the distance between commitments are kept (up to a given modulo). That is, for a target commitment (not at the edge), the possible four neighbours are at distance one for the left or right one, and \(p+1\) for the bottom or top one. Therefore, P and V can determine the positions of all the four neighbours.
-
4.
Among these four neighbours, P chooses one commitment using the chosen pile protocol and reveals it.
-
5.
P and V end the second and first chosen pile protocols.
1.3 C.3 Full Protocol
Assume that there is a grid having \(p\times q\) cells. Without loss of generality, P wants to arrange white commitments on the grid such that they form a white-polyomino while V is convinced that the placement of commitments is surely a white-polyomino. The method is as follows.
-
1.
P and V place a commitment to black (i.e.,
 ) on every cell and commitments to red as mentioned in Sect. 2.4 so that they have \((p+1)(q+1)\) commitments on the board.
) on every cell and commitments to red as mentioned in Sect. 2.4 so that they have \((p+1)(q+1)\) commitments on the board. -
2.
P uses the chosen pile protocol to choose one black commitment that P wants to change.
-
(a)
V swaps the two cards constituting the chosen commitment so that it becomes a white commitment (recall the encoding (1)).
-
(b)
P and V end the chosen pile protocol to return the commitments to their original positions.
-
(a)
-
3.
P and V repeat the following steps exactly \(pq-1\) times.
-
(a)
P chooses one white commitment as a target and one black commitment among its neighbours using the 4-neighbour protocol; the neighbour is chosen such that P wants to make it white.
-
(b)
V reveals the target commitment. If it corresponds to white, then V continues; otherwise V aborts.
-
(c)
V reveals the neighbour commitment (chosen by P). If it corresponds to black, then P makes the neighbour white or keep it black (depending on P’s choice) by executing the following steps; otherwise V aborts.
-
i.
If P wants to change the commitment, P places face-down club-to-heart pair below it; otherwise, P places a heart-to-club pair:

-
ii.
Regarding cards in the same column as a pile, V applies a pile-shifting shuffle to the sequence of piles:
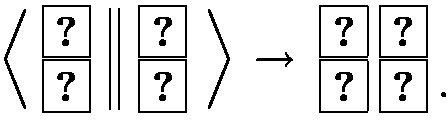
-
iii.
V reveals the two cards in the second row. If the revealed right card is
 , then V swaps the two cards in the first row; otherwise V does nothing.
, then V swaps the two cards in the first row; otherwise V does nothing.
-
i.
-
(d)
P and V end the 4-neighbour protocol.
-
(a)
-
4.
P and V remove all the red commitments (i.e., dummy commitments) so that we have pq commitments on the board.
After this process, V is convinced that all the white commitments represent a white-polyomino. Therefore, this method allows a prover P to make a solution that only P has in mind, guaranteed to satisfy the connectivity constraint.
If the number of white cells in the final polyomino, say k, is public to a verifier V, it is sufficient that in Step 3, P and V repeat \(k-1\) times and in Step 3c, and hence, V simply swaps the two cards constituting the neighbour commitment to make it white (without P’s choice).
D Security Proofs
Our protocol needs to verify three security properties given as theorems. Note that the sub-protocols used from the literature have been proven secure i.e., they are correct, complete, sound and zero-knowledge.
Theorem 1
(Completeness). If P knows the solution of an Usowan grid, then P can convince V.
Proof
P convinces V in the sense that the protocol does not abort which means that all the rules are satisfied. The protocol can be split into two phases: (1) the connectivity phase and (2) the verification phase.
(1) Since P knows the solution, the white cells are connected and hence P can always choose a black commitment at step 2 to swap it to white.
(2) For the lonely black verification, there is no configuration of two black cells that are touching horizontally nor vertically hence for every pair of adjacent cells, there is always at least one white cell.
For the liar verification, there is exactly (in each region) one numbered cell surrounded by a different number of black cells. Suppose, without lost of generality, that the liar cell is equal to i in a given region (the same result could be applied for each other region). When the sum of the four neighbours is done, the card at position (from left) \(i+1\) is
 otherwise the numbered card is not a liar. Thus when revealing the cards at the last step, there is always a
otherwise the numbered card is not a liar. Thus when revealing the cards at the last step, there is always a
 card.
card.
Theorem 2
(Soundness). If P does not provide a solution of the \(p\times q\) Usowan grid, P is not able to convince V.
Proof
Suppose that P does not provide a solution. If the white cells are not connected, then P cannot choose a neighbor commitment that P wants to change at step 3c. If there are two black commitments touching (or more), then the five-card trick will output 0; hence, V will abort. Finally, if there is not one liar exactly in a given region, then the last step of the verification will reveal either no
 or at least two
or at least two
 s; hence, V will abort.
s; hence, V will abort.
Theorem 3
(Zero-knowledge). V learns nothing about P’s solution of the given grid G.
Proof
We use the same proof technique as in [11], namely the description of an efficient simulator that simulates the interaction between an honest prover and a cheating verifier. The goal is to produce an indistinguishable interaction from the verifier’s view (with the prover). Notice that the simulator does not have the solution but it can swap cards during shuffles. Informally, the verifier cannot distinguish between the distributions of two protocols, one that is run with the actual solution and one with random commitments. The simulator acts as follows.
-
The simulator constructs a random connected white polyomino.
-
During the lonely black verification, the simulator replaces the cards in the five-card trick introduced in Sect. 2.3 with
 . While the latter sequence is randomly shifted, this ensure that the protocol continues.
. While the latter sequence is randomly shifted, this ensure that the protocol continues. -
During the liar verification, the simulator simply replaces, in the last step, the cards to have exactly one
 and the rest as
and the rest as
 s. This ensure that there is exactly one liar in a given region, meaning that the protocol does not abort.
s. This ensure that there is exactly one liar in a given region, meaning that the protocol does not abort.
The simulated and real proofs are indistinguishable and hence V learns nothing from the connectivity and verification phases. Finally, we conclude that the protocol is zero-knowledge.
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Robert, L., Miyahara, D., Lafourcade, P., Mizuki, T. (2022). Hide a Liar: Card-Based ZKP Protocol for Usowan. In: Du, DZ., Du, D., Wu, C., Xu, D. (eds) Theory and Applications of Models of Computation. TAMC 2022. Lecture Notes in Computer Science, vol 13571. Springer, Cham. https://doi.org/10.1007/978-3-031-20350-3_17
Download citation
DOI: https://doi.org/10.1007/978-3-031-20350-3_17
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-20349-7
Online ISBN: 978-3-031-20350-3
eBook Packages: Computer ScienceComputer Science (R0)




 , then the four bottom cards are
, then the four bottom cards are
 .
. , then the four bottom cards are
, then the four bottom cards are
 .
.


 (up to cyclic shifts), then
(up to cyclic shifts), then  (up to cyclic shifts), then
(up to cyclic shifts), then  .
. and swap the two cards of the commitment to
and swap the two cards of the commitment to  and one
and one
 , P places m face-down cards (denoted by row 2) below the given piles such that only the i-th card is
, P places m face-down cards (denoted by row 2) below the given piles such that only the i-th card is
 . We further put m cards (denoted by row 3) below the cards such that only the first card is
. We further put m cards (denoted by row 3) below the cards such that only the first card is
 :
: 
 appears, and the pile above the revealed
appears, and the pile above the revealed
 is the i-th pile (thus P can obtain
is the i-th pile (thus P can obtain  revealed in Step
revealed in Step  appears, and the pile above the revealed
appears, and the pile above the revealed
 is
is 
 ) on every cell and commitments to red as mentioned in Sect.
) on every cell and commitments to red as mentioned in Sect. 
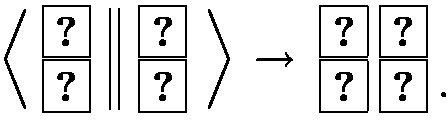
 , then V swaps the two cards in the first row; otherwise V does nothing.
, then V swaps the two cards in the first row; otherwise V does nothing. . While the latter sequence is randomly shifted, this ensure that the protocol continues.
. While the latter sequence is randomly shifted, this ensure that the protocol continues. and the rest as
and the rest as
 s. This ensure that there is exactly one liar in a given region, meaning that the protocol does not abort.
s. This ensure that there is exactly one liar in a given region, meaning that the protocol does not abort.