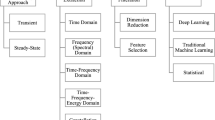
Abstract
Device or machine fingerprinting is the process of collecting information on a (part of a) device for its identification. This can be done under different scenarios and using information from different hardware and software layers of the device. Hardware fingerprinting typically refers to device fingerprinting using information collected from the hardware layer. Hardware fingerprinting can have nefarious usages related to privacy abuse, as well as many positive ones such as soft authentication, indoor positioning systems, and others. Here we introduce some of the uses of hardware fingerprinting, with special emphasis on those related to commonly available devices, and explain how machine learning and deep learning have enabled and/or improved them. Additionally, we discuss some of their limitations and possibilities for improvement.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
The MadWiFi driver, present in many Atheros chipsets.
- 2.
Periodic CAN messages can typically constitute around \(90\%\) of CAN bus messages, although this varies by vehicle platform and operating conditions.
- 3.
The CAN bus arbitrates priority based on the ID of the messages colliding. Using extended identifiers when there is no need, it is possible to fix 18 bits of the ID for all ECUs.
- 4.
Note that ML and DL algorithms aim for this, but typically can only test the behaviour in a particular test dataset.
References
Abdolmaleki, B., Baghery, K., Akhbari, B., Aref, M.R.: Cryptanalysis of two EPC-based RFID security schemes. In: International ISC Conference on Information Security and Cryptology - ISCISC2015, pp. 1–6. IEEE, September 2015
Abdolmaleki, B., Baghery, K., Akhbari, B., Reza Aref, M.: Attacks and improvements on two new-found RFID authentication protocols. In: International Symposium on Telecommunications - IST 2014, pp. 1–6, July 2014
Aghili, S.F., Bagheri, N., Gauravaram, P., Safkhani, M., Sanadhya, S.K.: On the security of two RFID mutual authentication protocols. In: Hutter, M., Schmidt, J.-M. (eds.) RFIDSec 2013. LNCS, vol. 8262, pp. 86–99. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-41332-2_6
Ahmadian, Z., Salmasizadeh, M., Aref, M.R.: Desynchronization attack on RAPP ultralightweight authentication protocol. Cryptology ePrint Archive, Report 2012/490 (2012)
Ahmadian, Z., Salmasizadeh, M., Aref, M.R.: Recursive linear and differential cryptanalysis of ultralightweight authentication protocols. Cryptology ePrint Archive, Report 2012/489 (2012)
Ain, Q.U., Mahmood, Y., Mujahid, U., Najam-ul islam, M.: Cryptanalysis of mutual ultralightweight authentication protocols: SASI and RAPP. In: International Conference on Open Source Systems and Technologies - ICOSST 2014, Lahore, Pakistan, pp. 136–145, December 2014
Akgün, M., Bayrak, A.O., Çaǧlayan, M.U.: Attacks and improvements to chaotic map-based RFID authentication protocol. Secur. Commun. Netw. 8, 4028–4040 (2015)
Akgun, M., Caglayan, M.U.: Weaknesses of two RFID protocols regarding de-synchronization attacks. In: International Wireless Communications and Mobile Computing Conference IWCMC - 2015, Dubrovnik, Croatia, August 2015
Akgün, M., Çaǧlayan, M.U.: On the security of recently proposed RFID protocols. Cryptology ePrint Archive, Report 2013/820 (2013)
Akgün, M., Çaǧlayan, M.U.: Providing destructive privacy and scalability in RFID systems using PUFs. Ad Hoc Networks, February 2015
Alavi, S.M., Abdolmaleki, B., Baghery, K.: Vulnerabilities and improvements on HRAP\(^+\), a hash-based RFID authentication protocol. Adv. Comput. Sci. Int. J. 3(6), 51–56 (2014)
Alavi, S.M., Baghery, K., Abdolmaleki, B.: Security and privacy flaws in a recent authentication protocol for EPC C1 G2 RFID tags. Adv. Comput. Sci. Int. J. 3(5), 44–52 (2014)
Arackaparambil, C., Bratus, S., Shubina, A., Kotz, D.: On the reliability of wireless fingerprinting using clock skews, pp. 169–174, January 2010. https://doi.org/10.1145/1741866.1741894
Avatefipour, O.: Physical-fingerprinting of electronic control unit (ECU) based on machine learning algorithm for in-vehicle network communication protocol “can-bus” (2017)
Avoine, G., Beaujeant, A., Hernandez-Castro, J., Demay, L., Teuwen, P.: A survey of security and privacy issues in ePassport protocols. ACM Comput. Surv. 48, 1–37 (2016). https://doi.org/10.1145/2825026
Baldini, G., Giuliani, R., Cano, E.: An analysis of the privacy threat in vehicular ad hoc networks due to radio frequency fingerprinting. Mob. Inf. Syst. 2017, 1–13 (2017). https://doi.org/10.1155/2017/3041749
Bauer, K., Mccoy, D., Anderson, E., Breitenbach, M., Grunwald, G.G.D.: The directional attack on wireless localization: how to spoof your location with a tin can. In: Proceedings of IEEE Conference on Global Telecommunications, pp. 4125–4130 (2009)
Bayar, B., Stamm, M.: A deep learning approach to universal image manipulation detection using a new convolutional layer, pp. 5–10, June 2016. https://doi.org/10.1145/2909827.2930786
Beale, J., Meer, H., van der Walt, C., Deraison, R.: Nessus Network Auditing: Jay Beale Open Source Security Series. Elsevier (2004)
Bellare, M., Rogaway, P.: Entity authentication and key distribution. In: Stinson, D.R. (ed.) CRYPTO 1993. LNCS, vol. 773, pp. 232–249. Springer, Heidelberg (1994). https://doi.org/10.1007/3-540-48329-2_21
Bennabhaktula, G., Alegre, E., Karastoyanova, D., Azzopardi, G.: Device-based image matching with similarity learning by convolutional neural networks that exploit the underlying camera sensor pattern noise, April 2020
Bertoncini, C., Rudd, K., Nousain, B., Hinders, M.: Wavelet fingerprinting of radio-frequency identification (RFID) tags. IEEE Trans. Ind. Electron. 59(12), 4843–4850 (2011)
Biham, E., Bitan, S., Gavril, E.: TCAN: authentication without cryptography on a can bus based on nodes location on the bus. In: Embedded Security in Cars - ESCAR Europe 2018 Conference. ESCAR (2018)
Bojinov, H., Michalevsky, Y., Nakibly, G., Boneh, D.: Mobile device identification via sensor fingerprinting. arXiv abs/1408.1416 (2014)
Bolliger, P.: Redpin-adaptive, zero-configuration indoor localization through user collaboration. In: Proceedings of the First ACM International Workshop on Mobile Entity Localization and Tracking in GPS-Less Environments, pp. 55–60 (2008)
Bratus, S., Cornelius, C., Kotz, D., Peebles, D.: Active behavioral fingerprinting of wireless devices. In: Proceedings of the ACM Conference on Wireless Network Security (WiSec), pp. 56–61. ACM, March 2008. https://doi.org/10.1145/1352533.1352543. https://www.cs.dartmouth.edu/~kotz/research/bratus-fingerprint/index.html
Brunato, M., Battiti, R.: Statistical learning theory for location fingerprinting in wireless LANs. Comput. Netw. 47(6), 825–845 (2005)
Butti, L.: Raw wireless tools homepage (2006). http://rfakeap.tuxfamily.org/
Butti, L., Tinnés, J.: Discovering and exploiting 802.11 wireless driver vulnerabilities. J. Comput. Virol. 4, 25–37 (2008). https://doi.org/10.1007/s11416-007-0065-x
Cao, Y., Li, S., Wijmans, E.: (Cross-)browser fingerprinting via OS and hardware level features, January 2017. https://doi.org/10.14722/ndss.2017.23152
Carlotto, A., Parodi, M., Bonamico, C., Lavagetto, F., Valla, M.: Proximity classification for mobile devices using Wi-Fi environment similarity. In: Proceedings of the First ACM International Workshop on Mobile Entity Localization and Tracking in GPS-Less Environments, pp. 43–48 (2008)
Chang, N., Rashidzadeh, R., Ahmadi, M.: Robust indoor positioning using differential Wi-Fi access points. IEEE Trans. Consum. Electron. 56(3), 1860–1867 (2010)
Checkoway, S., et al.: Comprehensive experimental analyses of automotive attack surfaces. In: Proceedings of the 20th USENIX Conference on Security, SEC 2011, p. 6. USENIX Association (2011)
Chen, D., et al.: S2M: a lightweight acoustic fingerprints-based wireless device authentication protocol. IEEE Internet Things J. 4(1), 88–100 (2017)
Chen, Y., Kleisouris, K., Li, X., Trappe, W., Martin, R.: A security and robustness performance analysis of localization algorithms to signal strength attacks. TOSN 5, 1–37 (2009). https://doi.org/10.1145/1464420.1464422
Cho, K.T., Shin, K.G.: Fingerprinting electronic control units for vehicle intrusion detection. In: Proceedings of the 25th USENIX Conference on Security Symposium, SEC 2016, pp. 911–927. USENIX Association (2016)
Choi, K., Lam, E., Wong, K.: Automatic source camera identification using the intrinsic lens radial distortion. Opt. Express 14, 11551–11565 (2006). https://doi.org/10.1364/OE.14.011551
Choi, K., Lam, E., Wong, K.: Source camera identification using footprints from lens aberration. In: Proceedings of the SPIE, vol. 6069, February 2006. https://doi.org/10.1117/12.649775
Choi, W., Jo, H., Woo, S., Chun, J., Park, J.: Identifying ECUs using inimitable characteristics of signals in controller area networks. IEEE Trans. Veh. Technol. 67, 4757–4770 (2016). https://doi.org/10.1109/TVT.2018.2810232
Cinefra, N.: An adaptive indoor positioning system based on Bluetooth low energy RSSI (2013)
Cozzolino, D., Verdoliva, L.: Noiseprint: a CNN-based camera model fingerprint. IEEE Trans. Inf. Forensics Secur. 15, 144–159 (2019). https://doi.org/10.1109/TIFS.2019.2916364
Danev, B., Heydt-Benjamin, T.S., Čapkun, S.: Physical-layer identification of RFID devices. In: Proceedings of the 18th Conference on USENIX Security Symposium, SSYM 2009, pp. 199–214. USENIX Association (2009)
Das, A., Borisov, N., Caesar, M.: Do you hear what I hear? Fingerprinting smart devices through embedded acoustic components. In: Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, CCS 2014, pp. 441–452. Association for Computing Machinery, New York (2014). https://doi.org/10.1145/2660267.2660325
Delvaux, J.: Machine-learning attacks on PolyPUFs, OB-PUFs, RPUFs, LHS-PUFs, and PUF–FSMs. IEEE Trans. Inf. Forensics Secur. 14, 2043–2058 (2019). https://doi.org/10.1109/TIFS.2019.2891223
Devernay, F., Faugeras, O.: Automatic calibration and removal of distortion from scenes of structured environments. In: Proceedings of the SPIE, vol. 2567, July 1995. https://doi.org/10.1117/12.218487
Dey, S., Roy, N., Xu, W., Choudhury, R., Nelakuditi, S.: AccelPrint: imperfections of accelerometers make smartphones trackable, January 2014. https://doi.org/10.14722/ndss.2014.23059
Ellch, J.P.: Fingerprinting 802.11 devices (2006). https://calhoun.nps.edu/handle/10945/2592
Englehardt, S., Narayanan, A.: Online tracking: a 1-million-site measurement and analysis, pp. 1388–1401, October 2016. https://doi.org/10.1145/2976749.2978313
Ferrara, P., Beslay, L.: Multimodal fingerprinting of imaging devices -inception report project AVICAO - authors and victims identification of child abuse on-line, December 2016. https://doi.org/10.2760/751517
Foruhandeh, M., Mohammed, A.Z., Kildow, G., Berges, P., Gerdes, R.: Spotr: GPS spoofing detection via device fingerprinting (2020)
Franklin, J., McCoy, D., Tabriz, P., Neagoe, V., Van Randwyk, J., Sicker, D.: Passive data link layer 802.11 wireless device driver fingerprinting. In: Proceedings of the 15th Conference on USENIX Security Symposium, USENIX-SS 2006, vol. 2015. USENIX Association (2006)
Goodfellow, I.J., Shlens, J., Szegedy, C.: Explaining and harnessing adversarial examples. arXiv:1412.6572 (2014)
Gopalakrishnan, S., Cekic, M., Madhow, U.: Robust wireless fingerprinting via complex-valued neural networks (2019)
Groza, B., Murvay, S., van Herrewege, A., Verbauwhede, I.: LiBrA-CAN: a lightweight broadcast authentication protocol for controller area networks. In: Pieprzyk, J., Sadeghi, A.-R., Manulis, M. (eds.) CANS 2012. LNCS, vol. 7712, pp. 185–200. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-35404-5_15
Hall, J., Barbeau, M., Kranakis, E.: Detecting rogue devices in Bluetooth networks using radio frequency fingerprinting, pp. 108–113, January 2006
Hartkopp, O., Schilling, R.M.: Message authenticated CAN. In: Escar Conference, Berlin, Germany (2012)
Hasse, J., Gloe, T., Beck, M.: Forensic identification of GSM mobile phones. In: Proceedings of the First ACM Workshop on Information Hiding and Multimedia Security, pp. 131–140 (2013)
Hernandez-Castro, J.C., Estevez-Tapiador, J.M., Peris-Lopez, P., Quisquater, J.J.: Cryptanalysis of the SASI ultralightweight RFID authentication protocol with modular rotations. In: International Workshop on Coding and Cryptography - WCC 2009, Ullensvang, Norway, May 2009
Hernandez-Castro, J.C., Peris-Lopez, P., Phan, R.C.-W., Tapiador, J.M.E.: Cryptanalysis of the David-Prasad RFID ultralightweight authentication protocol. In: Ors Yalcin, S.B. (ed.) RFIDSec 2010. LNCS, vol. 6370, pp. 22–34. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-16822-2_3
Hernandez-Castro, J.C., Tapiador, J.E., Peris-Lopez, P., Clark, J.A., Talbi, E.G.: Metaheuristic traceability attack against SLMAP, an RFID lightweight authentication protocol. In: Proceedings of the 23rd IEEE International Parallel and Distributed Processing Symposium - IPDPS 2009, Rome, Italy. IEEE Computer Society, May 2009
Hernandez-Castro, J.C., Peris-Lopez, P., Aumasson, J.-P.: On the key schedule strength of PRESENT. In: Garcia-Alfaro, J., Navarro-Arribas, G., Cuppens-Boulahia, N., de Capitani di Vimercati, S. (eds.) DPM/SETOP -2011. LNCS, vol. 7122, pp. 253–263. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-28879-1_17
Hospodar, G., Maes, R., Verbauwhede, I.: Machine learning attacks on 65nm arbiter PUFs: accurate modeling poses strict bounds on usability. In: 2012 IEEE International Workshop on Information Forensics and Security (WIFS), pp. 37–42 (2012)
Huo, Y., Zhu, X.: High dynamic range image forensics using CNN (2019)
Hupperich, T., Hosseini, H., Holz, T.: Leveraging sensor fingerprinting for mobile device authentication. In: Caballero, J., Zurutuza, U., Rodríguez, R.J. (eds.) DIMVA 2016. LNCS, vol. 9721, pp. 377–396. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-40667-1_19
Jana, S., Kasera, S.: On fast and accurate detection of unauthorized wireless access points using clock skews, vol. 9, pp. 104–115, January 2008. https://doi.org/10.1109/TMC.2009.145
Jenkins, I.R., Shapiro, R., Bratus, S., Speers, R., Goodspeed, T.: Fingerprinting IEEE 802.15.4 devices with commodity radios. Technical report. TR2014-746, Dartmouth College, Computer Science, Hanover, NH, March 2014. http://www.cs.dartmouth.edu/reports/TR2014-746-rev2.pdf
Kaemarungsi, K., Krishnamurthy, P.: Modeling of indoor positioning systems based on location fingerprinting. In: IEEE Infocom 2004, vol. 2, pp. 1012–1022. IEEE (2004)
Karagiannis, T., Papagiannaki, K., Faloutsos, M.: BLINC: multilevel traffic classification in the dark, vol. 35, pp. 229–240, January 2005
Khalafalla, M., Gebotys, C.: PUFs deep attacks: enhanced modeling attacks using deep learning techniques to break the security of double arbiter PUFs. In: 2019 Design, Automation Test in Europe Conference Exhibition (DATE), pp. 204–209 (2019)
Kharrazi, M., Sencar, H.T., Memon, N.: Blind source camera identification. In: 2004 International Conference on Image Processing, ICIP 2004, vol. 1, pp. 709–712 (2004)
Kimoto, R., Ishida, S., Yamamoto, T., Tagashira, S., Fukuda, A.: MuCHLoc: indoor zigbee localization system utilizing inter-channel characteristics \(\dagger \). Sensors (Basel, Switzerland) 19, 1645 (2019)
Kobusinska, A., Brzezinski, J., Pawulczuk, K.: Device fingerprinting: analysis of chosen fingerprinting methods. In: IoTBDS (2017)
Kohno, T., Broido, A., Claffy, K.C.: Remote physical device fingerprinting. In: 2005 IEEE Symposium on Security and Privacy (S&P 2005), pp. 211–225 (2005)
Koike-Akino, T., Wang, P., Pajovic, M., Sun, H., Orlik, P.V.: Fingerprinting-based indoor localization with commercial MMWave WiFi: a deep learning approach. IEEE Access 8, 84879–84892 (2020)
Koscher, K., et al.: Experimental security analysis of a modern automobile. In: 2010 IEEE Symposium on Security and Privacy, pp. 447–462. IEEE (2010)
Krizhevsky, A., Nair, V., Hinton, G.: CIFAR datasets (2000). https://www.cs.toronto.edu/~kriz/cifar.html
Kurachi, R., Matsubara, Y., Takada, H., Adachi, N., Miyashita, Y., Horihata, S.: CaCAN-centralized authentication system in can (controller area network). In: 14th International Conference on Embedded Security in Cars (ESCAR 2014) (2014)
Kurosawa, K., Kuroki, K., Saitoh, N.: CCD fingerprint method-identification of a video camera from videotaped images. In: Proceedings 1999 International Conference on Image Processing (Cat. 99CH36348), vol. 3, pp. 537–540 (1999)
Kushki, A., Plataniotis, K.N., Venetsanopoulos, A.N.: Sensor selection for mitigation of RSS-based attacks in wireless local area network positioning. In: 2008 IEEE International Conference on Acoustics, Speech and Signal Processing, pp. 2065–2068 (2008)
Li, X., Chen, Y., Yang, J., Zheng, X.: Designing localization algorithms robust to signal strength attacks, pp. 341–345, April 2011. https://doi.org/10.1109/INFCOM.2011.5935178
Li, Z., Trappe, W., Zhang, Y., Nath, B.: Robust statistical methods for securing wireless localization in sensor networks. In: Fourth International Symposium on Information Processing in Sensor Networks, IPSN 2005, pp. 91–98 (2005)
Lin, C.W., Sangiovanni-Vincentelli, A.: Cyber-security for the controller area network (CAN) communication protocol. In: 2012 International Conference on Cyber Security, pp. 1–7. IEEE (2012)
Lin, H., Zhang, Y., Griss, M., Landa, I.: WASP: an enhanced indoor locationing algorithm for a congested Wi-Fi environment. In: Fuller, R., Koutsoukos, X.D. (eds.) MELT 2009. LNCS, vol. 5801, pp. 183–196. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-04385-7_13
Mayer, O., Stamm, M.C.: Forensic similarity for digital images. IEEE Trans. Inf. Forensics Secur. 15, 1331–1346 (2020)
Merchant, K., Revay, S., Stantchev, G., Nousain, B.: Deep learning for RF device fingerprinting in cognitive communication networks. IEEE J. Sel. Top. Signal Process. 12(1), 160–167 (2018)
Michalevsky, Y., Boneh, D., Nakibly, G.: Gyrophone: recognizing speech from gyroscope signals. In: 23rd USENIX Security Symposium (USENIX Security 2014), San Diego, CA, pp. 1053–1067. USENIX Association, August 2014. https://www.usenix.org/conference/usenixsecurity14/technical-sessions/presentation/michalevsky
Miller, C., Valasek, C.: Remote exploitation of an unaltered passenger vehicle. Black Hat USA 2015, 91 (2015)
Nakibly, G., Shelef, G., Yudilevich, S.: Hardware fingerprinting using HTML5, March 2015
Nowdehi, N., Lautenbach, A., Olovsson, T.: In-vehicle can message authentication: an evaluation based on industrial criteria. In: 2017 IEEE 86th Vehicular Technology Conference (VTC-Fall), pp. 1–7 (2017)
Nürnberger, S., Rossow, C.: – vatiCAN – vetted, authenticated CAN Bus. In: Gierlichs, B., Poschmann, A.Y. (eds.) CHES 2016. LNCS, vol. 9813, pp. 106–124. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-53140-2_6
Olejnik, L., Acar, G., Castelluccia, C., Díaz, C.: The leaking battery - a privacy analysis of the HTML5 battery status API. IACR Cryptology ePrint Archive 2015, 616 (2015)
Organero, M., Brito-Pacheco, C.: Improving accuracy and simplifying training in fingerprinting-based indoor location algorithms at room level. Mob. Inf. Syst. 2016 (2016). https://doi.org/10.1155/2016/2682869
Peris-Lopez, P., Hernandez-Castro, J.C., Estevez-Tapiador, J.M., Li, T., Li, Y.: Vulnerability analysis of RFID protocols for tag ownership transfer. Comput. Netw. 54(9), 1502–1508 (2010)
Peris-Lopez, P., Hernandez-Castro, J.C., Tapiador, J.M.E., Li, T., van der Lubbe, J.C.A.: Weaknesses in two recent lightweight RFID authentication protocols. In: Bao, F., Yung, M., Lin, D., Jing, J. (eds.) Inscrypt 2009. LNCS, vol. 6151, pp. 383–392. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-16342-5_28
Peris-Lopez, P., Hernandez-Castro, J.C., Estevez-Tapiador, J.M., van der Lubbe, J.C.A.: Security flaws in a recent ultralightweight RFID protocol. In: Workshop on RFID Security - RFIDSec Asia 2010. Cryptology and Information Security, Singapore, Republic of Singapore, vol. 4, pp. 83–93. IOS Press, February 2010
Peris-Lopez, P., Hernandez-Castro, J.C., Estevez-Tapiador, J.M., Palomar, E., van der Lubbe, J.C.A.: Cryptographic puzzles and distance-bounding protocols: practical tools for RFID security. In: IEEE International Conference on RFID - IEEE RFID 2010, Orlando, Florida, USA, pp. 45–52. IEEE Computer Society, April 2010
Peris-Lopez, P., Hernandez-Castro, J.C., Estevez-Tapiador, J.M., Ribagorda, A.: RFID systems: a survey on security threats and proposed solutions. In: Cuenca, P., Orozco-Barbosa, L. (eds.) PWC 2006. LNCS, vol. 4217, pp. 159–170. Springer, Heidelberg (2006). https://doi.org/10.1007/11872153_14
Peris-Lopez, P., Hernandez-Castro, J.C., Estevez-Tapiador, J.M., Ribagorda, A.: Cryptanalysis of a novel authentication protocol conforming to EPC-C1G2 standard. In: Workshop on RFID Security - RFIDSec 2007, Malaga, Spain, July 2007
Peris-Lopez, P., Hernandez-Castro, J.C., Phan, R.C.-W., Tapiador, J.M.E., Li, T.: Quasi-linear cryptanalysis of a secure RFID ultralightweight authentication protocol. In: Lai, X., Yung, M., Lin, D. (eds.) Inscrypt 2010. LNCS, vol. 6584, pp. 427–442. Springer, Heidelberg (2011). https://doi.org/10.1007/978-3-642-21518-6_30
Peris-Lopez, P., Hernandez-Castro, J.C., Tapiador, J.M., van der Lubbe, J.C.: Cryptanalysis of an EPC class-1 generation-2 standard compliant authentication protocol. Eng. Appl. Artif. Intell. 24(6), 1061–1069 (2011)
Petit, J., Schaub, F., Feiri, M., Kargl, F.: Pseudonym schemes in vehicular networks: a survey. IEEE Commun. Surv. Tutor. 17(1), 228–255 (2014)
Quiring, E., Kirchner, M., Rieck, K.: On the security and applicability of fragile camera fingerprints, July 2019
Rao, X., Li, Z., Yang, Y.: Device-free passive wireless localization system with transfer deep learning method. J. Ambient. Intell. Hum. Comput. 11(10), 4055–4071 (2020). https://doi.org/10.1007/s12652-019-01662-y
Rivest, R.L.: Learning decision lists. Mach. Learn. 2(3), 229–246 (1987)
Rührmair, U., Sölter, J.: PUF modeling attacks: an introduction and overview. In: 2014 Design, Automation Test in Europe Conference Exhibition (DATE), pp. 1–6 (2014)
Safkhani, M., Bagheri, N., Peris-Lopez, N., Mitrokotsa, A., Hernandez-Castro, J.C.: Weaknesses in another Gen2-based RFID authentication protocol. In: IEEE International Conference on RFID-Technology and Applications - IEEE RFID TA 2012, Nice, France. IEEE Press, IEEE, November 2012
Safkhani, M., Peris-Lopez, P., Badheri, N., Naderi, M., Hernandez-Castro, J.C.: On the security of Tan et al. serverless RFID authentication and search protocols. In: Workshop on RFID Security - RFIDSec 2012, Nijmegen, Netherlands, June 2012
Safkhani, M., Peris-Lopez, P., Hernandez-Castro, J.C., Bagheri, N.: Cryptanalysis of the Cho et al. protocol: a hash-based RFID tag mutual authentication protocol. J. Comput. Appl. Math. 259, 571–577 (2013)
Safkhani, M., Peris-Lopez, P., Hernandez-Castro, J.C., Bagheri, N., Naderi, M.: Cryptanalysis of Cho et al’.s protocol, a hash-based mutual authentication protocol for RFID systems. Cryptology ePrint Archive, Report 2011/311 (2011)
Sagong, S., Ying, X., Clark, A., Bushnell, L., Poovendran, R.: Cloaking the clock: emulating clock skew in controller area networks, pp. 32–42, April 2018. https://doi.org/10.1109/ICCPS.2018.00012
Sankhe, K., Belgiovine, M., Zhou, F., Riyaz, S., Ioannidis, S., Chowdhury, K.: Oracle: optimized radio classification through convolutional neural networks. In: IEEE INFOCOM 2019 - IEEE Conference on Computer Communications, pp. 370–378 (2019)
Santikellur, P., Bhattacharyay, A., Chakraborty, R.S.: Deep learning based model building attacks on arbiter PUF compositions. IACR Cryptology ePrint Archive 2019, 566 (2019)
Schweppe, H., Roudier, Y., Weyl, B., Apvrille, L., Scheuermann, D.: Car2x communication: securing the last meter-a cost-effective approach for ensuring trust in car2x applications using in-vehicle symmetric cryptography. In: 2011 IEEE Vehicular Technology Conference (VTC Fall), pp. 1–5. IEEE (2011)
Shaik, A., Borgaonkar, R., Park, S., Seifert, J.P.: New vulnerabilities in 4G and 5G cellular access network protocols: exposing device capabilities. In: Proceedings of the 12th Conference on Security and Privacy in Wireless and Mobile Networks, WiSec 2019, pp. 221–231. Association for Computing Machinery, New York (2019). https://doi.org/10.1145/3317549.3319728
Shields, C., Levine, B.N.: A protocol for anonymous communication over the internet. In: Proceedings of the 7th ACM Conference on Computer and Communications Security, pp. 33–42 (2000)
Smith, L., et al.: Classifying WiFi “physical fingerprints” using complex deep learning. In: Hammoud, R.I., Overman, T.L., Mahalanobis, A. (eds.) Automatic Target Recognition XXX, vol. 11394, pp. 82–96. International Society for Optics and Photonics, SPIE (2020). https://doi.org/10.1117/12.2557933
Smith, S.: Cryptographic scalability challenges in the smart grid, pp. 1–3, January 2012. https://doi.org/10.1109/ISGT.2012.6175564
Subbu, K.P., Zhang, C., Luo, J., Vasilakos, A.V.: Analysis and status quo of smartphone-based indoor localization systems. IEEE Wirel. Commun. 21(4), 106–112 (2014)
Subramaniam, N.: Google buys slicklogin: this is how its sound-based password system works (2014). https://www.firstpost.com/tech/news-analysis/google-buys-slicklogin-heres-sound-based-password-system-works-3647955.html
Szegedy, C., et al.: Intriguing properties of neural networks. arXiv:1312.6199 (2013)
Tromba, D., Huber, J.: Assessment and guidance for autosar secure onboard communication application. In: 17th Escar Europe: Embedded Security in Cars (Konferenzveröffentlichung). (Extended Abstract) (2019)
Van Goethem, T., Scheepers, W., Preuveneers, D., Joosen, W.: Accelerometer-based device fingerprinting for multi-factor mobile authentication. In: Caballero, J., Bodden, E., Athanasopoulos, E. (eds.) ESSoS 2016. LNCS, vol. 9639, pp. 106–121. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-30806-7_7
Van Herrewege, A., Singelee, D., Verbauwhede, I.: CANAuth-a simple, backward compatible broadcast authentication protocol for CAN bus. In: ECRYPT Workshop on Lightweight Cryptography, vol. 2011, p. 20 (2011)
Wang, H., Cheng, W., Xu, C., Zhang, M., Hu, L.: Method for identifying pseudo GPS signal based on radio frequency fingerprint. In: 2018 10th International Conference on Communications, Circuits and Systems (ICCCAS), pp. 354–358 (2018)
Wang, Q., Sawhney, S.: Vecure: a practical security framework to protect the can bus of vehicles. In: 2014 International Conference on the Internet of Things (IOT), pp. 13–18. IEEE (2014)
Wang, Y., Yang, X., Zhao, Y., Liu, Y., Cuthbert, L.: Bluetooth positioning using RSSI and triangulation methods. In: 2013 IEEE 10th Consumer Communications and Networking Conference (CCNC), pp. 837–842 (2013)
Weimerskirch, A.: Automotive and industrial data security. In: Cybersecurity and Cyber-physical Systems Workshop (2012)
Weisglass, Y., Oren, Y.: Authentication method for can messages. Escar Europe (2016)
Woo, S., Jo, H.J., Lee, D.H.: A practical wireless attack on the connected car and security protocol for in-vehicle can. IEEE Trans. Intell. Transp. Syst. 16(2), 993–1006 (2014)
Wu, Q., et al.: Deep learning based RF fingerprinting for device identification and wireless security. Electron. Lett. 54(24), 1405–1407 (2018)
Yang, J., Chen, Y., Lawrence, V.B., Swaminathan, V.: Robust wireless localization to attacks on access points. In: 2009 IEEE Sarnoff Symposium, pp. 1–5 (2009)
Yu, J., et al.: Radio frequency fingerprint identification based on denoising autoencoders, July 2019
Yuan, L., Hu, Y., Li, Y., Zhang, R., Zhang, Y., Hedgpeth, T.: Secure RSS-fingerprint-based indoor positioning: attacks and countermeasures. In: 2018 IEEE Conference on Communications and Network Security (CNS), pp. 1–9 (2018)
Zalewski, M.: p0f (2012). http://lcamtuf.coredump.cx/p0f3/
Zeng, H., Liu, J., Yu, J., Kang, X., Shi, Y., Wang, Z.: A framework of camera source identification Bayesian game. IEEE Trans. Cybern. 47, 1–12 (2016). https://doi.org/10.1109/TCYB.2016.2557802
Zhang, K., Zuo, W., Chen, Y., Meng, D., Zhang, L.: Beyond a Gaussian denoiser: residual learning of deep CNN for image denoising. IEEE Trans. Image Process. 26(7), 3142–3155 (2017)
Zhou, C., Xie, H., Shi, J.: Wi-Fi indoor location technology based on k-means algorithm. In: Zhang, Z., Shen, Z.M., Zhang, J., Zhang, R. (eds.) LISS 2014, pp. 765–770. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-43871-8_110
Zhuang, Y., Yang, J., Li, Y., Qi, L., El-Sheimy, N.: Smartphone-based indoor localization with Bluetooth low energy beacons. Sensors 16(5), 596 (2016)
Zuo, Z., Liu, L., Zhang, L., Fang, Y.: Indoor positioning based on Bluetooth low-energy beacons adopting graph optimization. Sensors 18, 3736 (2018). https://doi.org/10.3390/s18113736
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 Springer Nature Switzerland AG
About this chapter
Cite this chapter
Hernandez-Castro, C.J. (2022). Machine Learning and Deep Learning for Hardware Fingerprinting. In: Batina, L., Bäck, T., Buhan, I., Picek, S. (eds) Security and Artificial Intelligence. Lecture Notes in Computer Science, vol 13049. Springer, Cham. https://doi.org/10.1007/978-3-030-98795-4_9
Download citation
DOI: https://doi.org/10.1007/978-3-030-98795-4_9
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-98794-7
Online ISBN: 978-3-030-98795-4
eBook Packages: Computer ScienceComputer Science (R0)