Abstract
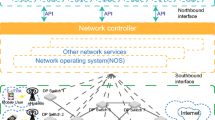
5G networks are being actively implemented in many countries around the world. The goal of introducing technologies that make up the new standard is to reduce information transmission delays, increase transmission speed, and increase the number of devices served. To achieve the targets, 5G networks must be built using software-defined networking (SDN) and network function virtualization (NFV) technology. This paper analyzes the integrity, resilience and security of 5G networks based on SDN/NFV, as well as provides recommendations for the comprehensive information security of such networks.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
GOST R 53111–2008. The stability of the functioning of the public communication network. Requirements and verification methods
GOST R 52448 Information security. Ensuring the security of telecommunication networks. General Provisions
Methodology for determining threats to information security in information systems. FSTEC (2015)
The basic model of threats to the security of personal data during their processing in personal data information systems (extract). Approved by the Deputy Director of FSTEC of Russia on February 15 (2008)
Methodology for modeling threats to information security (draft). FSTEC of Russia (2020)
Concept of creation and development of 5G/IMT-2020 networks in the Russian Federation
RFC 7426 - Software-Defined Networking (SDN): Layers and Architecture Terminology
ETSI GS NFV-SEC 003 V1.1.1 (2014–12) Network Functions Virtualisation (NFV); NFV Security; Security and Trust Guidance
3GPP TS 23.501 V16.4.0 (2020–03) System architecture for the 5G System (5GS)
3GPP TS 33.501 V16.2.0 (2020–03). Security architecture and procedures for 5G system
Technical Specification SDN Security Considerations in the Data Center. ONF Solution Brief (2013)
GOST R 51275 Information security. Object of informatization. Factors affecting information. General Provisions
GOST R 50922 Information security. Basic terms and definitions
Open Flow Switch Specification 1.5.1, Open Networking Foundation (2015)
Threat Analysis for the SDN Architecture 1.0 Technical Specification, Open Networking Foundation, (2016)
3GPP TS 23.502, “Procedures for the 5G System”
Databank of information security threats
Shaghaghi, M.K., Buyya, R., Jha, S.: Software-Defined Network (SDN) Data Plane Security: Issues, Solutions and Future Directions. arXiv:1804.00262v1
Prasad, A.R., Arumugam, S., Sheeba, B., Zugenmaier, A.: 3GPP 5G security. J. ICT Standardization 6(1–2), 137–158 (2018)
Arfaoui G., et al.: A security architecture for 5G networks. IEEE Access (2018), p. 1. https://doi.org/10.1109/ACCESS.2018.2827419
Gao, S., Li, Z., Xiao, B., Wei, G.: Security threats in the data plane of software-defined networks. IEEE Network, pp. 1–6 (2018). https://doi.org/10.1109/MNET.2018.1700283
Yao, J., Han, Z., Sohail, M., Wang, L.: A robust security architecture for SDN-based 5G networks. Future Internet, pp. 1–14 (2019)
Casado, M.: SANE: a protection architecture for enterprise networks. In: USENIX Security Symposium (2006)
Scott-Hayward, S., Natarajan, S., Sezer, S.: A survey of security in software defined networks. IEEE Commun. Surv. Tutorials 18(1), 623–654 (2016)
Zaidi, Z., Friderikos, V., Yousaf, Z., Fletcher, S., Dohler, M., Aghvami, H.: Will SDN be part of 5G? arXiv:1708.05096v2
Zhang, X., Kunz, A., Schroder, S.: Overview of 5G security in 3GPP (2017). https://doi.org/10.1109/CSCN.2017.8088619
Zakharov, A.A., Popov, E.F., Fuchko, M.M.: Information security aspects of SDN architecture. Bull. SibSUTI 1, 83–92 (2016)
Tikhvinsky, V., Bochechka, G., Minov, A., Babin, A.: 5G networks: international standardization. CONNECT, No. 1–2, pp. 52–58 (2017)
Efimushkin, V.A., Ledovskikh, T.V., Korabelnikov, D.M., Yazykov, D.N.: Review of SDN/NFV solutions of foreign manufacturers. T-Comm. Telecommun. Transport. 9(8), 5–13 (2015)
Kurochkin, I.I., Humenny, D.G.: Security of SDN networks. Classification of attacks. Modern Inf. Technol. IT Educ. 11(2), 381–383 (2015)
Loginov, S.S.: About control levels in a software-defined network (SDN). TComm. Telecommun. Transport. 11(3), 50–55 (2017)
S. Volkov, I. Kurochkin Application of machine learning methods in SDN in intrusion detection problems // International Journal of Open Information Technologies ISSN: 2307–8162 vol. 7, no. 11, 2019, pp. 49–58
Smelyanskiy R.L., Pilyugin P.L. Sovremennyye problemy obespecheniya bezopasnosti v SDN [Modern security problems in SDN]// REDS: Telekommunikatsionnyye ustroystva i sistemy [REDS: Telecommunication devices and systems]. 2017, No 4. p. 523–526
Bernardo, D.V., Chua, B.B.: Introduction and Analysis of SDN and NFV Security Architecture (SN-SECA). 796–801 (2015). https://doi.org/10.1109/AINA.2015.270
Feghali, K., Maroun, C.: SDN security problems and solutions analysis, pp. 1–5 (2015). https://doi.org/10.1109/NOTERE.2015.7293514
Liyanage, M., Ahmad, I., Ylianttila, M., Gurtov, A., Abro, A.B., de Oca, D.E.M.: Leveraging LTE security with SDN and NFV. In: Proceedings of the 10th IEEE International Conference on Industrial and InformationSystems (ICIIS), pp. 220–225 (2015)
Kloti, R., Kotronis, V., Smith, P.: OpenFlow: a security analysis. In: 21st IEEE International Conference on Network Protocols (ICNP), pp. 1–6, October 2013
Scott-Hayward, S., O’Callaghan, G., Sezer, S.: SDN security: a survey. In: IEEE SDN for Future Networks and Services (SDN4FNS), pp. 1–7 (2013)
Kreutz, D., Ramos, F., Verissimo, P.: Towards secure and dependable software-defined networks. In: Proceedings of the Second ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking, pp. 55–60 (2013)
Francois, J., Festor, O.: Anomaly traceback using software defined networking. In: International Workshop on Information Forensics and Security (2014)
Vanbever, L., Reich, J., Benson, T., Foster, N., Rexford, J.: HotSwap: correct and efficient controller upgrades for software-defined networks. In: Proceedings of the Second ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking, pp. 133–138 (2013)
3GPP TS 23.101 Universal Mobile Telecommunications System (UMTS). General UMTS Architecture
Principles and Practices for Securing Software-Defined Networks. ONF TR-511 Open Networking Foundation (2015)
Security Foundation Requirements for SDN Controllers. Version 1.0. TR-529. Open Networking Foundation (2016)
Samuilov, K.E., Shalimov, I.A., Buzhin, I.G., Mironov, Yu.B.: Model of functioning of telecommunication equipment of software defined networks. Modern Inf. Technol. IT Educ. 14, 13–26 (2018). No. 1
Tsvetkov, V.K., Oreshkin, V.I., Buzhin, I.G.: Mironov Model of restoration of the communication network using the technology of software defined networks. In: ELCONRUS 2019, pp. 1559–1563. Institute of Electrical and Electronics Engineers Inc. (2019)
Buzhin, I.G., Mironov, Y.B.: Evaluation of delayed telecommunication equipment of Software Defined Networks. In: SOSG 2019, p. 8706825. Institute of Electrical and Electronics Engineers Inc. (2019)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 Springer Nature Switzerland AG
About this paper
Cite this paper
Buzhin, I., Bessonov, M., Mironov, Y., Farkhadov, M.P. (2022). Integrity, Resilience and Security of 5G Transport Networks Based on SDN/NFV Technologies. In: Vishnevskiy, V.M., Samouylov, K.E., Kozyrev, D.V. (eds) Distributed Computer and Communication Networks. DCCN 2021. Communications in Computer and Information Science, vol 1552. Springer, Cham. https://doi.org/10.1007/978-3-030-97110-6_9
Download citation
DOI: https://doi.org/10.1007/978-3-030-97110-6_9
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-97109-0
Online ISBN: 978-3-030-97110-6
eBook Packages: Computer ScienceComputer Science (R0)