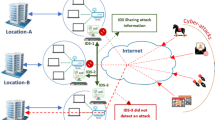
Abstract
Intrusion detection is an important problem in cybersecurity research. In recent years, researchers have leveraged different machine learning algorithms to empower intrusion detection systems (IDS). In this paper, we study the intrusion detection problem using the dataset CIDDS-001 released in 2017. The dataset is much different from the popular datasets using in the literature in that it is not equipped with a comprehensive feature list. We show empirically that we can effectively classify the attacks by using state-of-the-art machine learning algorithms.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Benkhelifa, E., Welsh, T., Hamouda, W.: A critical review of practices and challenges in intrusion detection systems for iot: toward universal and resilient systems. IEEE Commun. Surv. Tutor. 20(4), 3496–3509 (2018)
Chen, T., Guestrin, C.: Xgboost: a scalable tree boosting system. In: KDD, pp. 785–794. ACM (2016)
Dang, Q.V.: Outlier detection in network flow analysis. arXiv:1808.02024 (2018). 4
Dang, Q.V.: Studying machine learning techniques for intrusion detection systems. In: Dang, T., Küng, J., Takizawa, M., Bui, S. (eds.) Future Data and Security Engineering. FDSE 2019. LNCS, vol. 11814, pp. 411– 426. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-35653-8_28
Dang, Q.V.: Active learning for intrusion detection systems. In: IEEE Research, Innovation and Vision for the Future (2020)
Dang, Q.V.: Understanding the Decision of Machine Learning Based Intrusion Detection Systems. In: Dang, T.K., Küng, J., Takizawa, M., Chung, T.M. (eds.) Future Data and Security Engineering. FDSE 2020. LNCS, vol. 12466, pp. 379–396. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-63924-2_22
Dang, Q.V.: Improving the performance of the intrusion detection systems by the machine learning explainability. Int. J. Web Inf. Syst. (2021)
Dang, Q.V., Vo, T.H.: Reinforcement learning for the problem of detecting intrusion in a computer system. In: Proceedings of ICICT (2021)
Dorogush, A.V., Ershov, V., Gulin, A.: Catboost: gradient boosting with categorical features support. arXiv preprint arXiv:1810.11363 (2018)
Elkan, C.: Results of the kdd’99 classifier learning. Acm Sigkdd Explor. Newsl. 1(2), 63–64 (2000)
Ferrag, M.A., Maglaras, L., Moschoyiannis, S., Janicke, H.: Deep learning for cybersecurity intrusion detection: approaches, datasets, and comparative study. J. Inf. Secur. Appl. 50, 102419 (2020)
Liu, F.T., Ting, K.M., Zhou, Z.: Isolation forest. In: ICDM, pp. 413–422. IEEE Computer Society (2008)
MontazeriShatoori, M., Davidson, L., Kaur, G., Lashkari, A.H.: Detection of doh tunnels using time-series classification of encrypted traffic. In: 2020 IEEE International Conference on Dependable, Autonomic and Secure Computing, International Conference on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, International Conference on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), pp. 63–70. IEEE (2020)
Ring, M., Wunderlich, S., Grüdl, D., Landes, D., Hotho, A.: Flow-based benchmark data sets for intrusion detection. In: Proceedings of the 16th European Conference on Cyber Warfare and Security, pp. 361–369. ACPI (2017)
Salih, A.A., Abdulazeez, A.M.: Evaluation of classification algorithms for intrusion detection system: a review. J. Soft Comput. Data Min. 2(1), 31–40 (2021)
Samrin, R., Vasumathi, D.: Review on anomaly based network intrusion detection system. In: 2017 International Conference on Electrical, Electronics, Communication, Computer, and Optimization Techniques (ICEECCOT), pp. 141–147. IEEE (2017)
Settles, B.: Active learning. Synthesis Lect. Artif. Intell. Mach. Learn. 6(1), 1–114 (2012)
Sharafaldin, I., Lashkari, A.H., Ghorbani, A.A.: Toward generating a new intrusion detection dataset and intrusion traffic characterization. ICISSp 1, 108–116 (2018)
Thakkar, A., Lohiya, R.: A review of the advancement in intrusion detection datasets. Procedia Comput. Sci. 167, 636–645 (2020)
Wang, H., Bah, M.J., Hammad, M.: Progress in outlier detection techniques: a survey. IEEE Access 7, 107964–108000 (2019)
Zhou, X., Hu, Y., Liang, W., Ma, J., Jin, Q.: Variational lstm enhanced anomaly detection for industrial big data. IEEE Trans. Ind. Inf. 17(5), 3469–3477 (2020)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Dang, QV. (2022). Studying the Attack Detection Problem Using the Dataset CIDDS-001. In: Antipova, T. (eds) Digital Science. DSIC 2021. Lecture Notes in Networks and Systems, vol 381. Springer, Cham. https://doi.org/10.1007/978-3-030-93677-8_46
Download citation
DOI: https://doi.org/10.1007/978-3-030-93677-8_46
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-93676-1
Online ISBN: 978-3-030-93677-8
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)