Abstract
Global navigational satellite systems provide accurate time synchronization and location services. Satellites transmit navigation messages that can be used by a receiver to compute its location. However, most navigation messages are not protected and are easily spoofed. Several attacks have been reported that transmit spoofed or replayed GPS signals to divert or hijack autonomous vehicles, ships and drones. Unfortunately, non-cryptographic protection methods that use antenna arrays, pseudorange differences and multi-receivers to detect GPS spoofing tend to be inaccurate due to environmental conditions.
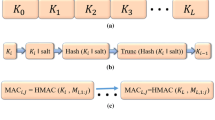
This chapter proposes an efficient GPS signal authentication protocol that engages a dedicated server to continuously compute hash-based message authentication codes of GPS navigation messages received from satellites using the chameleon hash keychain. The keychain is practically unbounded, which enables GPS receivers to easily authenticate the server and verify GPS signals concurrently by checking the hash-based message authentication codes. A proof-of-concept prototype has been developed to demonstrate the feasibility of the authentication scheme. Experimental results demonstrate that the hash key in the keychain can be updated every 30 seconds, enabling every five GPS message subframes to be secured with a different hash key. This makes it difficult for attackers to compromise GPS navigation
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
J. Bhatti and T. Humphreys, Hostile control of ships via false GPS signals: Demonstration and detection, Journal of the Institute of Navigation, vol. 64(1), pp. 51–66, 2017.
M. bin Mohammad Fadilah, V. Balachandran, P. Loh and M. Chua, DRAT: A drone attack tool for vulnerability assessment, Proceedings of the Tenth ACM Conference on Data and Application Security and Privacy, pp. 153–155, 2020.
D. Borio and C. Gioia, A sum-of-squares approach to GNSS spoofing detection, IEEE Transactions on Aerospace and Electronic Systems, vol. 52(4), pp. 1756–1768, 2016.
A. Broumandan, A. Jafarnia-Jahromi and G. Lachapelle, Spoofing detection, classification and cancellation (SDCC) receiver architecture for a moving GNSS receiver, GPS Solutions, vol. 19(3), pp. 475–487, 2015.
R. Di Pietro, A. Durante, L. Mancini and V. Patil, Practically unbounded one-way chains for authentication with backward secrecy, Proceedings of the First IEEE International Conference on Security and Privacy for Emerging Areas in Communications Networks, pp. 400–402, 2005.
I. Fernandez-Hernandez, V. Rijmen, G. Seco-Granados, J. Simon, I. Rodriguez and J. Calle, A navigation message authentication proposal for the Galileo Open Service, Journal of the Institute of Navigation, vol. 63(1), pp. 85–102, 2016.
K. Ghorbani, N. Orouji and M. Mosavi, Navigation message authentication based on a one-way hash chain to mitigate spoofing attacks on GPS L1, Wireless Personal Communications, vol. 113(4), pp. 1743–1754, 2020.
T. Humphreys, B. Ledvina, M. Psiaki, B. O’Hanlon and P. Kintner Jr., Assessing the spoofing threat: Development of a portable GPS civilian spoofer, Proceedings of the Twenty-First International Technical Meeting of the Satellite Division of the Institute of Navigation, pp. 2314–2325, 2008.
K. Jansen, N. Tippenhauer and C. Popper, Multi-receiver GPS spoofing detection: Error models and realization, Proceedings of the Thirty-Second Annual Computer Security Applications Conference, pp. 237–250, 2016.
S. Keoh, K. Au and Z. Tang, Securing industrial control systems: An end-to-end integrity verification approach, presented at the Industrial Control System Security Workshop of the Thirty-First Annual Computer Security Applications Conference (www.acsac.org/2015/workshops/icss), 2015.
S. Keoh, H. Tan and Z. Tang, Authentication and integrity protection for real-time cyber-physical systems, in Handbook of Real-Time Computing, Y. Tian and D. Levy (Eds.), Springer, Singapore, chapter 3, 2020.
N. Koblitz, Elliptic curve cryptosystems, Mathematics of Computation, vol. 48(177), pp. 203–209, 1987.
H. Krawczyk and T. Rabin, Chameleon Hashing and Signatures, Cryptography ePrint Archive, Report 1998/010 (eprint.iacr.org/1998/010), 1998.
K. Liu, W. Wu, Z. Wu, L. He and K. Tang, Spoofing detection algorithm based on pseudorange differences, Sensors, vol. 18(10), article no. 3197, 2018.
D. Manandhar and R. Shibasaki, Authenticating Galileo Open Service signals using QZSS signals, Proceedings of the Thirty-First International Technical Meeting of the Satellite Division of the Institute of Navigation, pp. 3995–4003, 2018.
J. Noh, Y. Kwon, Y. Son, H. Shin, D. Kim, J. Choi and Y. Kim, Tractor Beam: Safe-hijacking of consumer drones with adaptive GPS spoofing, ACM Transactions on Privacy and Security, vol. 22(2), article no. 12, 2019.
A. Perrig and J. Tygar, TESLA broadcast authentication, in Secure Broadcast Communication, A. Perrig and J. Tygar (Eds.), Springer, Boston, Massachusetts, pp. 29–53, 2003.
M. Psiaki, B. O’Hanlon, J. Bhatti, D. Shepard and T. Humphreys, GPS spoofing detection via dual-receiver correlation of military signals, IEEE Transactions on Aerospace and Electronic Systems, vol. 49(4), pp. 2250–2267, 2013.
D. Radin, P. Swaszek, K. Seals and R. Hartnett, GNSS spoof detection based on pseudoranges from multiple receivers, Proceedings of the Twenty-Eighth International Technical Meeting of the Institute of Navigation, pp. 657–671, 2015.
J. Su, J. He, P. Cheng and J. Chen, A stealthy GPS spoofing strategy for manipulating the trajectory of an unmanned aerial vehicle, IFAC-PapersOnLine, vol. 49(22), pp. 291–296, 2016.
H. Tan, K. Lim, S. Keoh, Z. Tang, D. Leong and C. Sum, Chameleon: A blind double trapdoor hash function for securing AMI data aggregation, Proceedings of the Fourth IEEE World Forum on the Internet of Things, pp. 225–230, 2018.
J. Van Sickle and J. Dutton, GEOG862: GPS and GNSS for Geospatial Professionals, Department of Geography, Pennsylvania State University, University Park, Pennsylvania (www.e-education.psu.edu/geog862/home.html), 2014.
W. Wang, G. Chen, R. Wu, D. Lu and L. Wang, A low-complexity spoofing detection and suppression approach for ADS-B, Proceedings of the Integrated Communications, Navigation and Surveillance Conference, 2015.
K. Wesson, M. Rothlisberger and T. Humphreys, A proposed navigation message authentication implementation for civil GPS anti-spoofing, Proceedings of the Twenty-Fourth International Technical Meeting of the Satellite Division of the Institute of Navigation, pp. 3129–3140, 2011.
Z. Wu, Y. Zhang and R. Liu, BD-II NMA&SSI: A scheme for anti-spoofing and open BeiDou II D2 navigation message authentication, IEEE Access, vol. 8, pp. 23759–23775, 2020.
M. Yuan, Z. Lv, H. Chen, J. Li and G. Ou, An implementation of navigation message authentication with reserved bits for civil BDS anti-spoofing, in China Satellite Navigation Conference (CSNC) 2017 Proceedings: Volume II, J. Sun, J. Liu, Y. Yang, S. Fan and W. Yu (Eds.), Springer, Singapore, pp. 69–80, 2017.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 IFIP International Federation for Information Processing
About this paper
Cite this paper
Chu, Y.H., Keoh, S.L., Seow, C.K., Cao, Q., Wen, K., Tan, S.Y. (2022). GPS Signal Authentication Using a Chameleon Hash Keychain. In: Staggs, J., Shenoi, S. (eds) Critical Infrastructure Protection XV. ICCIP 2021. IFIP Advances in Information and Communication Technology, vol 636. Springer, Cham. https://doi.org/10.1007/978-3-030-93511-5_10
Download citation
DOI: https://doi.org/10.1007/978-3-030-93511-5_10
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-93510-8
Online ISBN: 978-3-030-93511-5
eBook Packages: Computer ScienceComputer Science (R0)