Abstract
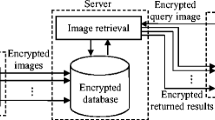
Search through a database of encrypted images against a crumpled and encrypted query will remain privacy preserving only if comparisons between selective features derived from these images is executed in the encrypted domain itself. To facilitate this, the encryption process must remain transparent to specific image statistics computed in the spatial or transform domain. Consequently, the perceptual hash formed by quantizing the image statistics remains the same before and after the encryption process. In this paper, we propose a transparent privacy preserving hashing scheme tailored to preserve the DCT-AC coefficient distributions, despite a constrained inter-block shuffling operation. These DCT distributions can be mapped onto a generalized Gaussian model characterized by shape and scale parameters, which can be quantized and Gray-coded into a binary hash matrix. The encryption scheme has been shown to be perceptually secure and does not impair the search reliability and accuracy of the hashing procedure. Experimental results have been provided to verify the robustness of the hash to content-preserving transformations, while demonstrating adequate sensitivity to discriminate between different images.















Similar content being viewed by others
References
Venkatesan, R., Koon, S.-M., Jakubowski, M., Moulin, P.: Robust image hashing. In: Proceedings of International Conference on Image Processing, vol. 3, pp. 664–666 (2000)
Karthik, K.: Robust image hashing by downsampling: between mean and median. In: World Congress on Information and Communication Technologies (WICT), pp. 622–627 (2011)
Monga, V., Evans, B.L.: Perceptual image hashing via feature points: performance evaluation and tradeoffs. IEEE Trans. Image Process. 15, 3452–3465 (2006)
Nister, D., Stewenius, H.: Scalable recognition with a vocabulary tree. In: IEEE Computer Society Conference on Computer Vision and, Pattern Recognition (CVPR06), vol. 2, pp. 2161–2168 (2006)
Lu, W., Swaminathan, A., Varna, A.L., Wu, M.: Enabling search over encrypted multimedia databases. In: Proceedings Media Forensics and Security I, vol. 7254 of SPIE Proceedings, SPIE (2009)
Monga, V., Banerjee, A., Evans, B.L.: A clustering based approach to perceptual image hashing. IEEE Trans. Inf. Forensics Secur. 1, 68–79 (2006)
Lu, W., Varna, A.L., Swaminathan, A., Wu, M.: Secure image retrieval through feature protection. In: Proceedings of the IEEE International Conference on Acoustics, Speech, and, Signal Processing (ICASSP09), 19–24 April 2009, pp. 1533–1536 (2009)
Achlioptas, D.: Database-friendly random projections. In: Proceedings of the Twentieth ACM Symposium on Principles of Database Systems, PODS ’01, pp. 274–281 (2001)
Vempala, S.S.: The Random Projection Method. DIMACS Series in Discrete Mathematics and Theoretical Computer Science. American Mathematical Society, Providence (2004)
Chum, O., Perdoch, M., Matas, J.: Geometric min-hashing: finding a (thick) needle in a haystack. In: International Conference on Computer Vision and Pattern Recognition (CVPR 2009), 20–25 June 2009, Miami, Florida, USA, pp. 17–24, IEEE (2009)
Hsu, C.-Y., Lu, C.-S., Pei, S.-C.: Homomorphic encryption-based secure SIFT for privacy-preserving feature extraction. In: Proceedings of SPIE 7880, Media Watermarking, Security, and Forensics III, 788005, 8 Feb 2011
Kashyap, S., Karthik, K.: Authenticating encrypted data. In: National Conference on Communications (NCC) 2011, January 28–30 (2011)
Shannon, C.E.: Communication theory of secrecy systems. Bell Syst. Tech. J. 28, 656–715 (1949)
Wang, Y.-G., Lei, Y.-Q.: A robust content in DCT domain for image authentication. In: International Conference on Intelligent Information Hiding and Multimedia Signal Processing, pp. 94–97, Kyoto, Japan (2009)
Sharifi, K., Garcia, L.: Estimation of shape parameter for generalized Gaussian distribution in subband decomposition of video. IEEE Trans. Circuits Syst. Video Technol. 5, 52–56 (1995)
Dominguez, J.A.: A practical procedure to estimate the shape parameter in a generalized gaussian distribution. Technical Report. http://www.cimat.mx/reportes/enlinea/I-01-18_eng.pdf (2001)
Swaminathan, A., Mao, Y., Wu, M.: Robust and secure image hashing. IEEE Trans. Inf. Forensics Secur. 1, 215–230 (2006)
Zhu, G., Kwong, S., Huang, J., Yang, J.: Random gray code and its performance analysis for image hashing. Signal Process. 91, 2178–2193 (2011)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Karthik, K., Kashyap, S. Transparent hashing in the encrypted domain for privacy preserving image retrieval. SIViP 7, 647–664 (2013). https://doi.org/10.1007/s11760-013-0471-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11760-013-0471-0