Abstract
A significant volume of information leaks in organizations are inadvertent, a form of information spillage. Because the leakage of information is driven by the complex interaction of technology, social, and behavioral factors, we use a hybrid agent-based and dynamic network model, Construct, to simulate the flow of sensitive information in knowledge-driven organizations. Because interaction patterns often change when an organization is under stress, we simulate stress to the organization with effect-based (reliability and integrity) crisis scenarios. Using a virtual experiment, we vary the crisis scenarios, organization’s structure, IT connections, and pressure to separate personnel based on security ratings. Our experiment suggests that the organization’s structure, IT connections, separation pressure, and typical performance all influence how much an organization suffers from inadvertent leakage. In evaluating how organizations respond to crisis, organizations with stove-piped IT tend to clamp down on leakage in response to the crisis, while organizations with Mesh IT tend to have more leakage. Integrity crises tend to decrease leakage; while reliability crises tend to increase leakage in organizations, especially those with Mesh-based IT.




Similar content being viewed by others
Notes
See InformationIsBeautiful.net for a frequently updated list of attacks. InformationIsBeautiful.net. (2015, August 6th, 2015). World's Biggest Data Breaches. Retrieved August 2015, from http://www.informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks/.
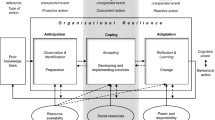
This is not a hard assumption of the model. Five functional areas were merely considered sufficient and illustrative.
We also evaluated a measure that strictly relied on performance within functional category, and we found that many of these simulated organizations essentially end up with stable coherent groups that nominally do one thing and actually do another. We feel this is realistic to actual organizational practice (functional labels and actual work processes are often distinct), but makes this measure difficult to apply in assessing response.
References
Alexander KB (2008). National Instruction on Classified Information Spillage CNSS Instruction. Committee of National Security Systems (CNSS), Ft. Meade, MD
Alphonso C, Hammer K (2014) Inadvertent information leak costs TDSB $700,000, The Globe and Mail, Toronto. http://www.theglobeandmail.com/news/national/education/security-breach-forces-tdsb-to-change-locks-at-more-than-100-schools/article19437531/. Accessed June 2015
Associated Press (2012) Unsecured email led to leak of FBI and Scotland Yard call. Retrieved July 26 2015, July 2015, from http://www.nbcnews.com/id/46643788/ns/technology_and_science-security/t/unsecured-email-led-leak-fbi-scotland-yard-call/#.VbhG6_lVino
Band DR, Cappelli D, Fischer LF, Moore AP, Shaw ED, Trzeciak RF (2006) Comparing insider IT sabotage and espionage: a model-based analysis (Carnegie-Mellon University: Software Engineering Institute. CERT Coordination Center, 2006), available at: http://www.cert.org/archive/pdf/06tr026.pdf
Bishop M (2013) Position: insider is relative. In: Proceedings of the 2005 workshop on new security paradigms, ACM, pp 77–78
Cappelli D, Desai AG, Moore AP, Shimeall TJ, Weaver EA, Willke BJ (2008) Management and education of the risk of insider threat (MERIT): system dynamics modeling of computer system, SEI White paper
Carley KM (1990) Group stability: a socio-cognitive approach. In: Lawler E, Markovsky B, Ridgeway C, Walker H (eds) Advances in Group Processes: Theory and Research (Vol, vol III. JAI Press, Greenwhich, CT, pp 1–44
Carley KM (1991) A theory of group stability. Am Sociol Rev 56(3):331–354
Carley KM (1992) Organizational learning and personnel turnover. Organ Sci 3(1):20–46
Carley KM (2003). Dynamic network analysis. In Breiger R, Carley KM, & Pattison P (Eds.) Summary of the NRC workshop on social network modeling and analysis (pp 133–145): Committee on Human Factors, National Research Council
Carley KM, Hill V (2001) Structural change and learning within organizations. In: A. Lomi, Larsen ER (Eds.), Dynamics of organizations: Computational modeling and organizational theories (pp 63–92)
Carley KM, Lee J, Krackhardt D (2001) Destabilizing Networks. Connections 24(3):31–34
Carley KM, Martin MK, Hirshman BR (2009) The etiology of social change. Topics Cognit Sci 1(4):621–650
Carley KM, Morgan GP, Lanham M, Pfeffer J (2012) Multi-modeling and socio-cultural complexity: reuse and validation. Adv Des Cross Cult Act 2:128
Chan M (2003) Corporate espionage and workplace trust/distrust. J Bus Ethics 42(1):45–58
Chandrasekaran M, Sankaranarayanan V, Upadhyaya S (2008) Inferring sources of leaks in document management systems. In: Advances in Digital Forensics IV, Springer, pp 291–306
Cisco (2008) Data Leakage Worldwide: The High Cost of Insider Threats, Cisco Publications, USA, also available at http://www.cisco.com/c/en/us/solutions/collateral/enterprise-networks/data-loss-prevention/white_paper_c11-506224.html
Cluley G (2015) Dropbox users continue to unwittingly leak tax returns and other private data. Retrieved July 2 2015, July 2015, from https://grahamcluley.com/2015/04/dropbox-leak-tax-return/
Cox LP, Gilbert P (2009) Redflag: reducing inadvertent leaks by personal machines. Technical Report TR-2009-02, Duke University
CSI/FBI (2005) Computer crime and security study, Forrester Research, Inc
CSI/FBI (2012) Computer crime and security study, Forrester Research, Inc
Denison DR, Hart SL, Kahn JA (1996) From chimneys to cross-functional teams: developing and validating a diagnostic model. Acad Manag J 39(4):1005–1023
Fairweather NB (1999) Surveillance in employment: the case of teleworking. J Bus Ethics 22(1):39–49
Federal Bureau of Investigation (2014) The insider threat: an introduction to detecting and deterring an insider spy. FBI. September. http://www.fbi.gov/about-us/investigate/counterintelligence/the-insider-threat
Financial Services Technology (2010). The true cost of a data leak, http://www.usfst.com/article/The-true-cost-of-a-data-leak/. Accessed Feb 2014
Good N (2010) A brief history of inadvertent sharing on P2P networks: causes, current solutions and future directions. Intelligent methods for protecting privacy and confidentiality in data, 13
Green C (2014) Accidental data leaks by staff now a primary security weak point. http://www.information-age.com/technology/security/123458600/accidental-data-leaks-staff-now-primary-security-weak-point. Accessed June 2015
Greitzer FL, Hohimer RE (2011) Modeling human behavior to anticipate insider attacks. J Strateg Secur 4(2):25–48
Gudaitis TM (1998) The missing link in information security: three dimensional profiling. Cyber Psychology & Behavior 1:321–340
Heimbuch J (2008) Hackers Help the Hacking Down of the Amazon Rainforests, Treehugger, http://www.treehugger.com/corporate-responsibility/hackers-help-the-hacking-down-of-the-amazon-rainforests.html. Accessed June 2015
Herbig KL (2008) Changes in espionage by Americans, 1947-2007. PERSEREC Technical Report 08-05. Defense Personnel and Security Research Center (PERSEREC). https://www.scribd.com/doc/192035027/Katherine-L-Herbig-Changes-in-Espionage-by-Americans-1947-2007-Technical-Report-08-05-Northrop-Grumman-March-2008
Hogan R, Hogan J (1994) The mask of integrity. Citizen espionage: studies in trust and betrayal, pp 107–125
Johnson ME (2008) Information risk of inadvertent disclosure: an analysis of file-sharing risk in the financial supply chain. J Manag Inf Syst 25(2):97–124
Johnson ME, Dynes S (2007) Inadvertent disclosure-information leaks in the extended enterprise. In: Proceedings of the sixth workshop on the economics of information security, Carnegie Mellon University, Pittsburgh PA, http://weis2007.econinfosec.org/papers/43.pdf
Joseph K, Morgan GP, Martin MK, Carley KM (2014) On the coevolution of stereotype, culture, and social relationships: an agent-based model. Soc Sci Comput Rev 32(3):295–311. doi:10.1177/0894439313511388
Kemerlis VP, Pappas V, Portokalidis G, Keromytis AD (2010) iLeak: A lightweight system for detecting inadvertent information leaks. In Proceedings of the 6th European Conference on Computer Network Defense (EC2ND), pp 21–28
Kessler S (2011) Sony promises all PlayStation services will return this week (again). Retrieved August 2015, 2015, from http://mashable.com/2011/05/31/sony-playstation-services-return/
Kraemer S, Carayon P, Clem J (2009) Human and organizational factors in computer and information security: pathways to vulnerabilities. Comput Secur 28(7):509–520. doi:10.1016/j.cose.2009.04.006
Luft M, Holz T (2011) A small leak will sink a great ship: an empirical study of DLP solutions. In: ISSE 2010 securing electronic business processes, Vieweg + Teubner, , pp 354–364
Martinez-Moyano IJ, Rich E, Conrad S, Andersen DF, Stewart TR (2008) A behavioral theory of insider-threat risks: a system dynamics approach. ACM Trans Model Comput Simul 18, 2, Article 7
McMillan R (2006) Auditor loses thousands of McAfee employees’ data. http://www.infoworld.com/article/2656626/security/auditor-loses-thousands-of-mcafee-employees–data.html. Accessed June 2015
McPherson M, Smith-Lovin L, Cook JM (2001) Birds of a feather: homophily in social networks. Ann Rev Sociol 27:415–444
Merrill Lynch survey of 50 North American CISOs, July 2006
Parno B, McCune JM, Wendlandt D, Andersen DG, Perrig A (2009) CLAMP: practical prevention of large-scale data leaks. In: Security and privacy, 2009 30th IEEE symposium on IEEE Ponemon Institute, SVB Alliant 9, pp 154–169
Royds J (2009) Virtual battlefield. CIR Magazine, London
Ruighaver A, Maynard S, Chang S (2006) Organizational security culture: extending the end-user perspective. Comput Secur 26:2006
Schölkopf B, Smola AJ (2005) Learning with kernels. MIT Press, Cambridge 2002
Schultz EE (2002) A framework for understanding and predicting insider attacks. Comput Secur 21:526–531
SecureList (2010) Global Research on Data Leaks in 2009. Research on Data Leaks in 2009. http://www.securelist.com/en/analysis/204792108/Global. Accessed Feb 2015
Shaw ED, Fischer L (2005) Ten tales of betrayal: an analysis of attacks on corporate infrastructure by information technology insiders. Defense Personnel Security Research and Education Centre, 1
Shaw ED, Ruby K, Post J (1999) Inside the mind of an insider. Secur Manag 1999:34–44
Simon HA (1991) Bounded rationality and organizational learning. Organ Sci 2(1):125–134
Son T (2002) Leaks: how do codes of ethics address them? J Mass Media Ethics 17(2):155–173
Spitzner L (2003) Honeypots: catching the insider threat. In: Computer security applications conference, 2003, proceedings, 19th annual, IEEE
Stealth Aircraft Report (1980) Stealth aircraft: a report of the house investigations subcommittee of the committee on armed services. In: 96th congress, 2nd session
Tant AP (1995) ‘Leaks’and the nature of British government. Polit Q 66(2):197–209
Valente TH, Poppe PR, Merritt AP (1996) Mass-media-generated interpersonal communication as sources of information about family planning. J Health Commun Int Perspect 1(3):247–266
Wall DS (2013) Enemies within: redefining the insider threat in organizational security policy. Secur J 26(2):107–124
Wegner DM (1995) A computer network model of human transactive memory. Soc Cognit 13(3):319–339
Wicks AC, Berman SL, Jones TM (1999) The structure of optimal trust: moral and strategic implications. Acad Manag Rev 24(1):99–116
Xanders EL (1988) Handyman’s guide to fixing national security leaks: an analytical framework for evaluating proposals to curb unauthorized publication of classified information. A J L Pol 5:759
Morgan GP, Carley KM Network-centric socio-technical organizational models to predict cyber-attack impact, working paper
Zavou A, Pappas V, Kemerlis VP, Polychronakis M, Portokalidis G, Keromytis AD (2013) Cloudopsy: an autopsy of data flows in the cloud. In: human aspects of information security, privacy, and trust, pp 366–375, Springer, Berlin
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Carley, K.M., Morgan, G.P. Inadvertent leaks: exploration via agent-based dynamic network simulation. Comput Math Organ Theory 22, 288–317 (2016). https://doi.org/10.1007/s10588-016-9215-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10588-016-9215-3